Since January 2020, Microsoft Azure SQL DB has grown nearly 3x in popularity. This rapid growth comes as no surprise as Platform-as-a-service (PaaS) offerings have many benefits in the migration strategy from traditional SQL Server database workloads. The Microsoft PaaS offering, Azure SQL Database, takes care of mundane tasks once performed by Infrastructure Engineers such as patching operating systems and applying SQL Server updates or critical security patches.
However, even with the luxuries of the cloud experience, migrating to the cloud does not resolve the many challenges of data security. Data security is a concern because databases typically house critical and sensitive business data. If attackers take down that data or exfiltrate it, that could mean significant financial and brand impact. Because of this, IT needs to leverage systems that not only back up their critical data but secure it by ensuring the least privilege to backup data.
With the Rubrik winter release, data security capabilities now extend to Azure SQL PaaS solutions for Azure SQL Database and Azure SQL Managed Instance. For Rubrik customers, this means they can now protect their Azure SQL data with operational efficiency, automation, and governance of an SLA Domain Policy! On top of this, the inherent data security benefits of Rubrik also apply–such as granular role-based access control and multi-factor authentication.
Let’s dive into a few of the highlights of our new Azure SQL protection capabilities.
Centralized Data Protection for Azure SQL
SQL databases have proliferated in order to support the exploding amount of applications on which businesses run. But, ensuring critical business data housed in those databases is protected and secured is a huge challenge for IT organizations today. While Azure SQL offers benefits to day-to-day operations, businesses often need to deploy databases and applications across various Azure subscriptions creating additional infrastructure and data silos.
With Rubrik, a single SLA policy can span multiple Azure subscriptions and regions to unify the protection strategy across an enterprise Azure SQL deployment. Additionally, the same benefits of governance and monitoring a data protection strategy are gained by having a single interface to audit, report, and remediate encountered issues.
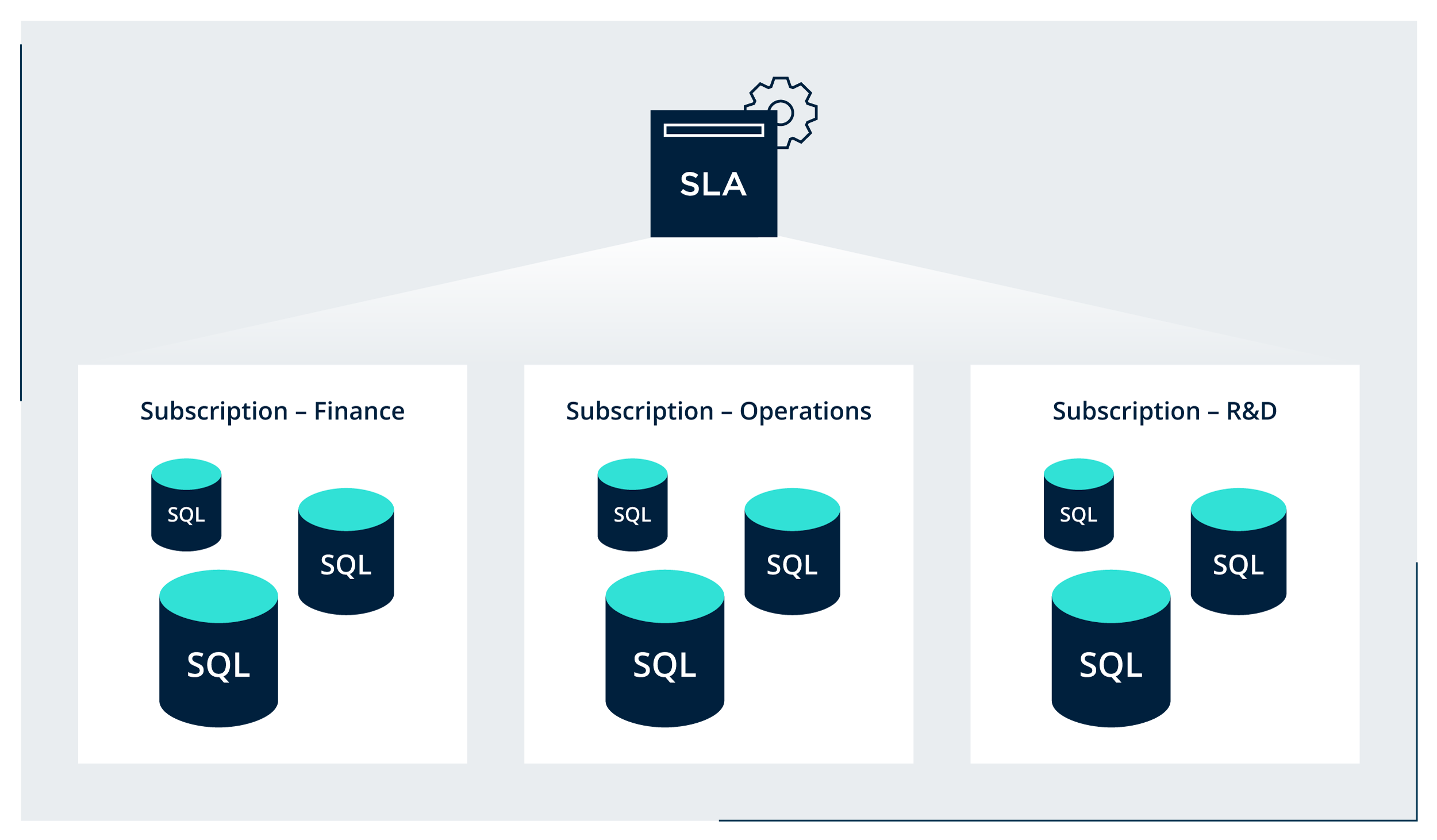
For added flexibility, an SLA policy can be applied at the individual database, database tag, managed instance, resource group, or Subscription level. This flexibility provides a simple way to implement a baseline protection strategy by applying an SLA to a subscription (top-level) that inherits to all databases at the object level. If any exceptions are needed for more granular protection (or exclusion) an SLA can be directly applied at a lower level through a resource group, instance, tag, etc.
Protecting Azure SQL with Rubrik
Once an SLA policy is applied, Rubrik orchestrates the necessary Azure SQL backup job scheduling and operations as specified by the SLA. When a backup job is scheduled to run, Rubrik initiates the required API calls to initiate the Azure SQL backup process and monitor the return status information to ensure compliance and proper enforcement. In addition to standard backups, Rubrik is also SQL transaction log aware to support low RPO requirements.
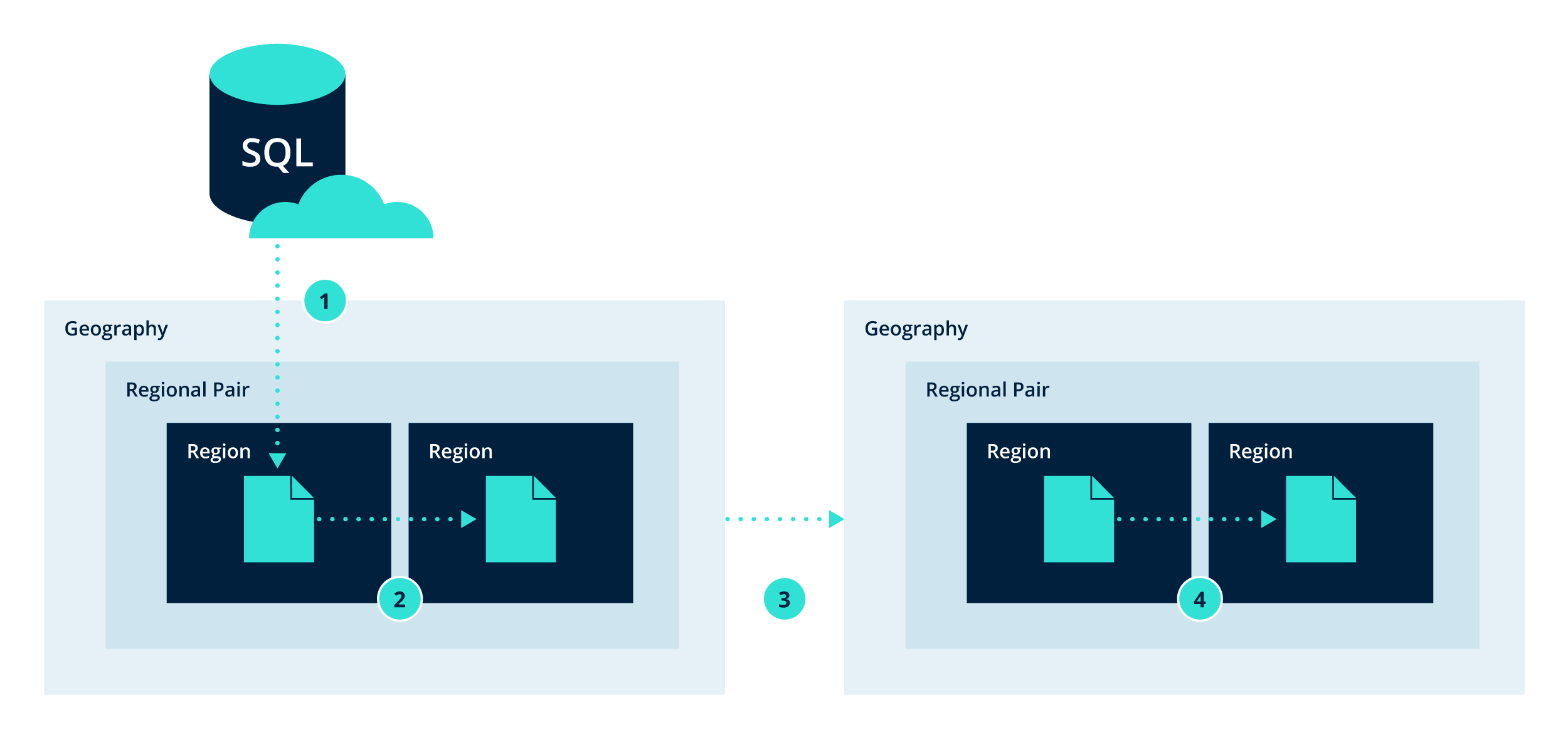
For resiliency, backups are replicated to other regions and geographies to ensure availability. In the replication process, backup data is stored and distributed synchronously in locally redundant storage (LRS), where three copies are kept for durability. It is then asynchronously replicated to a secondary region in a paired region, then a separate geographical blobstore, also known as geo-redundant storage (GRS).
Simplified Recovery of Azure SQL Databases
The recovery of a protected Azure SQL database is a simple workflow within Rubrik. Let’s walk through the process.
After logging into Rubrik and selecting either the Azure SQL Database or Azure SQL Managed instance card from the inventory, the UI provides a consolidated database view. From here, all databases discovered from the connected subscriptions are listed.
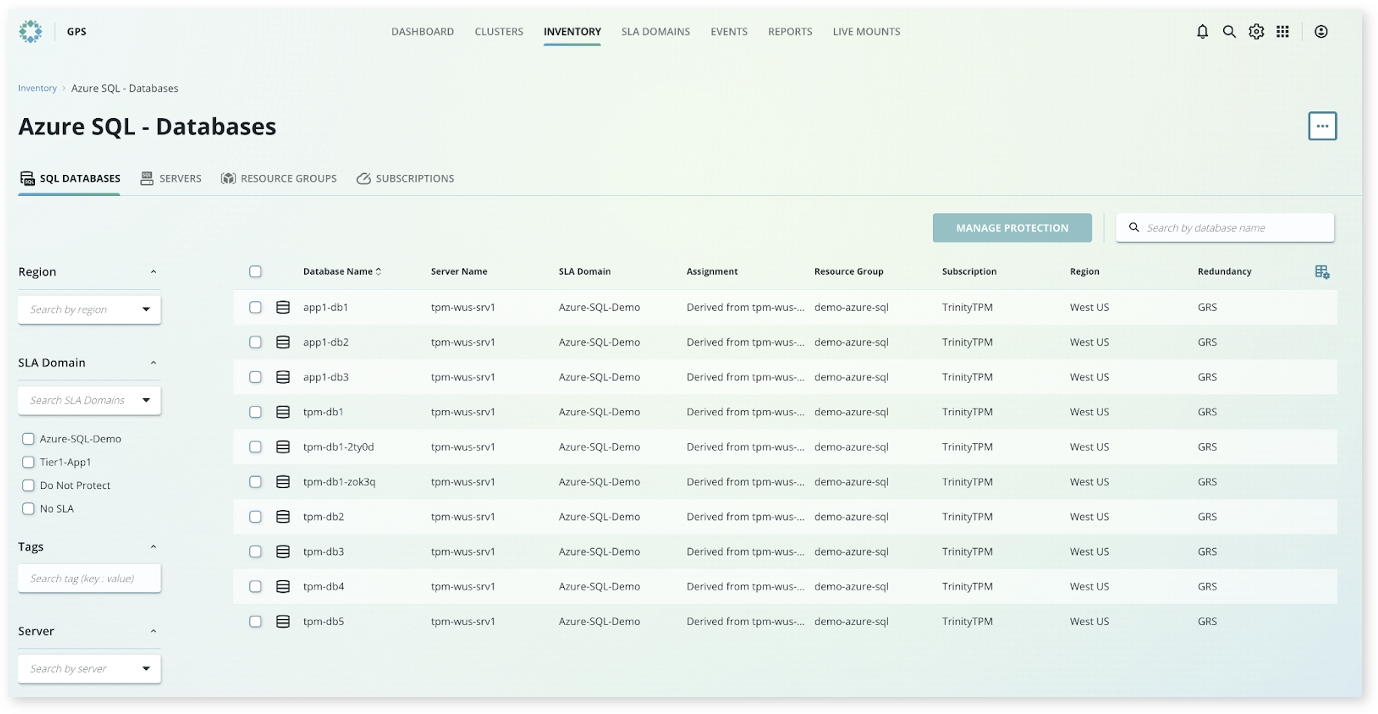
Note: this view can be categorized by subscription, resource group, server, or database. Additionally, objects can be searched by name and filtered by region, SLA Domain, tag, etc.
To begin the recovery workflow, simply select the database from the consolidated view to access the object details. From here, a familiar calendar view is presented where you can select the desired recovery date.
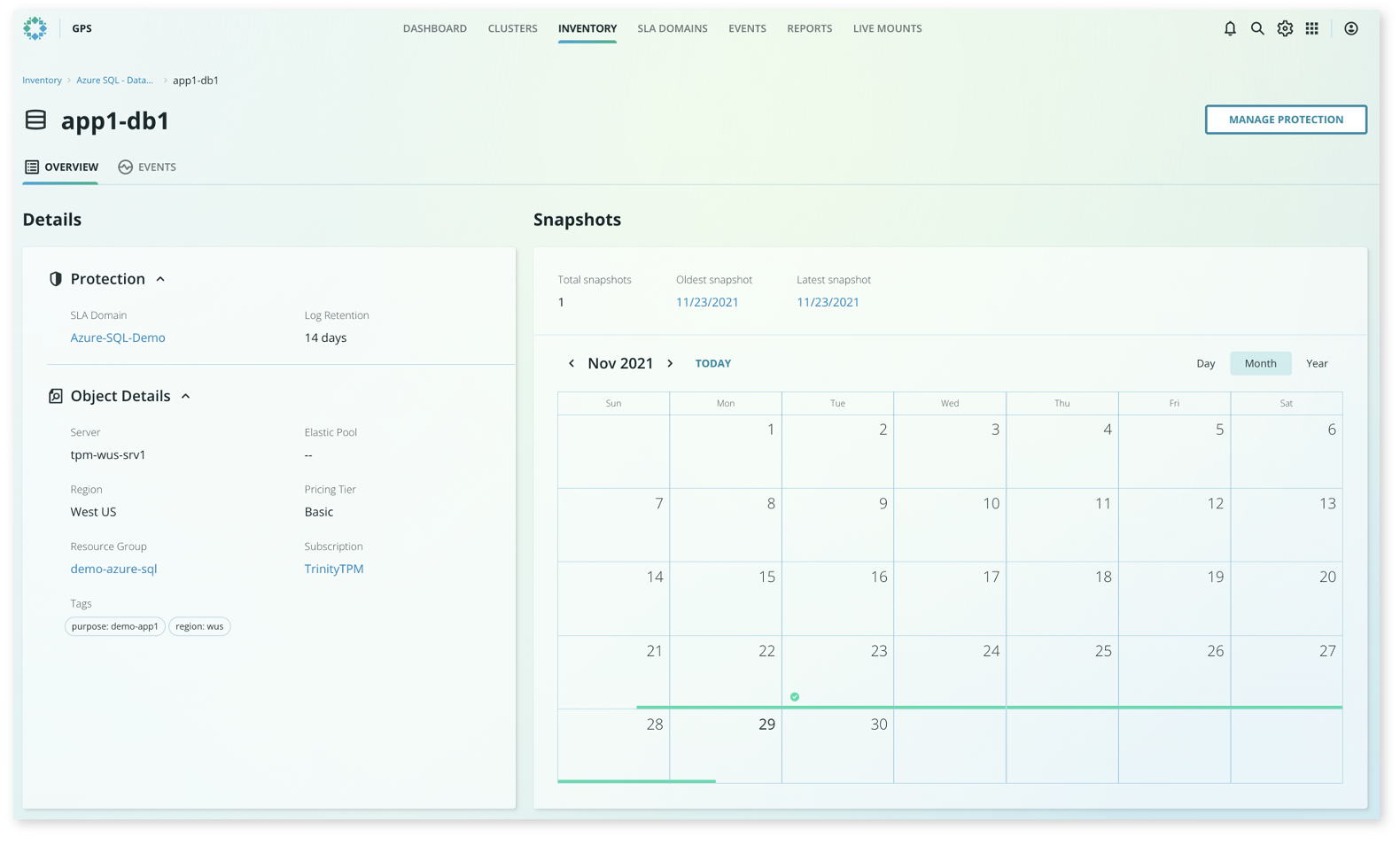
Once a date is selected from the calendar, you can simply specify a recovery point by either using a slider bar or by typing in the desired time—the same experience as any other protected object in Rubrik.
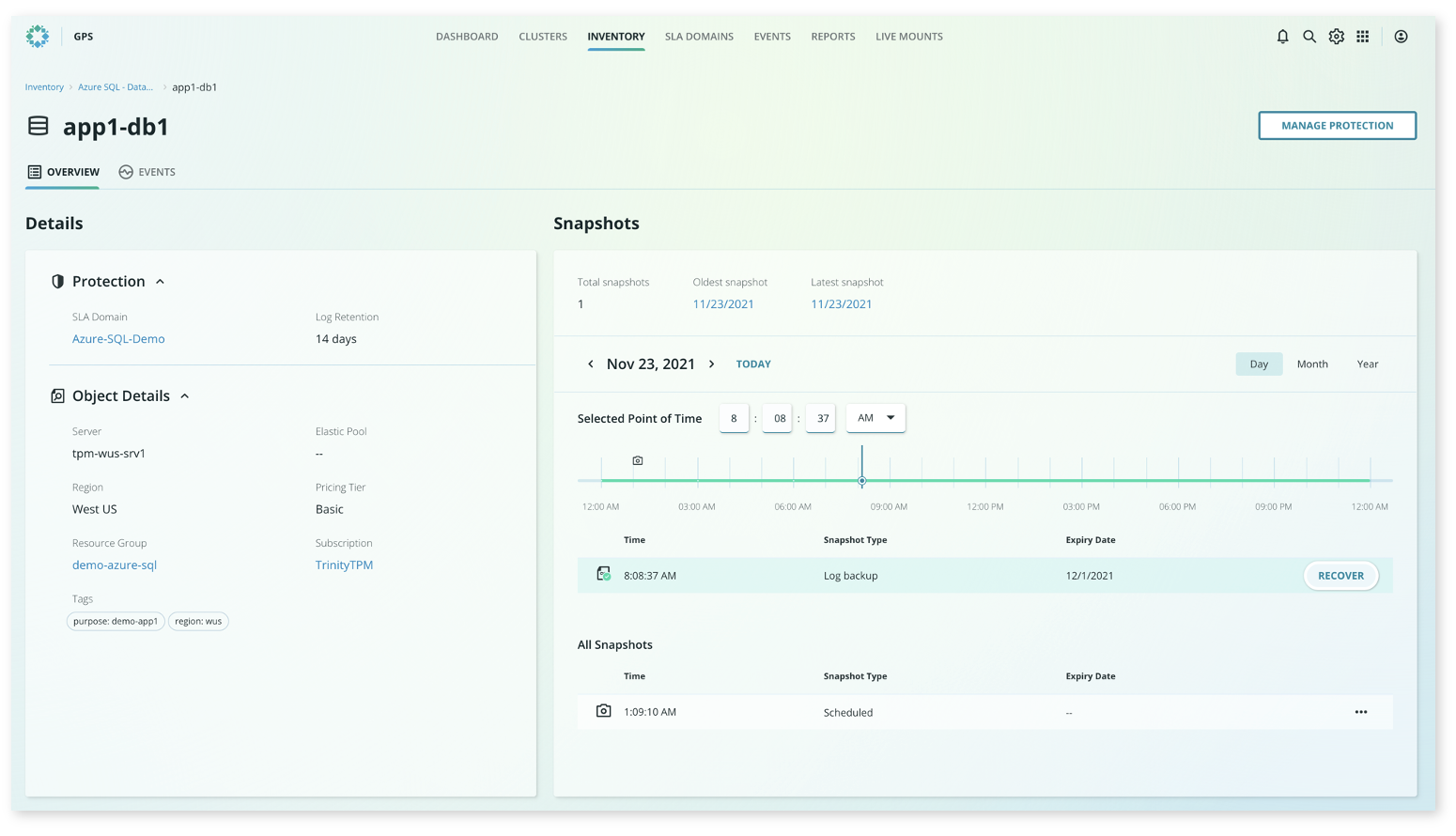
Once the desired point-in-time is defined, click Recover to initiate the recovery workflow.
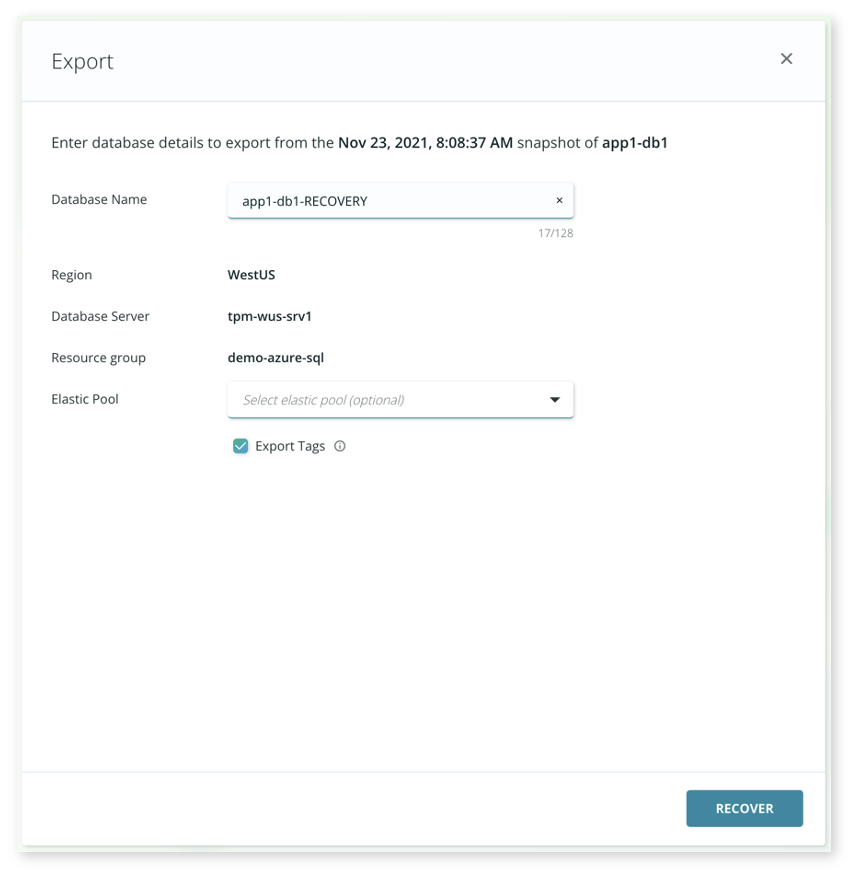
With the simplicity and value of PaaS for traditional workloads like Microsoft SQL, it is safe to assume that the enterprise will continue the adoption of cloud solutions. With Rubrik for Azure SQL, Rubrik customers can secure their Azure SQL data with the same simplicity and automation that Rubrik is known for.
Be on the lookout for additional details in our Data Security Spotlight, where we discuss the details of the feature, accompanied by a product demo.
For more information on Rubrik protection for Azure workloads, check out our technical whitepaper where we next dive into protecting Infrastructure as a Service (IaaS) with “How it Works: Cloud-Native Protection for Azure.”
