There is a lot of change going on in the way applications are created and hosted right now. Between big changes with hypervisor vendors and the accelerating pace of business, organizations are looking to make changes in how they can create, update, and manage their applications and data. On top of all of that, there’s been no lack of evidence as to the dangers that corporate and customer data are under by cyber threats.
All of these trends make for a significant number of challenges for organizations:
No app modernization journey jumps straight from start to finish, requiring interim steps and all the support that they need
Organizational charts and processes need to adjust as much as the technologies
Some technology may need to to be eliminated due to unsupportability, cost, or other factors that make them untenable in their current use
Protecting data from attack is complex, multifaceted, and needs to be robust
This leads to a strong need for flexibility, consistency across multiple platforms and data types, and a focus on cyber resiliency. This has been the focus of Rubrik's partnership with Red Hat, supporting data protection for the OpenShift platform. Rubrik has been protecting objects and persistent volumes of containers managed by Kubernetes and the OpenShift platform for several years.
As more customers are looking to migrate VMs to new virtualization platforms it made sense to extend Rubrik to more directly support protection of VMs running on OpenShift Virtualization. This gives customers who are looking to consolidate their containers and VMs onto a single platform the ability to use a single data protection platform to protect their applications no matter where they are in their modernization journey.
Easing the Application Modernization Journey
Protecting across all of these stages in a consistent manner helps to ease the journey. Knowing their historical data will be encrypted in-flight and at-rest, air-gapped and immutable to prevent modification, and protected from unauthorized access with role-based authorization controls and quorum authorization allows for one less thing to worry about when change is occurring throughout the environment.
One of the most powerful aspects of the app modernization journey is the decentralization of infrastructure and application management, which reduces friction by distributing management of the environment based on job role. Fortunately, Rubrik already has robust role-based access controls that allow, for example, a governance team to define and monitor data protection SLAs, database or application administrators to apply the appropriate SLAs, and infrastructure administrators to manage the underlying backup and archive locations.
Furthermore, Rubrik has created custom resource definitions (CRDs) that provide backup and recovery functions directly through the OpenShift Kubernetes environment, reducing the interfaces needed. Whether managing data protection through Rubrik Security Cloud, using the CRDs, or with custom integration directly with the Rubrik APIs, every role will have a consistent and native experience.
How it Works
Rubrik protects Kubernetes applications by taking copies of both the persistent volume(s) (PV) and objects within the pod. This ensures consistency of the entire pod on restoration by collecting any interrelated changes together.
When a new OpenShift cluster is on-boarded within Rubrik, a Rubrik specific namespace is created with a controller and external interface. To ensure minimal impact to the resources in the cluster, Rubrik’s backup agent is only instantiated during the backup and recovery process, and is destroyed as soon as the process is completed.
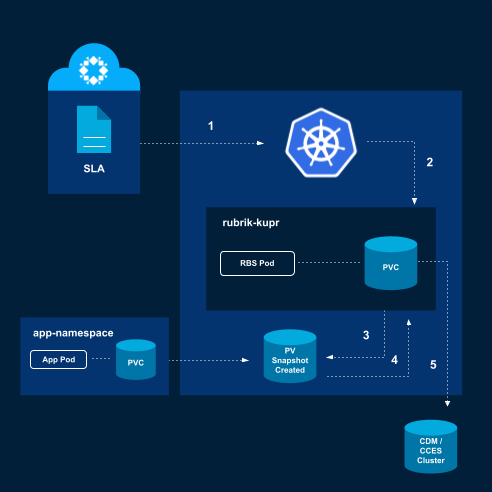
The backup process is pretty straightforward:
An SLA policy is applied to the cluster, namespace, protection set, or directly on the VM.
The Rubrik backup agent is instantiated to start the backup process.
A PV snapshot is created
The PV snapshot is mounted via a persistent volume claim (PVC) to the Rubrik Agent pod.
The blocks on the PV snapshot are copied to the Rubrik cluster.
After all the data is captured, the PV snapshot, PVC, and Rubrik Agent are destroyed.
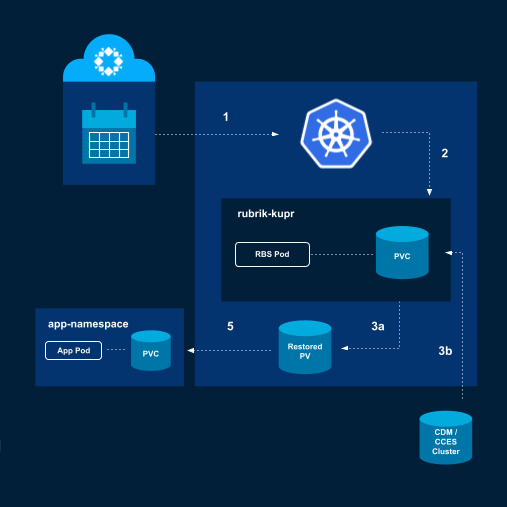
The restore process works very similar to the backup process, and can restore a VM to the same or a different namespace:
Start an on-demand recovery job by selecting the point in time from Rubrik Security Cloud or via the Rubrik CRDs.
The Rubrik backup agent is instantiated.
Data is restored to a new PV.
A new PV is created.
The blocks from the backup are copied from the Rubrik cluster to the new PV.
Once the data copy completes, the Rubrik pods are detached from the restored PV.
The restored PV is attached to the PVC in the application namespace.
The Rubrik agent is destroyed.
Evolving with the Industry
With the fast pace of change in application development, hosting, and threats, data protection is more important than ever and shouldn’t be left to chance as applications migrate to more modern platforms.
With a long history of VM data protection, Rubrik has shown the ability to continually improve and expand, and our support for OpenShift Virtualization will prove no different. This will include the full power of data security and cyber resilience that Rubrik provides for other hypervisors.
To learn more about how Rubrik can protect OpenShift Virtualization, see this guided demo or sign up today for our upcoming webinar.
