Rubrik customers have an advantage when it comes to mitigating the log4j crisis. Utilizing our API-first architecture, Rubrik customers can make a single API call to find instances of log4j across their protected systems.
curl example:
curl -X POST "<CDM HOST>/api/internal/search/global" -H "accept: application/json" -H "Authorization: Bearer <API TOKEN>" -H "Content-Type: application/json" -d "{ \"regex\": \"log4j-core\"}"
Python example (using the Rubrik CDM Python SDK):
import rubrik_cdm
r = rubrik_cdm.Connect(“CDM HOST”, “API TOKEN”)
body = {}
body['regex'] = "log4j-core"
r.post("internal", '/search/global', body)
PowerShell Example (using the Rubrik PowerShell module):
Connect-Rubrik <CDM_HOST> -token <API TOKEN>
Invoke-RubrikRESTCall -uri "https://<CDM HOST>/api/internal/search/global"-method POST -Body @{"regex" = "log4j-core"}
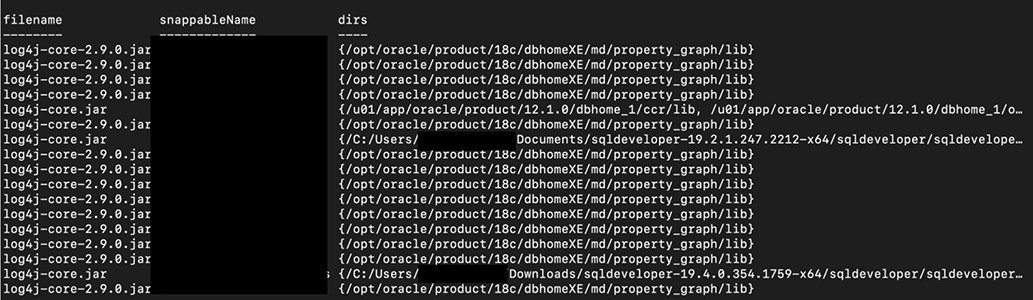
Here’s my output from PowerShell, showing the filename, object, and the path to the file. My next step is to remediate if necessary and/or contact the owners of these VMs!
For more information on the log4j exploit and how to remediate, refer to the CISA vulnerability guidance page.
