Rubrik named a Leader for the 2nd time in the IDC MarketScape for Cyber Recovery 2025 Vendor Assessment.
Keep your cloud data and applications resilient against cyberattacks, malicious insiders, and operational disruption.
Back up Okta and recover cleanly from unwanted changes. Simplify identity management across IdPs and minimize downtime.
Unleash agents. Not risk.
Accelerate AI transformation and stay in control with Rubrik Agent Cloud.
AI is here. Are you ready?
Build your resilient foundation for the AI era
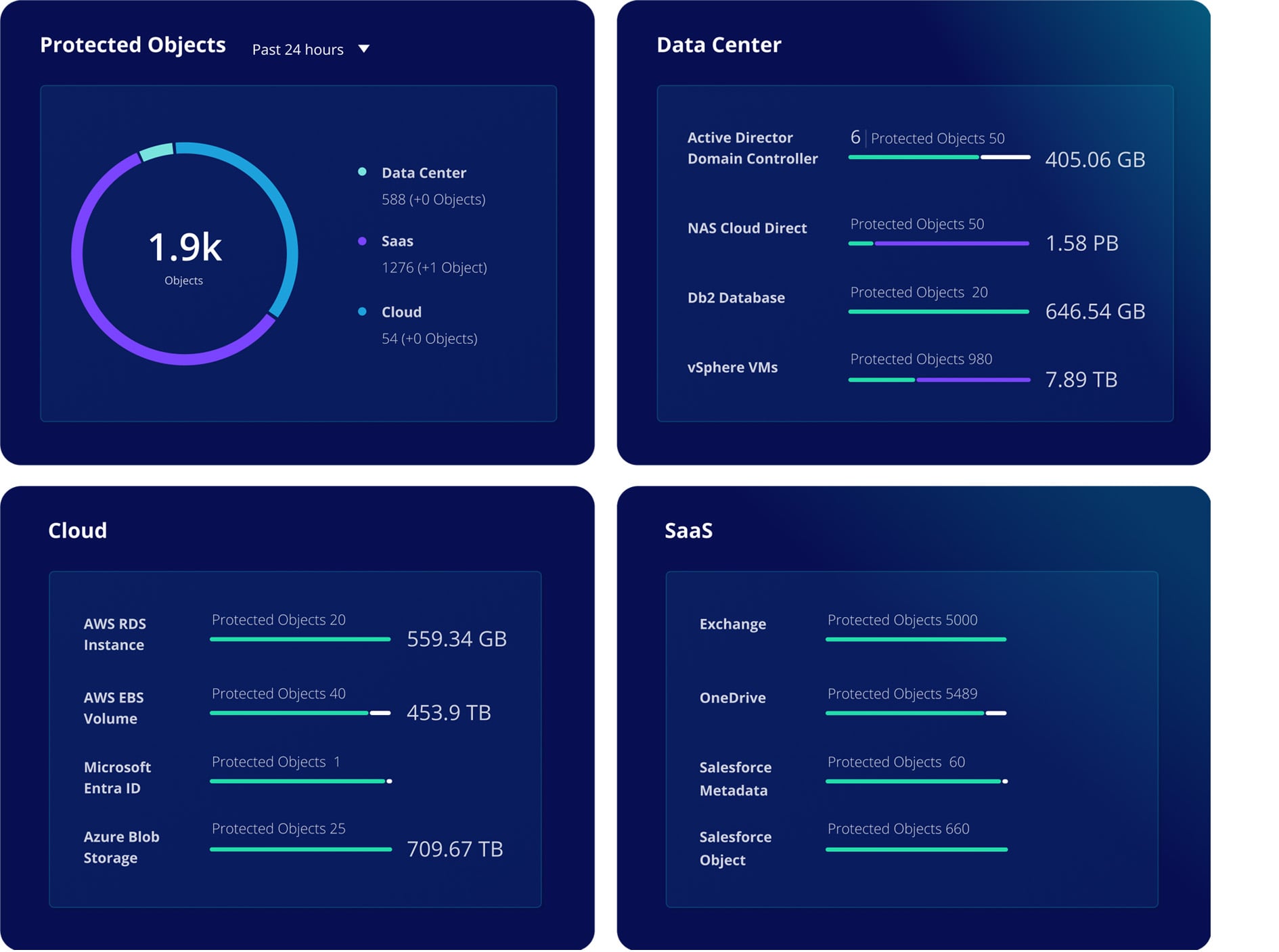
Secure your cloud data foundation
Withstand cyberattacks by maintaining secure backups of your on-premises, cloud, and SaaS data on a single platform.
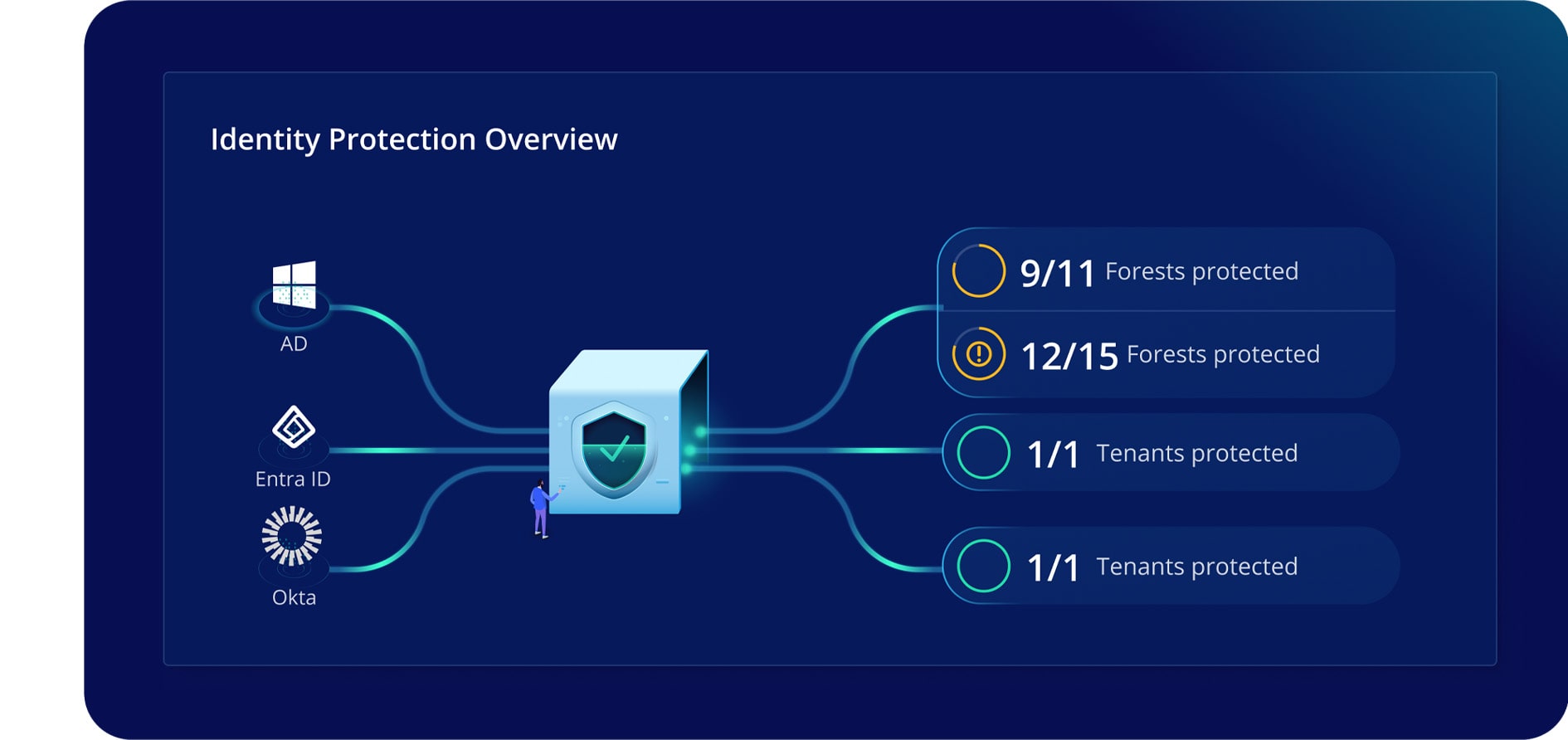
Protect identities from core to cloud
Secure identity systems – from AD to Entra ID and Okta – with visibility, continuous monitoring, attack rollback, and orchestrated identity recovery.
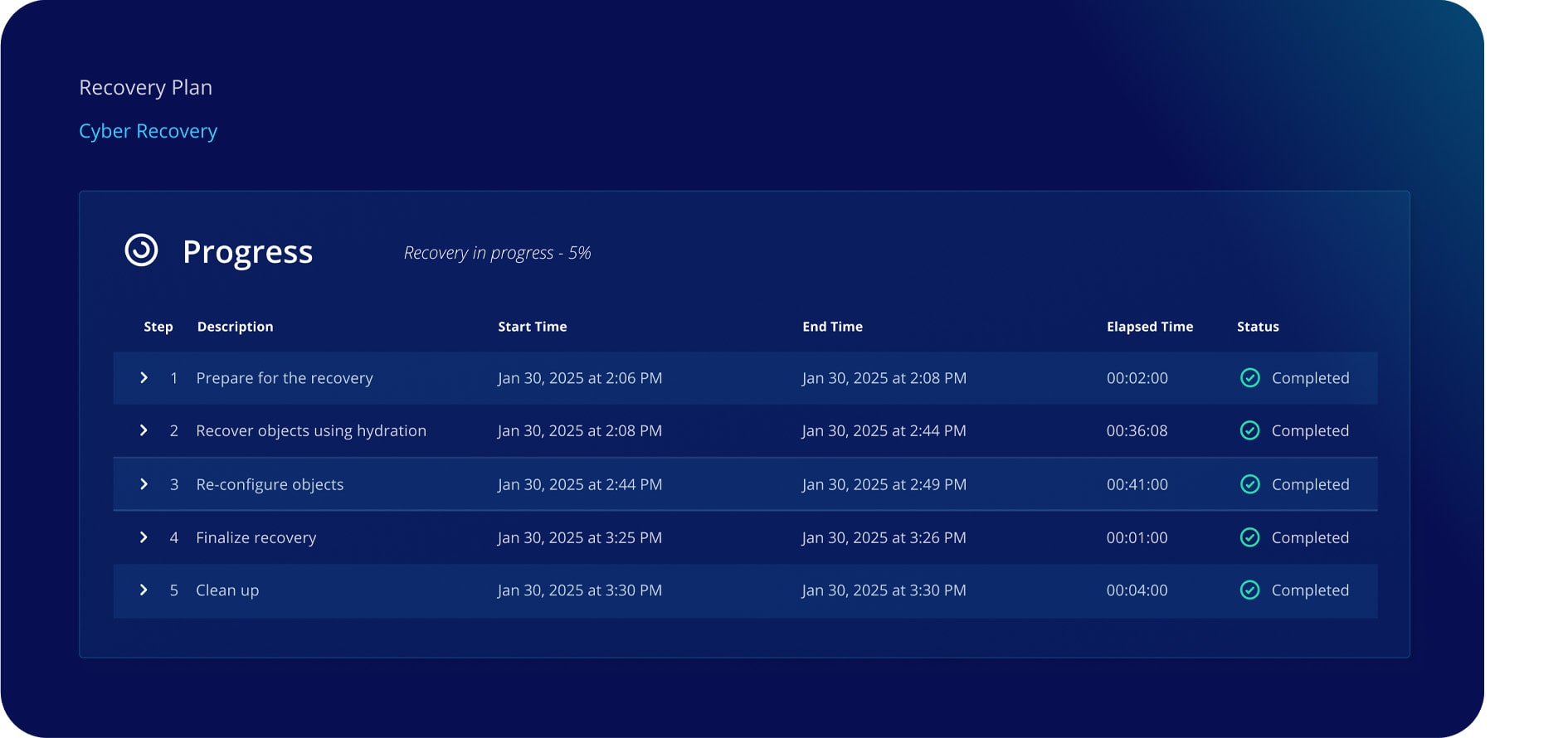
Rapidly restore to a clean state
Speed up and prove your fast cyber RTO. Bounce back from cyberattacks with minimal downtime and data loss.
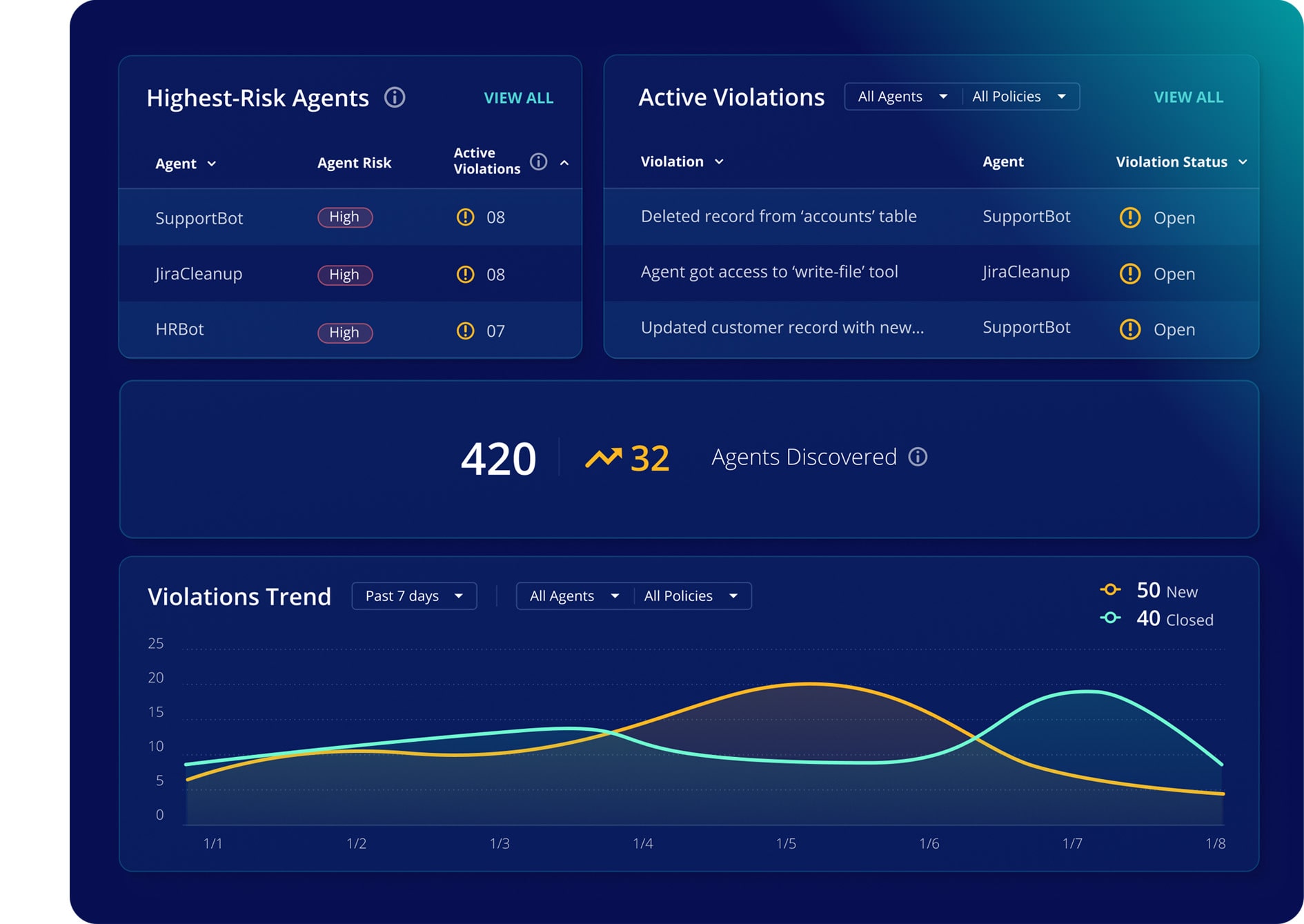
Accelerate your AI transformation
Monitor your agents, enforce guardrails, and remediate unwanted actions on one platform with Rubrik Agent Cloud.
Trusted by more than 6,000 leading organizations
Redefining cyber resilience














