Rubrik Security Cloud
Become unstoppable against cyberattacks and operational failures. Rubrik Security Cloud helps you protect your data, monitor data risk, and recover data and applications, so you can keep your business moving forward.

The State of Data Security
Cyberattacks are increasing in frequency and sophistication. Despite large investments in infrastructure security tools, bad actors are finding their way through to the data. And they know legacy backup tools are vulnerable, so they are increasingly targeting backup data.

of IT and security leaders were made aware of at least one attack in 2022.

of external organizations
reported malicious actors attempting to
impact data backups during a cyberattack.

of the attacks on backups were at least partially successful.
When a cyber attack takes down your data, it takes down your organization. It’s time for a new approach–one that marries the investments you’ve made in infrastructure security with data security.
The Trusted Data Security Solution for Cyber Recovery
Still relying on legacy backup systems? You're putting your data and your organization at risk. Here's why you need a data security approach instead.
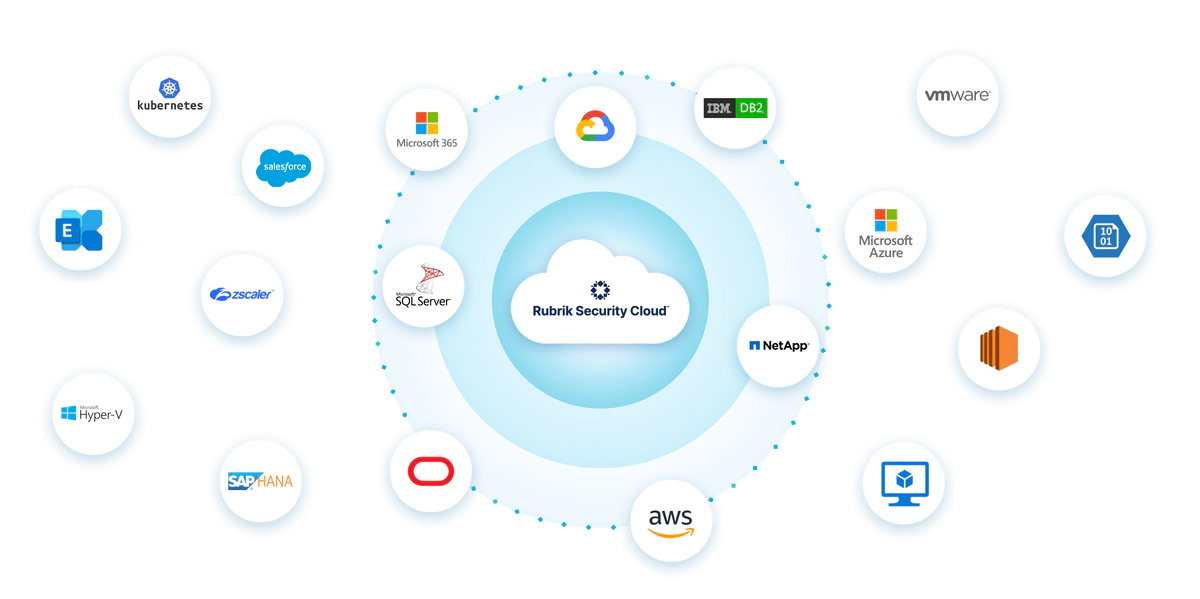
Secure your data wherever it lives
Protect data across the enterprise, in the cloud, and in SaaS applications.
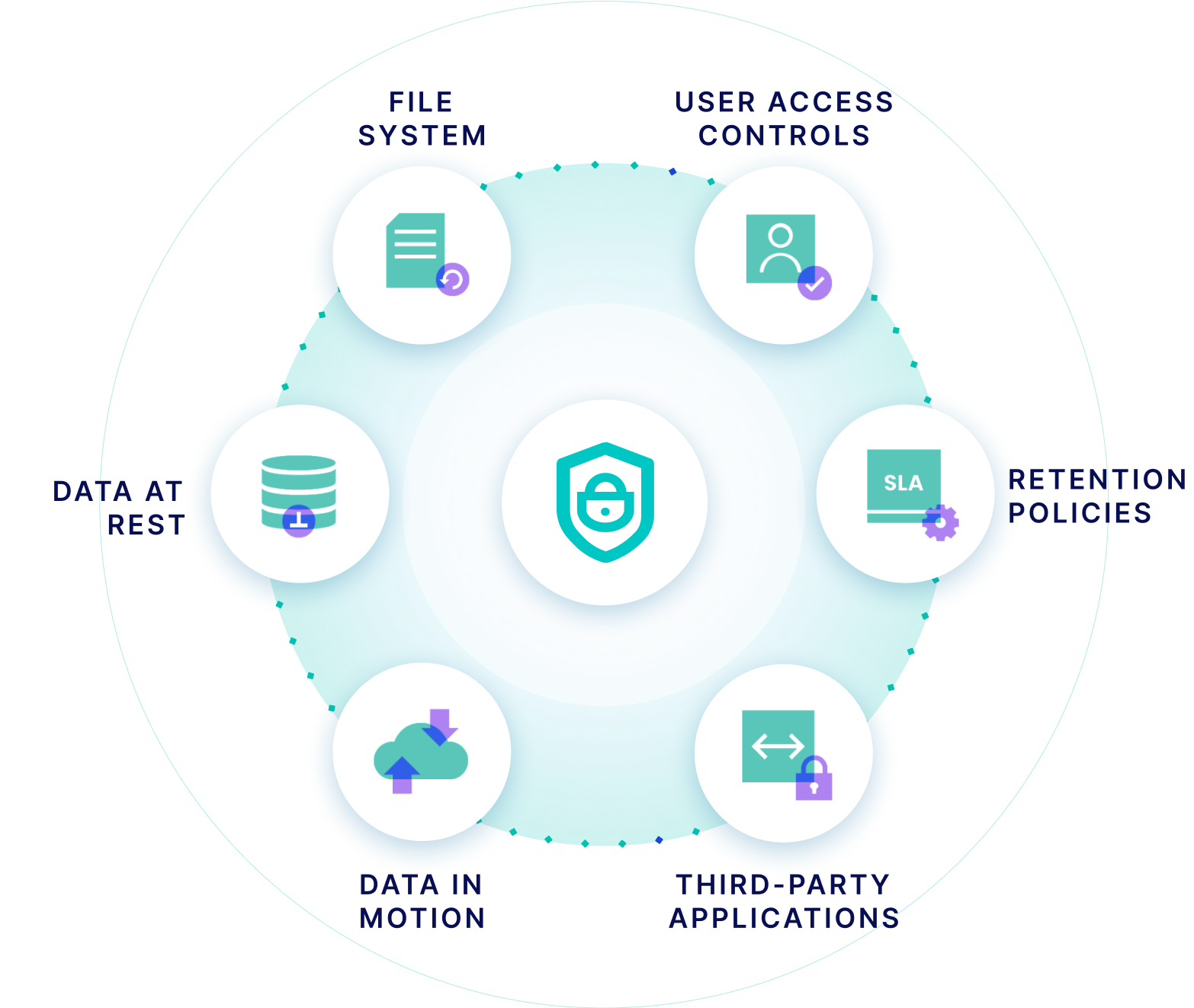
Zero Trust By Design
Rubrik Security Cloud was architected using Zero Trust principles to prevent threats at the data layer. Our use of native immutability, secure protocols, logical air gap, encryption, role-based access controls, multi-factor authentication, and native services uphold data integrity and availability.
Global Policy Driven Automation
With Rubrik’s Global Policy Driven Automation, you can ensure data availability, maintain policy compliance, and orchestrate recovery workflows. Rubrik enforces data security strategies with automated discovery and policy-driven workflows, while ensuring fast and predictable recoveries with an understanding of application relationships.

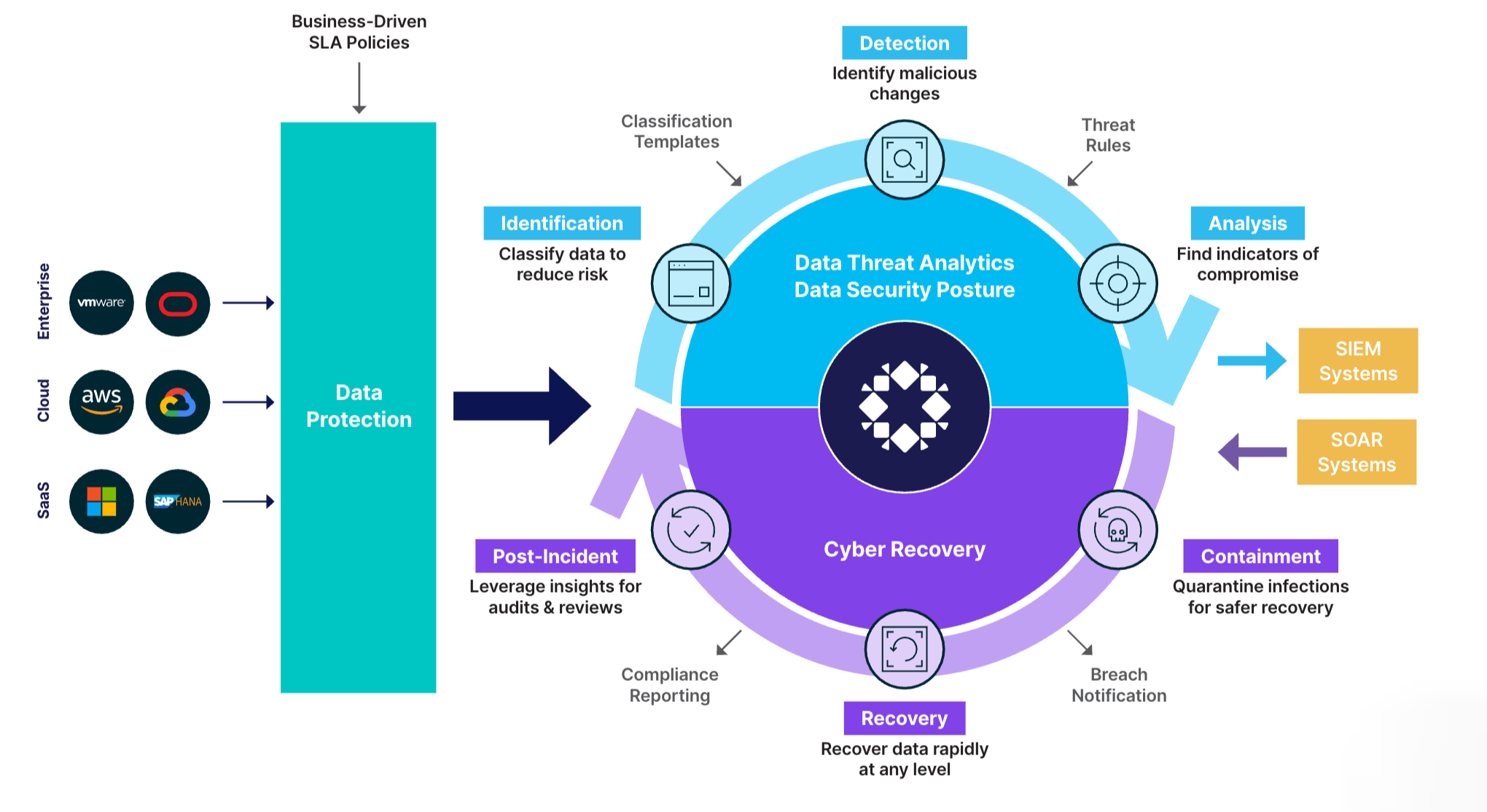
Data Risk Assessment & Anomaly Detection
With Rubrik’s Data Risk Assessment & Anomaly Detection, you can identify your data exposure, investigate threats faster and avoid reinfection by malware.

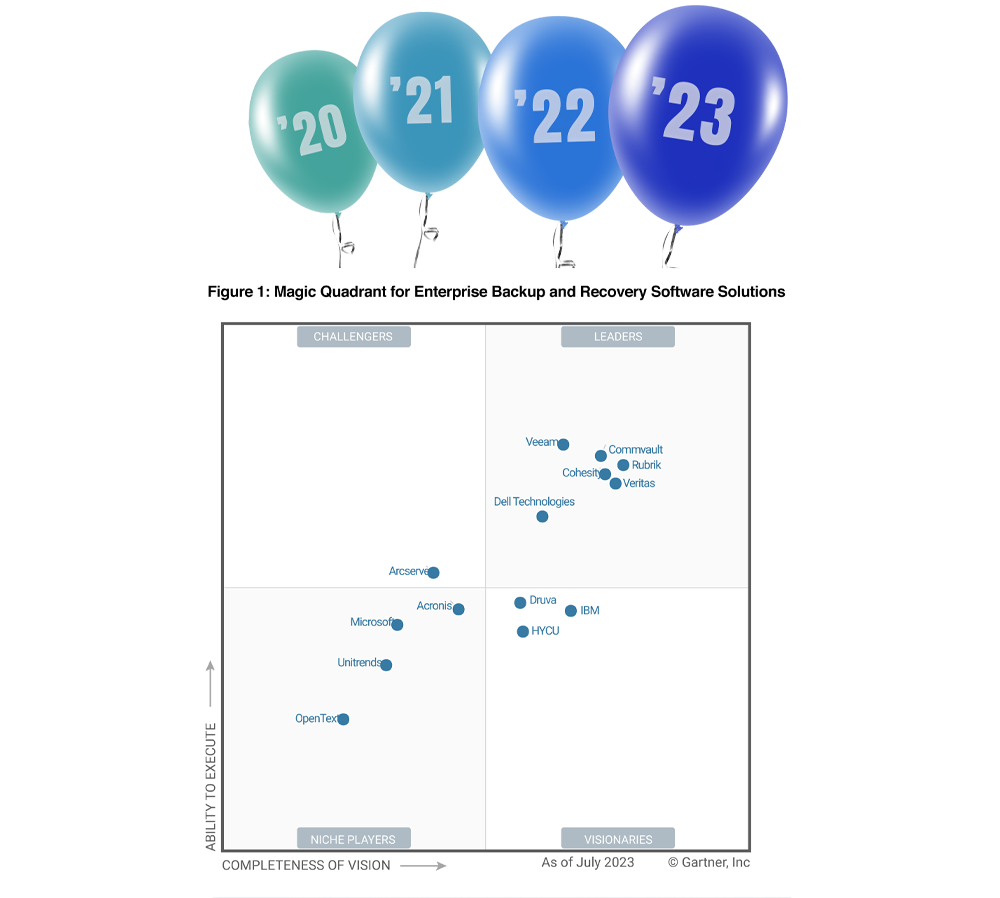
Rubrik: Four times a Leader and four times furthest in vision
For the 4th consecutive time, Rubrik has been named a Leader and the furthest in vision in the 2023 Gartner® Magic Quadrant™ for Enterprise Backup and Recovery Software Solutions.
Why Rubrik
With Rubrik Security Cloud, you can automatically protect data from cyberattacks, continuously monitor data risks, and quickly recover data and applications.
Data Protection
Secure your data with air-gapped, immutable, and access-controlled backups.
Data Threat Analytics
Continuously monitor for data threats, including ransomware and indicators of compromise.
Data Security Posture
Identify and monitor sensitive data exposure with intelligent risk monitoring.
Cyber Recovery
Improve cyber readiness by easily testing and orchestrating recovery workflows.
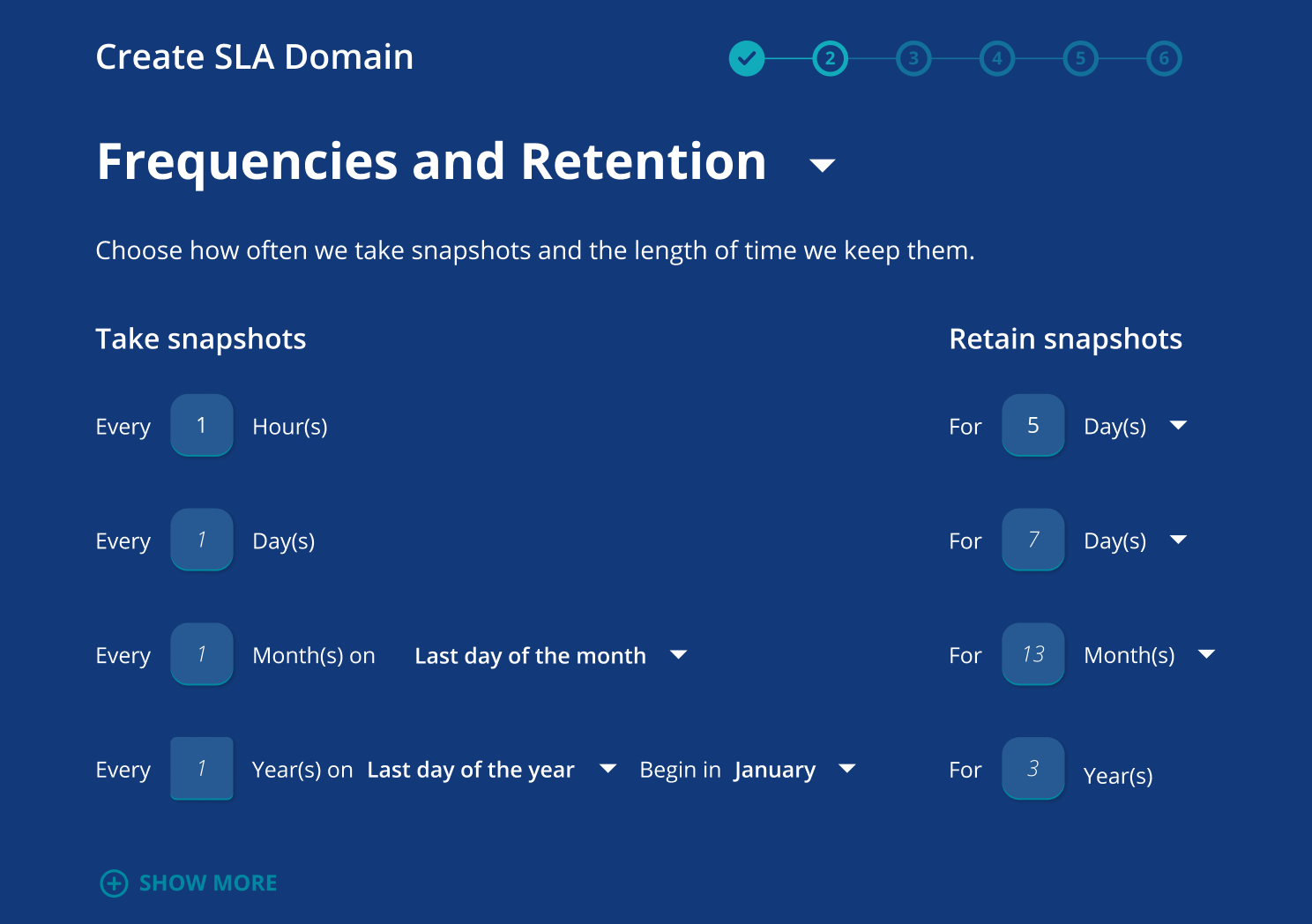
Safeguard data with secure backups
Protect your data from insider threats or ransomware with air-gapped, immutable, access-controlled backups.
Unstructured Data Protection
Protect, monitor, and rapidly recover against cyberattacks at petabyte-scale.
Mass Recovery
Restore business operations quickly by recovering apps, files, or objects at scale.
Monitor data risk and investigate faster
Continuously monitor risks to your data, including ransomware, data destruction, and indicators of compromise.
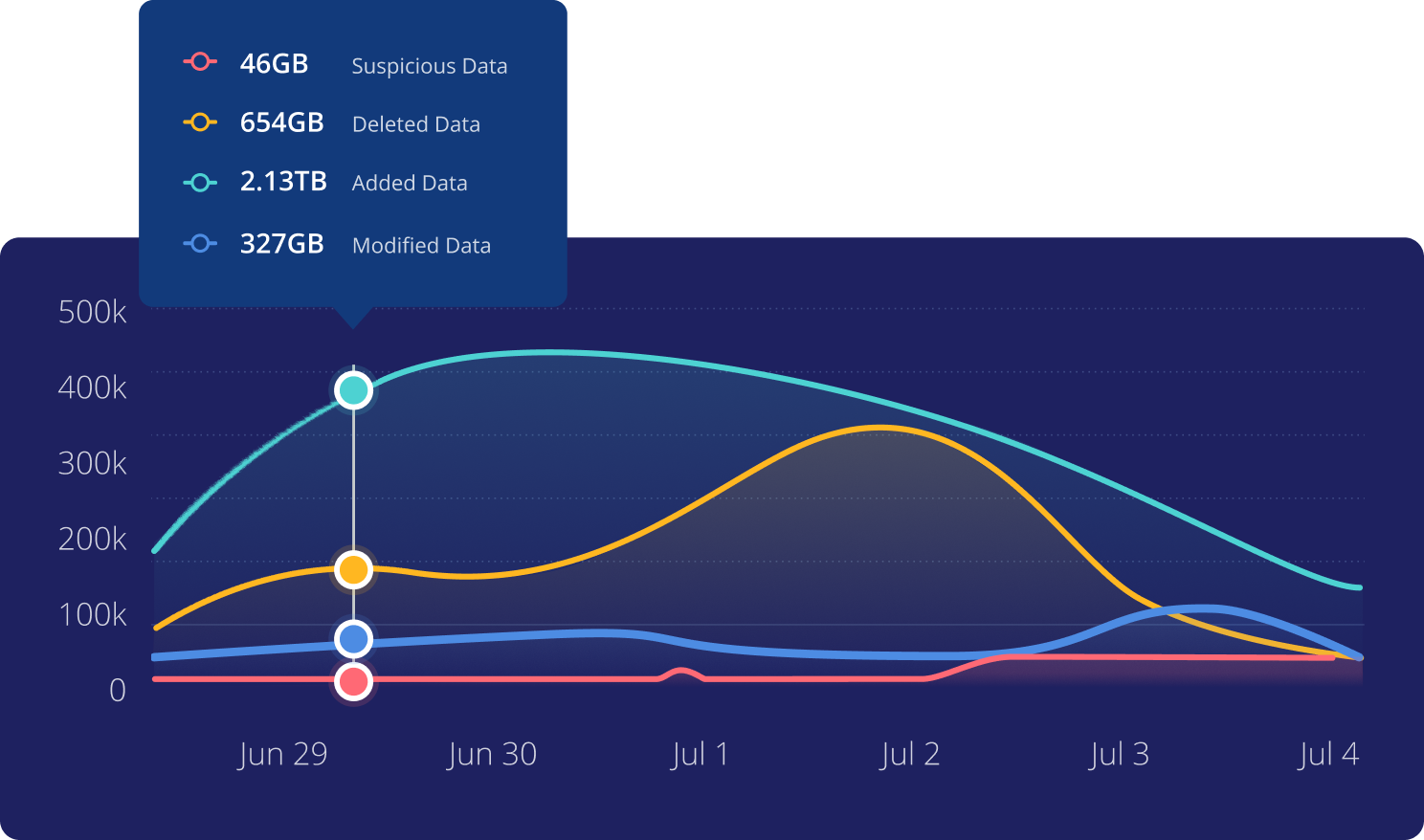
Anomaly Detection
Determine the scope of cyberattacks using machine learning to detect deletions, modifications, and encryptions.
Threat Monitoring
Detect threats early by automatically identifying indicators of compromise within backups using an up-to-date feed of threat intelligence.
Threat Hunting
Prevent malware reinfection by analyzing the time-series history of data for indicators of compromise to identify the initial point, scope, and time of infection.
Proactively reduce data exposure risk
Identify and monitor sensitive data exposure and use intelligent risk insights to maximize data security posture.
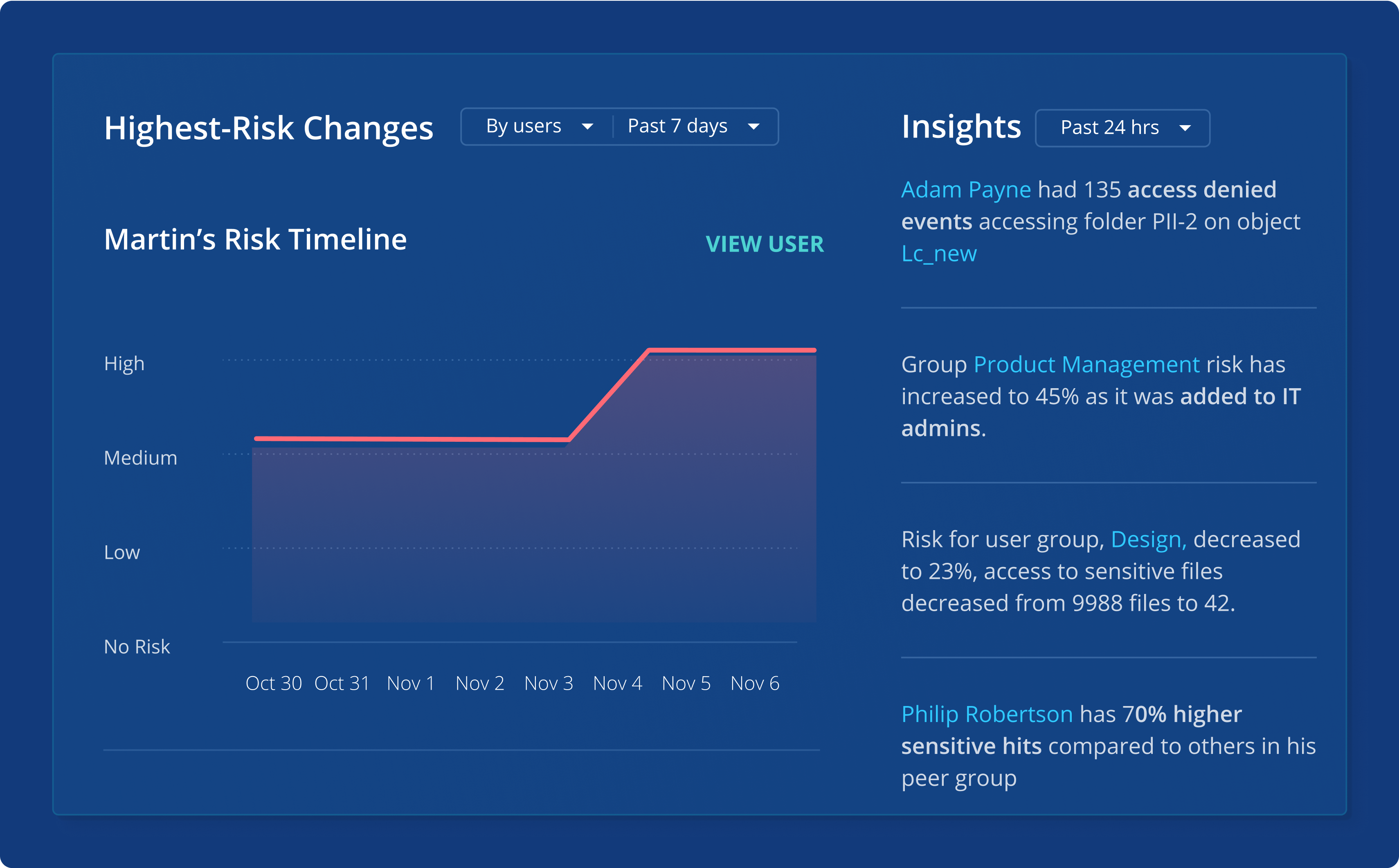
User Intelligence
Reduce data exposure risk by identifying and limiting who has access to sensitive data.
Sensitive Data Monitoring
Reduce sensitive data exposure and manage exfiltration risk by discovering what types of sensitive data you have and where it lives.
Data Security Command Center
Identify security gaps, quantify data risk, and provide actionable recommendations to improve data security posture.
Restore business operations faster
Improve cyber readiness by easily testing and orchestrating recovery workflows while reducing the risk of reinfection.
Threat Containment
Ensure safe and quick data recovery by quarantining data infected with malware.
Cyber Recovery Simulation
Improve cyber readiness and incident response by easily creating, testing, and validating cyber recovery workflows.
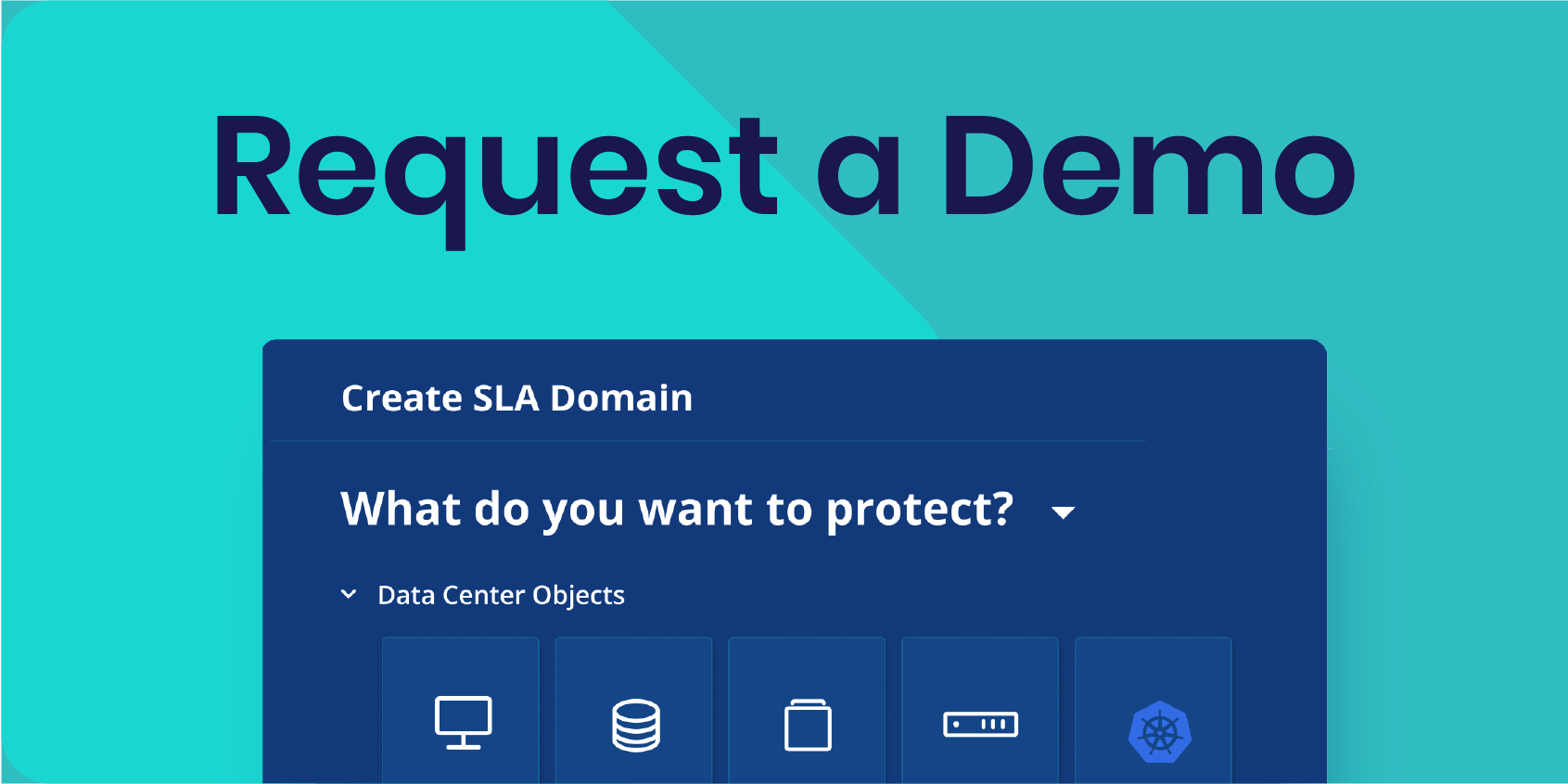
Ready to get started?
Get a personalized demo of the Rubrik Zero Trust Data Security platform.