As the attack surface widens and cybercriminals get more sophisticated, organizations are struggling to prepare for and respond to ransomware and other cyber incidents. According to the inaugural State of Data Security report from Rubrik Zero Labs, a staggering 92% of global IT and security leaders are concerned they are unable to maintain business continuity following an attack. In addition, the report found that a third of boards have little-to-no confidence in their organization’s ability to recover critical data and business applications in the event of a cyberattack.
As a result, executives and boards are increasingly asking two questions to their IT and security teams: “Are we sufficiently prepared to respond to a large-scale cyber attack?'' and “How quickly can we get our business back up and running if we were attacked?” Most organizations don’t often have the answers to these questions until a security breach occurs.
Relying solely on a reactive cybersecurity approach can result in serious financial and reputational damage, so organizations need a way to take the uncertainty out of cyber recovery.
The Challenges with Traditional Disaster Recovery Solutions
When critical data is compromised during a cyberattack, the speed and effectiveness of that recovery can have dire consequences for the organization. To recover quickly and mitigate the damage caused by an attack, organizations should design and implement proactive approaches to cyber recovery. The challenge for many organizations is they’re using traditional disaster recovery (DR) solutions that were designed to protect from natural disasters, such as floods, and not from cyber attacks. Using traditional DR tools for cyber recovery presents the following challenges:
Traditional DR tools that lack threat detection capabilities can contribute to an inefficient and time-consuming process to identify the last-known clean point-in-time before recovery can take place to production. IT teams are left with no choice but to play a guessing game amongst thousands of recovery points and manually test and validate whether each of those recovery points is clean.
Traditional DR tools that don’t offer a simple way to frequently test and validate cyber recovery plans and track success and performance metrics from those tests, present the risk of extending business downtime in the event of a cyberattack.
The tools typically require pre-defined recovery plans, but cyberattacks are unpredictable and require the flexibility to do both ad-hoc and planned recoveries.
A common DR design assumes that the primary site is down, so the focus is on mass recovery from one site to another, but most cyber recoveries only need to recover a subset of the infected objects or applications locally since the site is still intact.
In the event of an attack, traditional DR tools may not offer the flexibility to perform forensics in parallel with recovery, which results in production systems remaining offline until the investigation is complete.
Imagine if you had an easy way to create, test, validate, and measure the success of your cyber recovery playbook. Imagine if you had a sandbox environment where you could easily conduct your cyber investigations and assessments.
Introducing Rubrik Cyber Recovery
To address the above challenges, Rubrik is announcing Rubrik Cyber Recovery to enable easy recovery testing and validation in isolated environments and help organizations improve their cyber readiness and incident response. Rubrik Cyber Recovery orchestrates end-to-end cyber recovery workflows and enables IT and security teams to do the following:
Test and Validate Cyber Recovery Playbooks: Today, we are seeing that most organizations are reacting to cyber attacks rather than taking a proactive approach. This makes it difficult for IT teams to create, test, and validate predefined cyber recovery plans and to track the success and performance from those tests. This can result in increased downtime from lack of predefined or poorly tested recovery plans. Rubrik Cyber Recovery helps organizations meet their recovery SLAs by easily creating, testing, and validating their cyber recovery plans, including the sequence, timing, and potential failure points. Customers can launch end-to-end cyber recovery workflows from Rubrik Security Cloud. They can then monitor recovery progress, track performance metrics, and download reports about recovery performance on demand to prove that regular testing of cyber recovery capabilities is taking place.
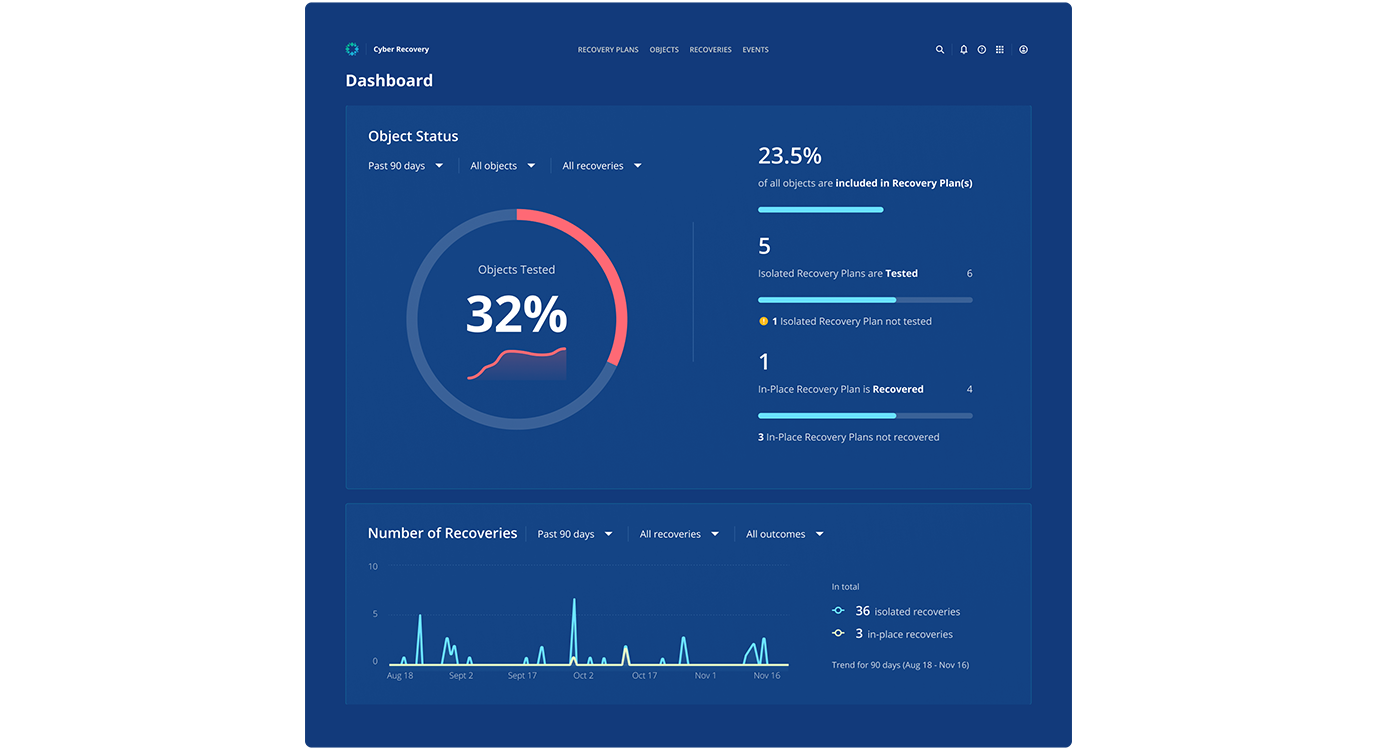
Figure 1: Cyber Recovery dashboard present insights from recovery tests
Clone Backup Snapshots For Faster Security Testing: Organizations today either go through manual, complex processes to build sandboxes to conduct regular cyber readiness tests, or they perform these tests directly in their production environments. This leads to increased downtime from insufficient testing and management of vulnerabilities. Rubrik Cyber Recovery enables organizations to assess and improve their cyber readiness faster by quickly cloning snapshots into isolated environments. It can clone infected snapshots that are identified and quarantined by Rubrik Ransomware Investigation and Threat Containment solutions for deeper testing and assessments. Security teams can then conduct cyber readiness testing even more frequently and run intrusive security exercises, such as penetration tests, vulnerability remediation or red team exercises using their own security tools, without any impact to production environments.
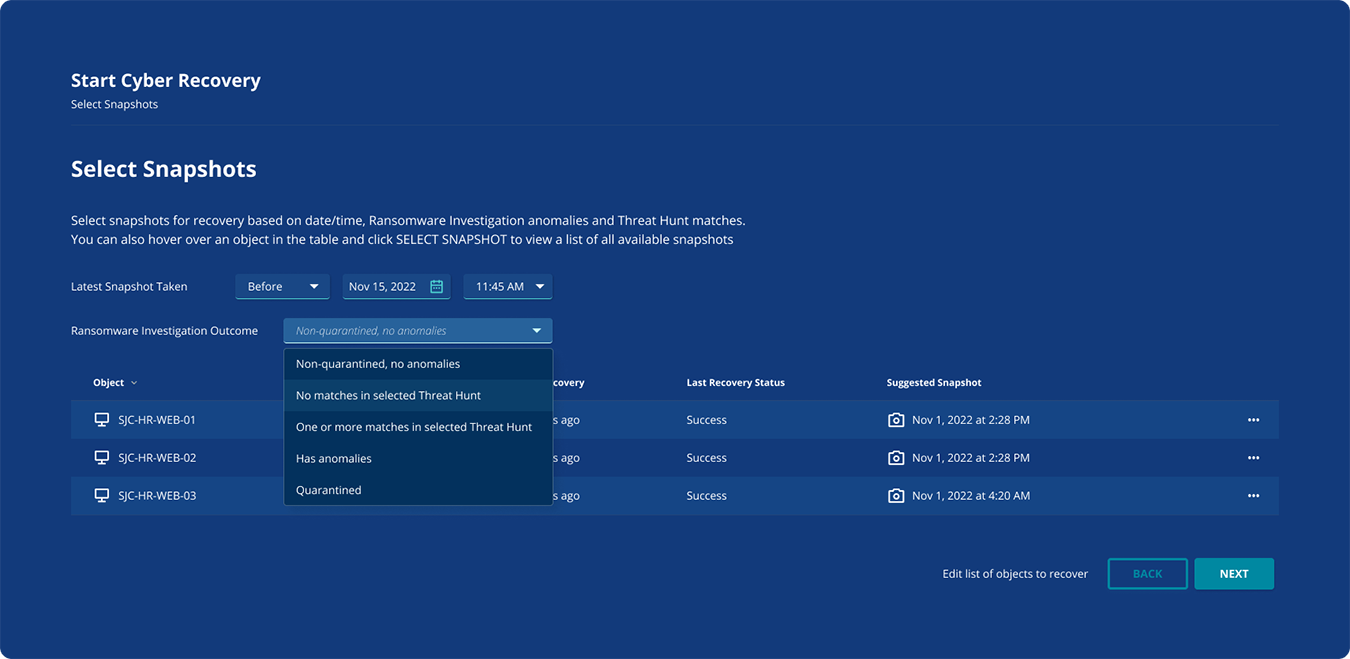
Figure 2: Recovery point selection to clone snapshots to an isolated environment
Conduct Forensic Investigations in Parallel to Recovery: When an attack happens, organizations often conduct their post-attack forensic investigations directly in production environments, and they risk extending recovery and business downtime. As a result, businesses are often forced to choose between meeting their speedy recovery objectives or ensuring that they can prevent reinfection of production workloads. Rubrik Cyber Recovery solves this problem by enabling out-of-band investigations in isolated recovery environments while organizations work on restoring their business operations. Rubrik uses live mount technology to quickly clone backup data into isolated recovery environments where organizations can easily conduct forensic investigations. In parallel with conducting forensic investigations, IT teams can restore their business operations using a safe recovery point suggested by Rubrik Ransomware Investigation.
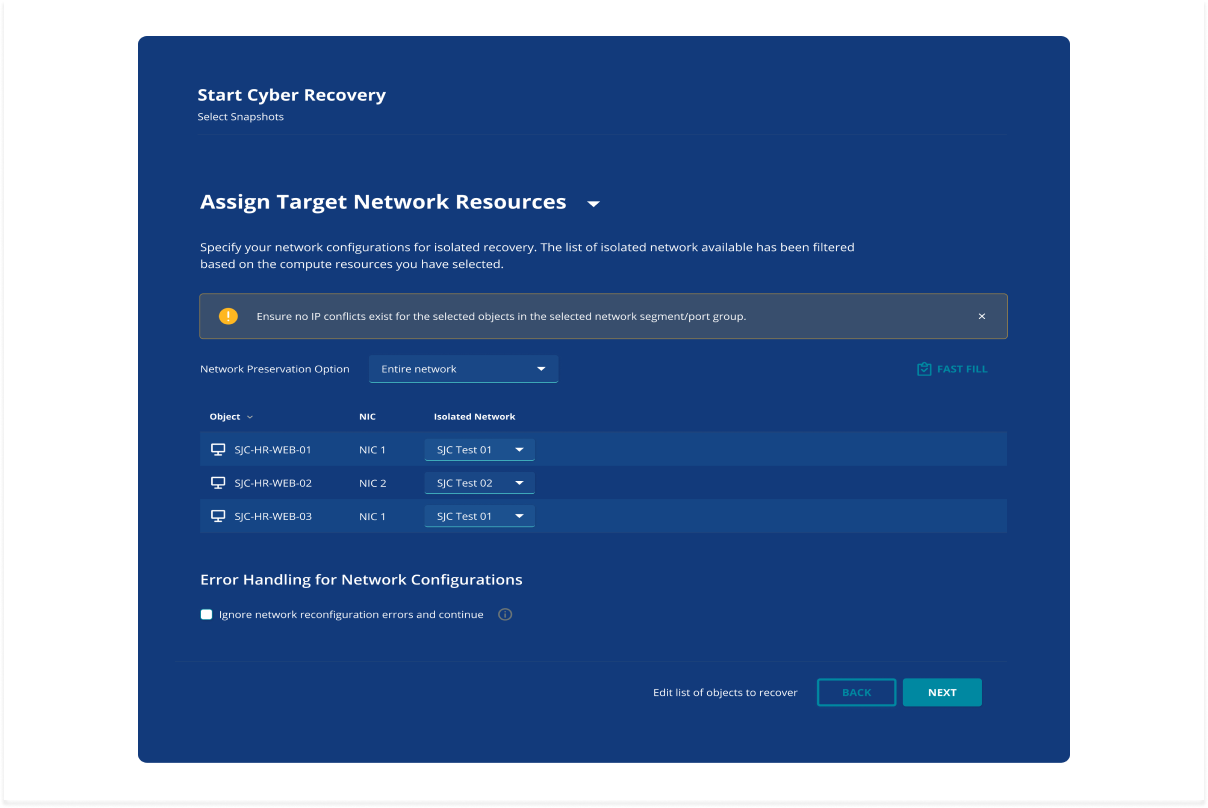
Figure 3: The Cyber Recovery wizard asks to specify network configuration for isolated recovery
Share Cyber Recovery Performance Reports: IT teams usually have to reference multiple different dashboards and go through a slow, manual process of compiling insights from various tools to create cyber recovery reports to share with stakeholders. Rubrik Cyber Recovery offers robust, built-in reporting functionality that allows organizations to download a recovery performance report showing successful recovery from a clean, immutable, air-gapped copy of their applications and data. IT teams can share these reports with stakeholders within their organization and cyber insurance companies to prove that they have the processes and controls in place to respond quickly and recover data and operations within their recovery SLAs.
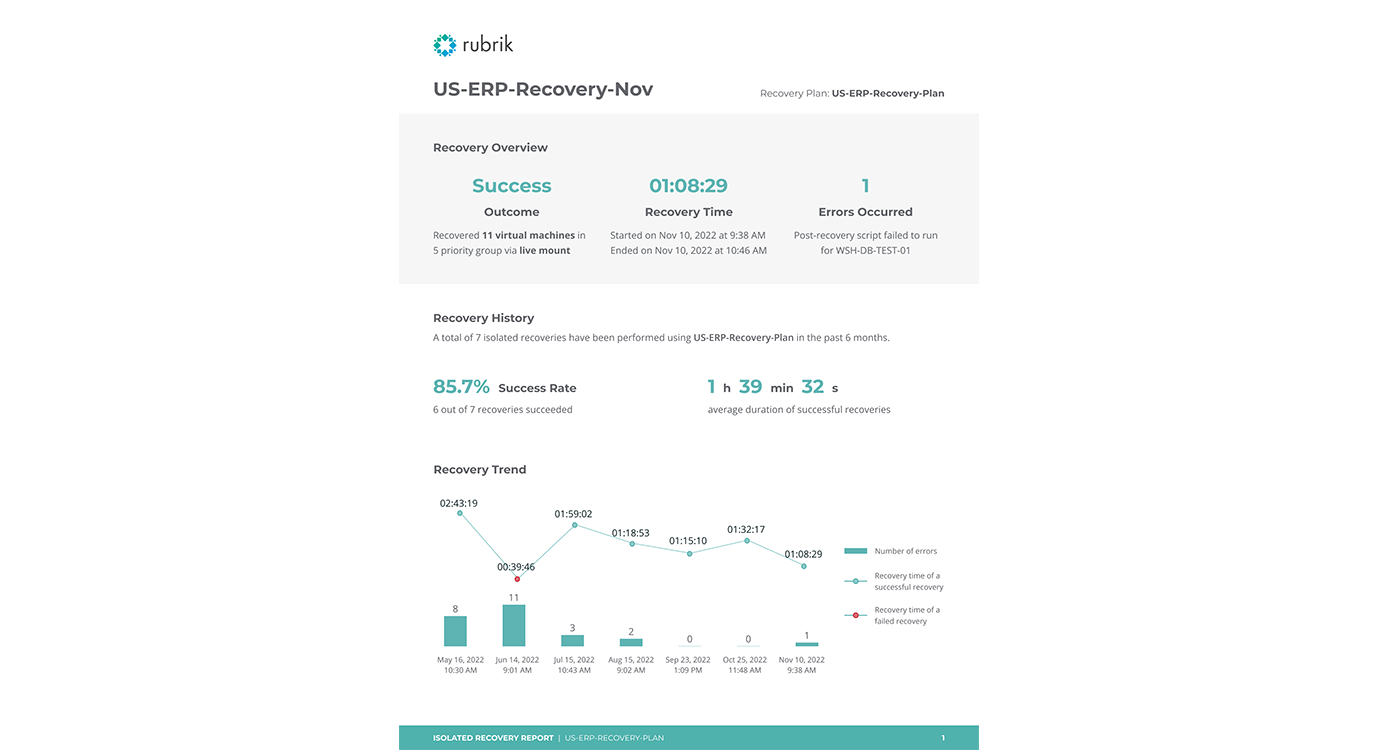
Figure 4: Example of a recovery performance report
Responding to a ransomware attack can be one of the most challenging events an IT or security professional can experience during their career. But with the right tools, it doesn’t have to be. Rubrik provides a simple way to test and validate recovery plans faster and investigate threats without delaying the restoration of business-as-usual. To learn more, watch the ‘Prove Your Ransomware Recovery Readiness’ breakout session on demand at the Rubrik Winter Release 2022.
Rubrik Cyber Recovery early access will be available in December 2022. For more information regarding the early access program, contact your Rubrik sales representative.
Ready to learn more? Visit our webpage.
