Ransomware hackers today are getting smarter and more sophisticated. The new object of their desire is often your backups, and the only way to protect them is to keep them inherently secure. This is why security must begin at the point of data.
As detailed in our previous blog, a Zero Trust Architecture (ZTA) trusts nothing and assumes that all users, devices, and applications are untrustworthy and may have already been compromised. Trust nothing. Always verify. The strategy is to reduce the risk of intrusion and limit the ability of hackers to remove your last line of defense, your backup data. With Zero Trust, only authenticated users are granted access to data, permissions are limited, and all system interfaces are secure.
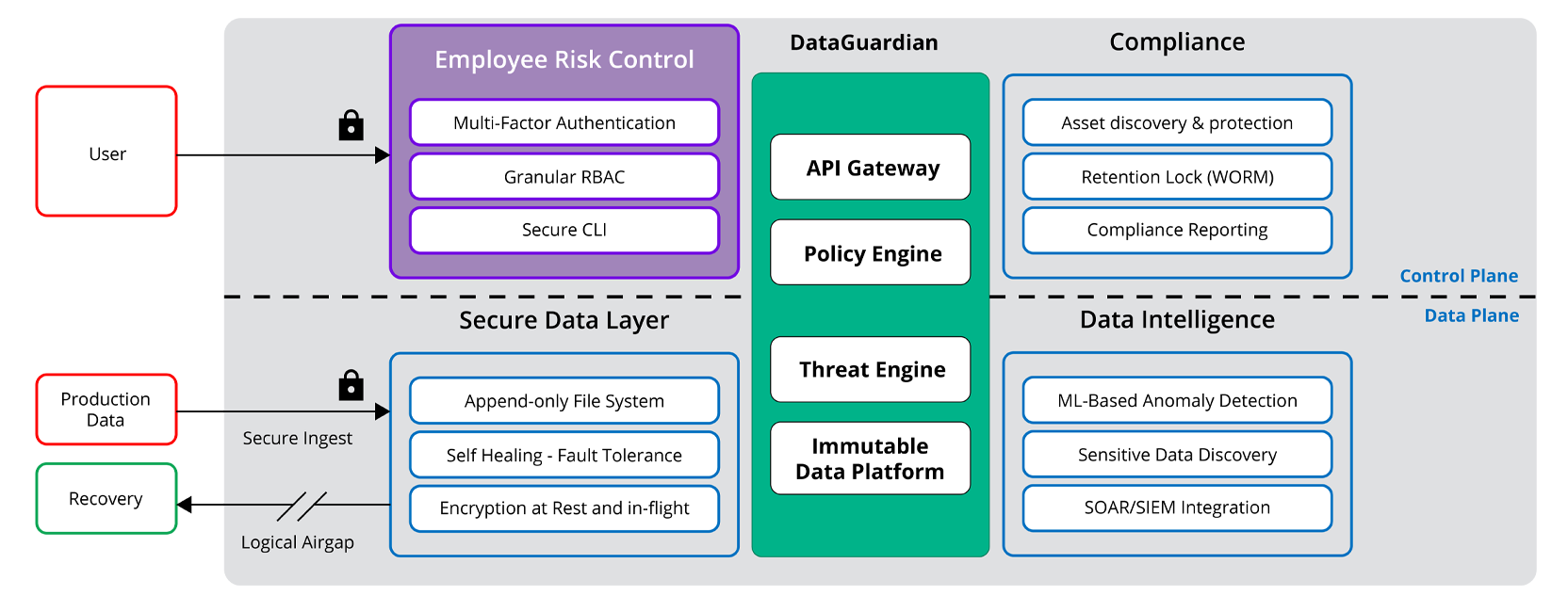
Zero Trust and Intrusion Risk
Intrusion risk control is a critical component of the Rubrik Zero Trust Data Security™ architecture, incorporating three important methodologies:
Multi-factor Authentication (MFA)
Granular Role-based Access Controls
Secure Command-Line Interface
Let’s take a closer look at these secure data protection techniques for user and employee risk management and see how Rubrik puts them into practice.
Multi-Factor Authentication
Following the principles outlined by the National Institute of Standards and Technology (NIST), Zero Trust requires that user identity be verified beyond a simple username and password. Should a user fall prey to a phishing attack, for example, their compromised credentials could allow an attacker to access privileged systems, including your backup systems, and threaten the organization’s ability to recover from a ransomware attack.
Rubrik stands out in the data protection industry with native Multi-factor Authentication (MFA). Using a Time-based One-Time Password (TOTP) method to implement MFA, the TOTP algorithm automatically generates an authentication code that changes after a certain period. In the case that an attacker was to obtain a user's login password, because that passcode is one-time and time-based, they would not be able to easily access the backup system and compromise backup data.
At Rubrik, MFA is available for local, Lightweight Directory Access Protocol (LDAP) and Single Sign-On (SSO) accounts. Rubrik integrates with SAML 2.0 Identity Providers (IdP) for SSO authentication, enabling users to access multiple applications with a single set of credentials. Rubrik users can register their device for two-step verification and utilize freely available applications - most of which also support MFA -- such as Google Authenticator, RSA SecurID, Microsoft Authenticator, or Cisco Duo Security.

Simply install your preferred application on your iOS or Android phone, load the app (no internet connection required), scan the QR code that appears, and enter in the one-time passcode to verify setup. Watch this demo to see how it all works. In addition, administrators have the option to enforce two-step verification for all users or for a certain set of users.
Note that if you’re utilizing an SSO provider, you should implement both SSO and MFA. The two are not mutually exclusive. By enabling TOTP, attackers cannot gain access to your backup data, even if your active directory is compromised and attackers obtain stolen username and password credentials or try to bypass SSO via your local accounts. Utilizing both SSO and MFA adds additional security.
Granular Role-Based Access
An additional form of data governance and prevention comes from Role-based Access Control (RBAC). RBAC restricts access based on an individual’s role within an organization, with different roles having different access privileges. Limiting access based upon role can greatly reduce the risk of data breaches.
Employees are only granted access to perform their specific job duties, and nothing more. This is the principle of least privileged access. Even if a user is successfully authenticated, if they are not assigned to perform a specific task as defined by policy (based on factors such as authority, responsibility and job competency), then they are not granted access rights.
Rubrik makes it easy to assign granular RBAC permissions, and integrate with Active Directory. MFA first verifies user identity, then the policy engine grants least privilege access based on the user's specific role. In this way, RBAC enhances the user verification of MFA.
In the case of an attacker stealing credentials from a user with approved access to your data, RBAC can drastically reduce the impact of account compromise, especially when it comes to ransomware. With Rubrik, for example, even if a hacker theoretically were able to access the Rubrik system with the desired set of stolen user credentials, factory reset commands are proactively disabled. This provides an important additional security measure. Similarly, if an individual Rubrik node or cluster reset is required, it requires contacting Rubrik Support and providing Rubrik with provable credentials.
Secure Command-Line Interface
Rubrik was built to secure and protect system interfaces. This includes protection for Command Line Interface (CLI) via the one-time passcode functionality. With the addition of TOTP for CLI, an additional layer of security prevents web security vulnerabilities such as OS command injection attacks from allowing an authenticated attacker to remotely execute arbitrary code on Rubrik-managed systems.
As the leader in Zero Trust Data Security, Rubrik continues to enhance platform security to keep backup data protected so you can successfully recover from ransomware attacks, and never pay a ransom. See how Yuba County was able to recover from a ransomware attack, paying $0 in ransom, recovering 100% of backups within 7 days, all using Rubrik Zero Trust Data Security solutions.

