Are Passive Backups Enough?
It goes without saying that organizations must back up their critical data to ensure business continuity in the event of cyber attacks, disasters, operational failures, or insider threats. But are passive backups enough in today’s environment of sophisticated cyber threats? Despite having backups and various security tools to monitor infrastructure, organizations remain vulnerable to attackers who are still managing to penetrate defenses. Cyber attacks can devastate businesses, disrupting revenue and day-to-day operations for weeks or months at a time as well as inflicting reputational damage on the brand.
While there are many tools to analyze anomalous behavior and ransomware signatures throughout your infrastructure, don’t overlook the opportunity to leverage data stored within backup systems as an even more active form of cyber defense. Your own backup data contains valuable intelligence on how your data is being impacted by threats. Putting this intelligence to use can help you maximize your cyber resilience and restore to a clean state quickly and confidently.
Recruit Your Own Data To Defend Against Ransomware
It is surprising how rarely organizations use their backup data to defend against cyber attacks. After all, the data – captured across your critical workloads and across time – is all there. With this unique understanding of the content, breadth, and evolution of data, it only seems logical to leverage your backup data for both the proactive monitoring of data risks and during the high-pressure investigation and recovery cycles following a cyber incident.
Detection and analysis within backup data are not luxury capabilities. When a single day of data downtime can cost millions of dollars, there are significant economic benefits to having intelligence about cyber threats. Timely alerts around unusual patterns of change or recommendations about the last known clean snapshot can provide invaluable insights to avoid the costs and challenges of cyber attacks.
If an attacker is present in your environment, how quickly can business as usual be restored? How can you arm yourself with the knowledge to make informed decisions to ensure a fast and successful recovery?
Introducing Data Threat Analytics
With Rubrik Data Threat Analytics, you can continuously monitor for threats to your data, including ransomware, data destruction, and indicators of compromise (IOCs).
The basic idea is this: if you’re taking regular backup snapshots, you’re well-positioned to analyze this data for information that will help defend against ransomware and other cyber incidents. By capturing the longitudinal time-series history of data and scanning these snapshots, you can generate signals that are fed into a highly trained machine learning model – building a historical baseline against which new data can be compared to find anomalous modifications, deletions, and encryptions. In addition, your backups can shed light on lurking malware, safe recovery points, and aid in digital forensics.
Rubrik Data Threat Analytics combines three powerful threat detection engines that scan your backups out-of-band from your production systems without additional agents, thus preserving production system performance and keeping adversaries unaware. Let’s examine each in turn.
Detect Data Anomalies with Machine Learning
During a potential cyber incident, do you know exactly which apps, VMs, files, and folders were impacted and need to be recovered?
Rubrik Anomaly Detection determines the scope of cyber attacks using machine learning to detect deletions, modifications, and encryptions. You can receive timely alerts for suspicious activity, identify the ransomware strain, and quickly assess the blast radius at a granular level. Instead of a mass, brute-force recovery of large parts of your environment – which can be quite time-consuming – you can surgically recover only the components of your environment that were actually impacted.
Anomaly Detection provides broad visibility across your most critical enterprise and cloud workloads, including filesets, VMs, and cloud-native workloads. Detection of VM-level encryption (as opposed to anomalies impacting files within VMs) is also supported. Additionally, Rubrik provides accurate alerts by using machine learning to establish a dynamic baseline of changes to your data and alerts on anomalous activity relative to that baseline.
Hunt for IOCs Throughout the Time-Series of Data
Can you be confident that a specific known threat is not present within your systems? If malware is present, can you quickly identify a safe recovery point?
Rubrik Threat Hunting determines the initial point, scope, and time of infection by identifying specific indicators of compromise within the time-series history of backup data. It allows for highly surgical hunts during both peacetime and wartime scenarios. Threat Hunting offers the flexibility to custom define your own IOCs – based on YARA rules, file patterns, or file hashes – and scan on-demand. IOCs can be defined within your organization or can come from third parties, government bodies, ISACs, etc. By identifying the first infected snapshot, Threat Hunting can shortcut the trial-and-error process typically used to determine a safe recovery point – which can take weeks – and accelerate recovery. If IOCs are found, Threat Containment can be used to quarantine infected data within your backups to minimize the chance of reinfecting your environment.
Find Lurking Threats Early with Automated Threat Monitoring
Is malware dwelling in your critical infrastructure? With shrinking dwell times, can you take advantage of this narrow window of opportunity to remediate threats before they detonate? Are you leveraging the latest threat intelligence to detect new threats?
Rubrik Threat Monitoring detects threats early by automatically identifying indicators of compromise within backups using an up-to-date feed of threat intelligence. Threat intelligence is aggregated from different contributors, including Rubrik’s InfoSec team, Rubrik Zero Labs, and third parties. The threat intelligence is vetted prior to its inclusion in the feed to ensure high quality and relevance to critical infrastructure environments. When new intelligence is available, a hunt will kick off automatically and search for threats based off of the hashes and YARA rules. Should a match occur, you will be notified right away via email. You can then drill down to see where the threat was located, what hash or YARA was matched, and additional IOC details to assist in additional threat hunts via Rubrik or third party tools such as a SIEM or EDR. Threats can be quarantined as well. Essentially, Threat Monitoring is an always-on, turnkey solution: the intelligence is downloaded automatically, hunts based off of this intelligence are automatic, and if threats are found, you will be automatically notified. It really is that simple; you can “set it and forget it.”
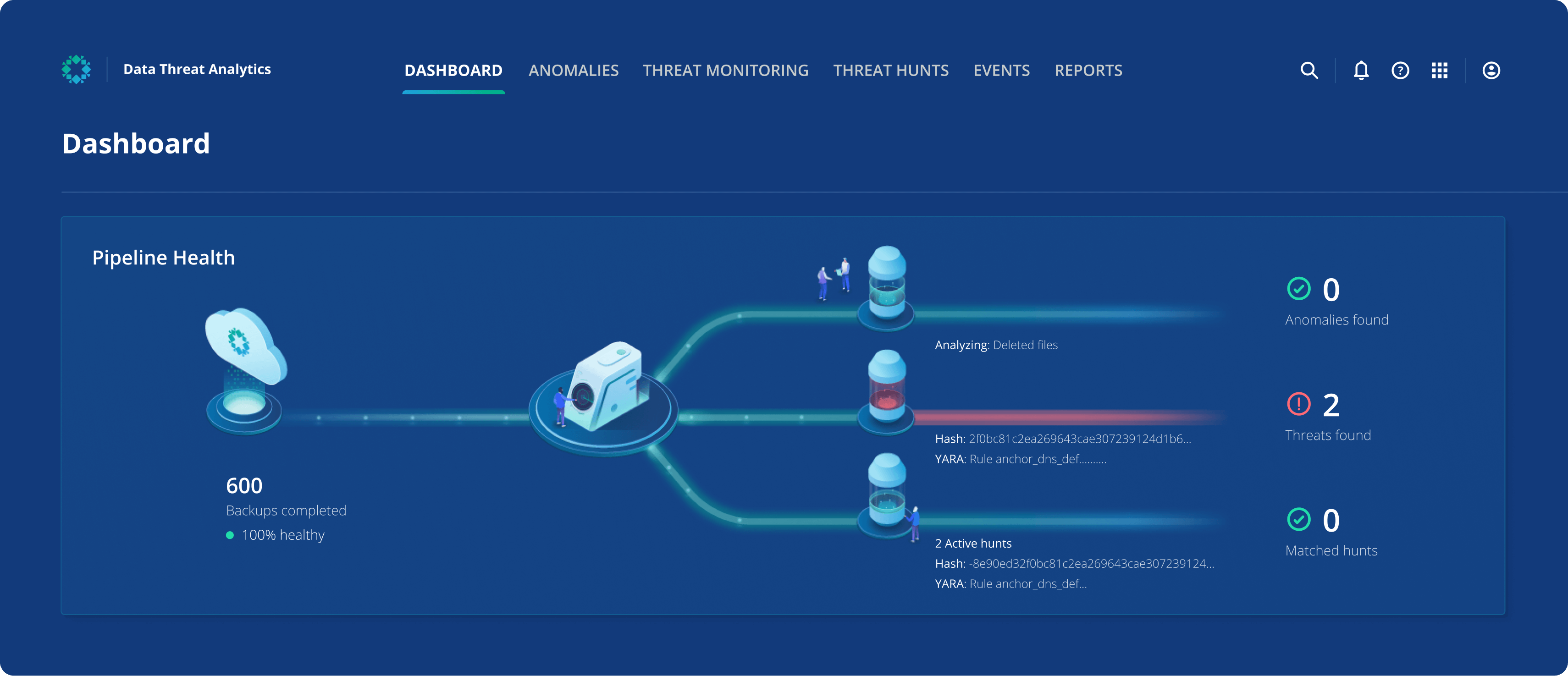
In summary, Rubrik Data Threat Analytics is a portfolio of three threat detection engines – Anomaly Detection, Threat Hunting, and Threat Monitoring (with more capabilities on the way!) – that analyzes your own backup data for valuable security intelligence, helping to keep your business resilient in the face of cyber threats.
Learn More
To learn more about Rubrik Data Threat Analytics, including the recently launched Threat Monitoring, please watch the session Identify Data Threats Faster While Avoiding Reinfection from Forward 2023.
