Rubrik’s technology leader for Australia and New Zealand, Dale Heath, has said many local organizations still have an operational resilience mindset and are relying on systems not designed for cyber resilience when ransomware attackers breach perimeter defenses.
Local IT teams can take the advantage by adopting a zero-trust approach, improving communication between ITOps and SecOps teams and decreasing unknowns by testing ransomware scenarios, in addition to prioritizing rapid data backup recovery, he said.
Jump to:
- Ransomware attacks demand urgent ‘assume-breach’ shift
- Rapid data recovery could save organizations millions
- Three problems in current approaches to cybersecurity
- Unknowns could be the enemy in attack preparedness
Ransomware attacks demand urgent ‘assume-breach’ shift
Cybercrime was expected, according to the World Economic Forum, to cost global companies US $5.2 trillion (AU $8.8 trillion) between 2019 and 2023, a figure higher than the world’s third-largest economy. Further, ransomware attacks are expected to happen every two seconds by the year 2031.
A number of Australian organizations have been high profile victims. One example is the attack on law firm HWL Ebsworth in 2023 by the Russia-linked ALPHV/BlackCat ransomware group. In this attack, a total of 65 Australian government departments and agencies were impacted.
Rubrik sees global customers hit by ransomware on a daily basis. Three of its over 100 Australian customers have been involved in ransomware attacks just in recent months.
“Investing in perimeter security is still essential to organizations for cyber resilience and cyber security,” said Heath. “But protecting applications, networks and perimeter security is not enough. And the reason is perimeter defenses are getting breached. Bad actors are getting in.”
PREMIUM: Download our comprehensive resource and data recovery policy.
Data backups being targeted in cyberattacks
Heath said a change in approach was required. While in the past organizations had focused on building the defenses required to keep cybercriminals out, the best hope of safeguarding data in the current risk-prone environment was to adopt zero-trust principles to defend data.
“An assume-breach mindset is now absolutely essential,” Heath said. “They are going to get in, and they are going to go after and get access to data. They will go after your data backups, which is your last line of defense, and then they will execute a ransomware attack.”
Whether cybercriminals gain access through a misconfigured firewall, a zero day exploit, compromised user credentials or a third-party software vendor, Heath said they are getting in, and when they do, they are going after sensitive data — including data backups.
In The State of Data Security: The Hard Truths, Rubrik’s Zero Labs cybersecurity research unit found 99% of organizations reported malicious actors attempting to impact data backups during a cyberattack. In addition, 74% said that these attempts were at least partially successful.
Paying a ransom no guarantee of data recovery
Rubrik’s research showed 64% of Australian IT and security leaders would likely pay a ransom to recover their data after a cyberattack. The main reason driving this was they would otherwise have no way to access their data. However only 14% of Australian organizations that paid attackers for decryption tools after a ransomware attack were able to recover all their data.
Rapid data recovery could save organizations millions
To avoid detection, ransomware attackers are moving faster. Data shows median dwell times of ransomware attackers between breach and detection have plummeted in recent years, with some estimates as low as five days during the first half of 2023. Meanwhile, the average downtime after a ransomware attack was at 24 days according to Statista (Figure A).
Figure A
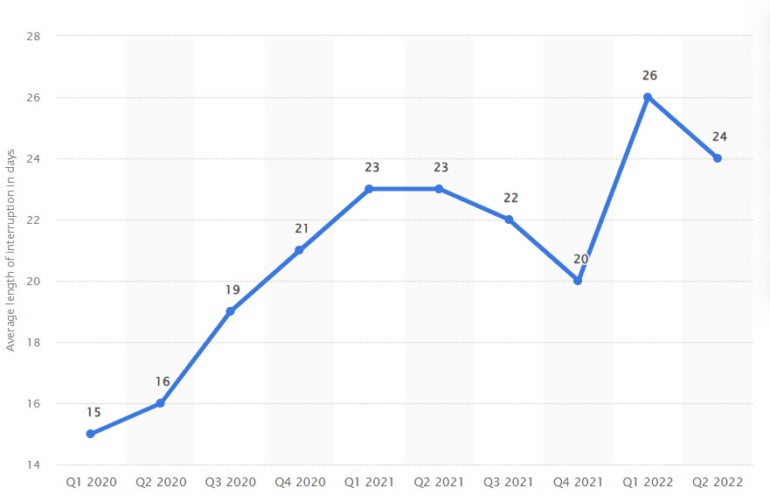
Heath argues organizations should focus on achieving rapid recovery after a ransomware or cyberattack event. Rather than looking at a recovery timeframe in the days, weeks or even months, he said organizations can now potentially be up and running again in hours.
SEE: Review our selection of the 8 best data recovery software systems for 2023
“These attacks are happening all the time now, and organizations are struggling to recover,” Heath said. “Operationally, they are able to recover, but in terms of cyber recovery, it can be weeks or sometimes months, and it can end up costing them millions of dollars.”
Langs Building Supplies avoided paying $15 million in bitcoin
Heath said Rubrik aims to safeguard a “bullet-proof” backup of an organization’s data. It combines this with the ability to observe and assess the scope and impact of an attack in real time, and get customers back up and running within hours without reinfecting the environment.
He mentions Langs Building Supplies as an example. It used Rubrik to survive a 2021 attack affecting hundreds of thousands of files. It was able to be fully back up and running within 24 hours without losing any data and without paying the $15 million bitcoin ransom demand.
Three problems in current approaches to cybersecurity
In addition to a continued traditional focus on boosting perimeter defenses, organizations are currently facing a number of key challenges in their approach to cybersecurity.
Systems have been designed for operational resilience
Organizations in the past have focused on operational recovery or disaster recovery rather than recovery from a cyber event. The systems haven’t been designed to recover and shorten the recovery process length or to do so without reinfecting the IT environment again.
Communication between ITOps and SecOps teams
Collaboration between ITOps and SecOps could be more streamlined, including through tech automation.
“There still seems to be a bit of a gap in communication,” said Heath. “ITOps have their role and so do SecOps, and while collaboration is getting better, it is not where it should be.”
Testing and readiness for a cyber or ransomware attack
Organizations aren’t as prepared as they could be for an attack because of lack of testing, meaning they don’t know how long it would take them to get back up and running.
“They are struggling to automate and test that and be able to say with absolute certainty when they will have critical workloads back into production after being hit with a cyber security event,” said Heath.
Unknowns could be the enemy in attack preparedness
Boards only want to know the answer to two questions in the event of an attack, Heath said. The first is what the extent of the data compromise or impact actually is, and the second is how long it will be until the organization is able to get back up and running.
Being able to demonstrate how an organization will manage and recover from an attack through testing — as well as a clear indication of how long that will take — can dispel the unknowns in the equation for boards and for the IT leaders safeguarding organizational data.
Heath recommends IT leaders think about how they would respond to a ransomware attack if one happened today. He also suggests acquiring the ability to increase the frequency of testing, even to the point of testing weekly, rather than every three, six or 12 months.
“If your ability to recover after an attack is unknown, that unknown could end up blowing out to days, weeks or even months,” Heath said. “We have seen some organizations still months down the line, still struggling to recover and to bounce back from an attack.”
