Rubrik Security Cloud
Cyber Resilience Platform for Immutable Backups, Identity Security, and Rapid Recovery
The place to turn to bounce back from cyberattacks. Bringing together IT and Security teams to mitigate the risk and minimize the impact of cyberattacks. Arming CISOs and CIOs to demonstrate cyber resilience to the board.
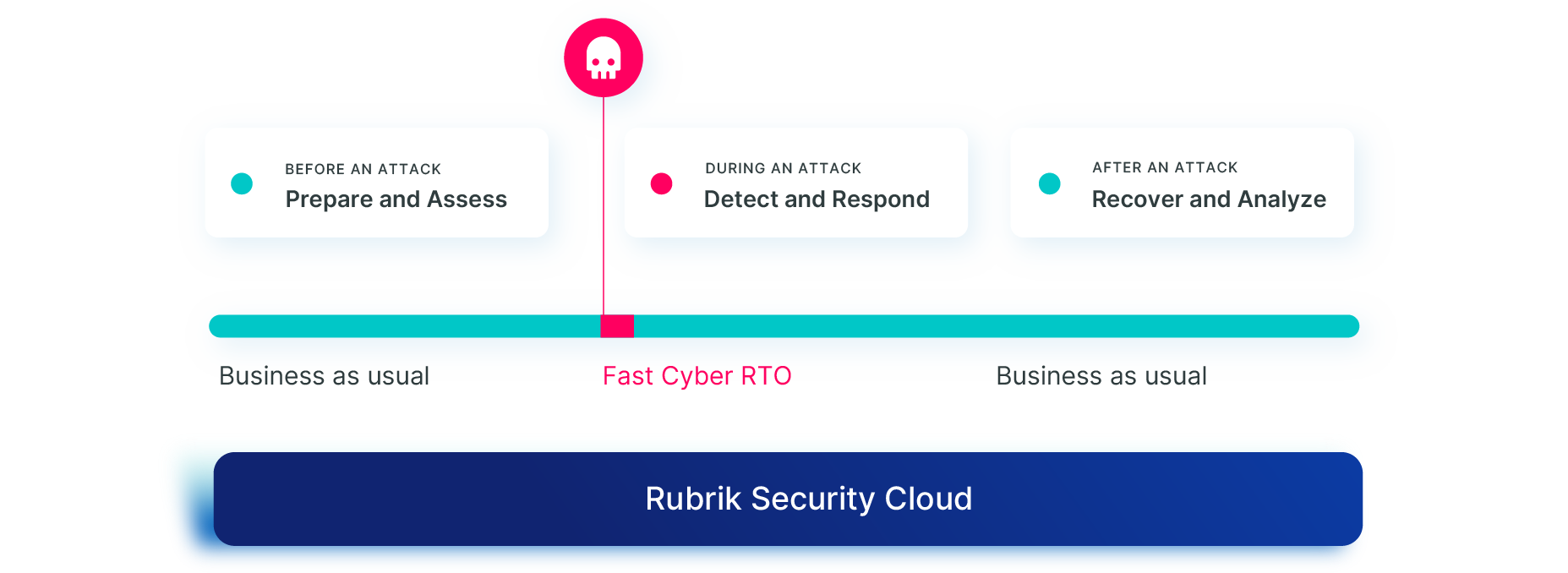
The path to business continuity
In the aftermath of a cyberattack, every minute of downtime can cause lost revenue, damaged reputation, and regulatory fines.
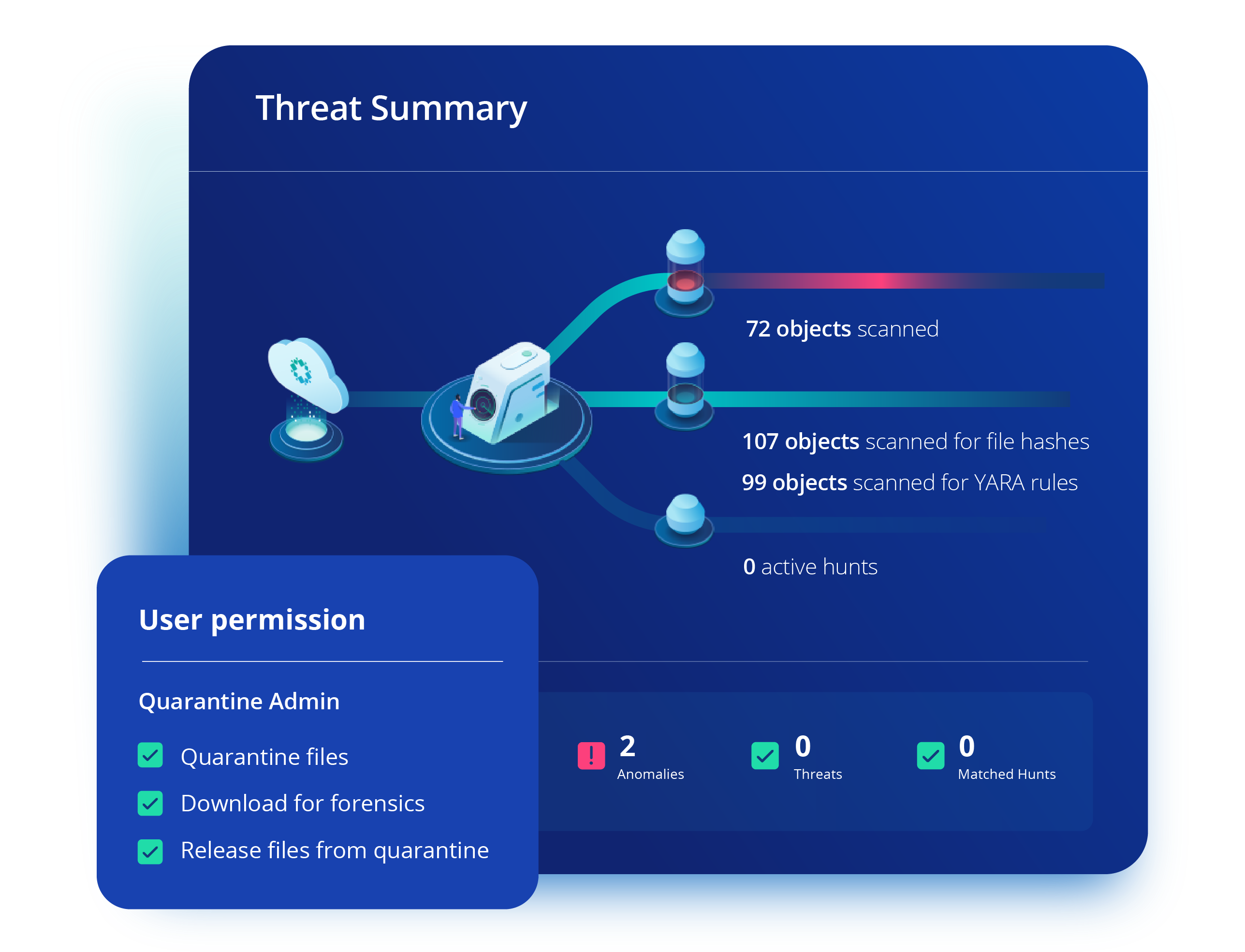
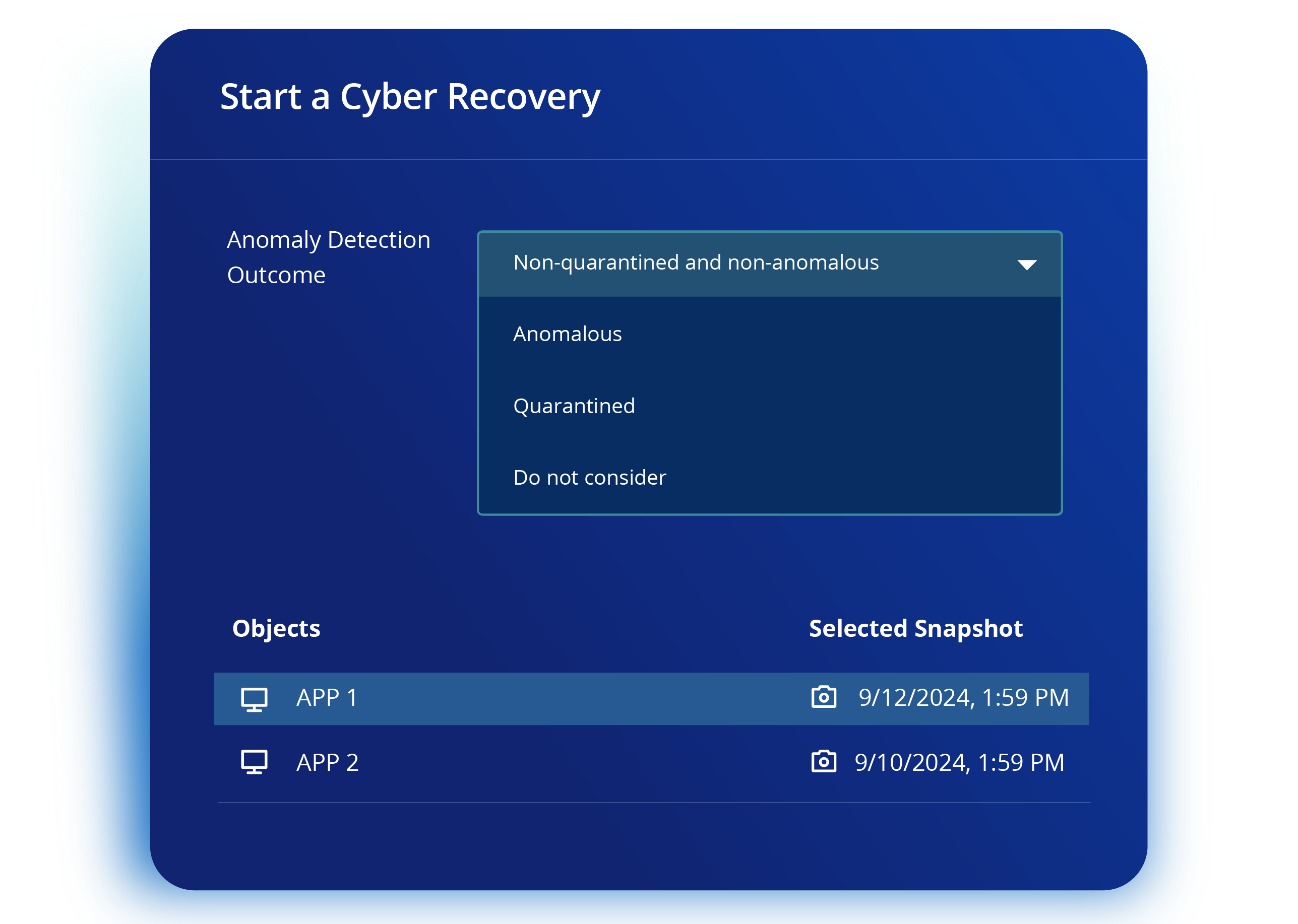
The difference between chaos and control lies in preparedness and collaboration. Can your IT team find clean data copies? Can your Security team assess the blast radius? Can they recover all enterprise, Cloud, and Saas data? Can they reduce reinfection risks?
If the answer is "no" or even a "maybe" to any of these questions, you're unprepared. It's time to bring cyber resilience into your cybersecurity strategy.
Leave nothing to chance
Know exactly what to do before, during, and after an attack
Unified effort to maintain business continuity amid cyberattacks

For IT & Cloud Teams

For Security Teams
For Compliance Teams

For CISOs & CIOs
Eliminate silos and disparate systems
Unified platform to go from preparation to detection to recovery, for enterprise, cloud, and SaaS data
Plug cyber resilience into your cybersecurity stack
How will you respond?
While the next cyberattack is unpredictable, your response doesn't have to be.
As someone responsible for maintaining operational continuity, it's crucial to have a strategic response plan in place.
Knowing what you know about cyber threats, what will your response be?