What is Data Security Posture Management?
Data security posture management (DSPM) is an approach to data security that solves one of the most complex issues in modern cloud environments—knowing where all your data is and how it is secured. This emerging security trend was named by Gartner in its 2022 Hype Cycle for Data Security and has quickly become one of the most critical practices in the cybersecurity space. DSPM addresses the inherent challenges arising from the rapid proliferation of sensitive data that lives in multiple clouds, is stored across many different environments and types of cloud storage technologies.

Data security posture management, sometimes known as cloud data security posture management (CDSPM), provides organizations with a practical approach to securing cloud data by ensuring sensitive and regulated data always has the correct security posture regardless of where it is stored or moved to. To accomplish this, DSPMs must be able to discover all cloud data, classify it by data type and sensitivity level, detect and alert on data security policy violations, prioritize those alerts, and provide remediation playbooks.
Because of the emerging nature of this new technology, you may still need to become familiar with the who, what, when, where, why, and how. This article aims to provide you with all the tools you need to fully understand why DSPM is so critical to a defense-in-depth strategy, including why you need it, how it compares to existing approaches, how it works, and what to look for in a DSPM solution.
Why do I need a DSPM Solution?
The proliferation of cloud data technologies: cloud data security leader Rubrik solves the complexity of cloud data with its DSPM solution - Rubrik
Cloud Transformation + Data Democratization = The Perfect Storm
As the world becomes more technologically advanced, customers and employees expect better and more advanced digital services in their daily lives and also from their business providers. Competition is fierce. Expectations are high. Innovation is critical, which is why organizations have embraced cloud transformation initiatives and moved to the cloud for its flexibility and scalability, but also for its ability to democratize data, aka—make the data available to more people so that they can better harness the value of that data. Because the biggest winners in the cloud era are those that generate the most value from their data.

Why is a DSPM solution important: Gartner data prediction – Rubrik
This new era shepherded in by cloud transformation and data democratization is characterized by:
The sprawl of cloud data storage technologies across multiple cloud providers which are often configured differently, resulting in multiple architectures that are constantly changing and difficult to manage.
The proliferation of data (mostly shadow data) caused by developers having so many technologies at their disposal that they can spin up or copy entire data stores quickly, without having to involve security.
The death of the traditional perimeter as cloud data is a shared model meaning that data is accessible to everyone from anywhere with no single choke point, leading to sensitive data being overexposed.
A faster rate of change as release cycles now happen in weeks, days, and hours rather than months and years, often leaving security out of the process or forcing security to respond quickly to ensure sensitive data is appropriately protected.
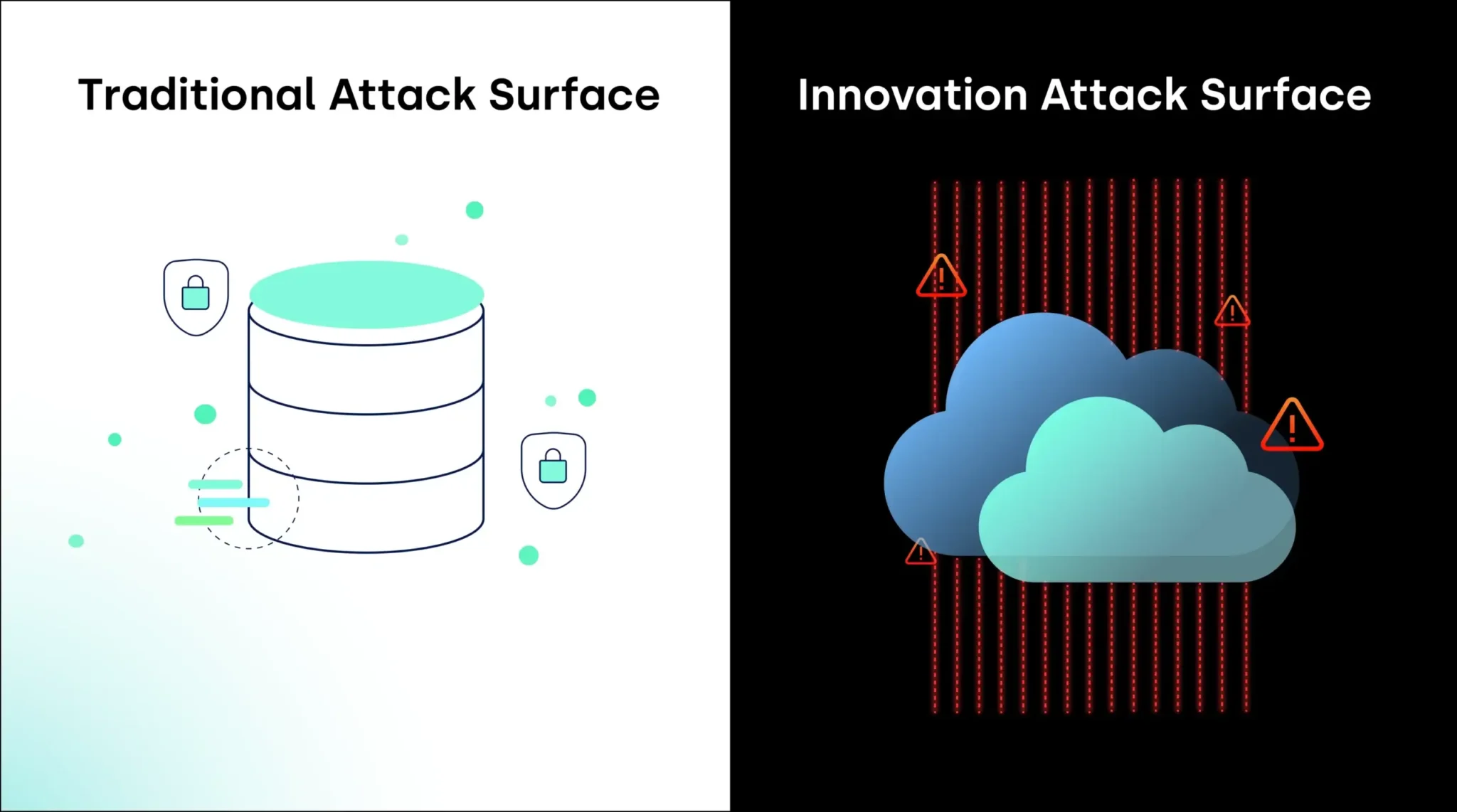
The convergence of these factors has created an “Innovation Attack Surface”: a new risk that most organizations unconsciously accept as part of the cost of doing business. Whereas the traditional attack surface was determined by outside-in activity—malicious external forces (including internal bad actors) seeking to exploit vulnerabilities to gain illicit access to protected information, the innovation attack surface is massive, decentralized, accidental risk creation by the smartest people in your business—your developers and data scientists.
It is in combating threats to this new attack surface that the need for data security posture management (DSPM) was born.
Limitations of Legacy and CSP-native Solutions
The nature of cloud data, which is magnitudes larger, more distributed, and more dynamic than it was in the on-premises days, has outpaced the capacity of traditional data security to protect it. The result is what we at Rubrik refer to as the Security Execution Gap – where security teams lack the resources, tools and expertise to securely support rapidly advancing data-led value creation in the cloud.
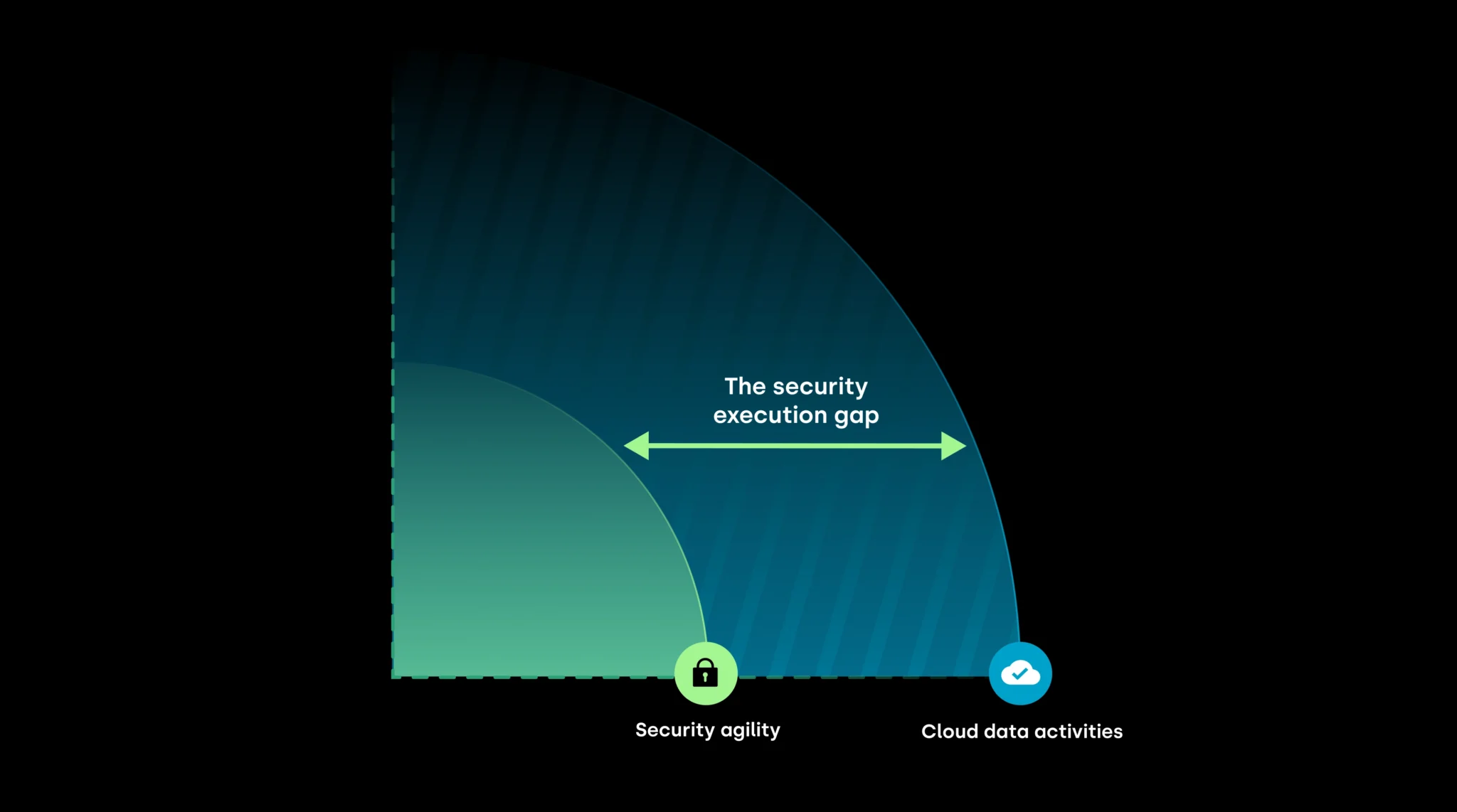
The security teams that close this gap don’t just create a more secure data environment—they actively enable cloud data practitioners to create more value faster (and safer) than the competition.
In this section, we will explore further the limitations of traditional and other solutions to better understand why DSPM is the only solution.
| Alternative | Main Limitations |
|---|---|
Manual/Homegrown |
|
Legacy, on-prem (e.g., BigID, Varonis) |
|
CSP-Native Tools (e.g., AWS Macie, Azure Purview, Google DLP) |
|
CSPM/CNAPP (e.g., Wiz, Orca, Lacework) |
A more detailed discussion on CSPM vs. DSPM. |
Why do organizations need both DSPM and CSPM?
Organizations need both CSPM and DSPM solutions. They are separate but complementary technologies. When a CSPM leverages the rich data context from the DSPM, the security teams can focus on those alerts that impact highly sensitive data, thereby gaining a higher return on remediation efforts.
The two technologies cover different perspectives that are needed to effectively secure multi-cloud environments. One is focused on their primary user of the infrastructure team. The other is designed for data security teams that prioritize security, governance, and privacy requirements independent of infrastructure.
How does DSPM benefit the business?
Deploying a DSPM in an organization yields many benefits to security and data leaders, data security owners, data governance team members, and the users of the data (e.g., developers, data scientists). Among them:
Prevention of sensitive data exposure
In this digital age, an organization’s most important asset is its data. By focusing on the data and finding all known as well as hidden or shadow data, DSPM protects cloud data from both external and internal threats.
A reduction in the innovation attack surface
Protecting your data becomes easier when you’ve eliminated the data you don’t need. Removal of abandoned or redundant data, and the identification and remediation of all data security violations ensures proper posture enforcement across your most important assets.
Secure support for the daily activities of value creators
With DSPM and its ability to automate the validation and enforcement of data security policies, security teams have a chance to empower their cloud data users to innovate, all while protecting the company by keeping sensitive data secure, effectively decoupling data risk from data growth.
The transformation of the role of security teams from gatekeepers to innovation enablers
Traditionally, security teams functioned as gatekeepers, preventing users from taking unauthorized actions with data. Gatekeeping in today’s fast-paced, cloud environments hinders innovation and productivity. A DSPM transforms security teams from overwhelmed gatekeepers to empowered innovation enablers.
More agility and more control over data
Instead of relying on a security team to manually monitor activities, a DSPM platform will automatically keep an eye on all data creation, movement and modification, and uphold policies to protect your sensitive data. The results: everyone can create, move, copy, or modify data as they need —safely
Reduced cloud cost
Storing data in the cloud costs money month in and month out. The right DSPM has features to help organizations identify redundant, obsolete and trivial (ROT) data in their cloud infrastructure that can be deleted or eliminated to reduce cloud usage fees and reduce the attack surface.
What are the key capabilities of a mature DSPM?
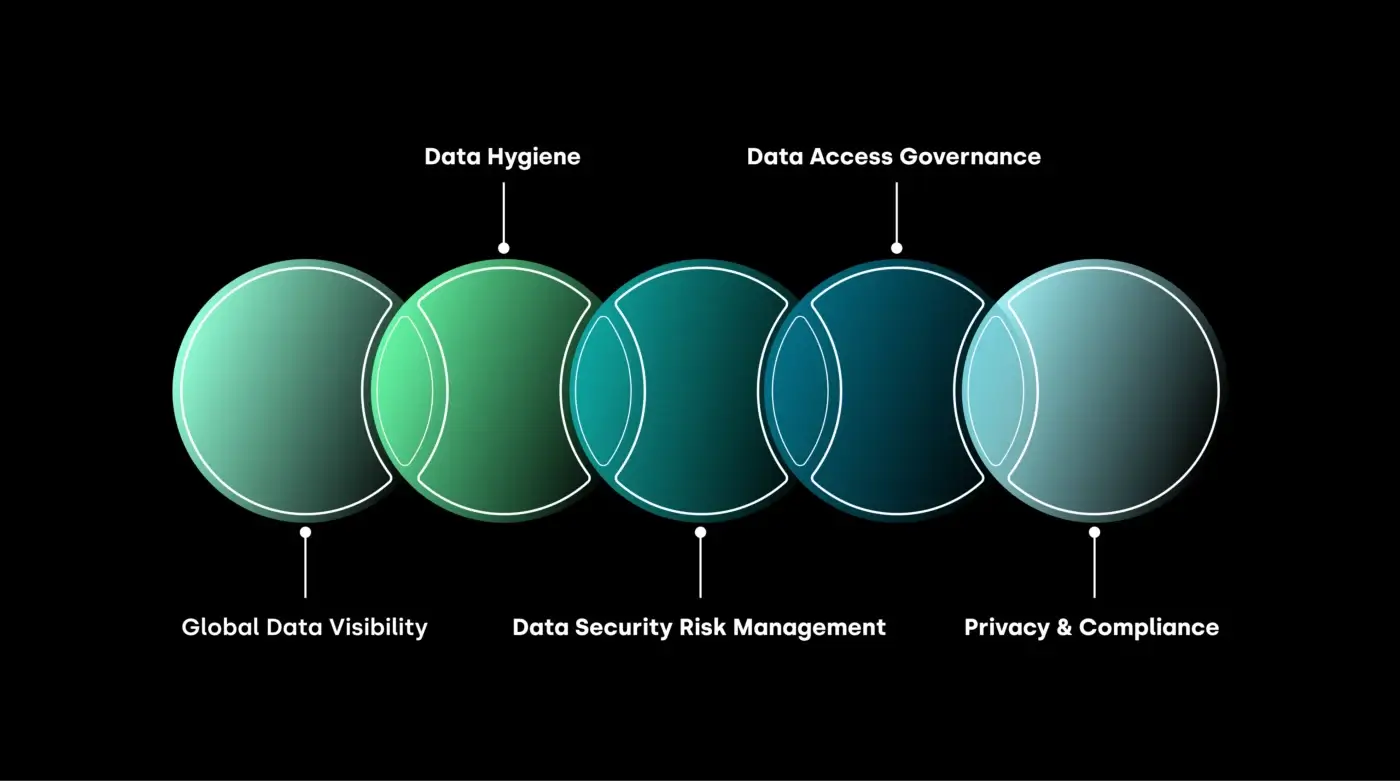
Key capabilities of a DSPM (Data security posture management) platform - Rubrik
An organization's data security posture DSPM solution should provide:
Global Data Visibility into all data (known and unknown), including type, location, owner, access, and security posture.
Data Hygiene through remediating misplaced, redundant, and obsolete data, and defining relevant policies for continuous monitoring.
Data Security Risk Management that prioritizes security issues based on data risk profile, then and detects and remediates overexposed, unprotected, and misplaced data.
Data Access Governance by identifying all internal or external users, roles, and resources with access to sensitive cloud data stores and enforcing their privileges.
Privacy & Compliance through detecting and remediating regulatory and industry compliance violations, and also generating audit-ready compliance reports.
How and when is DSPM used?
Data security, data governance, and privacy practitioners can use DSPM solutions in many ways to help keep their organization secure and compliant. The following are some of the core use cases:
Automate Data Discovery and Classification – Automatically and continuously discover and classify sensitive, proprietary, and regulated data, including shadow data, across multiple cloud environments and technologies.
Enforce Data Security Policies Automatically – Find, prioritize, and fix policy violations for all your cloud data as it travels through the cloud. Monitor security posture drift using policies aligned with security best practices, compliance frameworks, privacy regulations, and your organization’s specific needs.
Control data exposure – Pinpoint all exposed sensitive data and remediate—whether it’s misplaced data, misconfigured controls, or overexposed access.
Comply with data sovereignty – detect and create alerts when sensitive / regulated data violates data residency requirements. Gain a complete view into data store geolocations, as well as data movement across cloud environments and regions.
Control Data-centric Environment Segmentation – Get alerts whenever a user places sensitive or regulated data in untrusted or unauthorized environments, then remove this data from the segment or authorize the new environment.
Comply with Data Privacy and Governance Frameworks – Continuously enforce regulatory compliance and standards requirements for data, and streamline and fast-track evidence collection.
How do I choose a DSPM solution?
Subscribing to and installing a organization's data securitysecurity solution is a significant investment of time, effort, and money. So how can you make sure you’re choosing the best DSPM on the market? Here are a number of key features to look for:
Data discovery and classification capabilities
Specifically, these capabilities should offer:
Autonomous, cloud-native discovery & classification
The DSPM shouldn’t require you to connect to each data asset or provide access credentials. Instead, the solution should be cloud-native, utilizing the CSP’s APIs to scan your environment autonomously without intervention from your team. It should automatically detect and classify all data, including shadow data.
Continuous discovery & classification
Because cloud changes occur rapidly, you need a DSPM that continually monitors your environment for modifications. It should do so by automatically scanning for new data assets and changes to existing accounts, as well as identifying entirely new accounts.
Breadth of coverage
Most modern organizations use a plethora of CSP and data store types (not just basic object storage). The DSPM should seamlessly cover a variety of cloud environments and read from various databases, data pipelines, object storage, disk storage, managed file storage, data warehouses, lakes, and analytics pipelines — both managed and self-hosted.
Depth of coverage
The DSPM must discover and classify all sensitive data — whether it’s in a structured, semi-structured, or unstructured format. It should also work alongside several self-hosted databases that contain different configurations and file formats.
Intelligent classification
To identify sensitive data with minimal input and reduce false-positive/false-negative rates, the DSPM should use multi-step, intelligent classification beyond regular expression matching (reg-ex). Look for a solution that ensures accuracy by evaluating the context of the data type.
Low cost of scanning
To keep scan costs down, the DSPM should skip redundant data and use responsible sampling techniques when appropriate. It should also avoid rescanning data if it hasn’t changed.
Security by design
The DSPM solution should never remove data from your environment into the vendor’s; it should always scan the data inside your environment. This security measure prevents additional risk.
Data security policies framework
The framework should provide:
Both built-in and custom policies
This selection of policies should address all categories of sensitive data violations: overexposed, unprotected, misplaced, redundant, and non-compliant data. And because no two organizations are alike, a DSPM solution must allow for easy customization to meet each organization’s individual needs.
Multiple factors for risk prioritization
Risk prioritization should consider multiple factors such as data sensitivity level, data volume, data exposure, and data security posture. It should also allow for customization.
Context and Guided remediation for policy violations
When a DSPM detects a policy violation, it should provide granular context such as an event timeline, detailed evidence, describe how the violation occurred, and offer technology-specific actionable next steps for remediation.
Operationalization for your whole organization
The solution should be practical for your organization to use, with features like:
Zero disruption architecture and seamless system integrations
The DSPM should be agentless and asynchronous, and easy to deploy. It should also integrate seamlessly with your existing workflows and tools. Ideal integrations include multiple CSPs and data warehouses, CSPMs, enterprise data catalogs, ITSM tools, SIEM and SOAR tools, team communication services, and privacy and governance management tools via APIs.
Installation simplicity and fast time-to-value
Installing a DSPM should be simple, with a short deployment time and no need for connector configurations or credentials. Expect to see significant results within a week of installation.
Self-explanatory features and access to support
It should also have a modern, easy-to-use interface with self-explanatory features. And if your team has questions or concerns, the DSPM provider should offer a wide variety of self-service resources, technical documentation, and expert support.
Unified Console
The DSPM should offer centralized reporting and drill-down views based on governance, privacy, or security functions.
All of these factors combine to make the best DSPM platforms. Here is a quick checklist to use when reviewing:

DSPM Checklist: Quick Data Security Posture Management Evaluation Checklist by Rubrik