Detect, Analyze and Respond to Ransomware Attacks Faster
Identify ransomware threats in real-time, detect the infection type, and map the impact—helping you respond and recover faster.
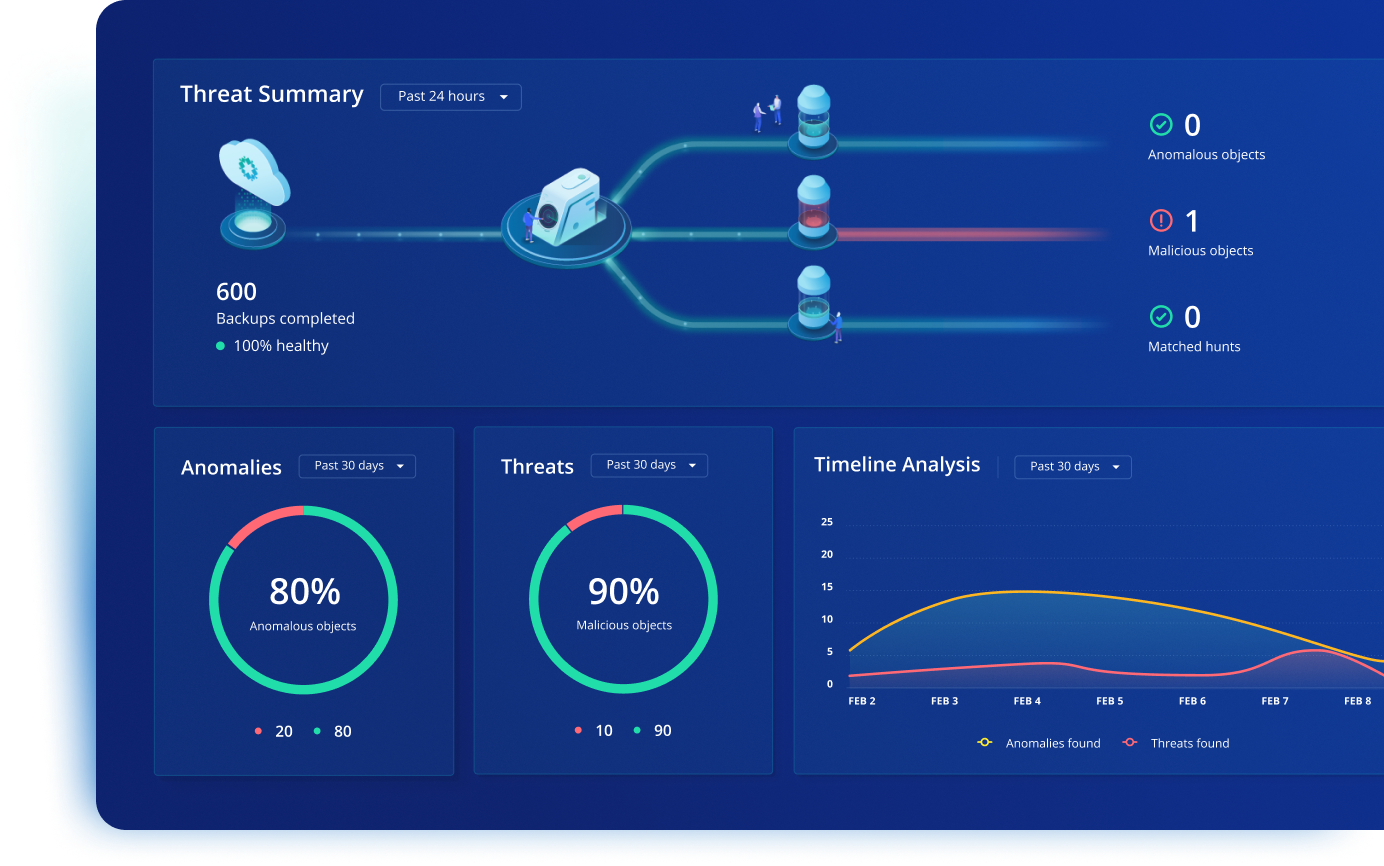
Get alerts for suspicious activity
Rubrik’s Anomaly Detection monitors for encryption, unusual access patterns, and other ransomware indicators—alerting you to threats in your backup data.


Identify the ransomware strain
Speed up incident response by using anomaly detection algorithms trained on a broad data set of known ransomware behaviors. These algorithms analyze specific data points such as encryption methods, registry changes, network traffic, and file modification patterns to pinpoint the ransomware strain. Early identification of the variant allows for a precise and effective response plan. Incorporating outlier detection also minimizes the risk of overlooking novel variants or tactics, though care must be taken to validate findings and reduce false positives, which could otherwise mislead the investigation.
Assess the impact of an attack
Rapidly assess affected systems by applying comprehensive data analysis across the network. Sophisticated outlier detection techniques identify abnormal access patterns and modifications by comparing current activity against a baseline data set of normal operations. This helps isolate compromised files and applications efficiently. While some data anomalies may be benign, accurate tuning of algorithms helps distinguish true threats from false positives so your recovery efforts remain focused and effective.

Trusted by more than 6,000 leading organizations

“Anomaly Detection will help us protect our bottom line and potentially save us millions of euros in case of an attack. If we did not have Anomaly Detection, we would not have been approved for a cyber insurance contract.”
–Fabrice De Biasio, CIO, ASL Airlines France

Explore more of our resources


Demo
Intro to Rubrik Security Cloud
Take a self-guided demo to explore our data security platform that protects, monitors, and quickly recovers your data.