IBM DB2 database administrators face a growing disconnect between increasingly sophisticated database environments and the outdated tools protecting them. Traditional backup methods for IBM Db2 rely heavily on complex scripting and disparate tools, creating challenges that directly impact your operations.
These traditional Db2 backup methods have failed to keep pace with modern enterprise needs, creating operational bottlenecks and recovery risks across Windows, Linux, and Unix environments.
Rubrik suggests an architectural approach that eliminates scripts, automates protection, and provides consistent experiences across all OS platforms. This approach to Db2 backup strategy delivers granular recovery, simplifies management, and promotes the kind of operational efficiency that today's database administrators require to match today’s complex hybrid computing environments.
The Hidden Costs of Traditional DB2 Protection
Limiting your data protection, backup, and recovery tools to traditional Db2 tools and methods can lead to unexpected costs, such as:
Granular Recovery Challenges: Traditional methods force you to restore entire databases—a time-consuming process that can result in significant data loss if an incident occurred recently.
Backup Management Complexity: Managing multiple backup jobs and schedules across various environments becomes increasingly cumbersome and error-prone as your DB2 footprint grows.
Operational Efficiency Impact: DBAs spend substantial time managing backups rather than focusing on core database administration tasks, creating a hidden productivity tax on your team.
These protection challenges compound across diverse environments, especially when managing DB2 deployments on both Windows and Linux platforms with inconsistent tools and approaches.
Architectural Overview: How Rubrik Protects DB2
Rubrik provides automated discovery of Db2 databases and manages the entire data lifecycle from a single console across on-premises and in the AWS and Azure public clouds. Rubrik integrates with DB2 through a native vendorlib integration that delivers secure, consistent, and automated protection. This architectural approach eliminates scripts and provides a streamlined configuration, backup, and recovery workflow.
Key Components and Data Flow
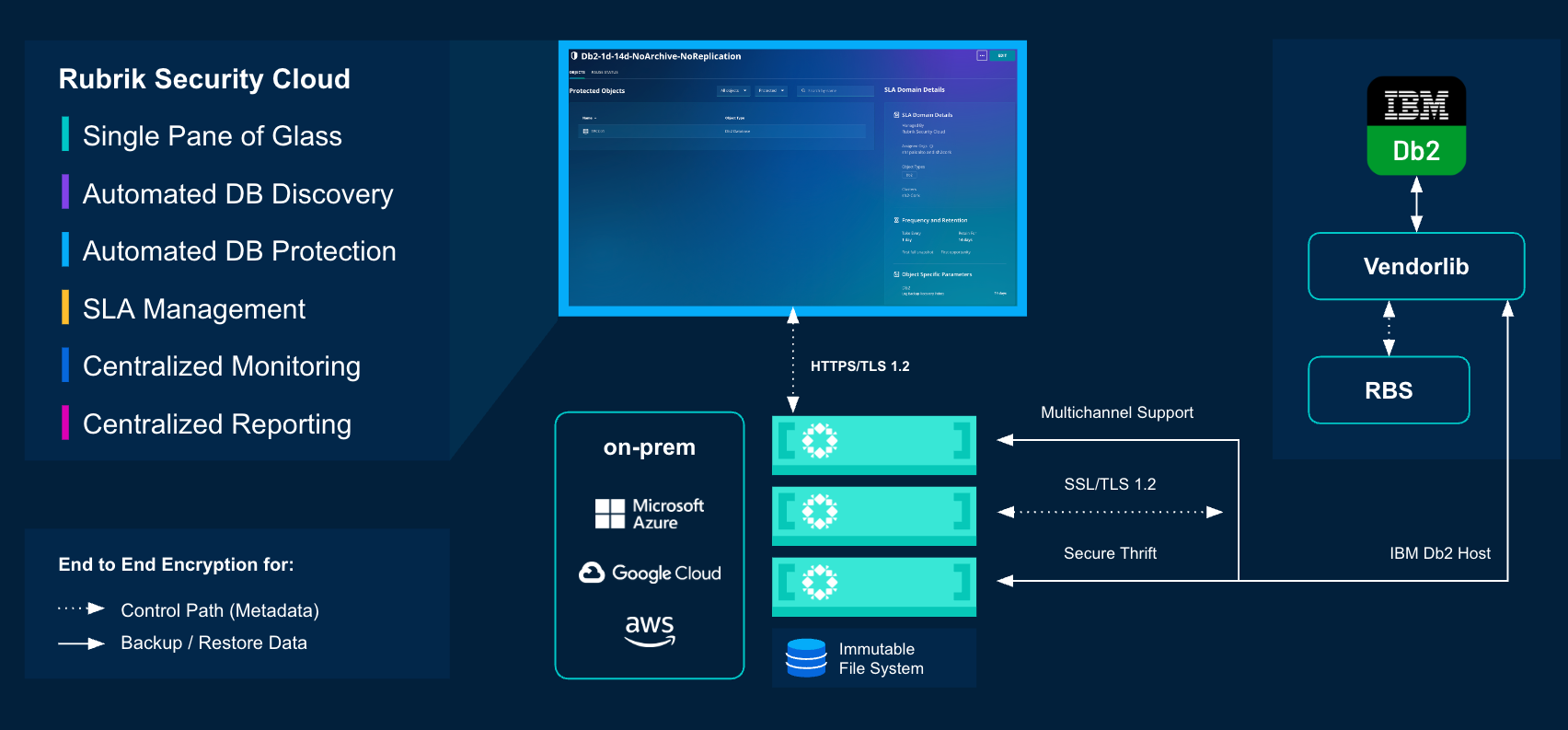
Rubrik’s native IBM Db2 database protection is similar to the backup and recovery protection offered for VMware, Oracle, MS SQL, PostgreSQL, and other workloads, consisting of the following five key components:
Rubrik Security Cloud (RSC): RSC is a SaaS platform that provides data protection and cyber resilience across on-prem, cloud, and SaaS environments, securing data assets and supporting rapid recovery from cyberattacks.
Rubrik Secure Vault (RSV) cluster connected to RSC. RSV is a key component of Rubrik's data security platform, providing a secure and isolated location for storing critical backup data. Secure Vault helps maintain continuity, minimizing data loss from cyber threats, especially ransomware.
IBM Db2 host in the Public Cloud or On-Premises: The data source that you want to protect.
Rubrik Backup Service (RBS): RBS helps ensure secure communication between Rubrik and Db2. The RBS software is deployed on the host or cloud virtual machine, running the Db2 database without impacting the host's performance.
Vendorlib: Rubrik provides a library that implements the Db2-provided backup interface to interact with backup vendors, which gets deployed once the RBS software is deployed and configured on the host. This client leverages the native Vendorlib client to perform backup and restore operations to enhance the backup process and ensure data durability and system resilience. It also allows for parallelization, where backups are executed across multiple threads, significantly speeding up the backup process for large data volumes.
Together, these elements streamline Db2 database management from setup through daily operations and compliance. Let’s analyze the customer workflows to understand how this architecture can simplify data protection in the enterprise:
Security and Communication: Rubrik provides end-to-end security throughout the protection process, encrypting all external and internal communications between protected objects, RSC, and cloud accounts. The control path communication between RSV and RSC uses the TLS 1.2 protocol encryption, while the data path leverages the Secure Thrift protocol for secure data transfer. TLS 1.2 & Secure Thrift protocol ensures that the actual backup and recovery data is exchanged between Rubrik's components and the database is secure to maintain the data confidentiality and integrity. RSV also provides an immutable file system that protects against ransomware and unauthorized modifications.
Agent Deployment: RBS software is deployed on the host or cloud virtual machine running the DB2 database. A vendorlib library is automatically deployed once the RBS software is configured on the host.
Discovery Process: The data discovery process is quite simple. An administrator adds Db2 hosts and instances to the RSC, and Rubrik retrieves metadata from the control plane flow. Using this metadata, Rubrik automatically discovers all databases for the added instance.
Protection Workflow: Once discovered, administrators create and assign Global SLA Policies that automate protection frequency, retention, replication, and archival. Backups (full, incremental, or delta) are triggered based on the assigned SLA—Db2 interacts with the IBM-provided and Rubrik-implemented vendorlib library to write to the immutable file system on RSV. The backup data is retained according to the SLA policy assigned to the database. Essentially, RSC manages the entire lifecycle of the data.
Recovery Process: Recovery is performed via CLI using native Db2 commands. During restore, Db2 interacts with vendorlib to retrieve relevant data snapshots and logs. Vendorlib communicates with RBS and Rubrik's immutable file system to recover to a consistent state. Existing DB2 tools and processes can be used alongside the fetch tool binary provided with the RBS installation. The fetch tool automates the downloading of backup images and log files during the recovery process in case the existing Db2 commands don't work or if the customer wants to hold these images/logs separately.
Rubrik’s Platform-Agnostic Data Protection
One of the most powerful aspects of Rubrik's approach is its consistency across platforms. Whether you are running Db2 on Windows or Linux, the experience remains the same:
Automated Discovery:
Rubrik automatically discovers databases during day 0 operations as DB2 hosts and instances are added to the platform.
Rubrik automates the configuration of LOGARCHMETH1 or LOGARCHMETH2 to the vendorlib path after the SLA assignment.
Declarative SLA Policy Engine:
Rubrik streamlines the protection of Db2 databases through SLA policies that configure backup frequency, retention, archival, and replication using the same engine.
Rubrik supports full, incremental, and delta backups along with transaction log backups.
Point-in-Time Granularity:
Rubrik enables point-in-time recovery by leveraging data and log backups together.
Rubrik provides granular control over recovery points by rolling forward log backups on top of data backups using native CLI commands.
Unified Management and Reporting Platform:
Rubrik protects Db2 and other databases alongside datacenter objects across on-premises and cloud environments with centralized visibility and control.
Rubrik provides active monitoring of Db2 data and log backup status through a centralized activities pane.
Rubrik delivers comprehensive SLA compliance reporting with backup summary information, the latest recovery points, and the identification of failed backups across your environment.
Rubrik's approach to Db2 data protection eliminates the traditional limitations and complexity that have long plagued database administrators. Rubrik provides the same streamlined protection experience whether your DB2 databases run on various operating systems like Windows and Linux, or across different platforms such as on-premises, AWS, and Azure. This deployment flexibility supports your evolving infrastructure strategy without changing your data protection approach. As organizations adopt hybrid and multi-cloud architectures, Rubrik's consistent protection model eliminates the need for environment-specific protection tools and processes.
Getting started is easy if you are ready to protect your IBM Db2 data! Check out our hands-on lab for the IBM Db2 Database and learn how to take the first step!
