It’s a challenge for any security-minded DBA: how do you identify exactly where sensitive data resides across Oracle and SQL Server environments without bringing the business to a halt?
Rubrik Data Discovery and Classification solves this problem by automatically mapping personally identifiable information (PII), financial records, healthcare data, and other sensitive records to specific database locations. This transforms security from guesswork to precision, enabling immediate response when exfiltration attempts or ransomware threats emerge.
For DBAs caught between security mandates and operational realities, Rubrik finally delivers the clarity needed to protect what matters most. Here’s how.
Stop Flying Blind
Let's face it: if you're managing Oracle or SQL Server databases, you're sitting on a goldmine of sensitive information. And while you're busy keeping those systems running smoothly, you're also on the hook to ensure all that data isn’t exposed to any security risks!
The problem? Your standard security logs are drowning you in noise while missing what actually matters. Did someone suddenly get privileges to access sensitive data? Is sensitive customer data quietly being copied to a dev environment or outside your organization? These changes are very hard to catch with native tools alone.
And when ransomware or targeted attacks hit, this visibility gap becomes catastrophic. Threat actors often focus on database environments because they understand that this is where the most valuable information is stored. Without a clear mapping of where PII, financial data, and sensitive data live across your database ecosystem, you can't properly prioritize protection or accurately assess breach impact.
On thop of that, you have to manage regulatory requirements from bodies such as GDPR, HIPAA, and CCPA, which impose stricter guidelines for monitoring access to and usage of sensitive data.
Uncovering Hidden Risks with Rubrik Data Discovery and Classification
This is where Rubrik Data Discovery and Classification comes in. It addresses these gaps by utilizing over 100 predefined sensitive data analyzers that target data mapped to GDPR, HIPAA, PII, and other regulatory standards.
With the rising threat of ransomware attacks and data breaches, it's more important than ever to have a proactive approach to data security. Rubrik Security Cloud (RSC) maintains a searchable catalog that maps sensitive data to specific database instances, schemas, tables, and columns. This provides database administrators with visibility into the locations of sensitive data without the need for additional agents, thereby reducing sensitive data exposure during any exfiltration attempt, including those associated with ransomware. Administrators can also create custom analyzers and policies tailored to their organization's specific needs.
Furthermore, role-based access controls ensure a clear separation between backup operations and security administration. And Rubrik's REST APIs facilitate integration with existing security tools and ticketing systems to streamline remediation workflows.
How Rubrik Data Discovery Works
Let’s take a look at how Rubrik performs sensitive data classification:
Step 1: Database Discovery and Policy Assignment
Once database hosts are onboarded to RSC, the platform automatically discovers all database instances using its built-in inventory capabilities. Database administrators can use the Data Security Posture Management (DSPM) application within RSC to assign one or more classification policies to each database. These pre-configured policies are designed for various regulatory frameworks, such as GLBA, HIPAA, etc., as well as for different data categories, including personal, financial, healthcare, etc. They define specific data patterns—such as credit card numbers, patient information, Social Security numbers, and bank routing numbers—that will be searched for.
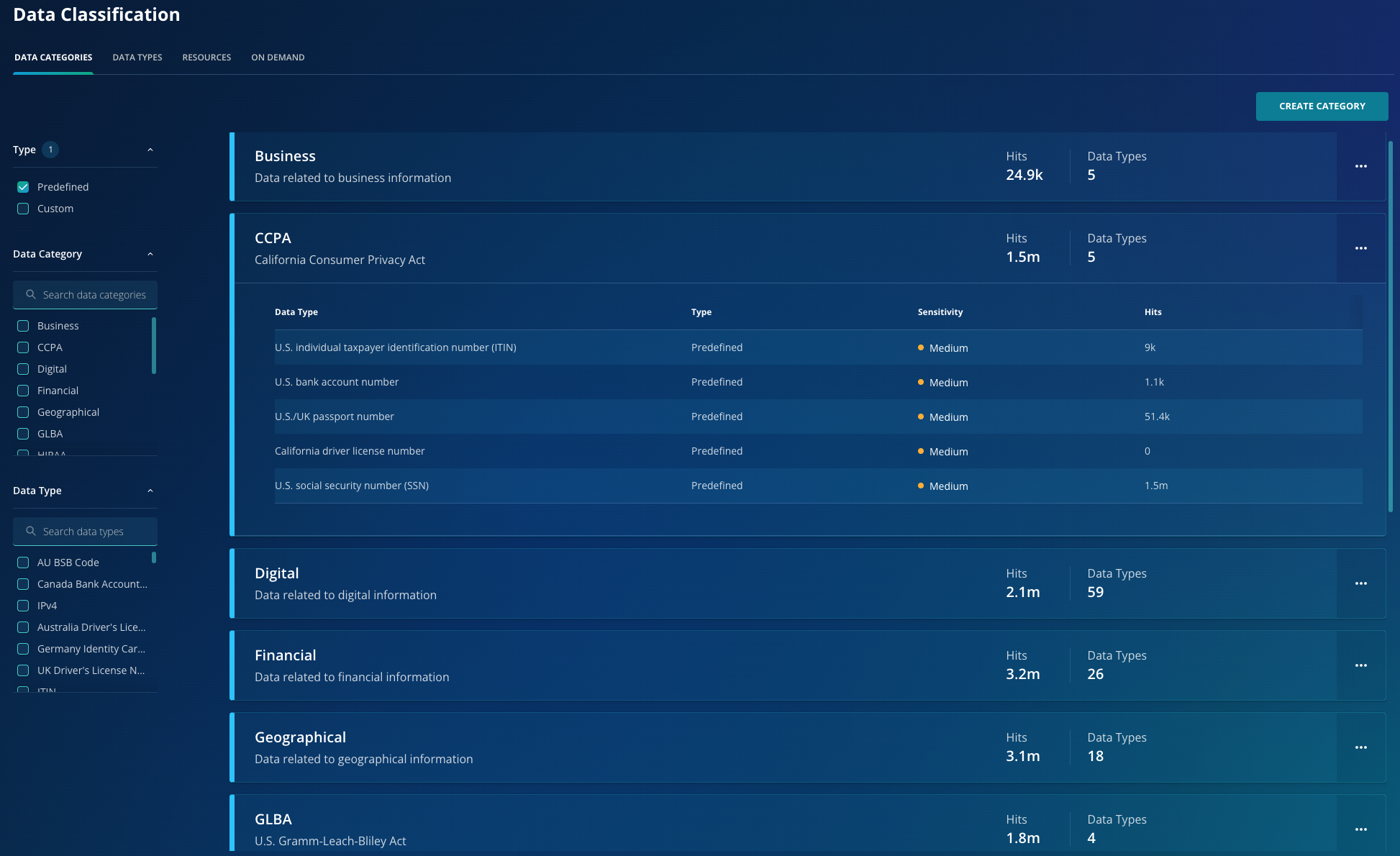
Step 2: Data Sampling & Data Classification
Rubrik's architecture effectively synchronizes sampling and classification operations with the scheduled backup process, removing the need for separate scanning windows. Once a database backup job is successfully completed, it automatically triggers a corresponding data sampling job on the Rubrik Secure Vault (RSV) cluster. This job extracts a small percentage of rows (approximately 1% of the total rows) from the live database.
The extracted data samples are then sent to Rubrik's classification engine, which operates entirely within the RSV. It is crucial to highlight that your data never leaves your data center. The classification engine performs its analysis according to the designated data policies, and only the classification results are subsequently uploaded to the RSC. The classification results contain only the metadata about the sensitive data and never your credit card, social number, or any other sensitive data.
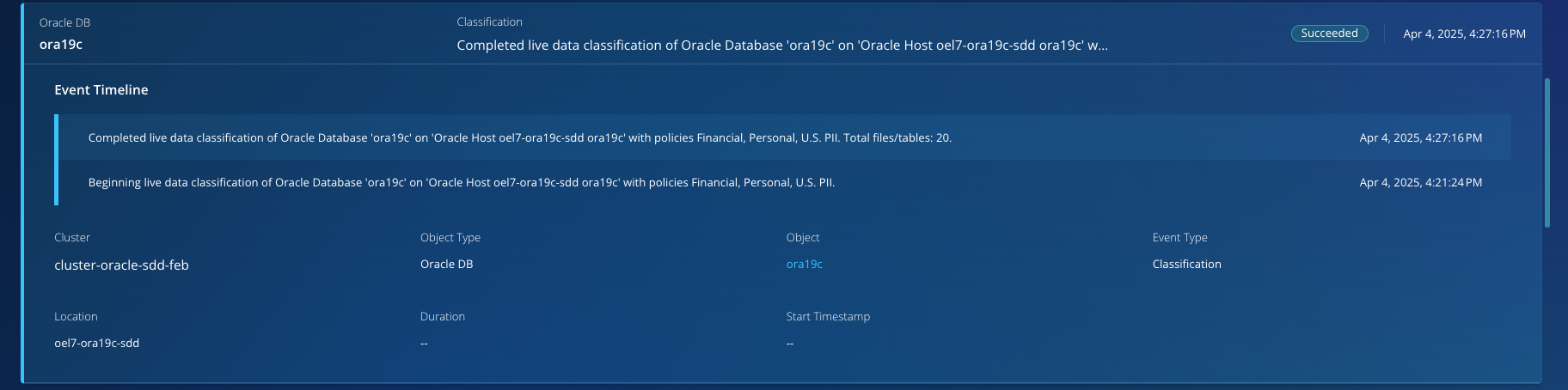
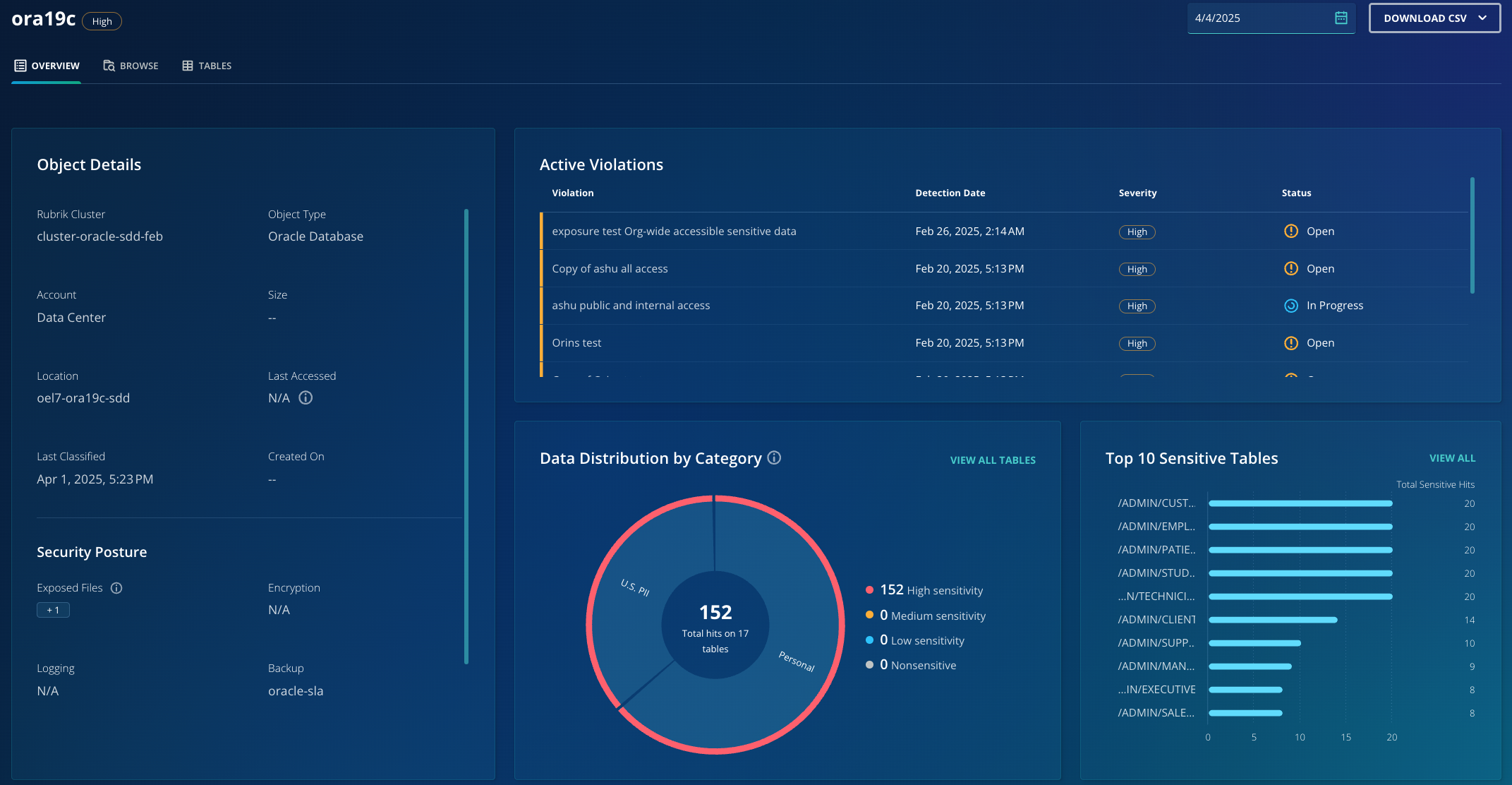
Step 3: Sensitive Data Analysis Results and Actionable Intelligence
Processed classification results become immediately available in the DSPM application within RSC. Database administrators gain access to comprehensive dashboards presenting actionable intelligence about sensitive data distribution across their environment. The dashboard provides detailed metrics on the number and types of sensitive data findings, lists affected tables and schemas with their sensitivity scores, and offers filtering capabilities to focus on specific databases, data types, or compliance frameworks. RSC maintains historical classification data to identify trends and changes in sensitive data distribution over time.
This visibility allows DBAs to establish targeted controls, remediation actions, and access policies based on accurate data sensitivity mapping, ensuring minimal exposure of sensitive data in the event of ransomware or cyberattacks.
Regain Control of Your Business-Critical Databases
Currently, Rubrik Data Discovery and Classification is available for Oracle and Microsoft SQL databases, providing three critical advantages for database management teams:
Automated Policy Enforcement: This feature allows organizations to streamline the identification and classification of sensitive data. Teams can efficiently ensure that sensitive information is recognized and protected using pre-defined templates or customized policies.
Data Exposure Identification: This proactive approach minimizes the risk of data breaches by knowing which databases contain sensitive data lives. This capability is essential for enhancing an organization’s security posture, as it allows for timely intervention and remediation before data loss or damage occurs.
Compliance Facilitation: Keeping track of the location and status of sensitive data is vital in today’s regulatory environment. Rubrik Data Discovery and Classification assists organizations in documenting data whereabouts, thereby simplifying compliance efforts with various data protection laws and industry standards. This helps ensure that all regulations are met and minimizes the risk of costly penalties due to non-compliance.
Ready to experience Rubrik Data Discovery and Classification firsthand? Access Rubrik Data Discovery and Classification for Oracle or Microsoft SQL hands-on lab to get started!
