In 2022 alone, there was a staggering 70% increase in malicious events across all public clouds. And cybercriminals are specifically targeting one of the most critical assets of any organization - its data. According to an 2023 IBM report, 82% of breaches involved data stored in the cloud. So this begs the question, which tools do defenders have at their disposal to address these mounting threats?
An often heard question is, if I already have this solution, CASB for example, why do I need something else? Any particular solution should always be a means to an end, it should enable the outcome you envision for your organization. In this case, the outcome might be “secure our cloud workloads”, which is where solutions like CASB (Cloud Access Security Broker) and DSPM (Data Security Posture Management) with DDR (Data Detection and Response) come in.
Think of it this way, a CASB is like a security guard at a concert. They check every person (data traffic) coming in and out of the venue (cloud environment), ensuring they have a legitimate ticket (credentials) and aren't breaking any rules (compliance policies), and removes anyone (blocks activity) that poses any potential risk.
DDR, on the other hand, is like having security cameras strategically placed around the concert venue. The cameras continuously monitor for any unusual activity, like someone trying to sneak backstage (unusual data access). If the system picks up on anything strange, the security team (SOC) is alerted to check the footage (investigate the event), and they can send in guards to take action (respond to the potential threat).
Our industry is extremely proficient in coming up with new acronyms, and in the world of securing cloud workloads, this is no different. Next to CASB and DDR, solutions like CNAPP (Cloud Native Application Protection Platform), CSPM (Cloud Security Posture Management), CWPP (Cloud Workload Protection Platform), CIEM (Cloud Infrastructure Entitlement Management), SSPM (SaaS Security Posture Management) and more all potentially come into play when thinking about successfully securing cloud workloads. Therefore, it is prudent to focus on what you want the solution to accomplish for you specifically, and build backwards from there.
Fundamentally, CASBs are security policy enforcement points (like gatekeepers) that sit between cloud service consumers and cloud service providers to combine and interject enterprise security policies as cloud-based resources are accessed.
DSPM solutions, on the other hand, focus on understanding and securing the actual data hosted in those public cloud and SaaS services, evolving from an infrastructure focus to a data and information focus. DDR extends this even further by using real-time information, detection, and response to secure cloud data from exfiltration. It provides dynamic monitoring, along with the static defense policies implemented via CASB (and other solutions like CSPM).
CASB solutions, either hardware or software based, are typically set up as proxies because they need to operate in the data path. A forward proxy intercepts client requests for cloud services, performs its security validation, and then forwards the requests to the actual cloud service. A DSPM with DDR solution, on the other hand, is completely out-of-band, i.e. it does not need to operate on the data path, introduces no network reconfiguration, no additional latency, and does not introduce any limitations on supported services or data types and object sizes.
Having said that, some CASB solutions also provide some level of out-of-band services through API integrations with the respective cloud providers, mostly for data-at-rest use cases. A CASB solution is also often combined with a DLP (Data Loss Prevention) solution to perform inline validation of sensitive data access. The reality is that this limits the scope to user data, as opposed to your entire organization's data landscape, which includes structured, unstructured, and semi-structured data. It also introduces an end-point agent approach with a respective compatibility list and management overhead. Again, being inline makes deployment complex and has a performance impact due to added latency. The scalability of such an approach is directly linked to the scale of the proxy network, while the DSPM with DDR approach scales on the basis of your public cloud.
So what is the outcome you can expect from either solution?
CASB solutions monitor and control the access and usage of your cloud applications (geared towards SaaS applications, typically with limited IaaS, PaaS, and DBaaS support) and services, and enforce security policies and rules. DSPM provides data security capabilities. While CASB helps you secure your SaaS applications and services, DSPM helps you secure your cloud data.
With DSPM and DDR, you gain discovery and classification of data. This reduces the risk of a data breach by giving you visibility over your entire data ecosystem. Understanding the sensitivity of your data and where it is stored will also help your security team understand the most critical areas to focus their attention on. DSPM and DDR will also allow you to control access to data and implement effective identity security hygiene leveraging least privileged access, which limits data breach exposure. Data also moves around the cloud, so you need to continuously monitor new and modified data stores against your security requirements and applicable regulations. This also proactively reduces risk. You can analyze and score data risks based on data sensitivity, regulatory compliance, security controls, and other secondary factors. Ultimately, governing how data is handled and protected requires the implementation of the right policies and procedures. These should cover data access, use, storage, and disposal, aligned with industry standards and regulatory requirements. By establishing clear policies and procedures, you’ll reduce the likelihood of human error or intentional misuse of data leading to a breach.
DDR is then the cherry on top, by allowing you to detect external and internal threats to your sensitive data. This allows you to quickly investigate, contain, and minimize the impact of data breaches, but with the added benefit of being completely transparent and out-of-band, so no additional configuration and management overhead is introduced.
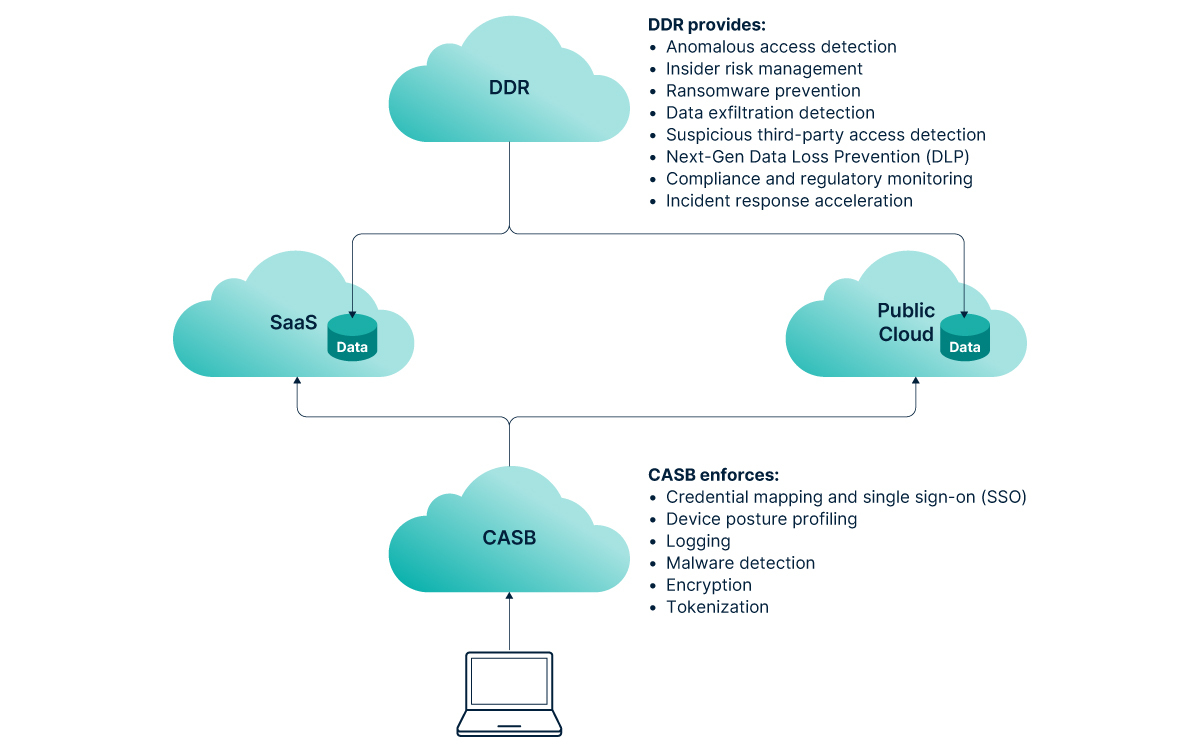
You can use Laminar’s DDR capabilities for key data security use cases:
Anomalous access detection
Insider risk management
Ransomware prevention
Data exfiltration detection
Suspicious third-party access detection
Next-Gen Data Loss Prevention (DLP)
Monitoring for compliance and regulatory relevant data
Incident response acceleration
Which One Should You Choose?
The decision between a CASB and Laminar's DSPM with DDR solution depends on your organization's specific needs. If you need broad coverage across numerous cloud services with various types of policy enforcement, a CASB may be the right choice. However, if your primary concern is the protection of sensitive data and quick response to data-related threats, Laminar DDR could provide the focused solution you require.
In many cases, organizations may find that a combination of both a CASB and a specialized DSPM with DDR solution like Laminar offers the most comprehensive cloud data security strategy. This layered approach ensures broad policy enforcement through CASB, with the added depth of data-centric security and rapid threat response from DSPM/DDR.
As cloud environments continue to evolve and expand, a clear understanding of the different tools and solutions available is essential. Whether you choose a CASB, Laminar DSPM/DDR, or a combination of both, the goal is always to secure your data effectively in the ever-changing landscape of cloud computing.
