ビジネスをオンラインへ復旧
災害やランサムウェア攻撃が発生した場合には、簡単で拡張性のある完全な復旧方法により、損害の大きいビジネスの中断を回避することができます。
ビジネスの目標復旧時間を満たすデータとアプリケーションを安全に復元することにより、ビジネスの継続性が保証されます。
最小限のダウンタイム
信頼性のある復元
柔軟な運用
Gartner® Magic Quadrant™のエンタープライズ向けバックアップ/データ保護プラットフォーム部門
エンタープライズ向けバックアップ/データ保護市場の詳細な分析と、Rubrikが6年連続で最も右側に位置するリーダーに選出された理由について、ガートナー社の2025年のマジック・クアドラントレポートをお読みください。

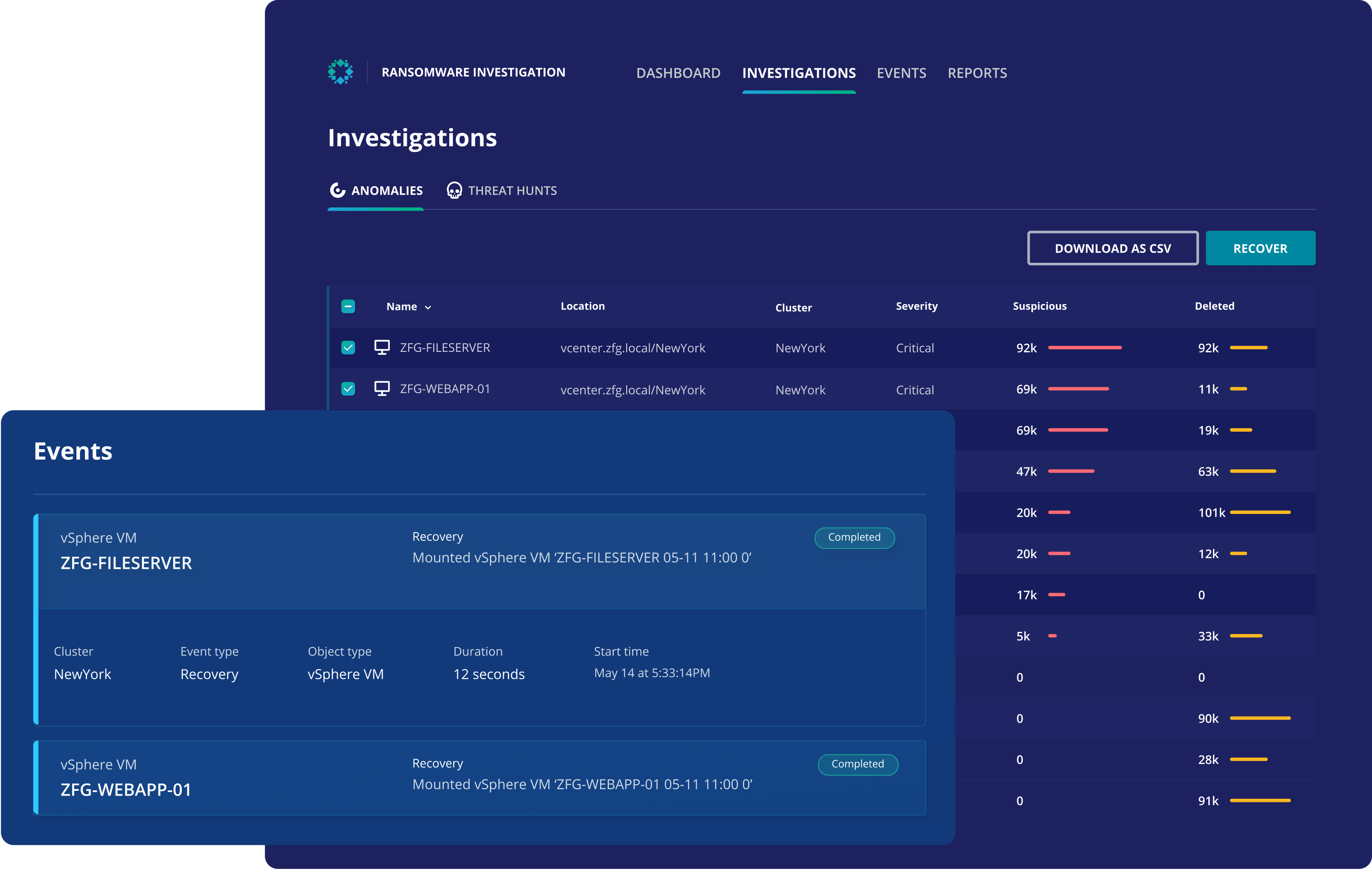
提案されたスナップショットへの復元
復旧ポイントを探す必要はありません。ランサムウェアの攻撃が発生した場合には、機械学習によって提案された最新のクリーンなスナップショットからすべてのデータが復元されます。
特定の人に依存したり、専門スキルを必要としたりせずにスムーズに一括復元することができます。

クリーンなスナップショットを簡単に特定
異常な挙動や暗号化の兆候を示すスナップショットを分析して、最新の適切なコピーを選択できます。
ランサムウェアの調査では、システムが感染した時点、場所、経路についての情報が提供され、データを安全に復元できます。
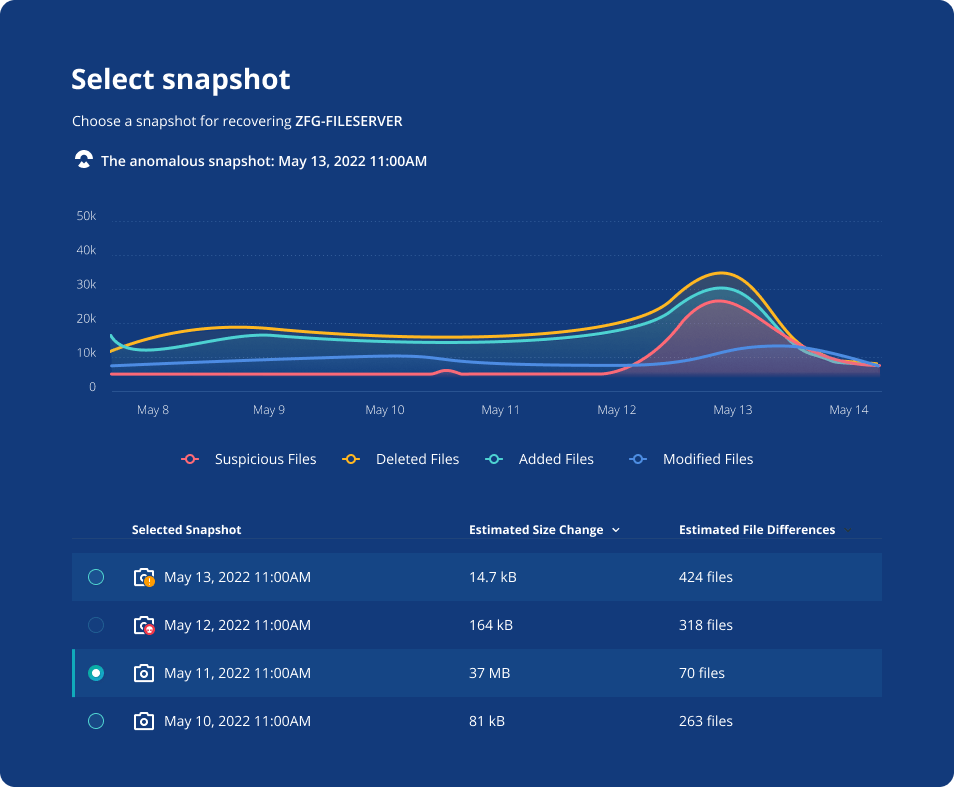
柔軟な復旧
復旧方法を選択可能
ダウンタイムほぼゼロでビジネス運営を復旧させるには、必要な対象だけを復元できる柔軟性だけでなく、一括復元も必要です。 攻撃の範囲と影響によっては、特定の復旧方法の方がスピードと効率の点で効果が高く、ビジネスのRTOを満たすうえで有効です。
正確なランサムウェア復旧
瞬時のアプリケーション復元
ストレージ停止の復旧
プロアクティブな復旧テスト
サイトの自動復元
Rubrikでランサムウェア攻撃への対策と復旧
この資料はRubrikのZero Trust Data Securityについて紹介し、保護されたデータがランサムウェア攻撃によってどのように書き換えを阻止しているのかという仕組みについて解説しています。その他にも、サイバー犯罪者による攻撃を回避するためのベストプラクティスについてもご紹介します。


whitepaper | eブック
バックアップ&リカバリーベストプラクティス
このeブックを活用することにより、従来とは異なるアプリやリモートワークの増加そして新しく生まれてくるランサムウェアの脅威に備えることができます。

blogpost | 0 min read
Rubrikでさまざまな種類のランサムウェア攻撃から復旧
2021年、連日のようにランサムウェア関連のニュースが世間を賑わせました。ランサムウェア攻撃は基幹ITシステムを長時間にわたって停止させることもありますが、Rubrikはこのような事態から迅速な復旧をするためのサポートをし、ビジネスを正常化するための支援を多数のお客様に提供してきました。