Being hit with a ransomware attack is one of the worst threats IT and Security teams can face. But it often turns out that another threat, the phantom menace, is the possible exfiltration of the data to leak or sell it on the dark web. Cyber criminals know that some organizations may have a chance to recover some of their data from backups, even if it will take a while. So instead of just encrypting the files, or the backups, they will also try to exfiltrate the data first, threaten to publish it, and thus apply more pressure to pay the ransom.
When organizations are facing a double extortion, they may not even know the contents of the data that was encrypted by ransomware or what is in the data that may be leaked. Is it sensitive personal data, banking data, health data, or the company’s IP? Between the panic, scramble, and the race to bring back the business, paying the ransom seems to be the quickest way out.
Luckily, there is a new hope in the fight against cyber criminals and phantoms. Rubrik enables customers to mitigate ransomware attacks so they don't have to pay the ransom and there is a way to discover what was in the encrypted data. Knowing what data may have been exfiltrated can help you prepare for a potential data breach and guide you in your negotiations with the criminals. Moreover, Rubrik ensures that any new added workload is automatically protected and ensures that backup policies are applied, thus eliminating further vulnerabilities and ensuring compliance with business requirements.
All this is possible with Rubrik Zero Trust Data Security™ architecture which provides security at the point of data. It helps to ensure you can now protect critical data from ransomware attacks, leverage secured backup data to perform attack forensics, and initiate recovery operations quickly to maintain business continuity.
Rubrik Zero Trust Architecture
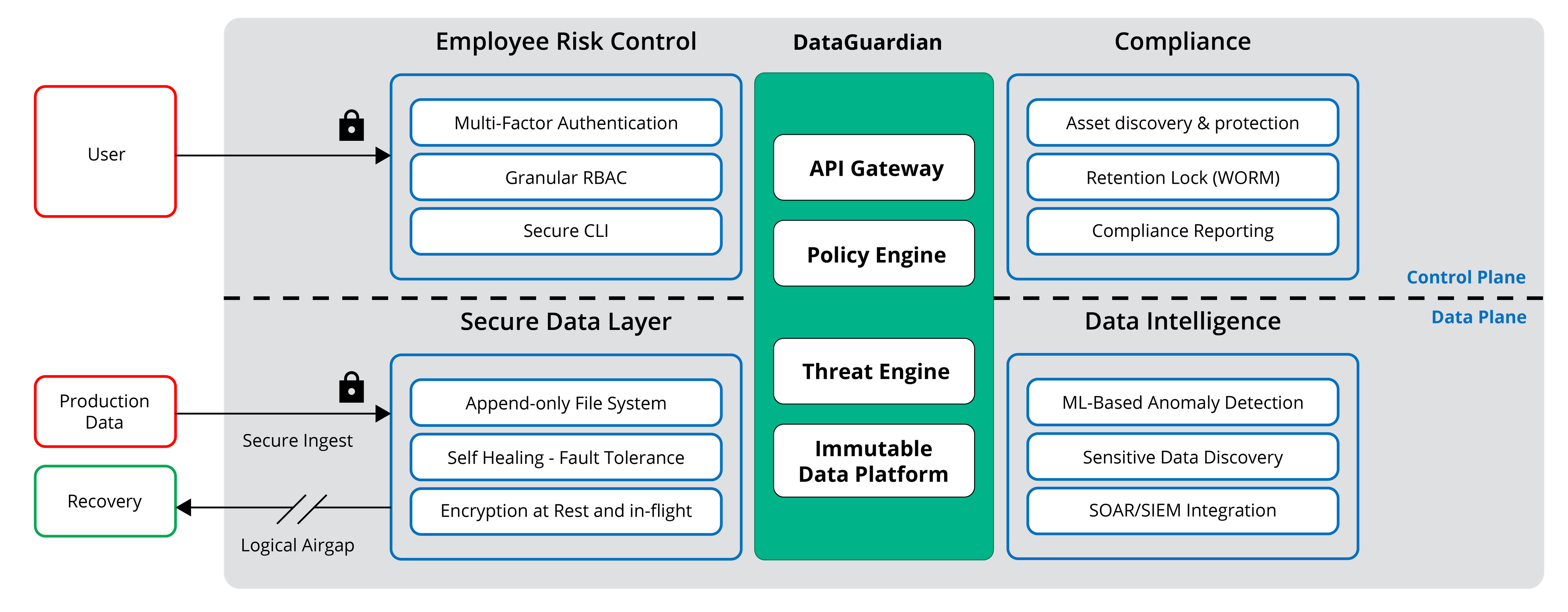
Compliance, a fundamental component of the Rubrik Zero Trust architecture, ensures that all workloads are automatically protected, backups can be locked to prevent tampering with, and specified contents of data that may have been exfiltrated can be identified.
Discovery, classification, and reporting on data is done via Rubrik Polaris Sonar. Sonar applies machine learning to scan and indexes the data and does not have any impact on the production environment. You simply leverage existing Rubrik deployments to process the backup data and metadata with zero additional infrastructure required and no installations of agents. The scanning and classification of the data is done with Analyzers, where a user defines the type of sensitive data that Sonar should be discovering, and Policies, which are a logical grouping of one or more analyzers that are associated with the specific objects, like VMware VM, NAS filesets, Windows filesets, and Linux filesets, for example.
By automating the process, you can drive consistent, repeatable monitoring of your data for instant visibility into where the data is stored, apply policies that alert you to policy violations, and proactively ensure data controls.
With Compliance, as part ot the Zero Trust architecture, you get to:
Minimize vulnerability with Asset Discovery and Protection: discover all assets with few API calls across your environments, from the data center to public cloud, and automatically apply SLA policies. When a new workload is added, it will be automatically protected and the backup cannot be corrupted by ransomware. You can periodically run an “Unmanaged Objects Report” to discover any virtual machine, database, fileset or cloud workloads without an assigned SLA and bring them under compliance, thus eliminating human error and ensuring you are always in compliance with your SLA policy and all workloads are backed up.
Prevent malicious actions of rogue users and intruders with Retention Lock: ensure no single person can clear or shorten retention policies or delete snapshots, archival or replication locations. The security of Retention Lock is controlled through a validation process within the Rubrik Compliance Team, who are part of the Support Team. If a modification to a retention locked SLA is requested by a customer, two appointed individuals from the customer’s organization are required to authenticate and acknowledge the modifications with the Rubrik Support Team. This is especially important in heavily regulated industries requiring WORM compliance, SEC Rule 17a-4(f) and FINRA Rule 4511(c) for example.
Mitigate sensitive data exposure with Compliance Reporting: proactively scan your backups to identify certain types of sensitive data and its location. By applying predefined or custom Policies, Rubrik can identify certain types of data that are governed by applicable privacy laws, such as GDPR, HIPPA, PCI-DDS, and others, and when needed, quickly produce reports on some types of regulated data or policy violations.
Rubrik is a holistic solution that can give IT teams the confidence that their data is always secure and available, while helping withstand a data breach or ransomware attacks. By automating the protection of new workloads and helping identify at-risk and non-compliant data, organizations can avoid reputation, financial, or legal damage and consequences associated with a ransomware attack and double extortion.
To learn more about how Rubrik can help your organization, check out our Achieving Security at the Point of Data webinar.
