Werner Vogels, CTO of AWS, has taken to wearing a T-shirt during his recent keynote speeches with the admonition, Encrypt Everything. This statement highlights the growing concerns over unauthorized access of data and regulations like the General Data Protection Regulation. Encrypting everything is no longer just a nice-have, it’s a must-have for any business with workloads running in a public cloud. The challenge for most customers is knowing what encryption method to choose and how to properly manage their encryption keys. Making the wrong choices can leave a customer’s data as unprotected as it would be with no encryption at all.
AWS, as well as other cloud providers, offers a number of options for simplifying the encryption of data in transit and at rest. This includes the capability to encrypt data stored in a customer’s Amazon Elastic Block Storage (EBS) volumes. This feature can be enabled with a check of a box, and the encryption is automatically handled using the AWS Key Management Service (KMS). To ensure end-to-end encryption, including when a snapshot of an Amazon EBS volume is taken and backed up, AWS will automatically encrypt the snapshot of any encrypted Amazon EBS volume. Supporting this capability is now table stakes for any cloud data management solution.
We previously announced Amazon EBS snapshot support in Rubrik Polaris, our SaaS platform for cloud data management. This includes the ability to create and restore a new encrypted volume from a snapshot and to create and restore a new encrypted volume using a different AWS KMS encryption key than was used to encrypt the original volume and snapshot.
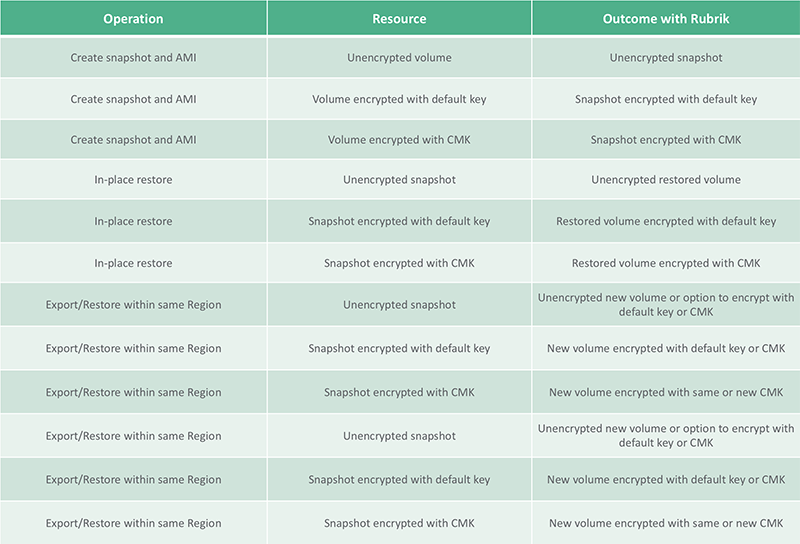
The table below outlines the different encryption options available using Rubrik Polaris. They differ slightly from what is available in our Cloud Data Management product in that Rubrik Polaris supports the ability to change the Customer Master Key (CMK).
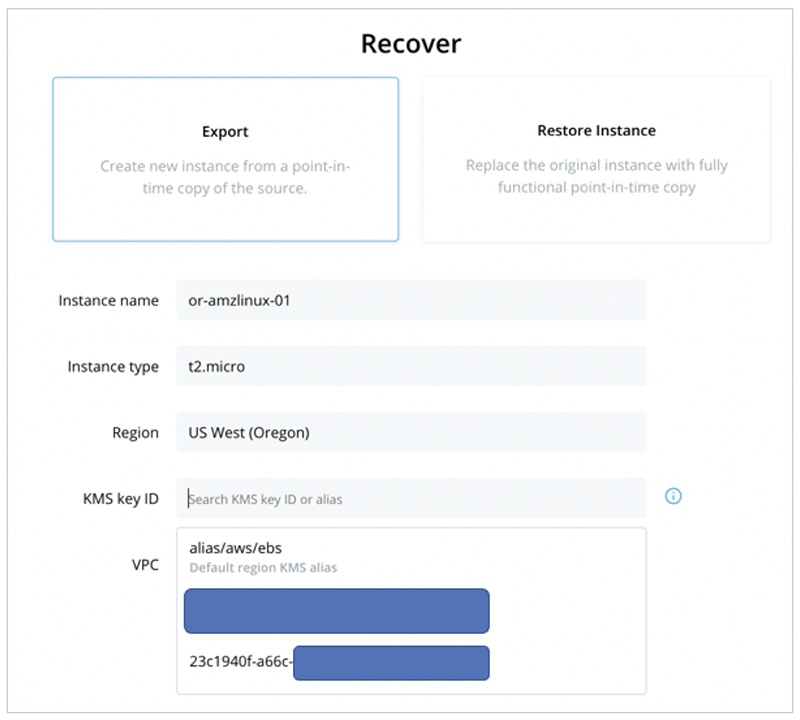
As an example, the screenshot below shows an Export operation in Rubrik Polaris where a KMS key ID can be defined for the new volume, using the default key or a CMK.
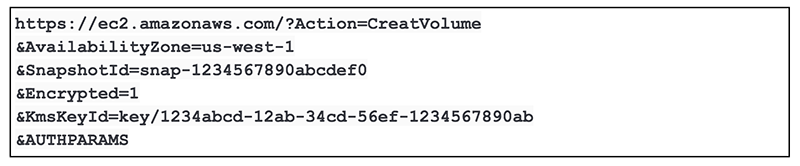
When a user creates a new encrypted volume from an encrypted snapshot, Rubrik Polaris initiates an API call similar to the one below. In this example, we are creating the new volume using a different CMK form the source. If a key is not specified, the default key is used.
Rubrik Polaris integrates with and leverages the standard AWS EC2 APIs for managing Amazon EBS snapshots to keep up with new innovations in AWS and ensure consistent results when protecting customer data. All the while, customers get the benefits of a simplified interface, automation of backup processes, and a consistent process for data protection. For more information, explore our approach to native protection for AWS.
