These days, you gotta encrypt your data. Everyone knows that.
But how encryption is managed matters—especially with businesses increasingly backing up their on-premises data to the cloud. The cloud era requires more advanced encryption strategies.
Thankfully, Rubrik has a solution for that.
Rubrik Cloud Vault (RCV) is an isolated, immutable, Rubrik-managed cloud storage instance that provides a destination for your enterprise backup data. This allows customers to securely backup data offsite, without the trouble (and concern) of designing and managing a secure cloud backup architecture.
RCV has always supported customer-provided RSA encryption keys to encrypt their data at rest. But this approach can leave a security gap if that RSA key is compromised. To address that gap, Rubrik has recently introduced an upgrade to RCV that gives Rubrik Secure Vault customers the ability to manage their data encryption via their own Azure Key Vault environment. This expands the efficacy of established encryption procedures, adding the ability to perform key rotation and rekeying of encryption keys. This enhancement puts broader key management and encryption compliance capabilities into the control of the customer.
Integrating RCV with Azure Key Vault
Azure Key Vault is a cloud service that provides secure key management and storage for encryption keys and secrets. By leveraging Azure Key Vault as the Key Management Service (KMS) for RCV, customers can more easily manage, store, and protect the encryption keys that secure their backup data in the cloud. When using Azure Key Vault as the KMS, customers can create, import, and manage their own encryption keys within their Azure subscription.
A Key Hierarchy for More Secure Data
Whether using an RSA key or Azure Key Vault, customer-managed keys are first used to encrypt a Rubrik-generated Root Key. This Root Key is then used to encrypt Rubrik-generated Key Encryption Keys (KEKs) that are part of the encryption key hierarchy for RCV data. These KEKs are then used to encrypt the Rubrik-generated Data Encryption Keys (DEKs) that are used to encrypt the actual customer data.
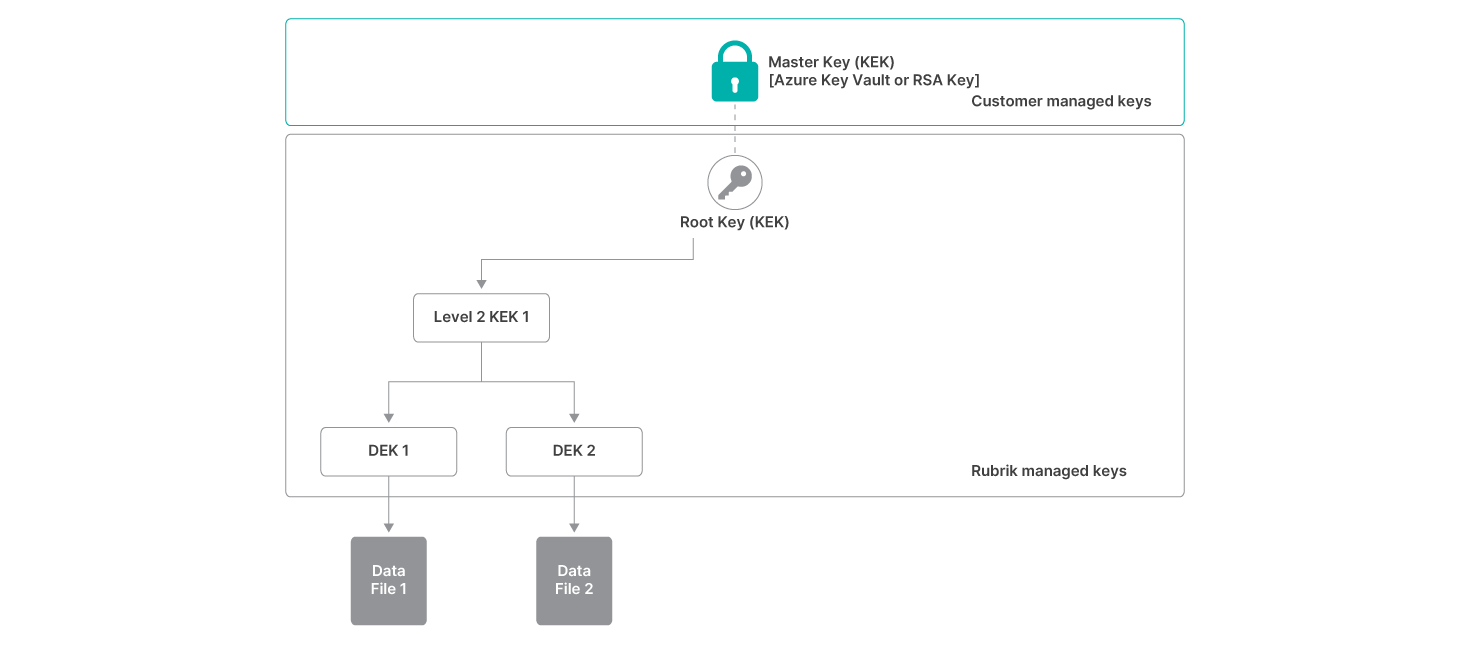
Using this approach, customers have ownership of the hierarchy of encryption keys used to secure their cloud-archived data. Since this encryption is happening with their on-premises Rubrik Secure Vault prior to sending to RCV, they maintain total control of their data security. Even Rubrik cannot read this data while it is in RCV.
Encryption Key Management
Azure Key Vault settings are managed via the Unified Encryption Key Management (UEKM) interface within Rubrik Security Cloud. The UEKM provides a centralized location to configure and manage encryption keys used to protect data across Rubrik's various solutions.
Once an RCV location is created, the UEKM interface allows for key lifecycle management operations like key rotation and rekeying. This allows administrators to monitor and maintain the integrity of their encryption keys throughout the entire data lifecycle.
One of the core benefits of RCV is that the data it protects is immutable; it is designed to be unchangeable and tamper-proof. While the stored data cannot be re-encrypted, the encryption keys used to protect the data can be updated and rotated. New Data Encryption Keys (DEKs) are regularly created and used to encrypt new customer data, often for each new data file. KEKs, which are used to encrypt the DEKs and lower level KEKs, can be replaced.
This means that encrypted data is protected by multiple levels of encryption, most of which will use fresh encryption keys for new data.
Updating Key Encryption Keys
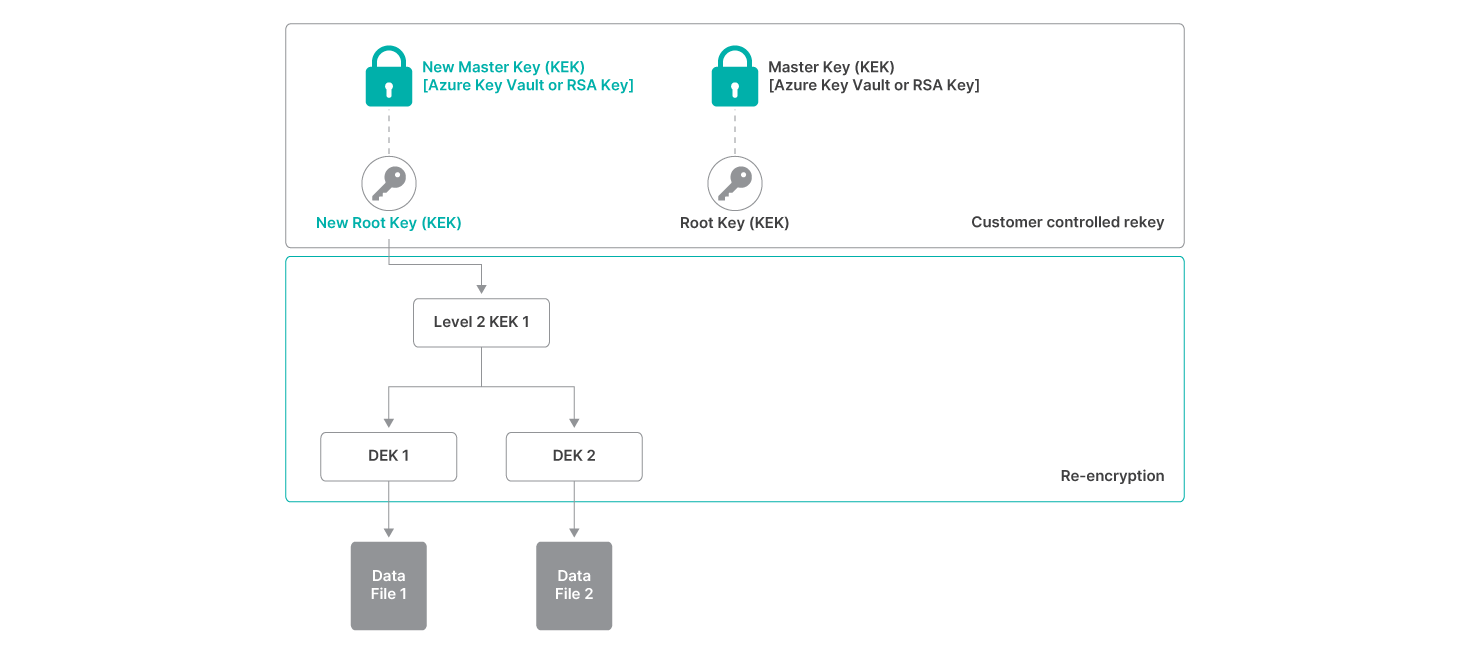
Rekeying is the process of replacing an existing KEK with a new key that is then used to protect child keys in the hierarchy. This allows customers to replace compromised keys and reset the security of the lower level KEKs and DEKs. Customers can manually initiate the rekeying process for either the Master Key (changing the KMS or RSA key that manages the entire key hierarchy) or the Root Key (at the top of the key hierarchy) via the Rubrik Security Cloud.
When the Root Key is updated, the intermediate KEKs and DEKs will be automatically re-encrypted using the new Root Key. If the Master Key is updated, a new Root KEK will be automatically issued, resulting in the re-encryption of intermediate KEKs and DEKs
Rotating Data and Key Encryption Keys
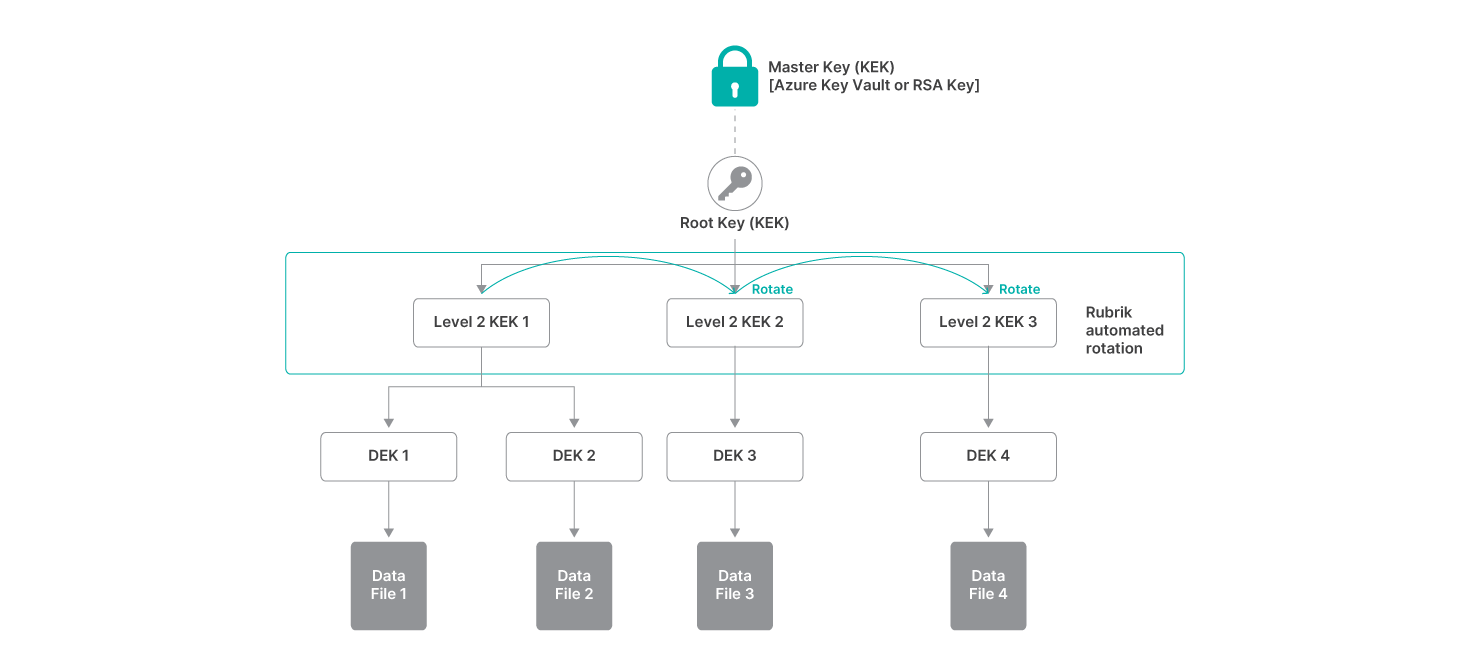
Key rotation is the process of regularly creating new keys for protecting new data. Older keys are kept for the purpose of reading old data, but no new data is protected with the old keys. By regularly having new branches of data files encrypted with a new KEK, the compromise of one KEK will not allow access to the other branches of data, thus reducing the blast radius of a single key compromise.
Automated key rotation for Rubrik-managed intermediate KEKs is a background job which runs on Rubrik Secure Vaults every 30 days. This is transparent to the customer with no input needed, though the results of key rotation are documented in the UEKM interface.
The automated key rotation applies to the Rubrik-managed intermediate KEKs only. The customer-managed Master Key (KMS or RSA key) and the Rubrik-managed Root Key do not support rotation. These keys can be manually re-keyed on-demand by the customer.
Basic encryption strategies are not enough to meet the threats of the cloud era. We need a better approach. Maintaining the integrity and recoverability of customer data is the heart of Rubrik’s mission. By providing an administratively air-gapped storage location with fully encrypted data that only the customer can decrypt, Rubrik Cloud Vault offers a reliable archival solution that can give customers the comfort of knowing only they can access their data and that it cannot be modified or destroyed outside of the policies they set.
