With the rise of ransomware and cyber attacks, the term defense-in-depth has risen to the forefront, but what exactly does it mean? At its core, defense-in-depth is a protection mechanism for network security–an approach that involves layering or using multiple controls in series to protect against possible threats. This layered concept provides multiple redundancies in the event systems and data are compromised. If one security layer is breached, defense-in-depth means that many more security layers lie before the attacker to increase the difficulty of a complete breach vastly.
Perhaps the easiest way to convey a defense-in-depth approach to security is to relate it to a medieval castle. In the event you want to penetrate a castle, you are first presented with many other obstacles.
For instance, before getting near the target, you often have to cross a moat, drawbridges, and get through various other choke points, each increasing in difficulty and even if you do get past these first layers of security, you are then faced with towers containing hidden threats, along with locked doors and armies. The point is, just because you have breached the moat, does not mean you have automatic access to the throne.
At this point, you may already be connecting the dots to a defense-in-depth approach in your organizations. You have firewalls, both on edge and locally on workstations. You have antivirus and antimalware software installed on clients and servers. All of these are indeed layers of defense-in-depth, but to truly understand the value of it, we must first understand the concept of security controls.
Layers belong to controls
The defense-in-depth approach to network security is architected through the deployment of security controls, which are designed to protect different aspects of your organization.
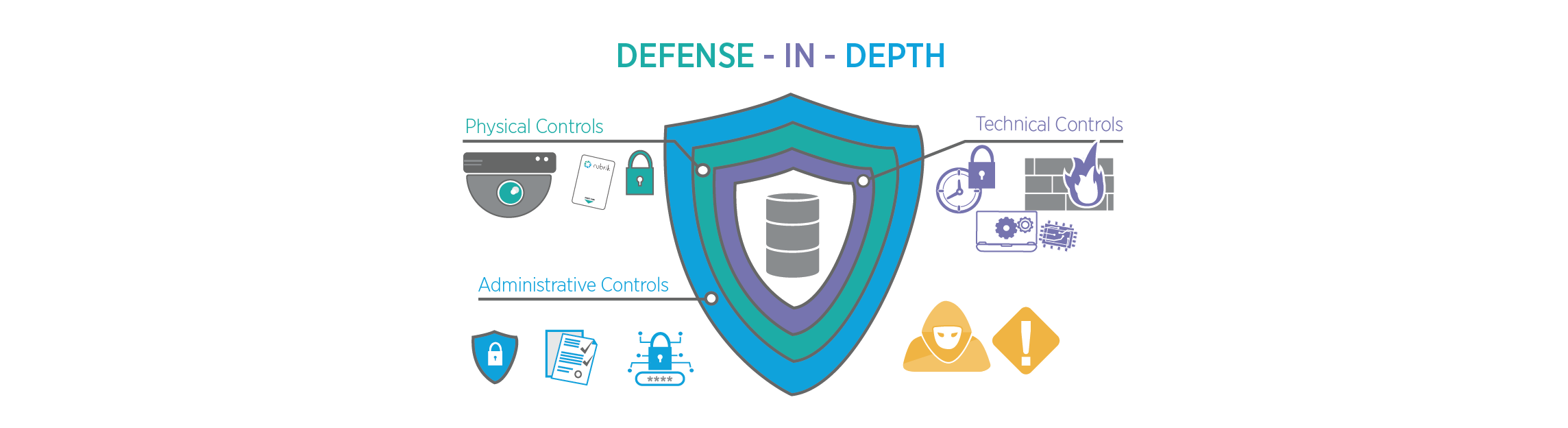
Physical Controls
Physical controls are designed to prevent physical access to your network and IT systems. Layers of security within the physical control can be as simple as a locked door to a network closet or data center, authorized key cards that must be scanned for entry, security cameras, or a security guard patrolling your building.
Technical Controls
Technical Controls are probably the most well-known layers within a defense-in-depth approach. These include security measures that technically protect our network systems and resources from known security vulnerabilities. Examples include well-known security measures such as firewall appliances and malware scanners and include features such as multi-factor authentication and time-based one-time passwords.
Administrative Controls
Administrative controls are mostly made up of the policies and procedures organizations put into their environment and are often implemented by the employees themselves. For instance, you may have a policy that instructs users to label sensitive data and store it within a highly secure location - or maybe you have a password policy that enforces your users to utilize complex passwords.
When multiple facets from each control group are combined, a true defense-in-depth approach is deployed. While hackers may breach one piece, they will quickly be presented with another challenge from multiple layered security measures.
For example, a hacker may be able to breach an account, obtaining a username and password for a certain user through a phishing attack. However, if Multifactor authentication has been enabled they are then forced to have physical access to that user's device before being completely authorized.
If physical security constructs have been deployed, gaining access to this device becomes daunting. Perhaps if policies and education around phishing were deployed, the entire breach could have been mitigated. The point being the more layers of security we implement, the harder it is to breach our environments, which greatly increases our security posture and ability to protect critical data.
Defense-in-depth applies to more than just production
Defense-in-depth becomes even more important as it pertains to your data security solution as well. We go to great lengths to protect our production infrastructure and must apply these same security measures to our backup data. After all, your data security solution is essentially a catalog of your entire dataset across your organization and must be available to act as your very last line of defense against cyber threats.
Out of the box, Rubrik provides several key security layers to ensure your data is protected. A custom-built immutable file system helps ensures that once data lands on the Rubrik platform, it can’t be changed, modified, or deleted by Ransomware. Globally enforced multi-factor authentication ensures that users are indeed who they claim to be, and role-based access control limits authenticated users to only the tasks they need to perform, and the data that they need access to. Features such as SLA Retention Lock ensure that backups cannot be deleted through NTP poisoning, either accidentally or maliciously.
To provide a true defense-in-depth approach, organizations must ensure that they are deploying both infrastructure and data security solutions within the environment. After all, at the end of the day, data is an organization's most valuable asset - let’s make sure we have multiple security layers in place to protect sensitive information.
To learn more about how the Rubrik Zero Trust Data Security™ solution can help improve your security posture and ensure your data remains safe be sure to read the Rubrik Security Hardening Best Practices.

