According to Cybersecurity Ventures, more than half of the world’s data will be stored in the cloud by 2025.
When organizations embrace cloud technologies, the barrier to deploying new resources virtually disappears. Teams across the business can independently provision cloud services with just a few clicks—often without centralized oversight. The result is organizational data rapidly dispersing across numerous accounts, regions, and service providers, creating a complex technological landscape that's difficult to track.
This dispersion—commonly referred to as “cloud sprawl”—makes tracking data locations increasingly difficult. More importantly, it complicates ensuring proper data protection. Remember: protecting your cloud data is your responsibility, not that of Azure, AWS, Google, or Oracle.
This cloud spawl challenge becomes particularly critical with sensitive information—whether personally identifiable information (PII), financial records, customer databases, or other business-critical data. When such data is compromised, organizations face potentially devastating consequences that can threaten business survival. In today's threat landscape, where 94% of cloud tenants were targeted in 2023 and 62% were successfully compromised, organizations must prepare for the inevitability of a cloud cyberattack.
It's not a matter of if, but when.
Cloud Sprawl Meets the Visibility Gap
The stark truth is that IT and security teams face significant challenges in maintaining a robust backup posture in the cloud due to limited visibility into their cloud environments. This lack of comprehensive insight raises a critical question: How can organizations effectively protect assets they cannot fully see or understand?
Many teams find themselves saying:
“I don’t know what data exists across my cloud environment.”
“I don’t know whether my critical cloud data is being backed up.”
“I don’t know if the backed up data has the right policies in place.”
“I don’t know how much am I spending on cloud backup costs.”
Even organizations using native tools like Azure Backup or AWS Backup face uncertainty about whether all data is being properly backed up and how much they're spending on backup costs.
Secure Your Unprotected Data With Rubrik Cloud Posture Risk Management
Today, Rubrik is proud to introduce Rubrik Cloud Posture Risk Management (CPR). This new feature gives customers visibility into whether cloud data is being backed up and if it's being backed up correctly based on the nature of the data and its usage patterns.
Simply put, Rubrik CPR empowers backup administrators with visibility across their entire cloud data estate, ensuring they know exactly what requires protection.
While it may seem obvious that your cloud backup tool should track the data it protects, most organizations use multiple products across their environments, creating significant visibility gaps that leave organizations uncertain about their overall protection status.
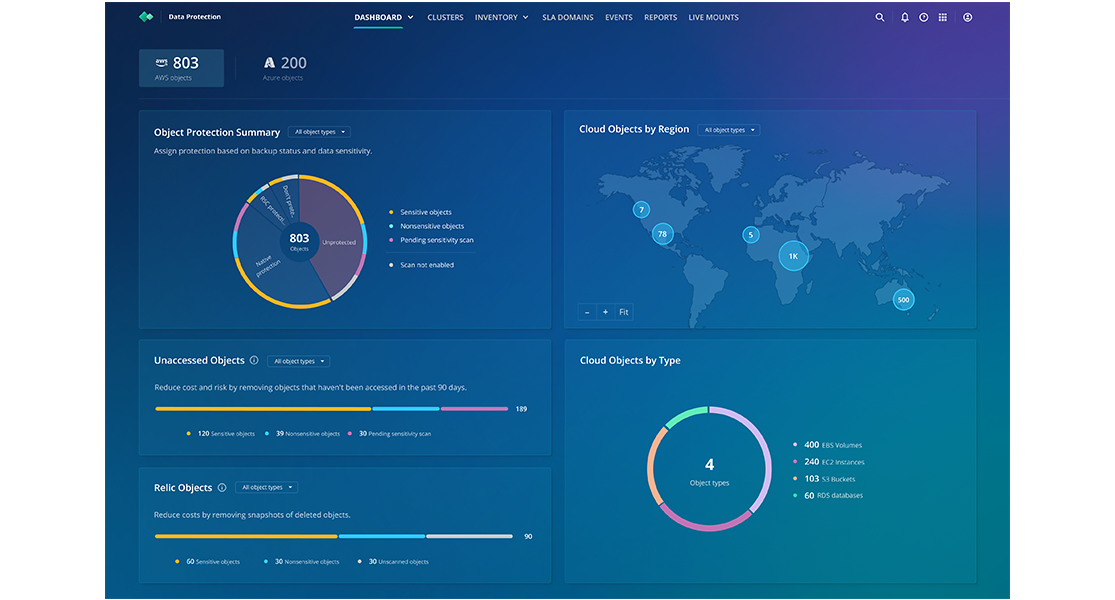
Rubrik Cloud Posture Risk Management (CPR) addresses this challenge by offering a unified view of your cloud data protection status. The solution categorizes cloud objects into four clear protection states:
Protected by Rubrik Security Cloud: Data fully protected by Rubrik
Protected by Native Tools: Data backed up through cloud provider services (AWS Backup, Azure Backup)
Unprotected or Unknown: Data without confirmed protection, including objects that may be protected by third-party tools
Do Not Protect: Objects explicitly flagged to remain unprotected, such as test data or easily reproducible information
Pay Attention to Sensitive Data
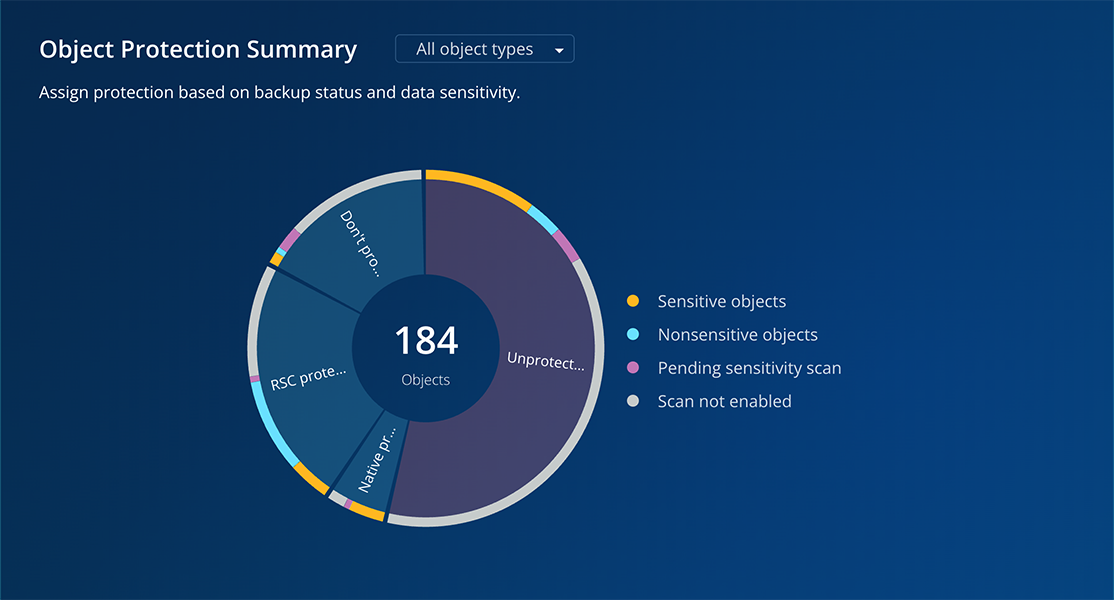
Beyond protection status, Rubrik CPR also analyzes data sensitivity levels. The dashboard clearly displays where sensitive data may be at risk, allowing you to quickly identify protection gaps in your most valuable information assets.
When viewing the dashboard, you can hover over any category—such as "Unprotected"—to see a breakdown of object types detected as sensitive. From there, one click takes you to a detailed inventory view of the specific objects.
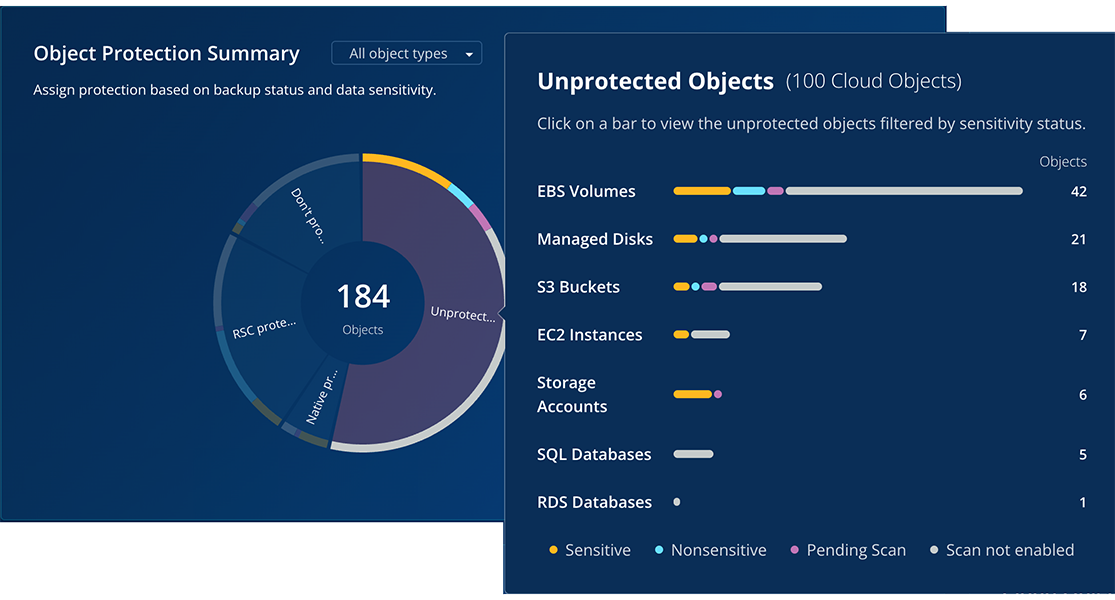
Taking action on unprotected sensitive data is straightforward. For example, when examining AWS S3 buckets (common repositories for sensitive information), you can see:
Bucket names
Sensitivity classifications
Number of high, medium, and low sensitivity content
With this critical context, you can make informed decisions about whether the data should be there and how it should be protected. Implementing protection is as simple as selecting objects and clicking "Manage Protection" to assign an SLA Domain.
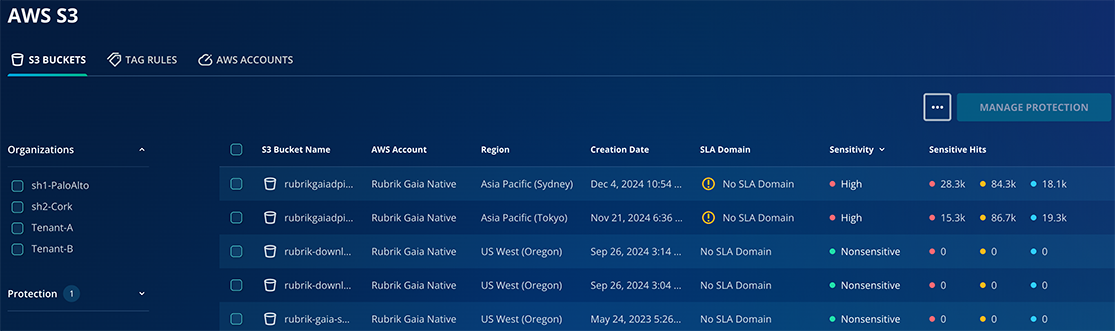
Cost Optimization Opportunities
Rubrik CPR also identifies cost optimization opportunities through two key categories:
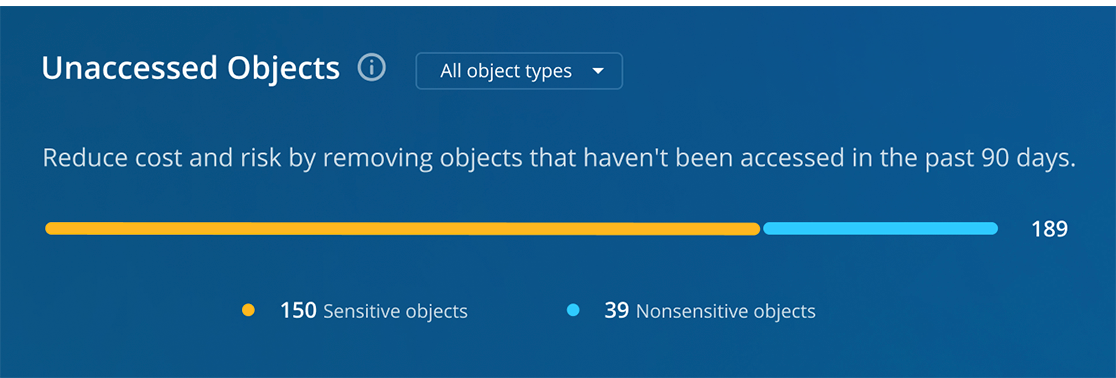
Unaccessed Objects (Stale Data)
Objects untouched for 90+ days represent potential storage cost savings. Removing stale sensitive data delivers the dual benefit of reducing both costs and security risks. The solution makes identifying and managing these objects simple through detailed filtering.
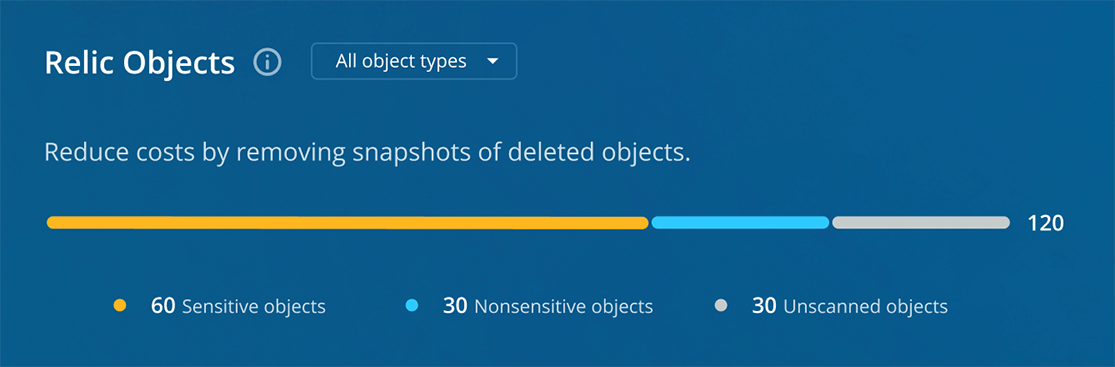
Relic Objects
These are snapshots of objects whose source has been deleted. While some may be intentional (such as final backups of decommissioned systems), most are often overlooked backups that were missed during cleanup processes—representing significant potential cost savings.
How Rubrik CPR Works
Rubrik CPR operates through a two-part analysis process:
Protection Analysis: Rubrik Security Cloud leverages cloud provider APIs to identify object protection status, location, and access patterns. This information combines with Rubrik's own protection data to create comprehensive visibility.
Sensitivity Analysis: Using serverless technology in your own cloud environment (through an Outpost account), Rubrik performs data sampling to identify sensitive content—without moving data outside your environment. Only metadata is transmitted to Rubrik Security Cloud for dashboard visualization.
This architecture ensures you gain complete visibility into your cloud data protection posture while maintaining strict data sovereignty and security requirements.
How do I enable this?
Sounds exciting, right? If you are a current Rubrik customer protecting native workloads in the cloud, you can turn on CPR today, without any additional fee!
1. In Rubrik Security Cloud, browse to the Settings page, then to Cloud Accounts, then select either AWS or Azure.
2. Click Configure under the Data Classification column for each account that you wish to enable.
3. At the bottom of the popup that you see, you’ll see a new option to toggle a switch to enable scanning to Optimize backup management, as shown in the image below.
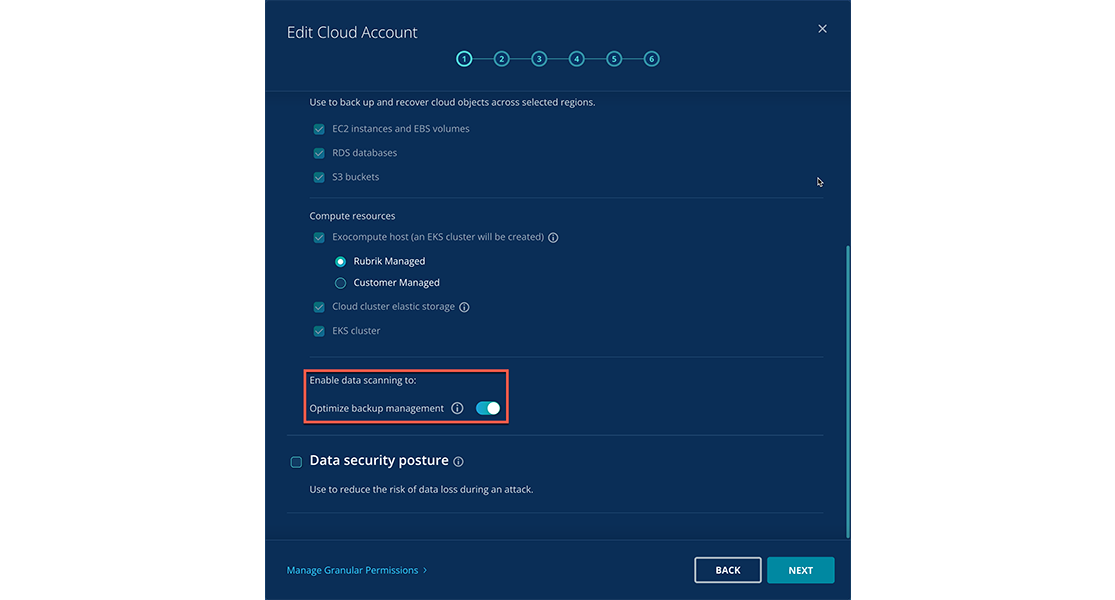
4. Flip this switch, then click Next.
5. You’ll see a summary of the onboarded account, including the regions that Rubrik is automatically discovering workloads in. You can add or remove regions in this screen as required, then click Next.
6. The next screen will ask for your Outpost account details. This account is where the data sensitivity analysis occurs. You can use an existing account or set up a separate one specifically for this purpose. Enter the account number, then click "Generate CFT" to create a CloudFormation Template for configuring the Outpost. Finally, click to log in to the AWS console for your Outpost account.
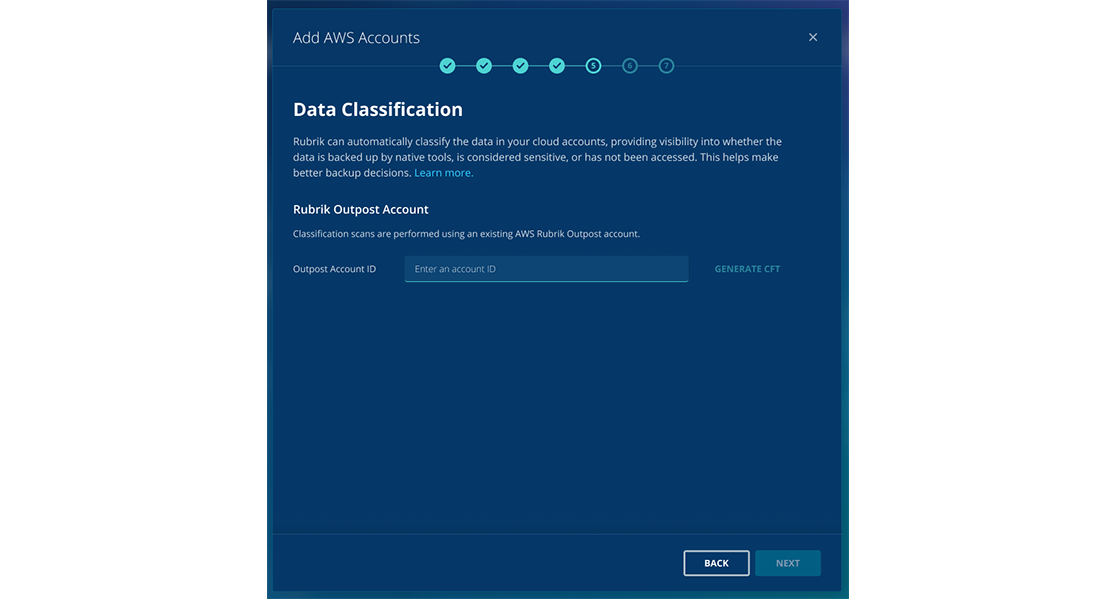
7. In the AWS account, click through the wizard to apply the CloudFormation Template. The final step of the setup sends a notification to Rubrik Security Cloud that the setup is completed. At this point, you can return to Rubrik Security Cloud and finalize the wizard.
Note - this post walks through the process to enable Cyber Posture Risk Management for an AWS account. The process for Azure is similar, and can be found in the online documentation.
With setup complete, it's time to review your insights.
From the main Data Protection page, you’ll find the new Cloud Posture Risk dashboard under Dashboard > Cloud Native Protection. (Please note that initial analysis may take a few hours to complete.)
Rubrik CPR doesn't stop at initial analysis. As your cloud environment evolves, the system continuously discovers new workloads and automatically analyzes them for protection status, sensitivity, and optimization opportunities. This ongoing monitoring ensures your organization maintains complete visibility as your cloud footprint changes.
Business Benefits Beyond Protection
Cloud Posture Risk Management delivers multiple strategic advantages:
Enhanced Data Visibility: Gain comprehensive visibility across your entire cloud data estate, uncovering previously hidden vulnerabilities and enabling proactive risk management before threats can exploit protection gaps.
Strengthened Protection Posture: Ensure business-critical data has appropriate protection policies aligned with its sensitivity level, establishing consistent backup standards across multi-cloud environments and improving recovery readiness.
Optimized Cloud Expenditure: Reduce unnecessary storage and protection costs by identifying stale, redundant, or trivial data, allowing targeted investment in protecting truly valuable assets rather than indiscriminate backup.
Streamlined Compliance Management: Maintain comprehensive records of sensitive data location and protection status, demonstrating due diligence to regulators and reducing compliance violations through automated discovery of regulated information.
Take Action Today
Perhaps most compelling is that these powerful capabilities come included with your Rubrik Cloud Native Protection license—no additional tools or complex deployments required. You gain comprehensive cloud data governance without the overhead typically associated with implementing new security solutions.
And if you’re not a current Rubrik cloud customer, we got something for you too: we’re excited to offer you a completely free CPR assessment. Without the need to deploy Rubrik into your environment, this assessment will run in your environment to help you understand exactly what data you have, how much of it is being backed up natively, and—perhaps more importantly—how much is sitting unprotected. Sign up today!