There has been no shortage of ransomware headlines in 2021. While these attacks can shut down critical IT systems for extended periods, Rubrik has helped numerous customers quickly recover from ransomware events and get their businesses back up and running.
This blog consists of two important sections. First, we’ll detail the multiple recovery options available with Rubrik Zero Trust Data Security™️. Then we will explore different variations of ransomware attacks and guide the best recovery strategies for individual incidents.
The Basics
Yuba County and the City of Durham are two organizations that have taken advantage of Rubrik Zero Trust Data Security architecture and immutable file system, ensuring that clean, uninfected copies of their data were recovered. In working with organizations all around the world on recovering from ransomware, Rubrik has developed a comprehensive Lessons Learned document outlining how to execute an effective ransomware remediation strategy.
The first step in recovering from an attack is to identify and isolate the incident, followed by determining the scope of infection. Rubrik Radar helps to detect data anomalies, and Sonar helps to identify if certain sensitive data has been affected by the attack. Once initial scoping has been determined, only then can we begin to execute the restore phase of our plan.
Rubrik provides multiple recovery options, from orchestrated mass restore with AppFlows to file-level recovery. Depending on the scope and type of attack, certain recovery techniques can outperform others in terms of speed and efficiency, helping you meet Recovery Time Objectives (RTOs).
For instance, if the ransomware attack has only targeted certain files and left the underlying operating system unaffected, performing a file-level recovery may be less intrusive and help mitigate data loss compared to a full system restore. In contrast, if data loss is not a major issue, it may be faster to utilize Rubrik Instant Recovery to almost instantaneously restore to a certain point-in-time. And in most cases, mixing different recovery options throughout your remediation plan may be called for.
What are the Rubrik Recovery Options?
Rubrik provides several recovery options:
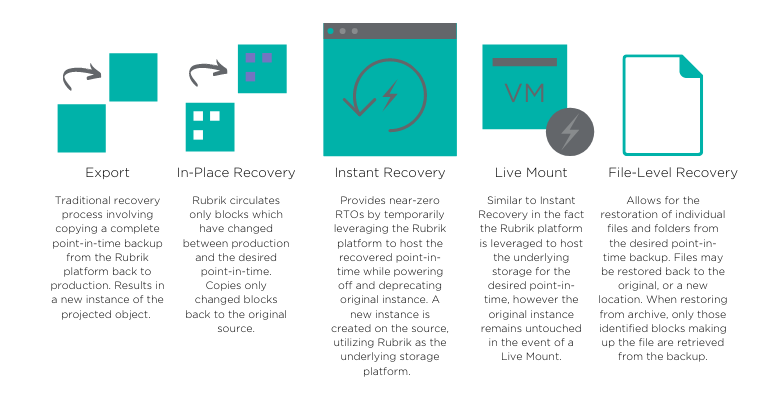
Export
Export copies a point-in-time backup from the Rubrik platform to a new instance of the protected object. Rubrik operators can choose to export data back to the original environment, or export to a completely new environment.
In-Place Recovery
In-Place Recovery is supported for VMware VMs and, similar to Export, copies point-in-time data from the Rubrik platform to the production environment. There are, however, a few key differentiators between the two recovery methods.
Export copies entire virtual machines or disks belonging to virtual machines and recovers these to new instances. Rather than copying entire data sets, In-Place Recovery copies only changed blocks between the production VM and the selected point-in-time and recovers data back to the original virtual machine. This allows for a more efficient recovery, especially for VMs containing larger virtual disks.
Instant Recovery
Rather than copying entire datasets across the network, Instant Recovery utilizes the Rubrik platform as the underlying storage for the recovery to provide near-zero RTOs. In the case of VMs, the Rubrik platform becomes a datastore, while a new copy of the protected VM is created and mounted utilizing the desired point-in-time backup files. The original VM is marked as deprecated and powered off. No production data is deleted from the original datastore. This allows for almost instantaneous recovery and enables IT and security teams to grant access to the workloads as fast as the underlying operating system can boot. The newly recovered VM can be migrated back to the production storage platform.
Live Mount
Live Mount is essentially the same technology with the same processes as Instant Recovery except for one step. When Live Mounting a VM or database, the source of the data is not deprecated. This means that your production environment is completely unaffected - no VMs are powered off. Because of this, IT teams often use Live Mount as a sandbox tool, providing access to point-in-time copies of their production environment to perform various tasks, beyond simple recoveries.
File-Level Recovery
Rubrik File-Level Recovery (FLR) is straightforward: a point-in-time copy of single (or multiple) files is restored either back to the original, or a new location within the same environment. Rubrik provides important FLR capabilities to make the process as efficient as possible.
First, Rubrik generates metadata describing ingested backups. This metadata powers fast and predictive search to assist in locating files that need to be recovered. Second, when performing an FLR from a backup that has been archived to the cloud, this metadata allows Rubrik to only retrieve the blocks making up the actual desired file, rather than having to endure unnecessary and expensive egress charges by extracting entire images from cloud storage.
AppFlows for Orchestrated DR
AppFlows is an orchestration layer that incorporates plans, or blueprints, detailing recovery execution steps. These customer-defined blueprints contain important recovery information such as the boot sequence, restart priority, and requisite resource mapping configurations. All of this intelligence allows IT teams to automate application failover and failback of production resources in the event of a ransomware attack. AppFlows takes ransomware remediation plans and automates the recovery process. This minimizes the chance of error or misconfiguration, but more importantly, reduces application downtime.
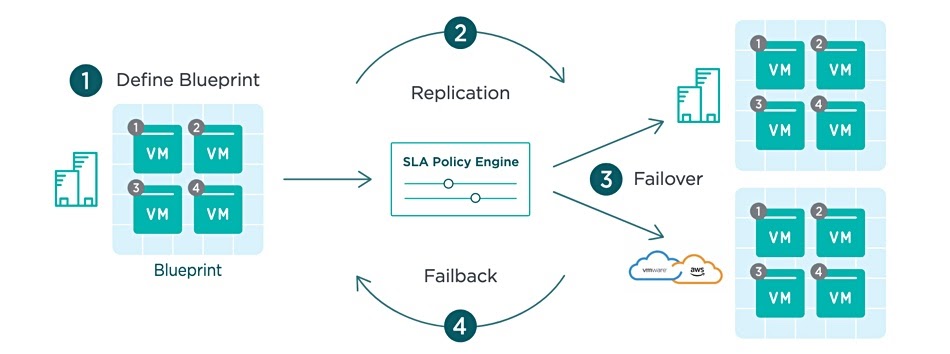
In the event of a ransomware attack, AppFlows orchestrates recovery to various sandbox environments, allowing infosec teams to investigate exact duplicates of production environments, without affecting production resources.
With multiple recovery options available to IT teams, it is important to understand which method to employ during a ransomware incident. To help understand and plan for recovery, let’s explore some of the more popular types of ransomware attacks and apply our Rubrik recovery methods to them.
Types of Ransomware Attacks
As with most attacks, ransomware has multiple variants. Commonly, these attacks often target different areas of the network, lying dormant while gathering data. Below are some of the approaches used today.
Encryption Ransomware
Encryption Ransomware is one of the most popular attack types today. It encrypts files, folders, and NAS shares throughout the network, effectively deleting the production data once the encryption takes place.
Recovery involves identifying infected files and systems and then restoring them to a safe point. Depending on the scope of the attack, many Rubrik recovery options can be used to combat Encryption Ransomware. For instance, if the underlying operating system is unaffected, performing a file-level recovery back to the system would suffice. If the underlying operating system is corrupted or encrypted, performing an Instant Recovery or Live Mount to a known good copy can be the best course of action. If the attack targeted a large number of virtual machines, leveraging Rubrik AppFlows can provide highly efficient recovery.
NAS Ransomware
NAS Ransomware works much the same way as Encryption Ransomware, but specializes in attacking Network Attached Storage (NAS) systems. By scanning the network for popular NAS-based protocols such as NFS and SMB, the attack identifies and encrypts all discovered shares. Often NAS systems hold crucial data such as user home directories, as well as VM files for major hypervisors. Simply put, NAS Ransomware can completely bring entire production systems to a halt.
Recovery involves identifying all the infected files and systems and restoring both image and file-level to safe point-in-time copies. Depending on the scope of the attack, several Rubrik recovery methods may be utilized. If only a small number of files have been affected, then Rubik NAS File Level Recovery options can be used. However, if the NAS device was also hosting infected virtual machines, a combination of the Export, In-Place Recovery, Instant Recovery and Live Mount can be utilized. And, just as with Encryption Ransomware, AppFlows can be utilized to orchestrate the entire recovery process.
Lock Screen Ransomware
Lock Screen Ransomware does what one might expect it to do - it locks the system's screen, demanding different forms of payment to perform an unlock. This type of ransomware rarely performs any encryption to the underlying files within the affected system and is often easily recoverable through the combination of booting into safe mode and running anti-virus recovery tools.
Most often recovery from Lock Screen Ransomware does not need to utilize Rubrik, however, to save time and recover faster, organizations may utilize Rubrik’s various image level recovery options.
Hardware Locker
Hardware Locker ransomware affects the system by changing the underlying Master Boot Record (MBR). Instead of the MBR directing the system to load the underlying operating system, a ransom demand is displayed on the screen during the boot cycle.
Recovery typically involves fixing the modified MBR. If the MBR is unable to be repaired, or organizations are simply looking to decrease the amount of downtime, recovery teams may leverage image-level recovery options from Rubrik such as Bare Metal Restore for physical servers, or Export, Instant Recovery, and Live Mount for virtual machines.
Application/Web Server Encryption
Application and Web Server Encryption encrypts files and web servers by replacing common Directory Index files such as index.php and index.html. Instead of a web or application server loading its desired content, a page containing ransom instructions is presented in its place.
Recovery typically involves identifying infected files and restoring them to a known good state. A variety of Rubrik recovery methods may be used to help remediate Application and Web Server encryption. While performing many of the Rubrik image-level recovery techniques such as Export and Instant Recovery will do the trick, often it is much faster to simply perform a file-level restore on the infected files themselves.
Conclusion
As ransomware attacks become more widespread and more sophisticated, organizations must have a recovery plan in place. Deploying a Zero Trust Data Security solution is a great first step to ensure your backups can serve as the last line of defense. Having an understanding of the various recovery options, and when to use each, is crucial in the event you need to execute your ransomware remediation plan.
To learn more about how you can accelerate ransomware recovery with Rubrik and avoid paying costly ransoms, visit our Ransomware Solutions page.

