You run many of your business-critical applications on Nutanix AHV. Protecting your data from cyberattacks and being able to quickly restore your applications, so your business can continue as usual. This is why, at Rubrik, we continue to innovate and expand protection for virtual environments, and we are humbled and proud to be a trusted partner when it comes to protecting businesses.
Earlier this year, we announced the Live Mount capability for Nutanix AHV. This proven method for recovery has long been available for vSphere and Hyper-V environments, and now you can use the familiar steps to quickly restore your Nutanix AHV virtual machines. When you use Live Mount, the Rubrik platform is exported to the Nutanix environment as an NFS mount, and the VM backups themselves are transformed and mounted as a VM within AHV. This helps to eliminate long wait times as no data needs to traverse the network prior to powering on the restored VM. Depending on your use case, you may wish to keep the VM on the Rubrik appliance (if your need is short-term, maybe testing an upgrade), or migrate the VM back to the Nutanix datastore if more long-term.
Rubrik is enabling customers to minimize backup duration, maximize storage efficiency, enhance data security, and have more granular backups of their Nutanix AHV environments. Namely:
Exclude disks to backup Nutanix AHV faster
For VM backups, you can now select the individual disks to exclude at a granular level, in a similar way you do it for VMware and Hyper-V protection. Thus you are able to quickly protect only the critical and needed pieces, backups are complete in a much shorter time, and you save space on your backup storage. Bottom line–you get more efficiency, with better storage utilization, and quite likely, the bandwidth to search for unprotected loads and bring them into the fold, so you can really keep that business secure.

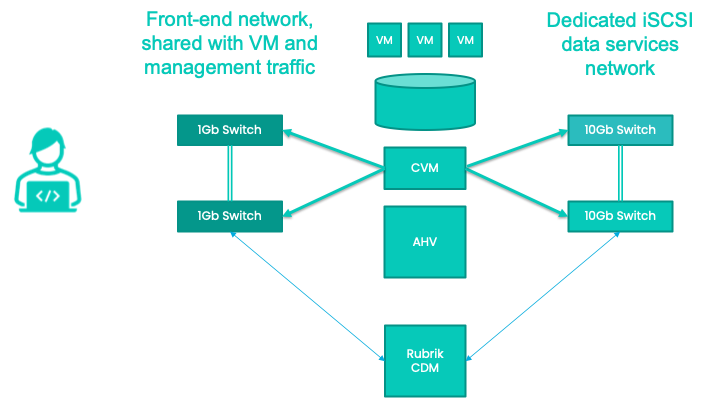
Separate backup traffic and optimize network bandwidth
You know by now that the criminals may go after your backups. We now enable you to send your entire AHV backup connectivity over a separate iSCSI Data Services network. If you take advantage of this option, the backup traffic will pass over a dedicated physical network, which you can lock away with appropriate security measures, thus isolating it from your main connectivity traffic for an extra security layer. As an added benefit, you also reduce your network resources and optimize network bandwidth.
We urge you to take advantage of those latest capabilities. Please remember to check our What’s new page for the latest product updates.
