As more organizations confront ransomware threats, IT teams must take proactive steps to protect data and applications, which have become a high-value target for attackers. One of these steps is enabling multi-factor authentication (MFA) wherever possible, especially in the backup environment.
MFA is an effective method of security that validates a combination of factors requested of the user, with the most common one being their credentials, and the second (or more) being a Time-based One-Time Password (TOTP), biometric, or a key card. MFA can most easily be understood as something you know and something you have. This additional authentication mechanism mitigates cyber attacks when an account is compromised, and reduces unauthorized access, since the attacker needs to pass the required combination of factors during authentication.
Without the security benefits of MFA, an attacker only needs compromised user credentials to gain system access (single-factor authentication). This is where traditional backup systems often fall short, and are targeted during a ransomware attack in an effort to eliminate the ability of the victim to recover their applications or data, and increase the likelihood of a ransom being paid.
Rubrik views backups as the last line of defense against ransomware. With the prevalence of compromised credentials through phishing attacks and social engineering, a username and password alone is never an acceptable level of access security for backups. This is why Zero Trust Data Security™️ and defense-in-depth security are strategies employed by Rubrik for securing the backup environment and stored backup data. One of the Rubrik features that emerged from this approach is a native multi-factor authentication (MFA) via a time-based one time password (TOTP), that provides protection of a backup environment when an account is compromised.
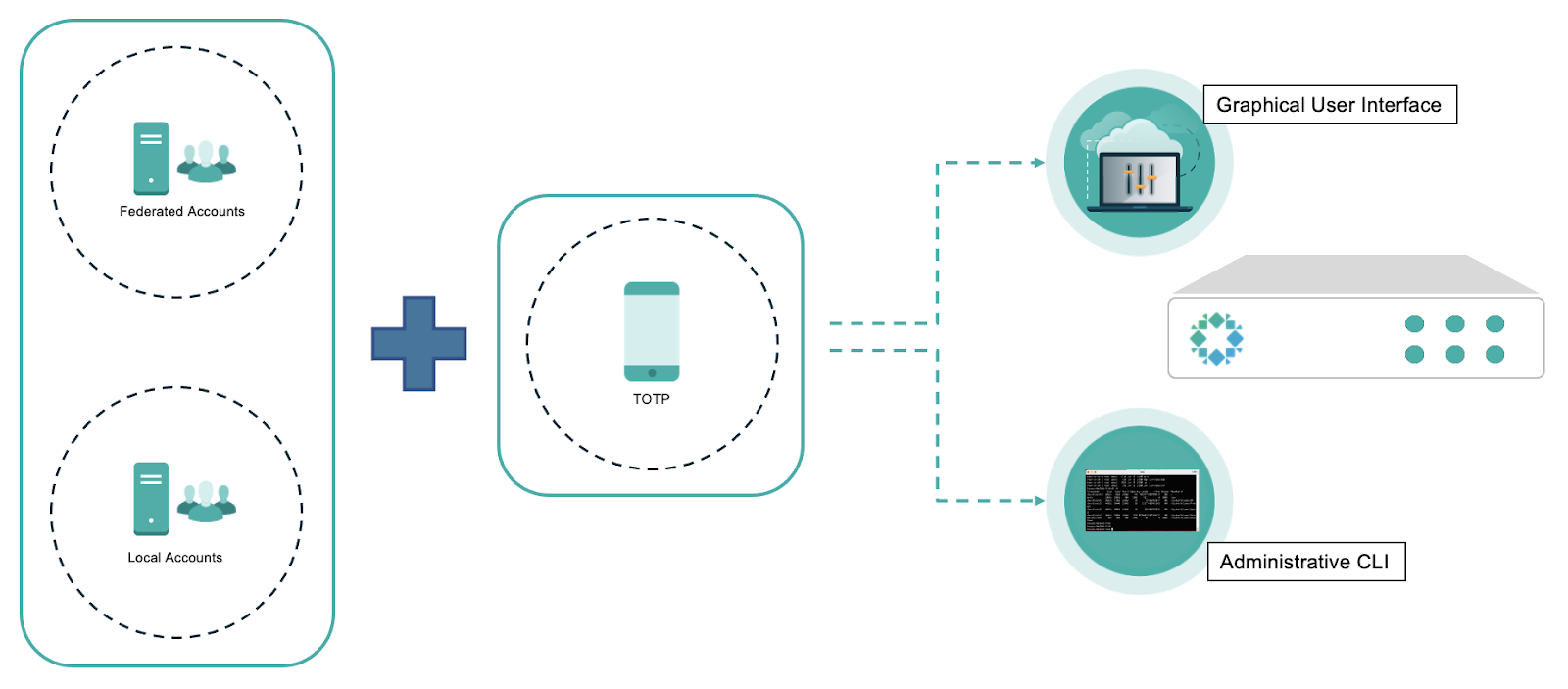
An important note is that both the graphical user interface (GUI) as well as the administrative command line interface (CLI) should enforce MFA. Attackers often scan and probe common ports and protocols to identify potential attack vectors, and if MFA doesn’t encompass these interfaces, it is very possible that data is protected by basic authentication only.
TOTP is a widely accepted, and broadly integrated algorithm with MFA that is based upon RFC-6238 from the Internet Engineering Task Force (IETF) and is often adopted due to enhanced security features, such as a shortened passcode expiration that typically ranges from 30-90 seconds. The MFA solution in Rubrik is self-sustainable, and provides MFA for both federated accounts (Active Directory or LDAP), as well as local accounts of the system. Additionally, Rubrik has the capability to integrate with existing SAML 2.0 identity management (IdM) solutions (RSA, Duo, Okta, etc.) most of which can support MFA. You can learn more about covering the ease of configuration and simplicity of a Rubrik MFA implementation with the Microsoft Authenticator application here.
Targeted ransomware attacks on organizations will likely continue to rise and apply pressure on IT to assemble,or modernize, their cyber incident response plan. Enabling MFA wherever possible in the environment (especially backups) is a critical step to help mitigate the threat of ransomware. Without a solution in place, a compromised credential could easily escalate to where IT teams can no longer recover applications or data, and the organization is forced to pay a ransom. As a part of the Rubrik Zero Trust Data Security architecture, MFA provides customers with a simple deployment and a strong defense against compromised accounts.

