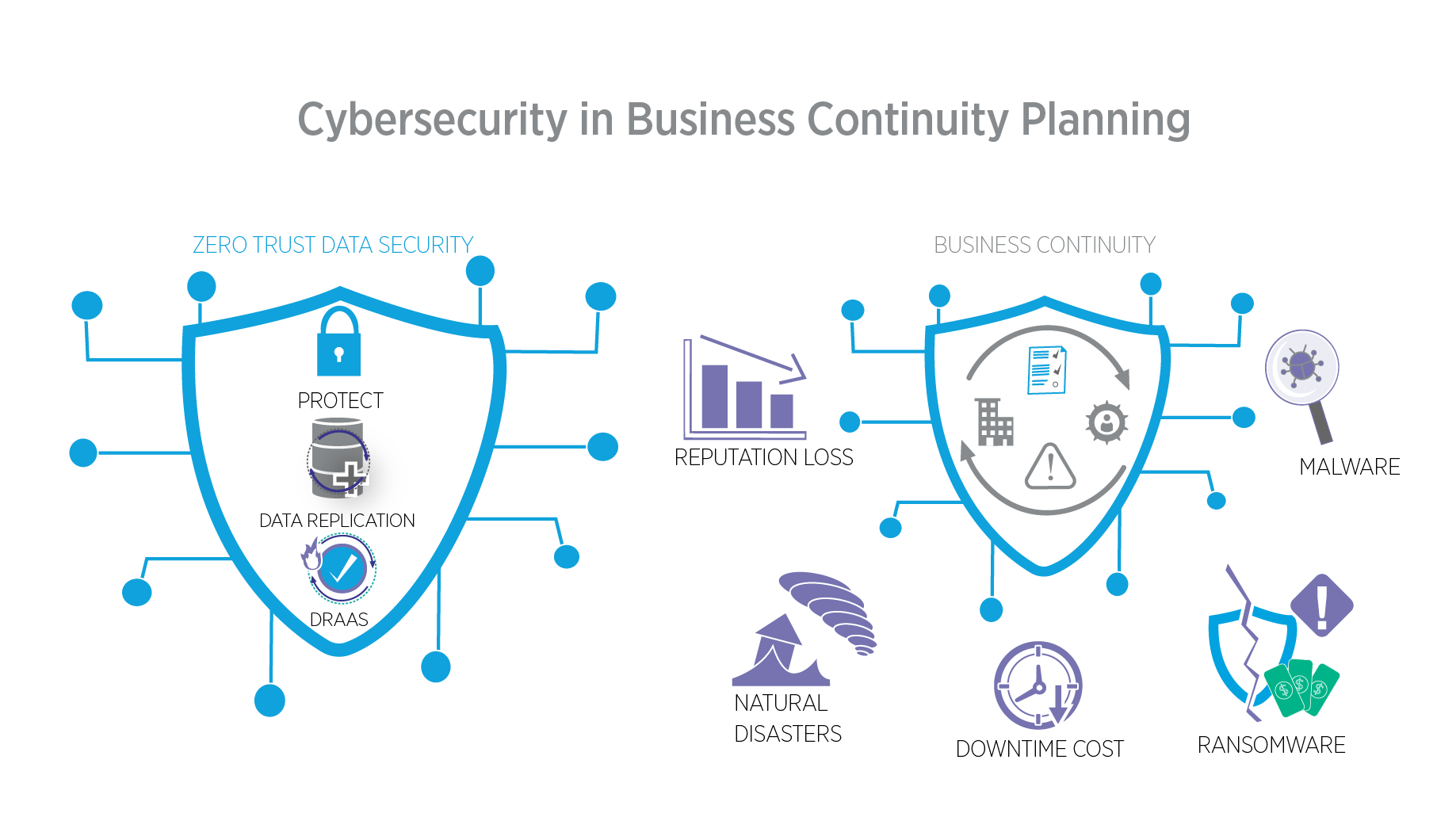
Business continuity planning often centers on large-scale disasters—tornadoes, floods, hurricanes, etc. More and more, however, cyber threats have become a major focus point for business continuity and disaster recovery (BCDR) planning, which is why cybersecurity must be accounted for in your business continuity strategy too.
Importance of Cybersecurity in Business Continuity Planning
Hacks and other forms of cyber attacks can have just as dramatic results for data and systems as any natural disaster. As such, integrating cybersecurity into your BCDR planning is crucial to maintaining IT reliability and application security in the modern age. Some of the reasons why this is so important include the following:
Unplanned Downtime is Costly
The events during the period after an attack are critical, but too often, they’re characterized by prolonged periods of downtime as your organization reels from the impact. Every hour your organization spends offline costs thousands (at least), made worse by the fact that unplanned downtime—as often occurs after an unanticipated cyber attack—is 35% more costly than planned downtime.
Both small and large businesses can have difficulty recovering from the costs of major downtime events, so being prepared to return to normal operations as quickly as possible is essential.
Reputation Loss
Potentially more expensive is the loss of reputation that results from an attack. These events indicate to the public that your network security and their data may not be all that secure in your hands, making it more difficult for them to trust your organization in the future. On average, the monetary damage caused by a single information security incident amounts to around $8,000 for small or medium businesses. For enterprises, that figure can reach as high as $200,000.
Multiple consecutive incidents may not even be survivable businesses without a solid recovery plan in place, making it crucial to prepare for the worst point in time.
Lost Data and Systems
Finally, cyber attacks may render data completely irrecoverable. Lack of immutable backups or recovery systems could make it difficult, if not impossible, to restore your data to a safe pre-attack state. Ultimately, this could mean lost potential down the line as relationships with clients, customers, partners, and suppliers are undermined.
Cybersecurity Strategies for Business Continuity
The types of strategies used in cybersecurity have vital applications when it comes to business continuity. Making sure your business can carry on as before is a function of the way your data is managed, stored, and protected. Some of the cybersecurity strategies utilized in BCDR include the following:
Data Replication
Keeping data in multiple repositories is good practice since it allows for quicker, more reliable data recovery after a disaster. Note that it’s not quite the same as data backup, which focuses on creating backups of historical data. Rather, data replication creates replicas of your business-critical data and stores it across your network to protect it from cyber attacks.
Disaster Recovery
Disaster recovery services—including mass data recovery—are, of course, central to any business continuity plan, but they are especially important when it comes to protecting your business from cyber attacks. Compromised data may be lost, corrupted, or contaminated with ransomware or malicious software, rendering it unusable.
The recovery process needs to be structured in a way that prevents reinfection. As such, there should be no risk that whatever attack compromised your apps, systems, or data could affect it again after you restore your operational functionality. Disaster recovery as a service (DRAAS) is a modern way to handle this process without having to dedicate exorbitant resources and infrastructure to your business continuity management plan. As a proactive cyber security preparedness measure, the addition of automated cyber recovery testing and validation prepares your organization against cyber attacks.
Zero Trust Data Security
The nature of most business’s data today is rarely centralized as it was in days past. As such, a system of firewalls and perimeter defenses—the traditional “castle and moat” approach—is no longer sufficient for modern cybersecurity needs. You can’t conceivably draw a moat around each point of data, and even if you could, any breach in one would lead to compromised systems across your organization.
Zero trust data security is far better suited to present-day applications since it verifies users and controls access to critical functions at every point within your network, not just on the outside perimeter. This process allows threats to be identified faster, expediting recovery after an attack while mitigating its overall impact.
Integrate Zero Trust Data Security into Your BCDR Plan
Integrating Zero Trust Data and Security solutions into your business continuity and disaster recovery plan is a highly effective way to mitigate damage from cyber attacks in the future. Security protocols that extend to every facet of your network and account for the interdependencies of your systems allow for faster recovery in the event of a disaster. In addition, insider attacks are less likely to be carried out successfully, saving your organization the costs of unplanned downtime.