Cyber threats are a growing concern for organizations of all sizes. Data breaches, malware infections, and ransomware attacks can severely disrupt operations, including financial loss, reputational damage, and legal liabilities. As a result, it is essential to proactively monitor your environment and identify malicious activity to detect threats before they can cause significant damage.
One of the critical steps toward improving your security posture is to conduct comprehensive and regular threat hunting. This involves identifying the current attacks, looking for potential vulnerabilities, and evaluating the likelihood and impact of any breach. Understanding your organization's risk profile allows you to prioritize your security investments and allocate resources to the most needed areas.
Current challenges with conducting Indicators Of Compromise (IOC) hunts in your production environment:
Reactive Monitoring
Customers may gather threat intelligence and perform log searches to identify potential threats. However, this process is often arduous, time-consuming, and requires the use of multiple tools. It can be challenging to piece together information from different tools and logs, leading to difficulty connecting the dots.
Lack of Threat Knowledge
IT teams have limited knowledge of current threats and vulnerabilities without involvement from SecOps teams. This lack of insight limits their ability to anticipate potential risks and determine how to respond when an incident occurs. The scarcity of security specialists also results in a reactive approach rather than a proactive one, as security teams are frequently in firefighting mode. Additionally, without conducting threat hunts, any intruders present in the environment can remain undetected for extended periods of time.
Production Systems Taxed
To oversee endpoints properly, it is necessary to have monitoring tools, such as EDR/XDR, installed on every server. Also, it is crucial to have these tools verified and maintained on different operating systems, updates, patches, and service packs across your datacenter. To maintain operational status, it is not uncommon to assign a dedicated individual or team to manage the compatibility matrix and upgrades required to ensure that the tools are always operational on different versions. The level of pain involved in maintaining EDR tools can vary depending on several factors, such as the complexity of the environment, the number of endpoints being monitored, the diversity of operating systems and applications, and the frequency of updates and patches. Also, these endpoint monitoring tools utilize compute resources that may impact the performance of essential applications.
These tools are critical for gaining insight into vital infrastructure. Unfortunately, endpoint monitoring tools are deployed more commonly on laptops or desktops – but not on servers – making critical infrastructure a security black box. This limits investigations to information derived from network activity, logs, or disparate tools. Even if your infrastructure is relatively stable, zero-day vulnerabilities are a lingering risk that attackers are known to exploit.
Introducing Rubrik Threat Monitoring
Rubrik Threat Monitoring offers a proactive cybersecurity strategy, enabling you to identify and react rapidly to potential threats. This can help minimize the time that threats remain undetected (threat dwell time) and reduces the likelihood of severe damage. Once enabled, through automatic IOC scanning, Rubrik Threat Monitoring will utilize a verified threat intelligence feed that includes YARA rules and file hashes to search for IOCs. If any IOC matches are identified, Threat Monitoring will notify you of the malware strain details, precise snapshot, and file location where the threat was discovered.
With Rubrik Threat Monitoring, you will be able to get the following:
Automated monitoring for threats
Threat Monitoring is designed to identify malware automatically rather than in a manual and reactive manner, thereby accelerating incident response. The sooner you spot issues, the earlier you can begin the root cause analysis and the subsequent remediation process. In other words, you are lowering the mean time to resolution (MTTR). Security teams gain the desired visibility into the most critical pieces of the infrastructure with limited or challenging monitoring capabilities. This also means you can send automated alerts to the appropriate IT teams so they can immediately address any pressing issues.
Earlier detection of new threats
Threat Monitoring will utilize an up-to-date threat intelligence feed which is vetted by Rubrik. The intelligence from this feed includes the latest threat information from the Rubrik Information Security team, Rubrik Zero Labs, and various 3rd party sources. To decrease the chances of potential false positive findings, Rubrik utilizes high-quality intelligence feeds.
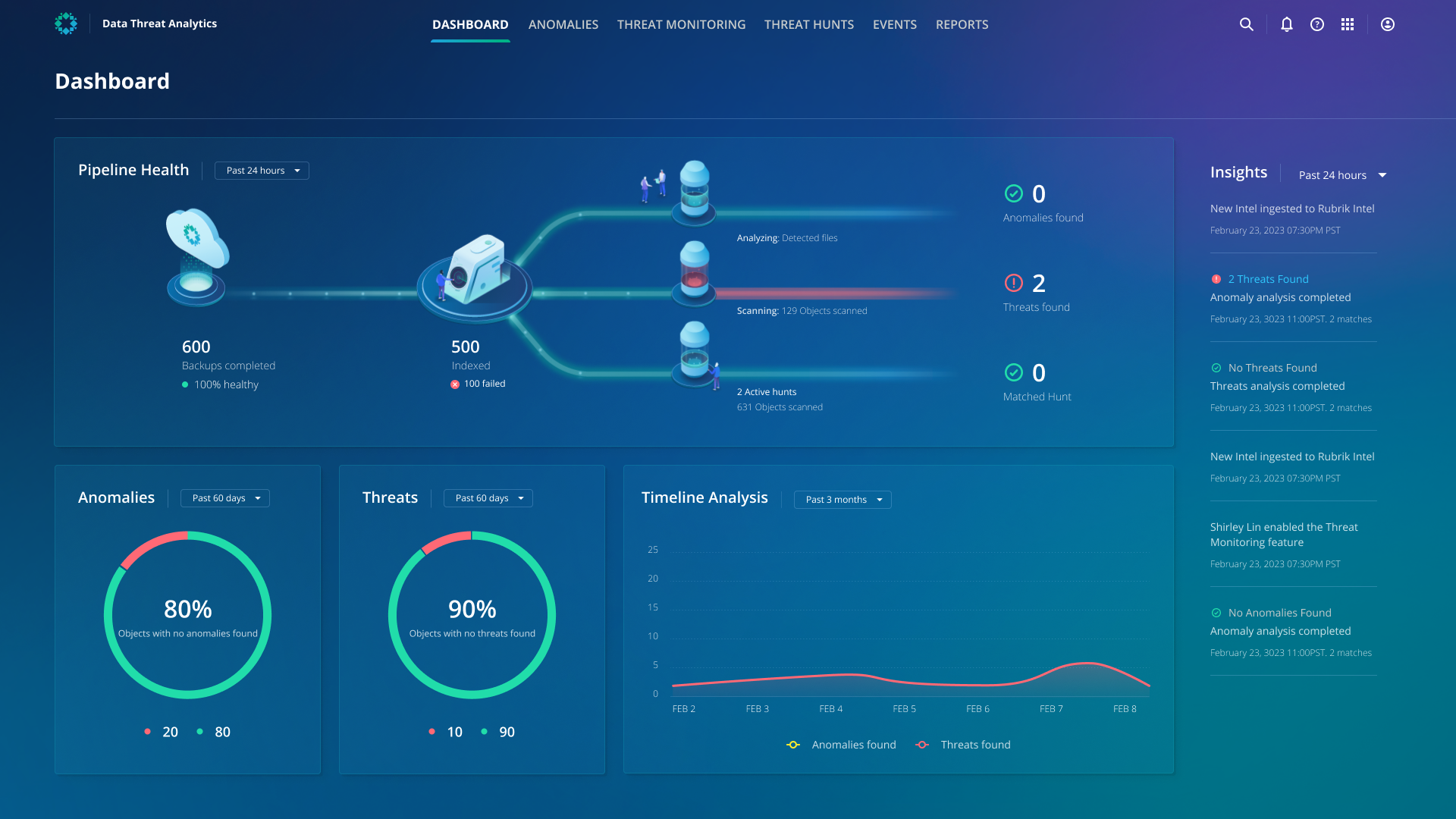
No impact to production system performance
Rubrik can back up data from many sources, offering an opportunity for various data analysis use cases to identify suspicious activity and files. This allows security teams to conduct thorough threat analyses out of band from production infrastructure without needing additional agents or compute resources. Even if attackers are present within your production environment, they won't be aware of any ongoing threat investigations.
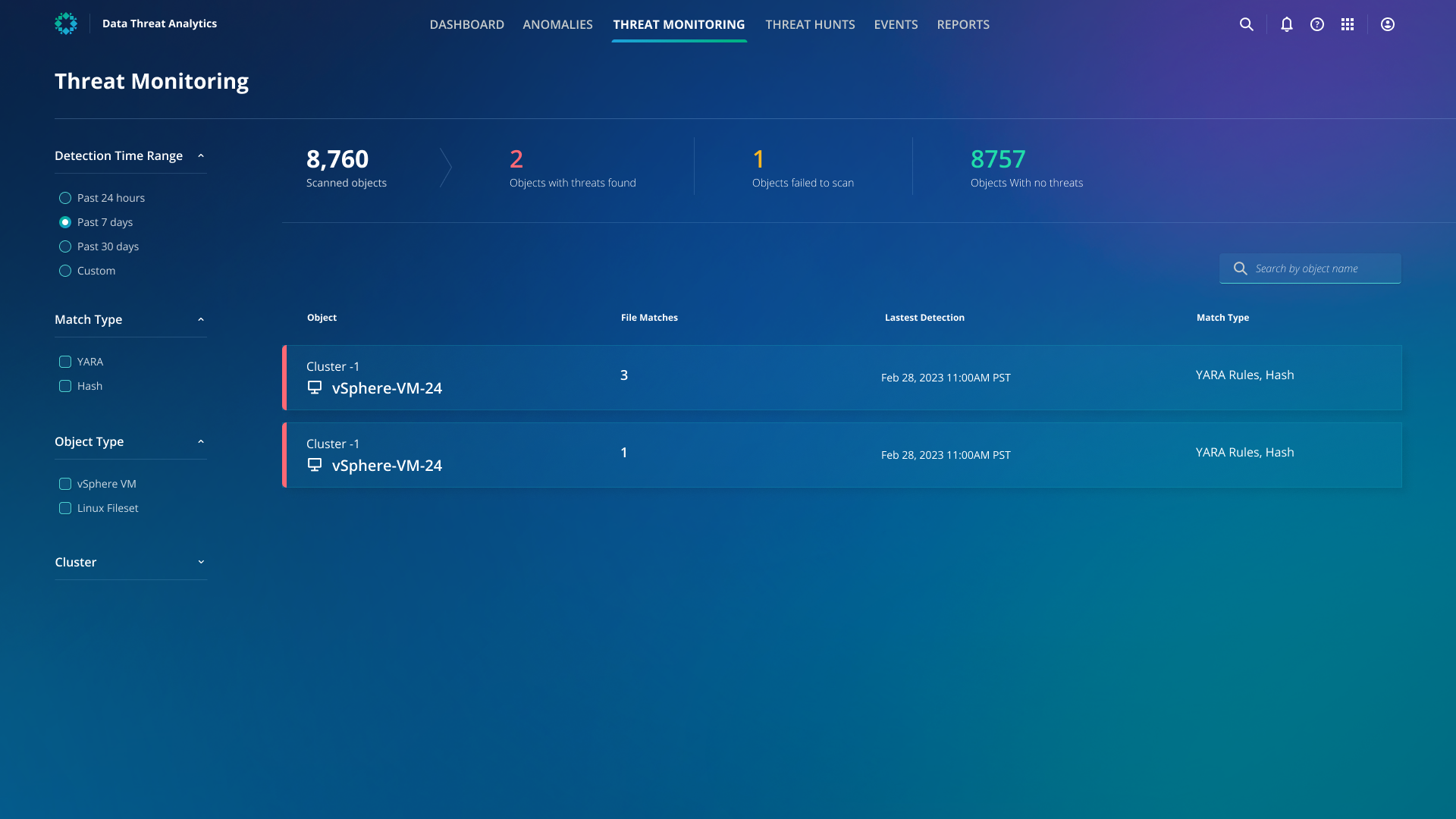
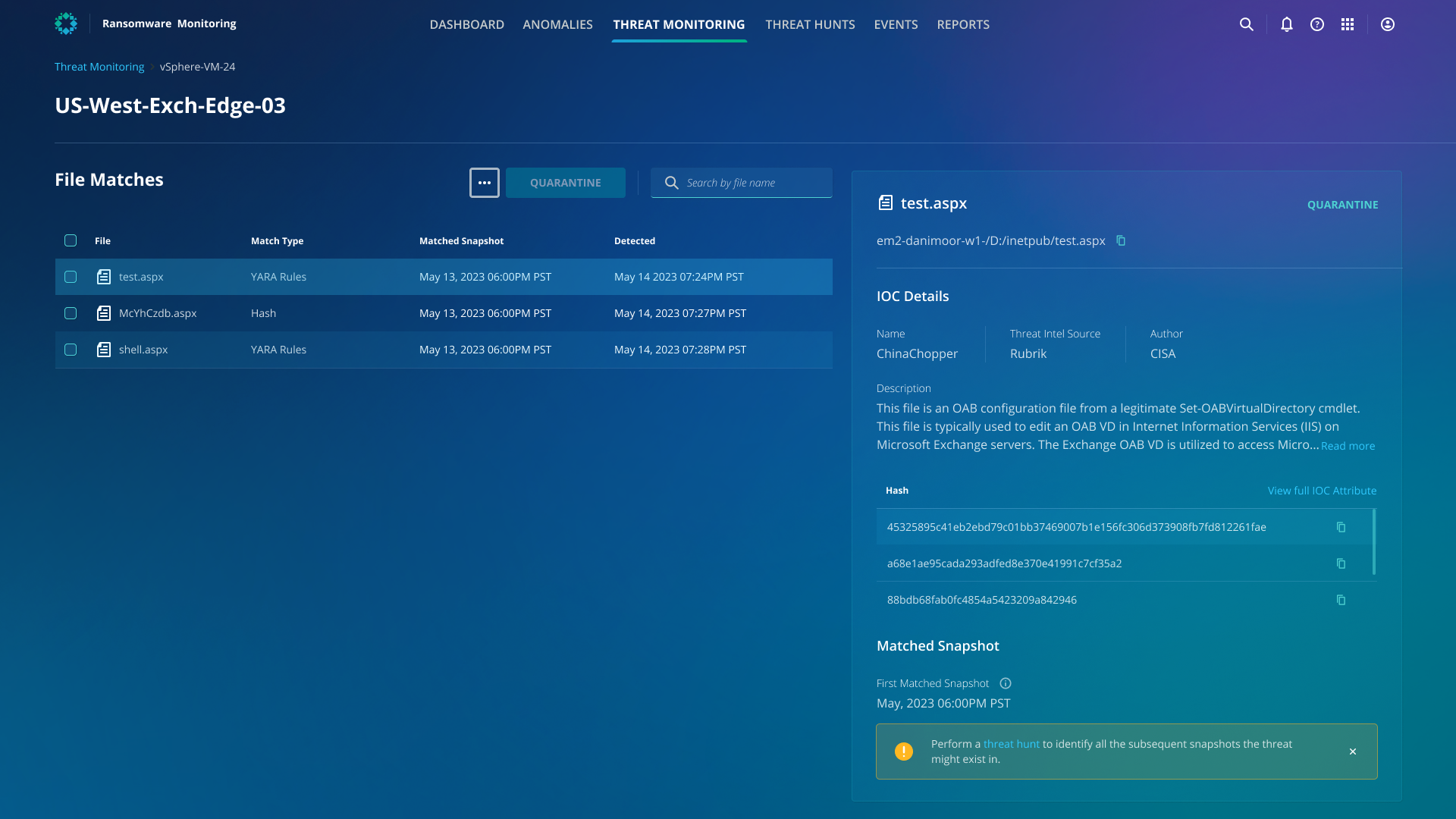
Cyber Recovery Performance Reports
Your IT teams usually have to reference multiple different dashboards and go through a slow, manual process of compiling insights from various tools to create threat monitoring and assessment reports to share with stakeholders within your organization. Rubrik Threat Monitoring offers robust, built-in reporting functionality that lets your IT team download a list of all the threats found, along with the affected and non-affected objects in your environment. The report also contains the threats found over a period of time.
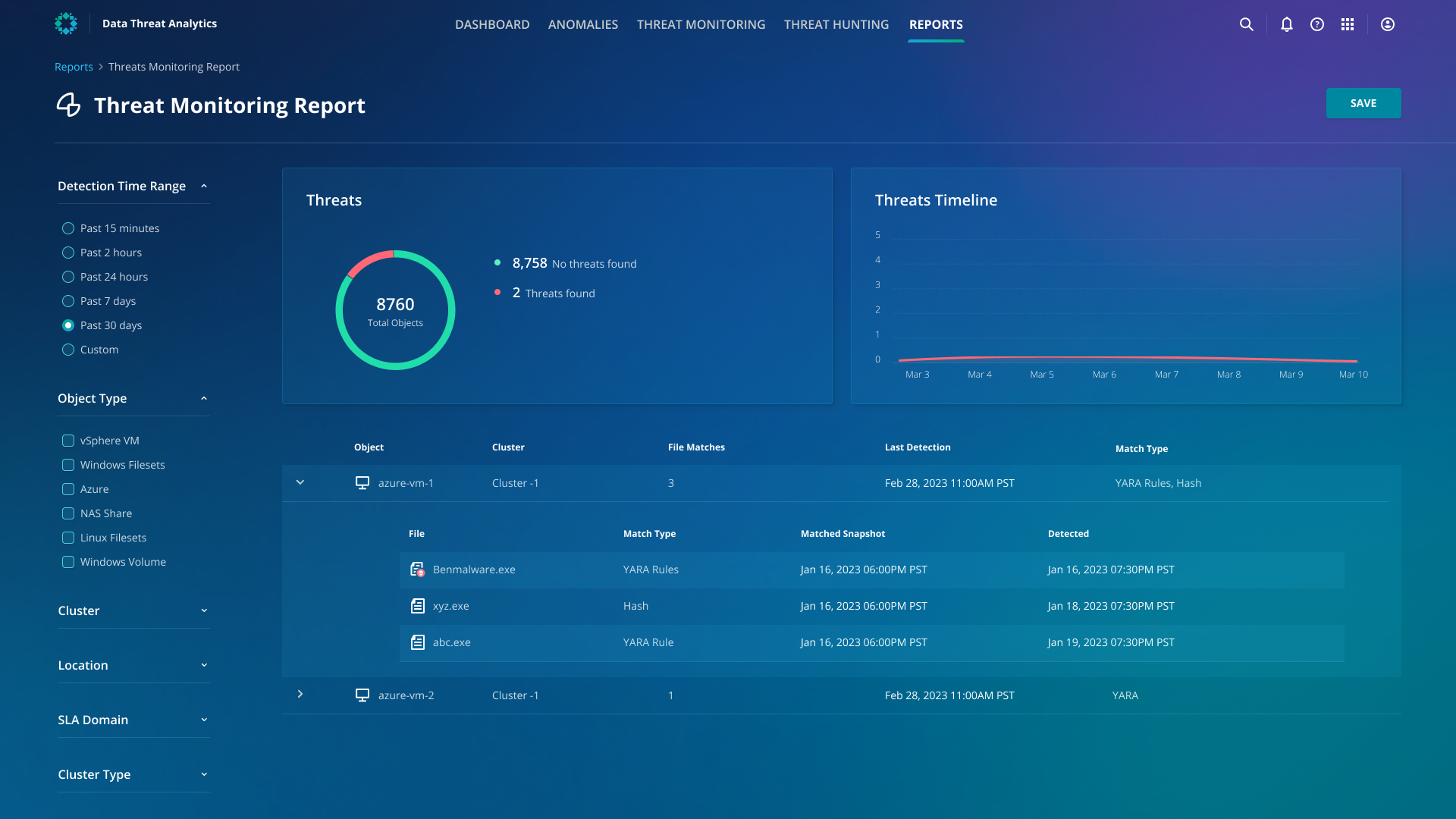
Having a proactive approach to cybersecurity is crucial in today's threat landscape. Rubrik Threat Monitoring offers a solution that will enable you to detect and respond to threats rapidly. Through automated and proactive threat hunts, you can remain ahead of the threat landscape, decrease risk exposure, and minimize the potential impact of security incidents. In comparison to current solutions, Rubrik provides the following:
Active monitoring of environments with little to no security visibility
An out-of-the-box Rubrik threat feed
Automatic updates to Rubrik threat feed
Automated threat hunts, which reduce the time and effort required to hunt for new threats
Ability to quarantine malicious files
What's Next
To learn more about how you can recognize attacks before they happen, join us at Forward virtual to learn more about Rubrik Threat Monitoring in-depth. You’ll also have the opportunity to get hands-on with Rubrik Security Cloud in our self-guided labs to explore the various cyber resilience features of our Zero Trust Data Security platform. Learn more and register for Forward here.
Safe Harbor
Any unreleased services or features referenced in this document are not currently available and may not be made generally available on time or at all, as may be determined at our sole discretion. Any such referenced services or features do not represent promises to deliver, commitments, or obligations of Rubrik, Inc. and may not be incorporated into any contract. Customers should make their purchase decisions based upon services and features that are currently generally available.
