The Relational Database Service (RDS) service offered by AWS is one of the most popular databases today. A lot of critical, confidential data resides inside of RDS. Hence it becomes imperative to protect this data from various threats and ensure that the data is secure.
Our approach to protecting the data inside RDS is based on two aspects:
Modernization of backup and recovery to have optimal operations: Fast backups, near-zero RTO with minimal operations, and automated workflow.
Air-gapped copy for a secure recovery, in case of cyber attacks by malicious actors.
Rubrik already supports a modern approach to safeguarding RDS data from an operational perspective and also maintains a clean, secure copy in a different region.
Today, we’re excited to add replication across accounts and regions to safeguard the data from account-wide attacks by ransomware, malicious actors, and other insider threats.
How to start using this new functionality?
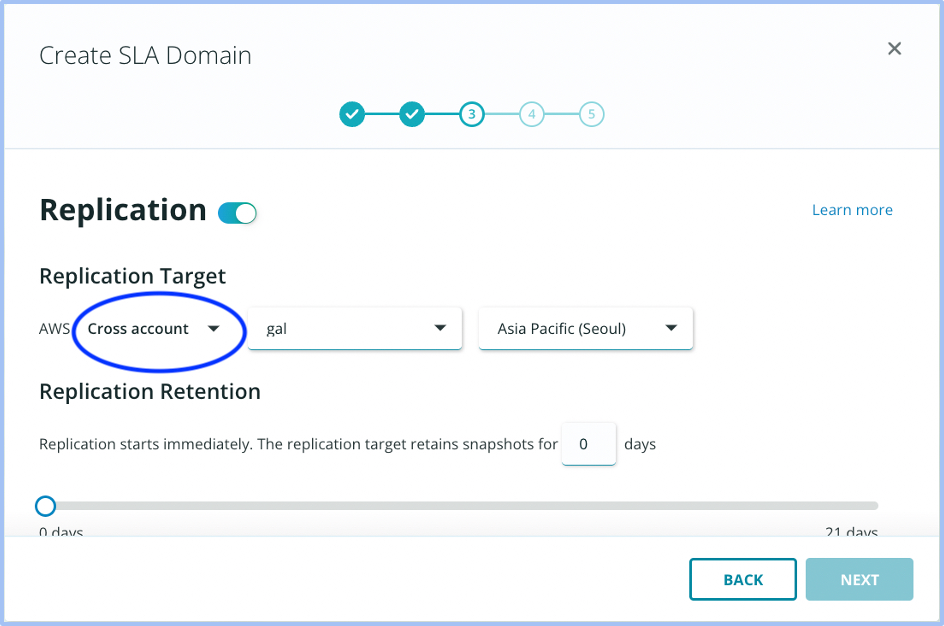
Updating SLA domains
In order to protect an existing RDS instance by replicating across accounts, the SLA domain needs to be updated to select the right destination for the replica. The options are simple where in addition to the previously available region selection, you can now select a new account as well.
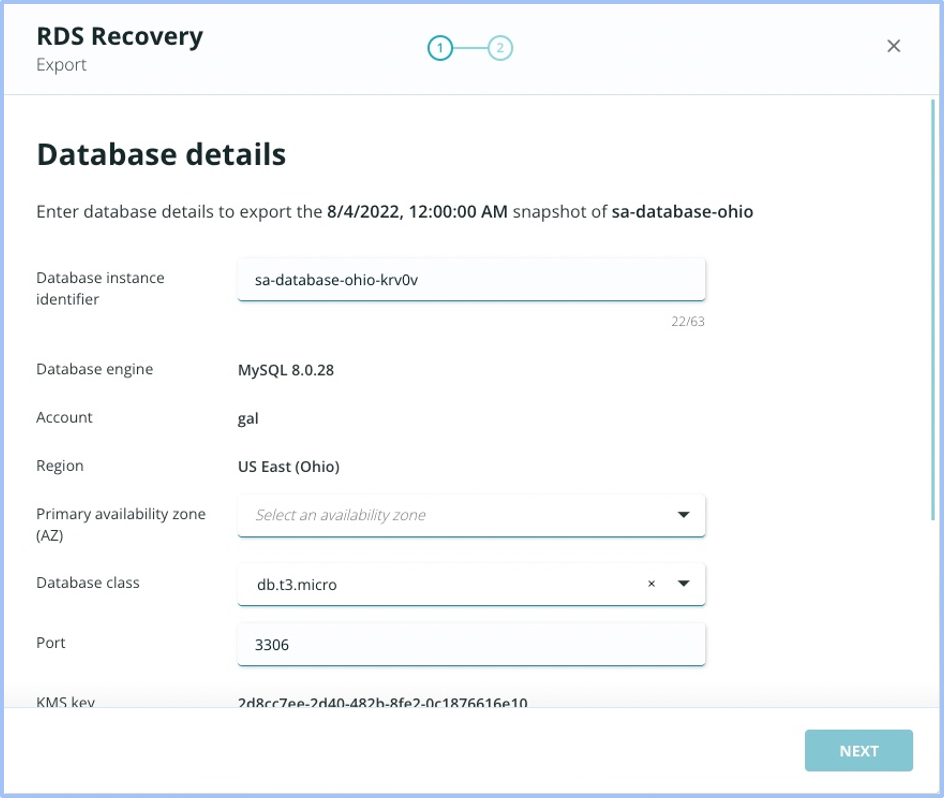
Exporting a cross-account replica
We will now be supporting the Cross-Account Export of RDS Instances taken by Rubrik Security Cloud. The export flow will now contain a dropdown listing ALL the AWS Accounts added for feature RDS.
We allow cross-account export of both source snapshots as well as a replicated snapshot.
Prerequisites to using the new functionality
The RDS data protection solution is based on the RDS APIs available for taking snapshots. Currently, the default limit for AWS RDS snapshots is 100 per account per region. This limit might not be sufficient to support all the RDS data protection jobs that might be running in the environment, considering new snapshots being taken and the retention of existing ones. Hence when the limit is hit, some issues might occur.
In order to prevent this situation, you can contact AWS to increase the snapshot limit for RDS. In order to understand what the new limit should be, here is an example calculation: If you want to protect 1 RDS instance while taking 1 snapshot daily with a retention period of 30 days, you will need to maintain a quota of a minimum of 35 snapshots (incl buffer) in the source account/source region. If you want to replicate the snapshot to a different account or a different region, the destination account/region needs enough quota to accommodate 35 snapshots on the destination based on this SLA definition.
Conclusion
Safeguarding your data that resides inside RDS is extremely important. Having a copy in a separate account helps to protect the data from account-wide threats. This standard of protection can go a long way in recovering from possible malicious events and attacks by ensuring the availability of a clean copy of the data at all times.
