An Accelerating Threat: Ransomware Targeting Virtualized Infrastructure
Organizations are increasingly relying on virtualization. As critical infrastructure and business systems continue to be virtualized, threat actors have responded in kind by deploying ransomware impacting hypervisor software.
According to a joint advisory published by CISA and the FBI on February 8, 2023:
Malicious actors may be exploiting known vulnerabilities in VMware ESXi servers that are likely running unpatched and out-of-service or out-of-date versions of software to gain access and deploy ransomware. The ESXiArgs ransomware encrypts configuration files on ESXi servers, potentially rendering virtual machines (VMs) unusable.
As of February, ESXiArgs attacks had targeted at least 3,800 IP addresses and compromised at least 2,250 machines spanning multiple countries in Europe, Canada, Asia, and the U.S. Ransomware payload offerings were observed from multiple groups, including ALPHV, LockBit, and BlackBasta. Roughly 60% of attacks reported to Rubrik’s Ransomware Response Team in the past several months involved the encryption of VMs – particularly ESXi. In all likelihood, adversaries will continue to target virtualization infrastructure.
Can You Detect and Respond to Encryption of Host VMs?
A combination of factors makes VMs a popular attack target.
Out-of-date software. Even though VMware patched this vulnerability over two years ago, many organizations continue to run versions of ESXi that are no longer supported and therefore received no patch. These systems remain vulnerable to attacks.
Lack of defensive products. The ESXi hypervisor is a specialized, purpose-built solution, which makes it unable to run “off-the-shelf” software, including security tools, designed for general-purpose operating systems. The lack of Endpoint Detection and Response (EDR) and antivirus (AV) software for ESXi, coupled with the difficulty of implementing security measures, makes it easier for threat actors to deploy malware on ESXi compared with Windows.
Potentially severe impact to virtualized systems. VM-level encryption attacks exploit host VMs and target the underlying virtual machine and virtual disk files. This means attacks can severely impair any virtualized infrastructure tools, including vCenter, monitoring and alerting, BCDR solutions, and other applications. Without the ability to quickly detect and recover from VM encryption, teams can find themselves flying blind. To make matters worse, 76% of attacks happen after hours or during the weekend. Furthermore, it is likely to be a manual process to identify the blast radius of the attack. If vCenter is down, you would need to manually inspect individual hosts (if you can log in) to even begin to formulate a recovery plan. And compromised hosts would need to be rebuilt from scratch.
Introducing VM Encryption Detection
Rubrik is pleased to introduce VM encryption detection, which detects when host VMs are encrypted, allowing customers to receive timely anomaly alerts for VM-level encryption activity, quickly assess the blast radius, and recover from such attacks. VM encryption detection is a new capability that is part of Rubrik Anomaly Detection, which until now has focused on detecting file system anomalies.
VM encryption detection enables customers to strengthen their detection of encryption without increasing cost, as it is performed by the backup solution, and gain confidence in the resilience of their virtualized infrastructure.
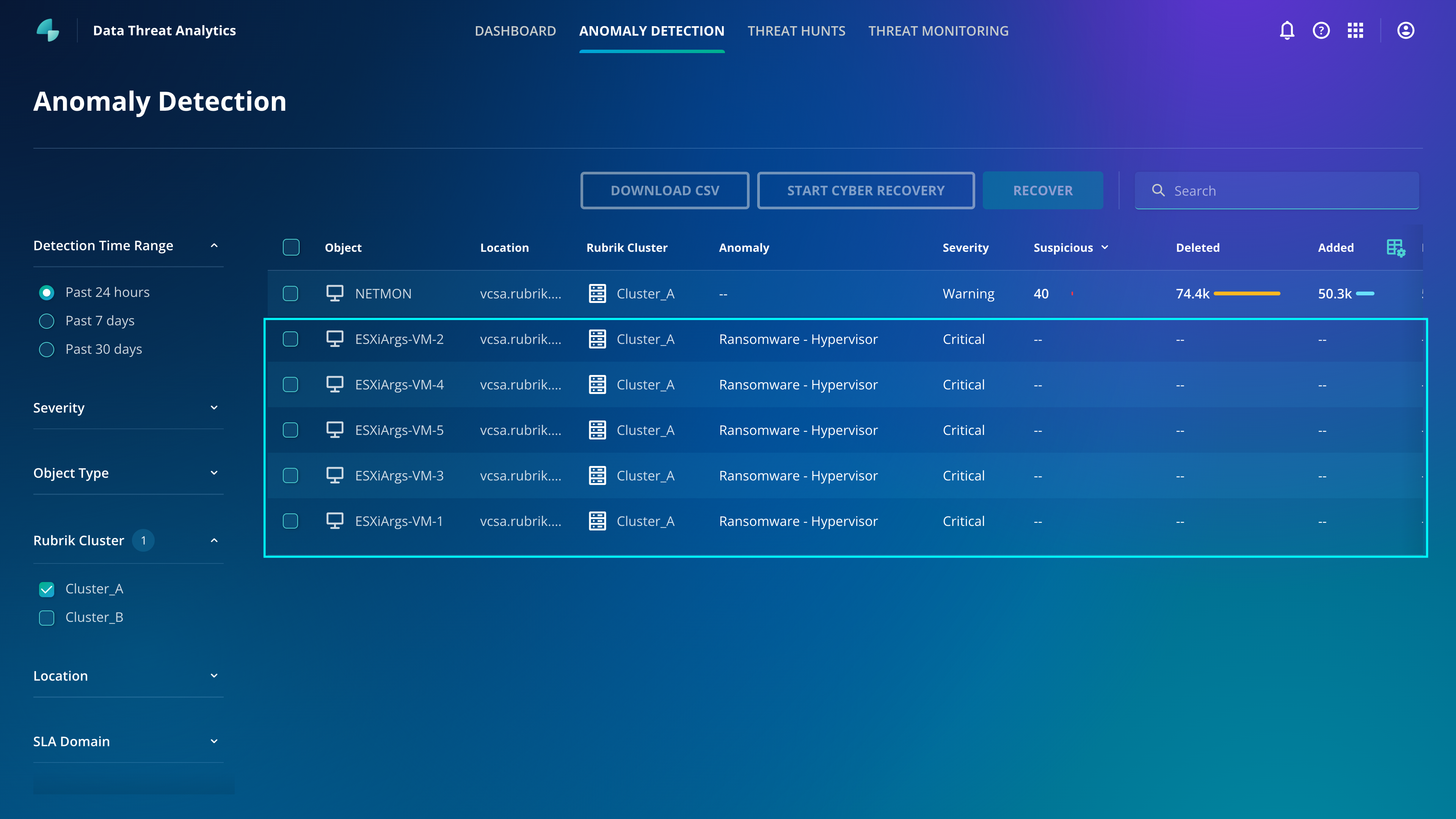
VM Encryption Detection Is Automatically Enabled
Rubrik began rolling out VM encryption detection to eligible customers on October 3. VM encryption detection is available to all customers entitled to Anomaly Detection, including customers licensed under Business Edition, Enterprise Edition, or Proactive Edition, as well as customers who have purchased Anomaly Detection à la carte. And the great news is that for eligible Rubrik Security Cloud customers, no action is required to enable VM encryption detection. Expand your Data Threat Analytics capabilities within your backup solution today!
