Encrypting your data has moved from being a “nice-to-have” to a mandatory procedure when creating or storing data on-premises or in the cloud. Cloud providers have generally taken the lead in making encryption a simple-to-use service on their platform. One example is Amazon Web Services (AWS), who offers users the ability to encrypt data in transit and at rest with many of their services, including Amazon Simple Storage Service (S3), Amazon Elastic File Service (EFS), and Amazon Elastic Block Storage (EBS).
Rubrik has integrated with AWS encryption services from its inception, beginning with Amazon S3 and Rubrik CloudOut, and now including Amazon EBS snapshots. This integration provides not only the ability to encrypt data that Rubrik manages in AWS, but also key management through the AWS Key Management Service (KMS) and customer-deployed key management systems. These integrations give our joint customers the flexibility to control their encryption keys seamlessly while using Rubrik for data management in AWS.
I’ve been writing about how Rubrik helps customer with protecting their Amazon Elastic Compute Cloud (EC2) instances using Amazon EBS and Amazon Machine Images (AMI). The earlier blog posts in this series can be found here:
In this post, I’ll walk through how to configure AWS KMS to enable EBS encryption and how Rubrik handles various encrypted volume options.
Introduction to Amazon EBS Encryption
Amazon EBS encryption leverages envelope encryption, a method in which data is encrypted using a data key and individual data keys are encrypted using a customer master key (CMK).
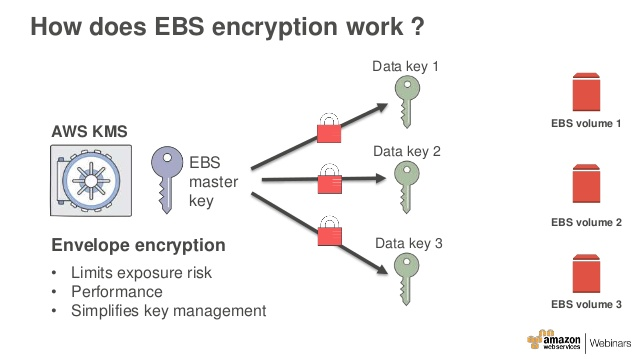
The CMK is stored and managed by KMS, which gives users the ability to rotate their CMK on a pre-defined schedule or on-demand. Users can also effectively “shred” their data by deleting the CMK, which renders data on their EBS volumes unreadable.
Another benefit of EBS encryption is its tight integration with the AWS Identity and Management (IAM) service. Users can choose to encrypt their volumes using a default EBS CMK that is created automatically when a user chooses to have AWS create a key for them. Users can also choose to create their own CMK using the KMS console for encrypting EBS volumes. This gives users more flexibility when managing their CMKs, including the ability to grant a specific user or application, such as Rubrik, permission to encrypt EBS snapshots.
Configuring Amazon EBS Encryption
All the work involved in giving Rubrik permission to use KMS to encrypt snapshots is done on the AWS side. We’ll use the AWS KMS console to walk through the steps:
Creating an AWS KMS CMK
1. Log into the KMS console as an IAM user with permission to administer KMS. Confirm that you are in the Region where you want to create the CMK. Note that a CMK is scoped to the Region it’s created in and can only be used to encrypt volumes in that Region.
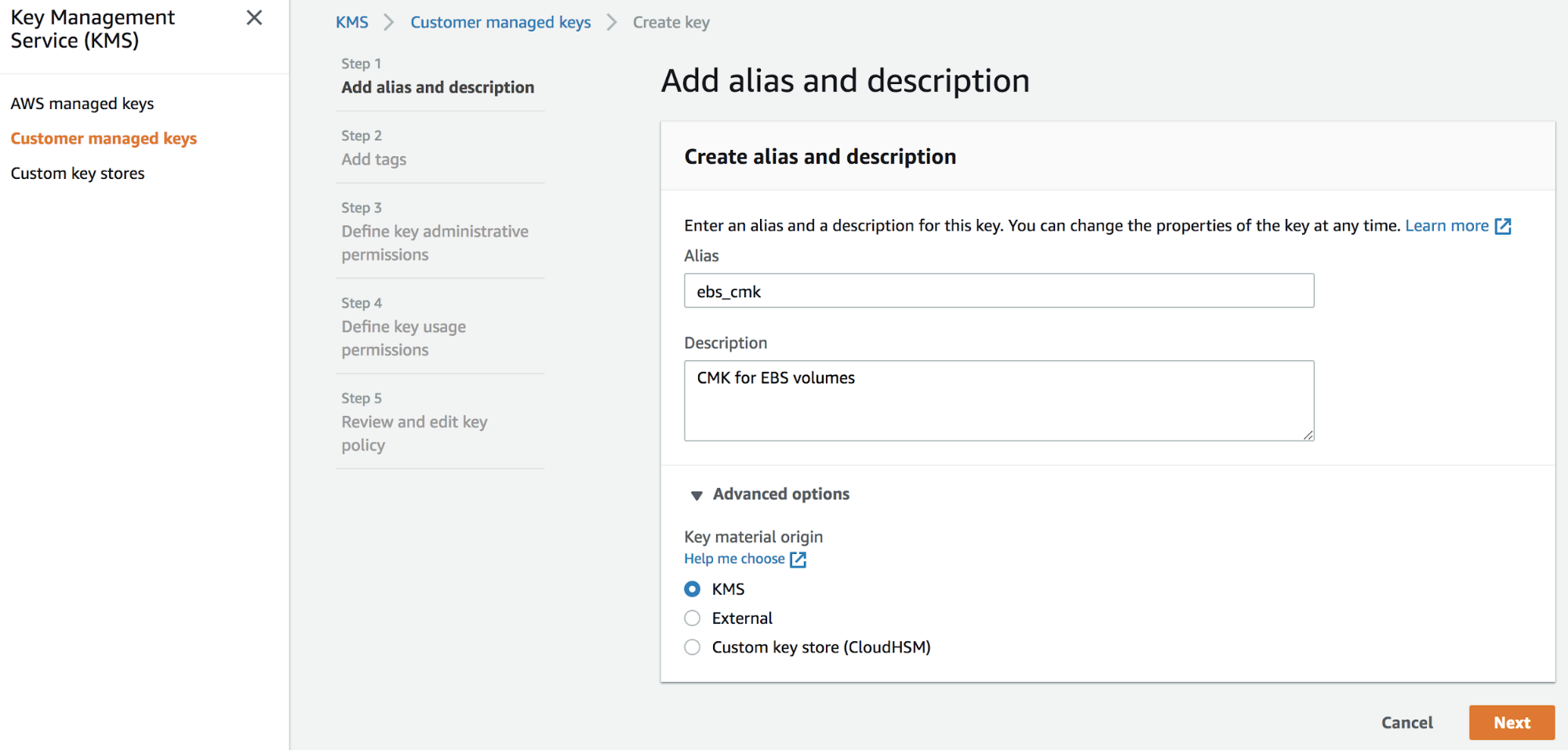
2. Navigate to the Customer managed key page and click on Create key to launch the wizard. This brings up the Add Alias and Description page. Create an alias and description for the master key. Expand the Advanced Options section and confirm that KMS has been selected as the Key material Origin.
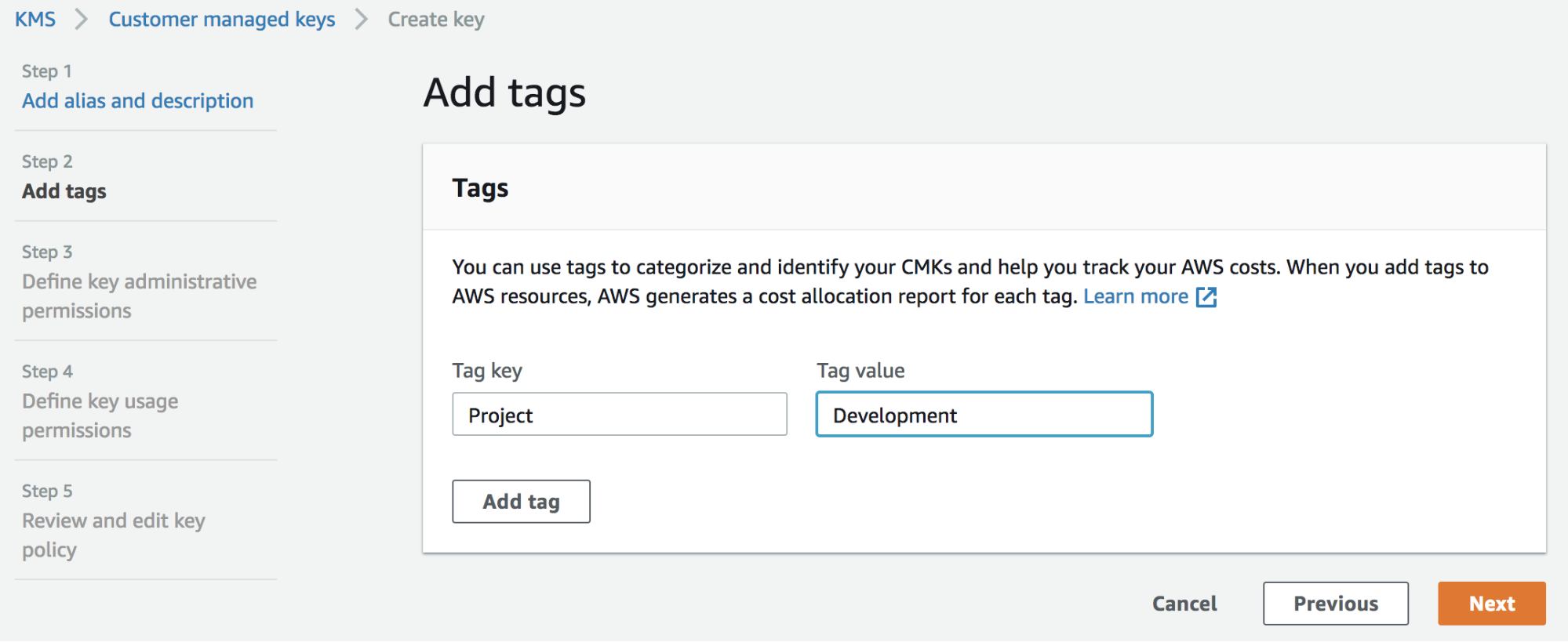
3. An optional Tag can be added but is not required.
4. This brings up the Define key administrative permissions page. It defines which IAM users can perform key management functions on the master key, including key deletions. Choose one or more valid IAM users.
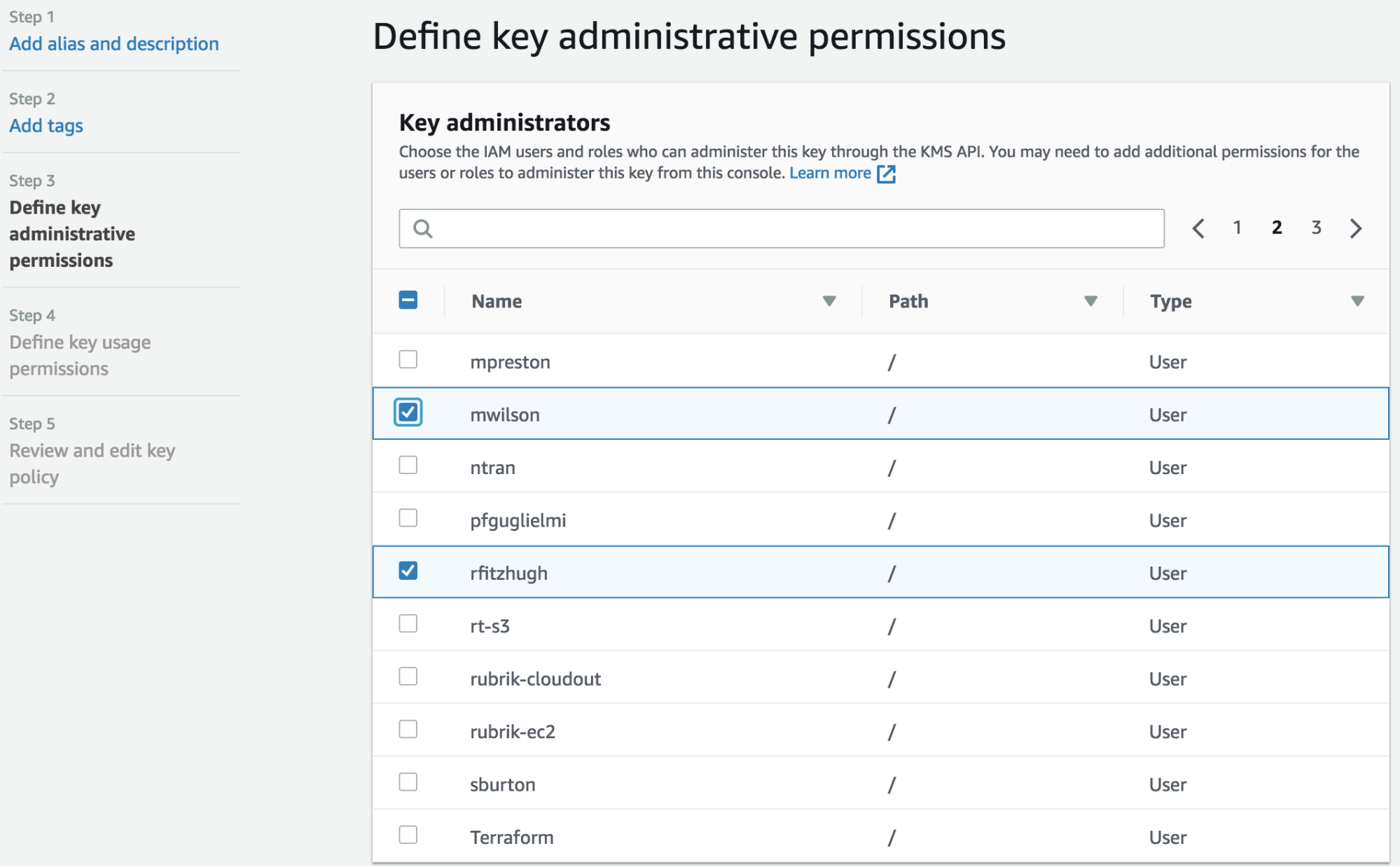
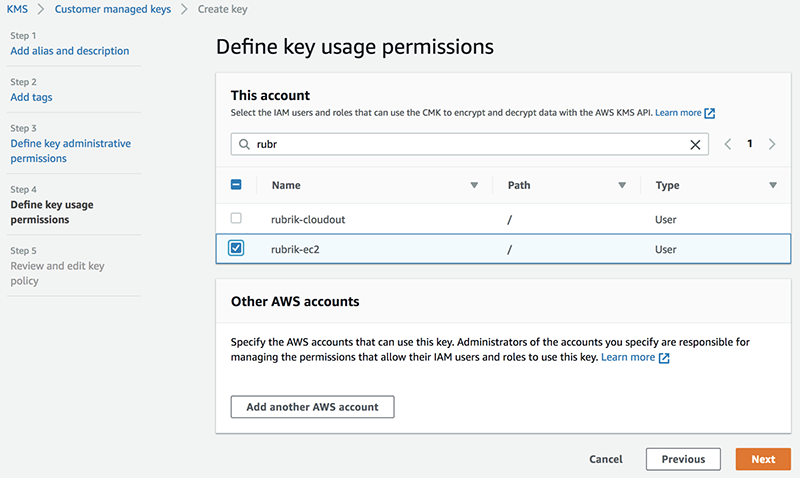
5. This brings up the Define key usage permissions page. It defines which IAM users will be able to use the master key to encrypt and decrypt EBS volumes. Choose the Rubrik IAM user that was created to manage EBS snapshots.
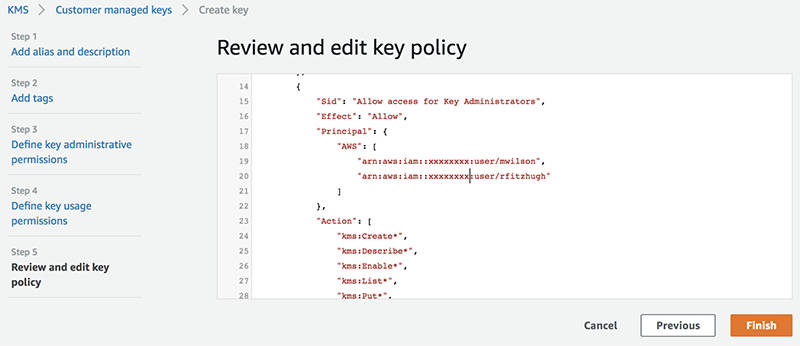
6. This brings up the Review and edit key policy page. Review the json-based policy file to confirm the key policy has been configured correctly, and then click Finish.
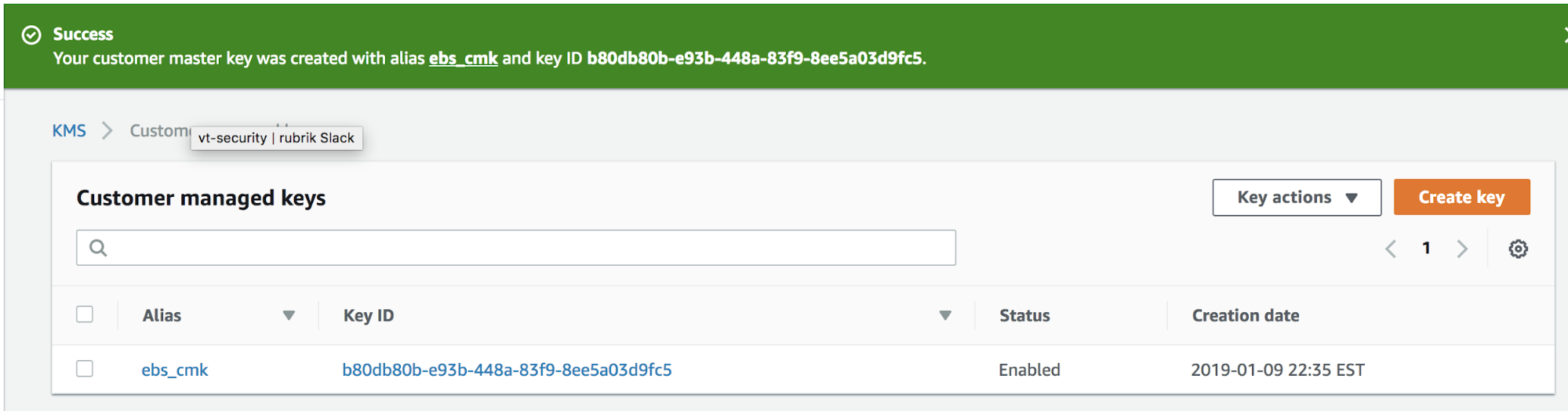
7. The newly created key will appear in the KMS console. Make note of the Key ID for the newly created CMK. The key ID is a unique identifier that allows the master key to be used without having to export the actual key material. The key ID stays constant for the life of the key so that the underlying key material can be rotated without the key ID having to be changed every time.
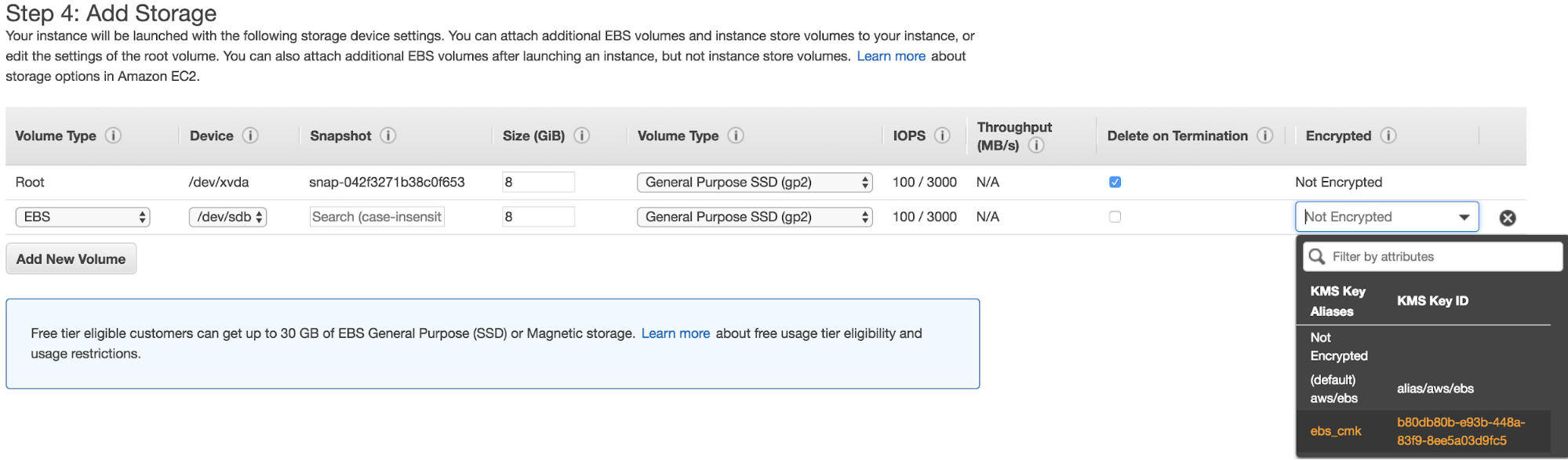
8. To encrypt an EBS volume with the new CMK, walk through the usual steps to launch a new instance. Click the Add Storage button to create a new volume and select the dropdown menu under the Encrypted column. Note that you may see the (default) aws/ebs key if you’ve previously created an EBS volume in this Region. Select the CMK created earlier to encrypt this volume with our CMK.
Managing Encrypted Snapshots with Rubrik
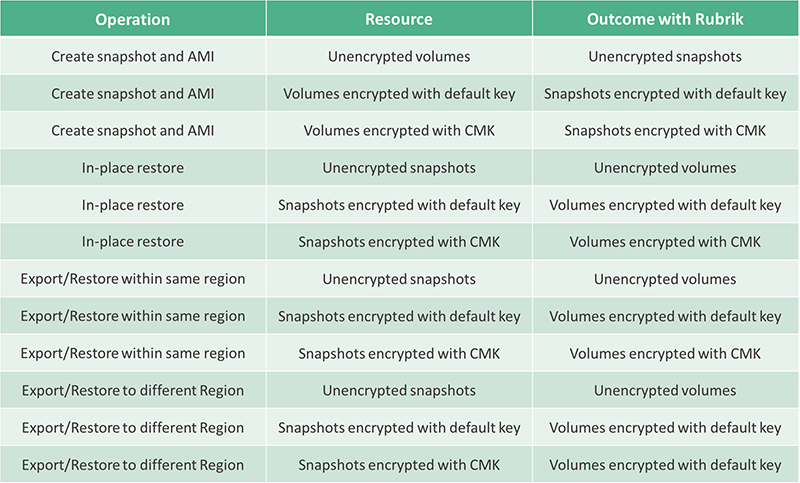
Nothing special has to be done to encrypt an EBS snapshot. Snapshots taken from encrypted volumes are automatically encrypted. Snapshots taken of volumes encrypted using a CMK will automatically be encrypted using the same CMK.
Volumes that are created from encrypted snapshots are also automatically encrypted. This means all restores performed using Rubrik will create new encrypted volumes as part of the restore of an existing instance or launch a new instance. For restores within the same Region, new volumes will be encrypted using the CMK that was used to encrypt the original EBS volume and its snapshot. For restores to a different Region, new volumes will be encrypted using the default CMK for that Region.
The table belows outlines the encryption behavior related to protecting and restoring EC2 instances with Rubrik. Please note the following:
- An in-place restore denotes restoring a volume to the original source instance.
- An export/restore within the same Region creates a new instance using the new volume created from a snapshot. The instance can be created in any AZ within the same Region as the original source instance.
- An export/restore to a different Region creates a new instance using a new volume created from a snapshot. The instance can be created in any AZ in a different Region from the original source instance.
Encrypting your EBS volumes is a critical component of any cloud security strategy. Customers who rely on Rubrik to protect their EC2 instances and EBS volumes can be assured that their AWS workload is properly protected.
