Let’s face it, you’re still vulnerable to ransomware.
Even if it feels like you’ve done everything—you’ve built a robust defense, you have multiple cybersecurity measures in place, and you’ve implemented a company-wide security training. But, is it enough?
Every business is vulnerable to ransomware. From the largest bank to the smallest school. Cyber attacks on the most technologically advanced companies like Samsung, Okta, and Uber, or attacks on education institutions make one thing clear.
Despite investments in cyber security, organizations are still vulnerable to cyber attacks.
When ransomware hits, cyber criminals can hold your business hostage by encrypting data and demanding you pay for its release. In an action movie, you have an option of sending in a SWAT team to hold the bad actors accountable. In real life, the most attainable option seems to be to pay the ransom. But there has to be a better way to recover from ransomware!
Which raises the question, what is that missing piece in defending against ransomware?
Moats Aren’t Enough
Cyber threats and malware have been around since the early days of the internet.
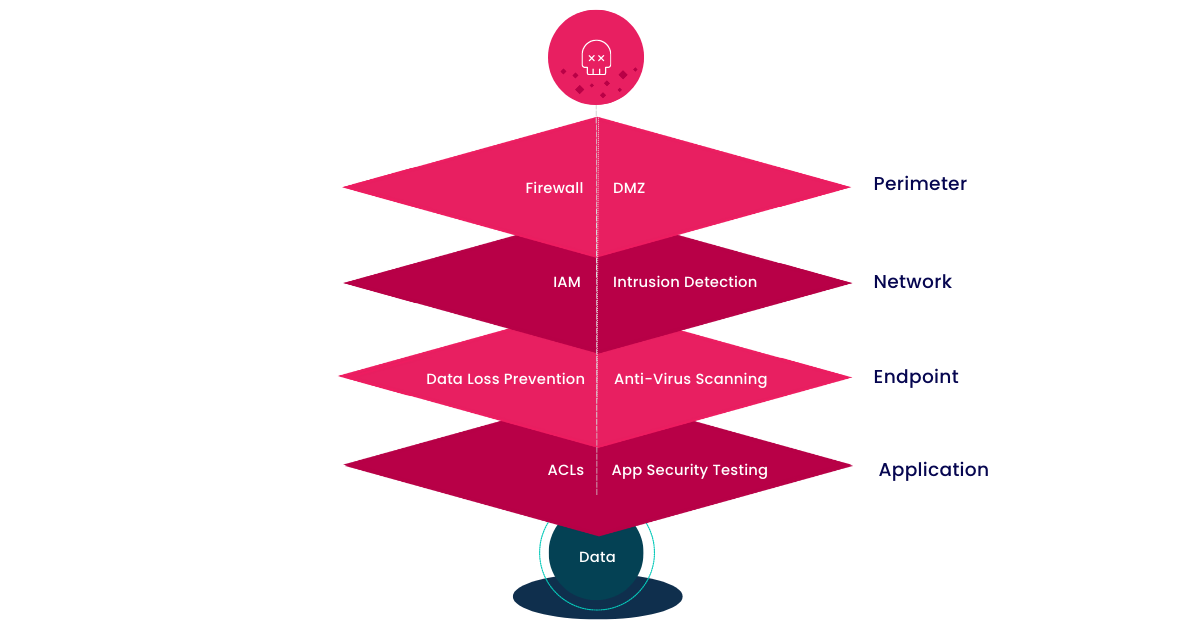
Cyber attacks have since become more sophisticated, and the cyber security industry has evolved with it. The traditional "castle-and-moat" defense aims to secure the network by blocking out any malicious actors.
At the perimeter, firewalls have become more intelligent, moving from simple packet filters to working with identity based rules
Endpoint protection software now leverages machine learning, behavioral analytics, and honeypots to provide a holistic view of the entire estate
Role-based access control (RBAC) enforces least-privilege approach. Multi-Factor Authentication (MFA) protects against brute-force attacks
The addition of SIEM and SOAR tools, and the Security Operations Center enables organizations to be more responsive to active threats
This layered defense approach continues to evolve with innovations in infrastructure security across prevention, detection, and investigation. Each layer is built on the idea that the layer above has failed, and you need to protect the business.
But, in the cat-and-mouse game of ransomware, bad actors seem to be winning.
These days, more and more data is being stored across public clouds and SaaS applications. And, the pandemic has completely reshaped the way organizations work. When we access critical data and applications remotely, it expands the network perimeter and creates significant vulnerabilities in the infrastructure defense.
Of course, infrastructure security is absolutely necessary.
But, if you look at the recent rise in ransomware attacks, cybercriminals are successfully breaching these layers, at a terrifying rate, and getting through to your data.
The Perfect Storm of Ransomware
What we’re seeing is an industrialization of cyber attacks with technologies, platforms, and supply chains:
Ransomware-as-a-Service enables sharing infrastructure, tools, and playbooks
Cryptocurrency gives anonymity with cross-border transactions
Nation-state hackers get a license to participate in ransomware action
It’s the ideal product-market fit for the ransomware industry. A perfect storm that threatens business continuity.
When attackers penetrate the infrastructure defense, they can access critical business data and destroy, encrypt, or exfiltrate it.
Once they get in, how do you stop them from taking your business down by holding your data hostage?
The Missing Piece
To protect against the vast threat landscape, everything must be secured. We cannot pick and choose...Attacks can’t be 100% prevented. We have to think about operating even while under attack. With data [availability], you can get back to your feet. Data resilience and data recovery are essential to managing risk.
If data is the most valuable asset, data security is absolutely critical.
Rethinking Cyber Security with Zero Trust Data Security
Infrastructure security is absolutely essential. You cannot leave the doors and windows of your house open. But in the face of ransomware, we need to approach cyber security with a new mindset.
Infrastructure security combined with data security is the comprehensive Zero Trust Security strategy that can guarantee business continuity.
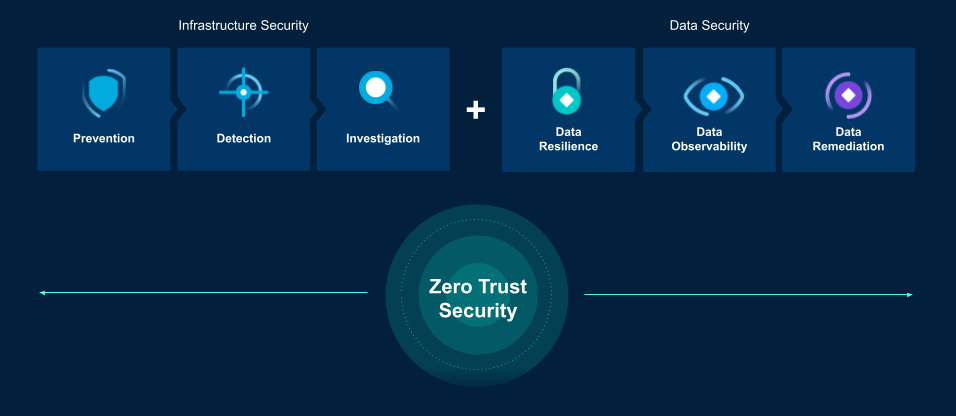
To better handle an adversary that breaches your security controls, you need investments in Zero Trust Data Security that delivers:
Data Resilience to protect your data from cyber threats with air-gapped, immutable, access-controlled backups
Data Observability to continuously monitor your data for ransomware, manage sensitive data exposure, and hunt for indicators of compromise
Data Remediation to surgically and rapidly recover your apps, files, or objects while avoiding malware reinfection
When your data is safe and available, even in adverse conditions, you can maintain business continuity, without paying the ransom.
Data security is more about having a process that not only protects the data when you know you've been breached, but protects the data before you become breached.
Learn more about the essentials of data security strategy and why it is important to protect your data, monitor data risk, and quickly recover your data, wherever it lives in our blog, Why Data Security is So Important.
