It’s 1983, and Ronald Reagan is sitting down to watch the hit film War Games. Five days later, the president asked his secretaries of state, “Could a scenario like war games ever happen?” One week later, General Vessey returned with the answer: “Mr. President, it is a lot worse than you think.”
Was this the first time that cyber security and privacy had surfaced in computer systems? Categorically, no. Security and Privacy in Computer systems 1967 by Willis Ware was the first paper on the topic — written in 1967. So, since the beginning of networked computing, cyber security, and privacy have been a factor. So, why is it suddenly a huge industry buzzword?
My thoughts on this are twofold:
- Across governments, the use and ideas of cyber warfare were dismissed, ignored, or forgotten. But in 2007, the Aurora test categorically proved that cyber attackers could inflict physical damage using computer tools. This was a pivotal moment, as critical infrastructure was at risk.
- Cybercrime then shifted to the public sphere with cyber groups lining their sights on non-government attacks, such as online fraud, ransomware, malware, and phishing.
The role that security and privacy now play in IT and our personal lives is huge. Strong security practices have gone from a nice interest to an expected standard.
The Ransomware Problem
Ransomware has dominated headlines over the last few years as businesses were, and still are, targeted. 2017 alone has seen some huge headline attacks – #wannacry #badrabbit #nonpetya – all targeting businesses to encrypt their data and charge ransom. To give you an idea of ransomware’s recent success:
- Q1 2016: $209 million in revenue with 2016 totaling $1 Billion
- 56,000 infections per month
- 101 known ransomware families
- Delivery via a range of mechanisms from exploit kits, email, and website links

What many are not aware of is the ecosystem that underpins these ransomware families. The Cerber ransomware family, for instance, accounted for 70% of all attacks this year up until #wannacry. This marks the increasing accessibility of “Ransomware-as-a-Service” or RaaS, which is now available to an audience beyond cybercriminal groups.
So how does RaaS work? It’s the simple franchise-like deployment model. Instead of writing their own malicious code, aspiring cybercriminals can now log in to their RaaS portal of choice, configure their deployment, and instantly distribute the malware to unwitting victims.
Ransomware Sophistication
Early forms of ransomware were not overly sophisticated. But the Cerber family exhibited an unprecedented amount of detail and sophistication.
For a detailed analysis on Cerber, read this report.
Some features of Cerber:
- An encrypted JSON file gives the user the ability to change settings (such as target certain file types), avoid certain language packs or IP ranges, or perform environment checks (looks for AV/VM).
- Modern ransomware looks for almost all file types, including VMware, databases, java-script, and email. It creates multiple Mutex’s, gains persistency in Windows, and has fault or watcher processes so that it can be re-spawned.
- If Cerber detects it’s being hunted, it will shut down and not run. UAC mode is completely bypassed
- Cerber can encrypt without having any internet connectivity; it has the encryption keys in the payload (RSA-2048)
- Sends statistics via UDP home. Essentially, it will upload statistics of what it discovered in your environment if possible
- Encrypts your data with a high degree of entropy
What Can We Do?
Over the years, I have been speaking about ransomware. By hearing people’s ideas and advice across the globe, I’ve created some basic tips that can help protect against ransomware:
Entry Points (Web, devices, USB and email)
- Use standard practices of scan emails and block USB ports
- Do not enable web access on VMs
- Patch, patch and patch again – just look at the #wannacry virus
- Isolate / different networks for your personal devices
Users and Access
- Train users, both end users and IT users. This is critical in identifying and responding to ransomware.
- Set software restrictions – remove the ability for users to run .exe. While this is radical, if users cannot run a payload, then ransomware cannot run!
- Least privilege access management. Only provide employees access to data to those who need it.
- Audit file shares
- Updated firewalls \ IPS and policies
The Bottom Line
These are just some practices you can use to help protect your data. The bottom line is that ransomware isn’t going away, and most customers I speak to (regardless of how many layers of defense are in their environments) admit it’s not if but when ransomware will strike. Any report you read on ransomware will state that “backups are a must.”
So, what if you are compromised? Don’t panic. Here’s what I recommend:
- Respond and isolate the spread
- Test before restoring
- Restore
- Root cause analysis
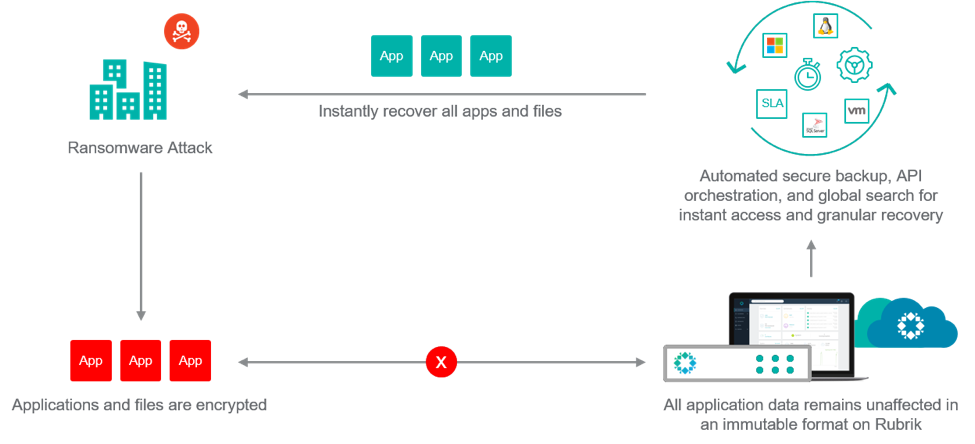
The key here is your response time and getting the affected data back online in the shortest time possible.
Rubrik delivers a highly-automated backup with near-instant RTO. But, most importantly, all the backups are immutable, so they can only be read not over written. Protecting your valuable data with a highly-automated backup platform is key in having the assurance that, should ransomware infect your environment, you can recover quickly.
Conclusion
Ransomware is not going away anytime soon. So, it’s imperative that businesses across industries adopt a data management strategy of multi-layered security, easy automation, and quick recovery. Watch how one of customers quickly recovered from ransomware without data loss.
More Resources
- Test your recoverability from ransomware using Shinolocker.
- Note this is not a test of your anti-virus or malware detection, it is a simple freeware encryption program that allows you to test your “restore” process.
- Cyber Security Information sharing partnership (CISP) a part of GCHQ, an online portal providing
- No more ransomware project.
