Cyber risk is growing. Ransomware attacks alone have jumped by 700% in 2021. While the Colonial Pipeline shutdown is the most recent high profile ransomware disaster, there have been many others—jeopardizing data assets and ongoing operations for all types of organizations. What’s even more alarming is that an estimated two out of three ransomware attacks target backup systems. And despite massive investments in perimeter, endpoint and application-layer security defenses, attackers are still successfully gaining access to data.
The Zero Trust (ZT) model of security is showing a great deal of promise in this regard. While Zero Trust has traditionally been used as a network security model, the principles also apply to data security and security architecture in general. ZT extends the principle of “least privilege” to its ultimate conclusion: Trust no one and grant the least privilege, so that once a user’s identity is verified, they only get access for the role they’re assigned - nothing more. It is the opposite of the prevailing “trust but verify” model of access control that allows users with basic credentials to have broad access to digital assets. Instead, ZT takes a “verify but trust” approach that closes off access until the user’s identity is confirmed, and then only grants the minimal access privileges to complete the assigned task.
Addressing the challenges with the “trust but verify” approach
John Kindervag, the renowned Field CTO of Palo Alto Networks who is credited with creating the Zero Trust model, offered an insight that should inform any discussion of protecting data from malicious actors. He said, “Trust is the foundational problem of all cybersecurity.” Who can you trust with access to your most precious digital assets? The answer is seemingly simple. Anyone who is on the list of trusted people should be granted access. However, as we know, life isn’t that simple, especially today. How can you know that a person is who they claim to be? What range of sensitive data access should you entrust to this person?
The great complication in this thought process comes to life in another brilliant observation by Kindervag. He said, “Trust is a human emotion injected into digital systems.” Computers in their raw, natural state are dumb, and oh so naïve. They’re machines. They lack guile, a quality well represented by the human race. To compensate, one must design the ability to establish trust into systems and security architecture as a whole.
Defining Zero Trust Architecture
A number of definitions of Zero Trust are available across the industry. Rubrik follows the model defined by the National Institute of Standards (NIST), which publishes the NIST SP 800-207 Zero Trust Architecture Specification. As NIST puts it, ZT comprises “an evolving set of cybersecurity paradigms that move defenses from static, network-based perimeters to focus on users, assets, and resources.” In the NIST view, a Zero Trust Architecture (ZTA) uses ZT principles in the creation of enterprise infrastructure and workflows.
To be effective, ZTA never assumes implicit trust based on a user’s physical or network location. For example, just because a user is logged onto the Local Area Network (LAN), that should not entitle him or her to see any specific data available on the LAN.
Nor does asset “ownership” matter. If user X is listed as the owner of a database, user X still needs to establish who they are before being allowed to access their database. ZT solutions use tools like Multi-Factor Authentication (MFA) to authenticate users and then authorize discrete access permissions. As shown in Figure 1, ZT separates the control plane from the data plane with a policy enforcement point.

Rubrik zero trust data security
Rubrik operationalizes ZT with its Zero Trust Data Security™ solution. At its core, Rubrik DataGuardian™ technology comprises policy definition and enforcement points that never expose backup data via open protocols. It supports a purpose-built file system that creates a logical airgap which blocks data from being discoverable or accessible over the network. The solution first identifies authorized users via MFA. The policy engine then grants least privilege access based on the user's specific role using robust RBAC controls. In this way, Rubrik’s Zero Trust Data Security™ combines robust user verification with policy-based data protection. Figure 2 shows how these elements fit together.
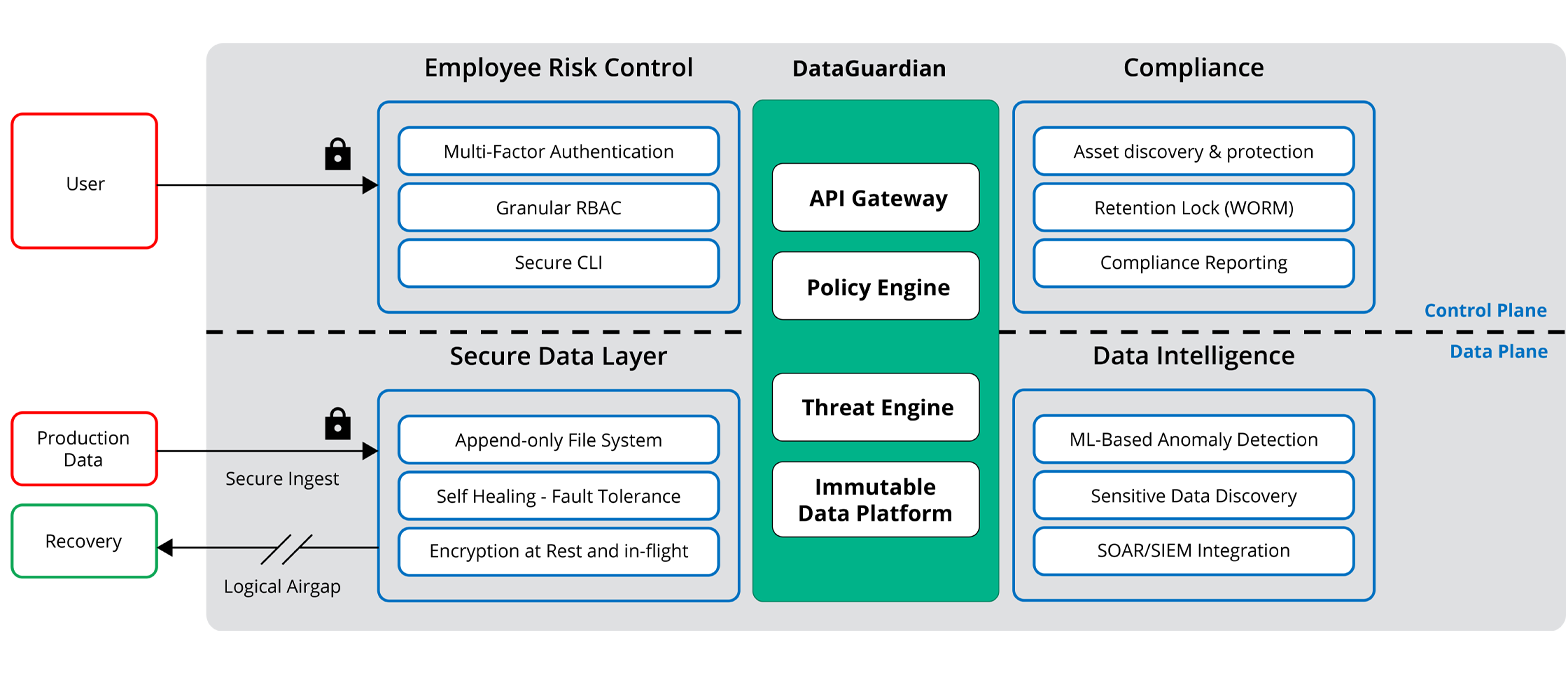
In addition, data written to the Rubrik system cannot be modified, deleted, or encrypted by an attacker. This ensures that a clean copy of the data will always be available for recovery. The solution inspects and logs traffic as a countermeasure against malicious data access and manipulation. It then embeds multiple expert-guided recovery options. These include LiveMount and Mass Recovery. IT teams can utilize these tools to quickly recover any files or workloads affected by an attack.
User and Employee Risk Management
As previously noted, Rubrik features built-in MFA. This control enables the careful user verification required for success with the Zero Trust data protection model. Attackers cannot gain access to Rubrik-managed data even if they have stolen credentials to the domain. For legitimate users, RBAC governs access to data, enforcing least privilege access. The solution only grants access for whatever specific actions that the user needs to perform, as defined by policy. Rubrik secures communications to all system interfaces, including Command Line (CLI) and Application Programming Interface (API) access, unlike other data management solutions.
Secure Data Layer
Rubrik offers a secure data layer, where data is always encrypted. This policy applies whether data is at rest or in-flight across sites or clouds. A proprietary append-only file system permits data to be added to a file, but never deleted. The solution also performs data integrity checksums throughout the data lifecycle to ensure data loss prevention and to mitigate the risk of unauthorized data modification. Data is always secure and available, even in the event of cluster node failure, due to a self-healing web-scale design.
Compliance
No matter where data resides, the solution applies Service Level Agreement (SLA) policies based on automatic data classification and discovery across data centers and public clouds. The solution’s Retention Lock prevents malicious actors from reducing or removing data retention policies that could lead to data deletion. Additionally, the Rubrik solution generates compliance reports which simplify the audit process.
Data Intelligence
Rubrik’s ZT solution features machine learning-based anomaly detection that discovers threats automatically. The solution can also scope the blast radius of an attack and make recommendations about the best possible recovery points. API-integration with popular security operations tools enables strong collaboration between IT and security groups for faster incident response processes.
Conclusion
Zero Trust is gaining prominence as a viable defense against ransomware and other serious cyber threats. With ZT, IT teams can better protect data, and be better prepared to recover data and applications without paying a ransom. Application owners can be confident that their data is safe and that applications will be quickly restored in the event of an attack. C-level executives get an improved ransomware defense strategy, which helps with cyber insurance costs and reduces the risk of financial losses and reputational damage from ransomware attacks. And the entire organization in between benefits in the process.
To learn more, visit rubrik.com/ransomware.


