Every business, organization, and enterprise relies upon IT governance to achieve its goals. IT governance intends to generate business value and mitigate IT risks. Security incidents, such as ransomware, jeopardize these strategic outcomes. Either by stealing sensitive data and threatening public exposure or crippling IT infrastructure, the threat of ransomware puts all data at risk, no matter where it resides.
The modern enterprise has applications and data that exist on many infrastructure platforms. They can live in the public cloud, SaaS, or in the traditional data center. Each with its point objectives and recovery time objectives (RPO/RTO). To complicate the task further, sensitive data has its own set of complex regulations. They dictate the use, collection, and storage of specific data.
The topic of data protection sounds complicated - because it is. Administrators are often tasked with managing and maintaining hundreds of individual backup jobs. Often interdependent, they create a proverbial house of cards - when one fails, it has a cascading effect. The need for an automated and policy-based approach to data protection is clear. One that uses software to determine the best approach to meeting data protection requirements.
Automate Data Protection
This policy-based approach is a core function in Rubrik Zero Trust Data Security™. An SLA Domain Policy translates data protection requirements in a simple workflow. This workflow abstracts away the complex backup job creation, tuning, and scheduling. It includes key requirements such as RPO, retention, replication, and archival. When applied to a workload, the Rubrik software translates the SLA into system tasks. These tasks are then delegated to the necessary platforms in Rubrik to meet a given SLA. An SLA is also agnostic, and a single policy can protect a diverse set of applications and data.
Let’s take a look at how we can create an SLA policy in Polaris. From the SLA Domains page, we click on the Create SLA Domain button:
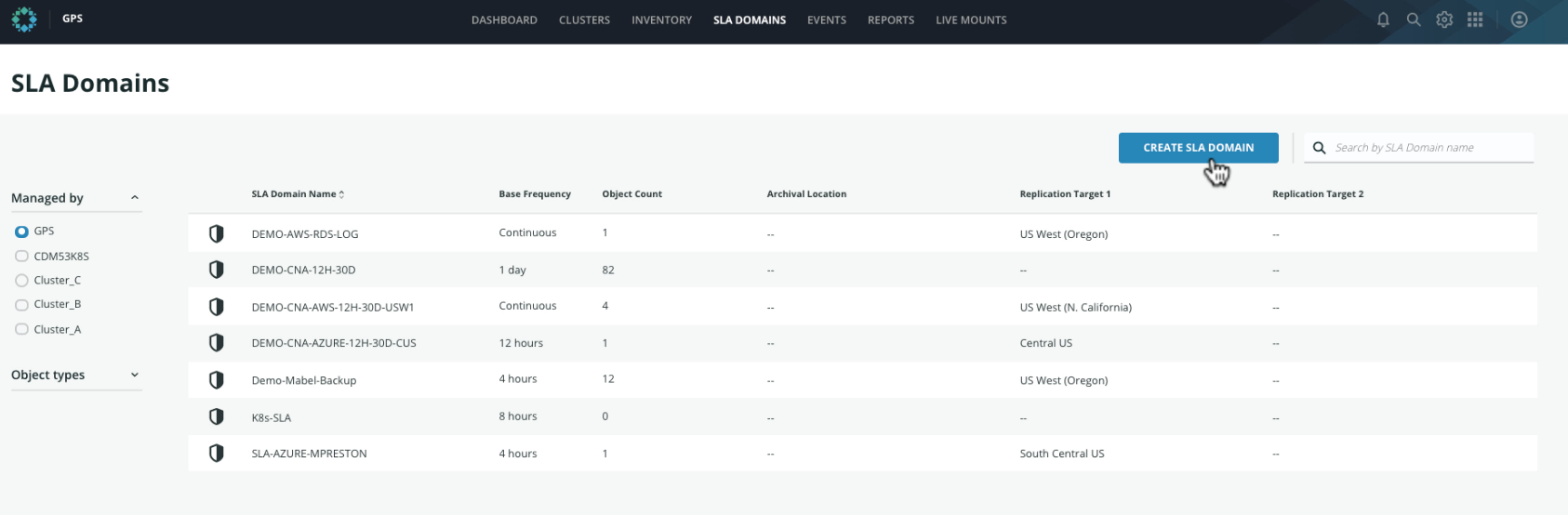
We select the workloads to protect:
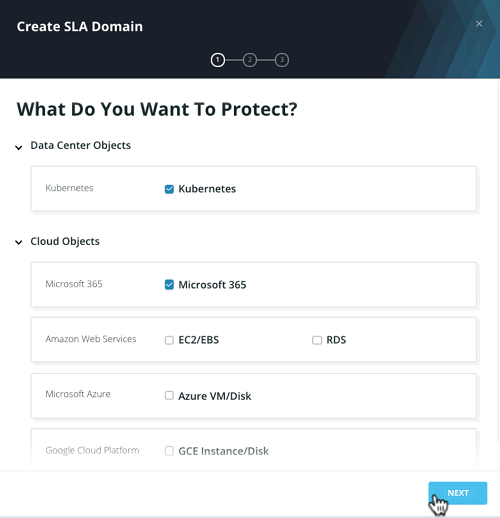
Provide the frequency and retention to define the recovery point objective:
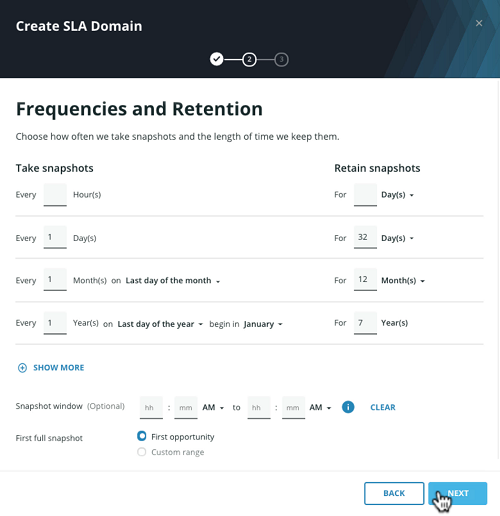
And give it a common name:
Another key aspect of an SLA is the monitoring and reporting of data protection tasks. It has two potential outcomes: in compliance or out of compliance. This matches the binary nature of data regulation and simplifies the audit process. Additionally, it consolidates the reporting of data protection across the environment. On a day-to-day basis, an administrator can receive notifications, or log in to the system to view the status. This is a welcomed change from the duties of collating individual job success or cloud environments, which only introduces further risk.
Centrally Govern IT Assets
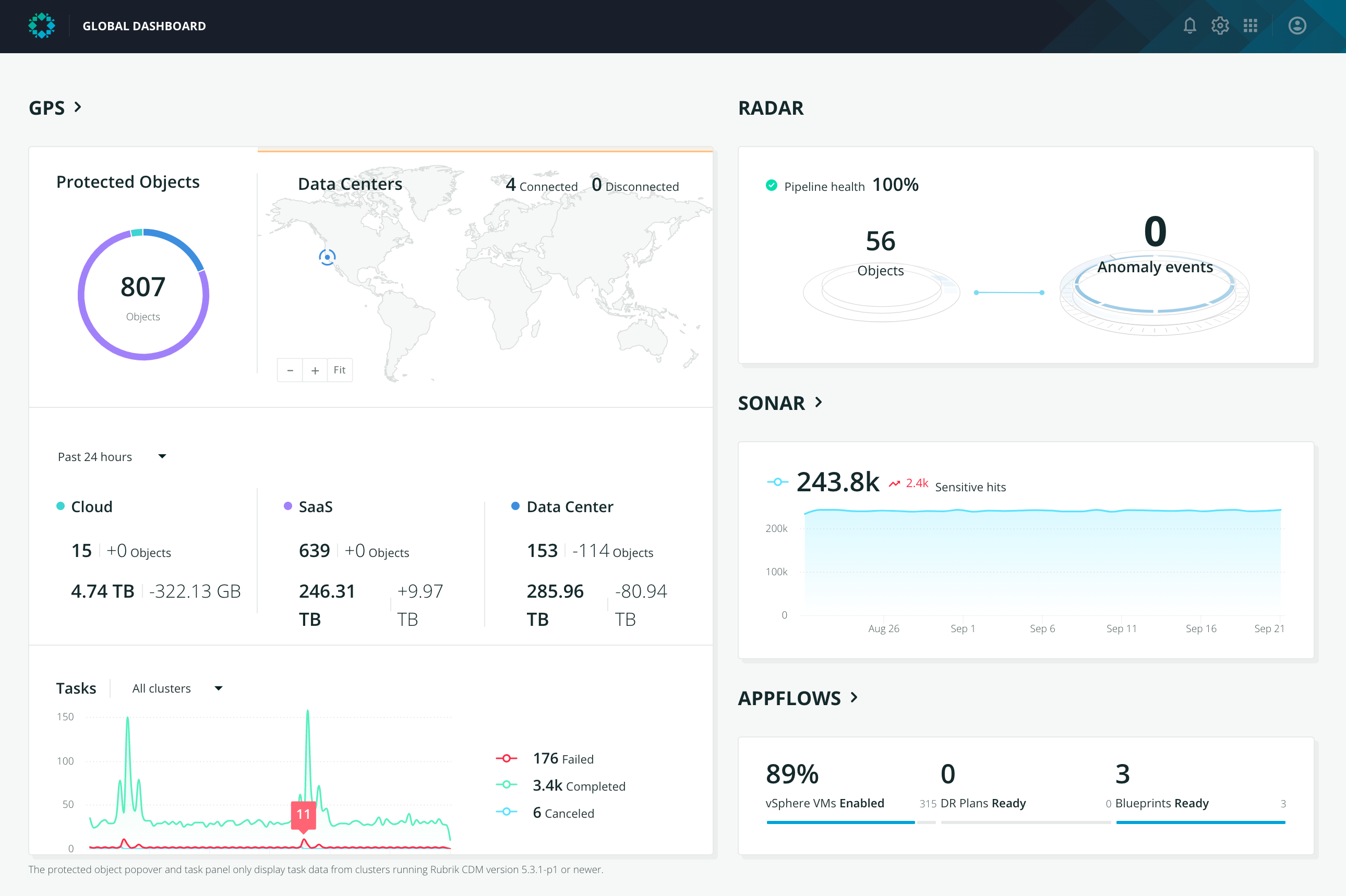
The scope of data protection and compliance has exploded alongside cloud adoption. One with an increased risk of missing workloads or not meeting data regulations. This creates a gap in data protection and poses a serious IT risk that needs mitigation. Rubrik recognized this, and three years ago, launched a SaaS application called Rubrik Polaris GPS.
GPS can connect an entire Rubrik deployment that spans an enterprise. This could be Rubrik in the traditional data center or in cloud instances. It uses Rubrik APIs and secured channels to communicate and transfer information. As a result, GPS becomes a centralized control plane for the administrator. From here, they can globally manage their entire data protection strategy. It also extends key capabilities, such as SLA policy, RBAC, monitoring, and reporting.
Ransomware can halt your business operations, threaten business objectives, and multiply IT risks. Administrators and IT teams need to rethink their data management strategy to combat this imminent threat. Only this way can you meet your business goals while ensuring data protection, facilitating compliance, and providing an effective path for recovery.
Learn more about Rubrik Polaris, and other SaaS offerings here.

