When organizations are attacked by ransomware, only a little more than half are able to recover their data using a backup. This begs the question, “What about the rest? Why might they be unable to recover?”
One reason may be that their backup data has been compromised. Backups are a hot target for hackers. If they can get to an organization’s backup data, they have far more leverage. The data in backups are essentially the keys to the kingdom–and potentially extremely profitable, with victims more likely to pay top dollar in the event they are compromised.
What can boost your preparedness in the fight against ransomware is a layer of protection specifically built to keep your backup data safe. Following the principles of the Zero Trust framework, a secure data layer helps prevent exposure to untrusted users and guards against malicious data encryption, modification, or deletion.
The Rubrik Secure Data Layer is part of Rubrik Zero Trust Data Security™ architecture, built to keep your backup data available, and provides:
Encryption at rest and in-flight to help prevent data exposure
An append-only, immutable file system to make sure data is never changed
A self-healing design with fault tolerance to keep data continuously available
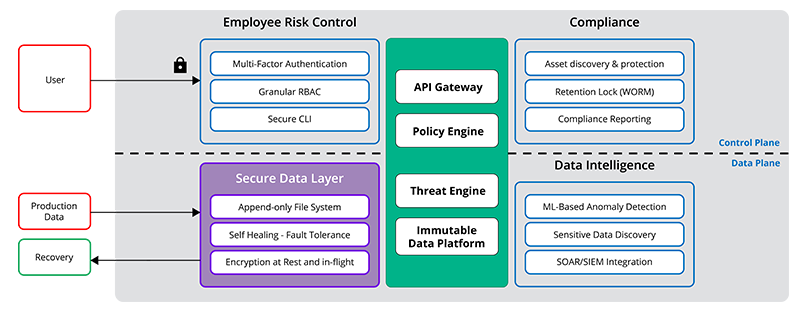
Let’s dive deeper into each of these Secure Data Layer components of the Rubrik Zero Trust model.
Encryption at Rest and In-Flight
With Rubrik, data is encrypted in-flight and at rest. In-flight encryption is critical for a data management solution such as Rubrik when it moves data around supporting long-term archival and replication. Thus, any requests made to the Rubrik platform, either through the UI or a RESTful API endpoint, must be authenticated and authorized as well as fully encrypted via industry-standard HTTPS/TLS (TLS 1.2+) during the transfer. In this way, all traffic between not only customer environments and Rubrik but also to third-party systems (as in the case of archival to public cloud storage providers) is secure during transit.
Rubrik also encrypts data when it is written to the system. Rubrik uses AES (Advanced Encryption Standard) encryption to protect all customer data in the Rubrik file system, including metadata, logs, and generated stats. AES is the first and only publicly accessible cipher approved by the US National Security Agency (NSA) for protecting top-secret information. As an extra measure of security, Rubrik chooses to use AES-256 bit encryption.
As an additional layer of protection, Rubrik offers optional self-encrypting drives (SED), a capability that is particularly important for sectors such as financial services. Rather than Rubrik performing the encryption of the data within the software, self-encrypting drives utilize drive firmware to perform the encryption. Each self-encrypting drive utilizes a password in order to generate a one-time-only Data Encryption Key (DEK).
Rubrik systems are also FIPS 140-2 Level 2 certified, and Rubrik appliances have a built-in Trusted Platform Module (TPM) chip that is used to generate, store, and protect encryption keys that can unlock encrypted drives.
Overall, the combination of data encryption in-flight between sites or clouds and encryption at rest helps provide peace of mind that your data is secure and protected wherever it lives. Your data is never exposed to untrusted users.
Append-Only File System
Unlike other services built on standard, open file systems where the data is susceptible to changes (and potential malicious manipulation), Rubrik took a different approach. The Rubrik append-only, immutable file system–where ingested applications and data cannot be modified by external or internal operations–is combined with a Zero Trust design. The default approach is to deny access, and operations can only be performed through authenticated APIs. IT teams can quickly restore to the most recent clean state with minimal business disruption.
The proprietary Rubrik distributed file system ensures availability by utilizing several purpose-built methods for writing data to disk and for handling hardware failures.
Writing Data to Disk
The Rubrik file system is application-aware and understands that it stores snapshot chains used by the Rubrik data management engine. This awareness allows Rubrik to know the captured data snapshots are immutable. When data is written to disk, the append-only file system permits data to be added to a file but never deleted.
Data integrity check methods are performed throughout the data lifecycle to ensure that data is never modified. As data enters the system, Rubrik creates checksums to protect against physical disks not providing absolute data integrity. Checksums–so named as they are always checking to make sure nothing has changed–refer to a compact signature of a larger piece of data that can be used to verify its integrity. Cyclic Redundancy Checks (CRCs) first validate that nothing has changed in the background, and then also validate the read path as well. Rubrik essentially utilizes checksums to ensure the data you are restoring is the same data you backed up. If Rubrik ever sees an anomaly, it can simply be thrown away, letting the system replicate.
Automatic Self-Healing and Fault Tolerance
Masterless, Self-Healing Scalability
An important point to consider with your data management solution is “What happens if I lose a node?” What’s more, “How do I make sure I don’t lose data because of it?” Unless the cluster re-replicates data, data may be lost or not kept in a secure state.
The Rubrik file system was designed specifically to store and track multiple versions of data. It employs a masterless shared-nothing architecture, eliminating bottlenecks and single points of failure. It is also built to be web-scale, scaling linearly with the number of nodes added, with cluster operations self-healing in a way that no one node is a master in a cluster, permanently assigned to manage tasks across the cluster. Therefore, if one node goes down, the masterless system ensures that the remaining nodes select a leader and keep going. In this way, you will always have a recoverable copy of your data.
In the event of a ransomware attack, the Rubrik ransomware recovery application can identify where files and applications were encrypted and then roll back to the last known good snapshot. You can be confident that the snapshot written to the file system has not been changed, therefore more confidently restoring a clean state without ransomware.
Handling Hardware Failure
When it comes to handling hardware failure, it’s crucial to ensure that you’re storing data on a fault-tolerant and distributed file system so that you always have a clean, available backup. If cluster hardware such as disk drives or other components degrade or fail within the cluster, the system will notice that something has gone wrong and re-replicate, redistributing data to prevent data loss.
In the case of a hardware or disk failure, automatic, self-healing mechanisms kick in and intelligently rebuild data sets on available disks. Even when a cluster node fails, the web-scale design reduces the probability of simultaneous node failures in large, distributed systems. Prior to failed disks being replaced, the cluster is also tolerant to additional failures, provided sufficient capacity exists. When failed disks are eventually replaced, that capacity is automatically added back into the system, and data is rebalanced.
Fault Tolerance
The way to achieve fault tolerance is through redundancy, which refers to storing extra information about the data across different drives to allow for complete recovery in the event of a failure. The more redundancy added, the greater the fault tolerance. However, the cost of redundancy is increased storage overhead. Every file system needs to make this tradeoff between availability and overhead. The Rubrik approach is to leverage a technique called erasure coding that addresses the tradeoff between storage redundancy overhead and availability. Erasure coding stores redundant pieces of data in a way that ensures full recoverability from storage device failures.
In considering your own security posture, think of it this way: If you were to be attacked by ransomware, what changes would you inevitably make to your backup and recovery operations in hindsight? Remember that if the right Zero Trust principles are in place, including a secure data layer, hackers lose the leverage they need to get you to pay the ransom. You’ll find the best course of action is to proactively implement those security protocols now before an attack actually takes place.
For more information and an inside look into Rubrik’s overall approach to ransomware remediation, including the steps to detection, isolation, and recovery, check out the whitepaper Lessons Learned: Recovering From Ransomware.
