Microsoft 365 isn’t just your collaboration suite anymore. It’s the backbone of your identity infrastructure, your AI strategy, and your most sensitive business data. But as its value has grown, so has the size of its bullseye.
The facts speak for themselves:
70% of cyberattacks over the past 4 years targeted M365
275% year-over-year surge in ransomware attacks on Microsoft customers
74% of ransomware victims saw their recovery options partially or fully compromised
50% of orgs suffered Active Directory (AD) attacks in just the last two years
This isn’t about whether M365 will be targeted. It’s about how quickly you can detect, respond, and recover—and whether identity compromise will take recovery off the table entirely.
So what are you supposed to do about it?
The Identity Threat Is Real
Attackers aren’t just encrypting files anymore. They’re targeting the very systems that govern access—AD, Entra ID, user credentials. With the right access, threat actors can escalate privileges, delete backups, and hide in plain sight. The average breakout time? 48 minutes. Lateral movement? Sometimes in under one minute.
At Rubrik Forward, Rubrik’s definitive virtual summit for organizations committed to complete cyber resilience in an era of relentless attacks, Microsoft’s GPS Architect Jim Prusak, explained the threat in stark terms. “Threat actors are adapting faster than organizations can respond,” he said. “They’re not just breaking in, they’re logging in.”
Microsoft Cloud Solution Architect Travis Wynn elaborated: “They’re targeting recovery itself. If they take out your identity and backup, they know you’re more likely to pay,” he said.
Native Tools Aren’t Enough
Microsoft protects the infrastructure. But because of something called the shared responsibility model, you’re on the hook for the data and identity inside that infrastructure. Native tools like Recycle Bin or Litigation Hold were not designed to stop blast radius expansion. And they won’t help if AD is down. Without orchestrated recovery or visibility into data risk, most organizations are flying blind.
Given the reality of the shared responsibility model, most enterprise cloud environments should consider third-party cyber resilience solutions. Finding the right solution starts by asking the right questions:
Can I embrace an effective cyber posture by reducing the surface area of attack?
Do I have the right cyber recovery capabilities to recover my M365 service quickly?
Rubrik Delivers End-to-End Resilience Across Four Pillars
In a Forbes article from 2024, Rubrik CEO Bipul Sinha defined the concept of cyber resilience for New York Times bestselling author Keith Ferrazzi. “Knowing that cyberattacks are inevitable, leaders must do advance work, to have the policies, systems and strategies in place so that when the attack happens, the business can keep moving forward,” he said.
“But the work doesn’t end there. You must learn and evolve in the aftermath of every attack to get stronger. And that requires a new organizational mindset.”
So how do you achieve cyber resilience? Here are four pillars that can add end-to-end resilience to your enterprise computing platform:
1. Immutable Backup + Air Gap
Create clean, locked-down snapshots across Exchange, OneDrive, SharePoint, and Teams—with a logical air gap in Cloud Vault. Even if attackers breach your tenant, they can’t alter or delete what’s been sealed away.
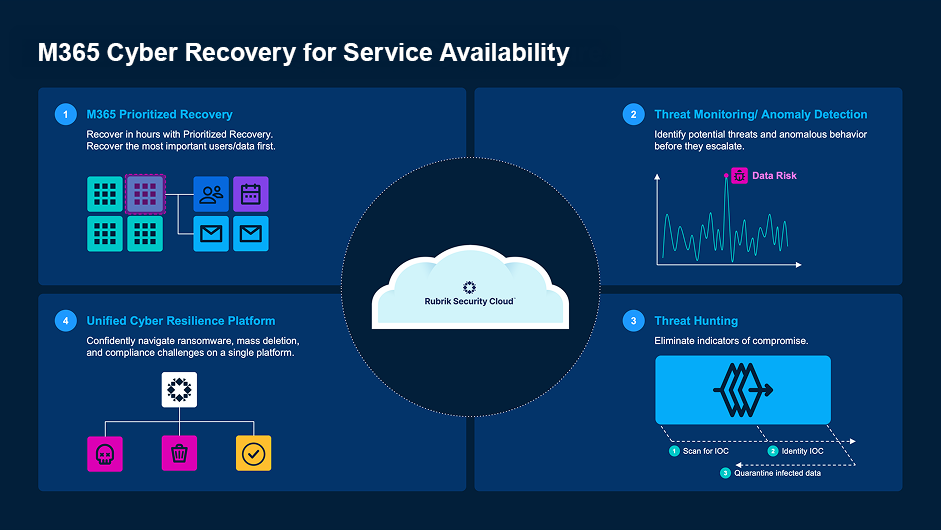
2. Integrated Threat Detection & Prioritized Recovery
Continuously scan for indicators of compromise and anomalous activity. If an attack hits, Rubrik helps you recover fast—starting with the users, sites, and mailboxes that matter most.
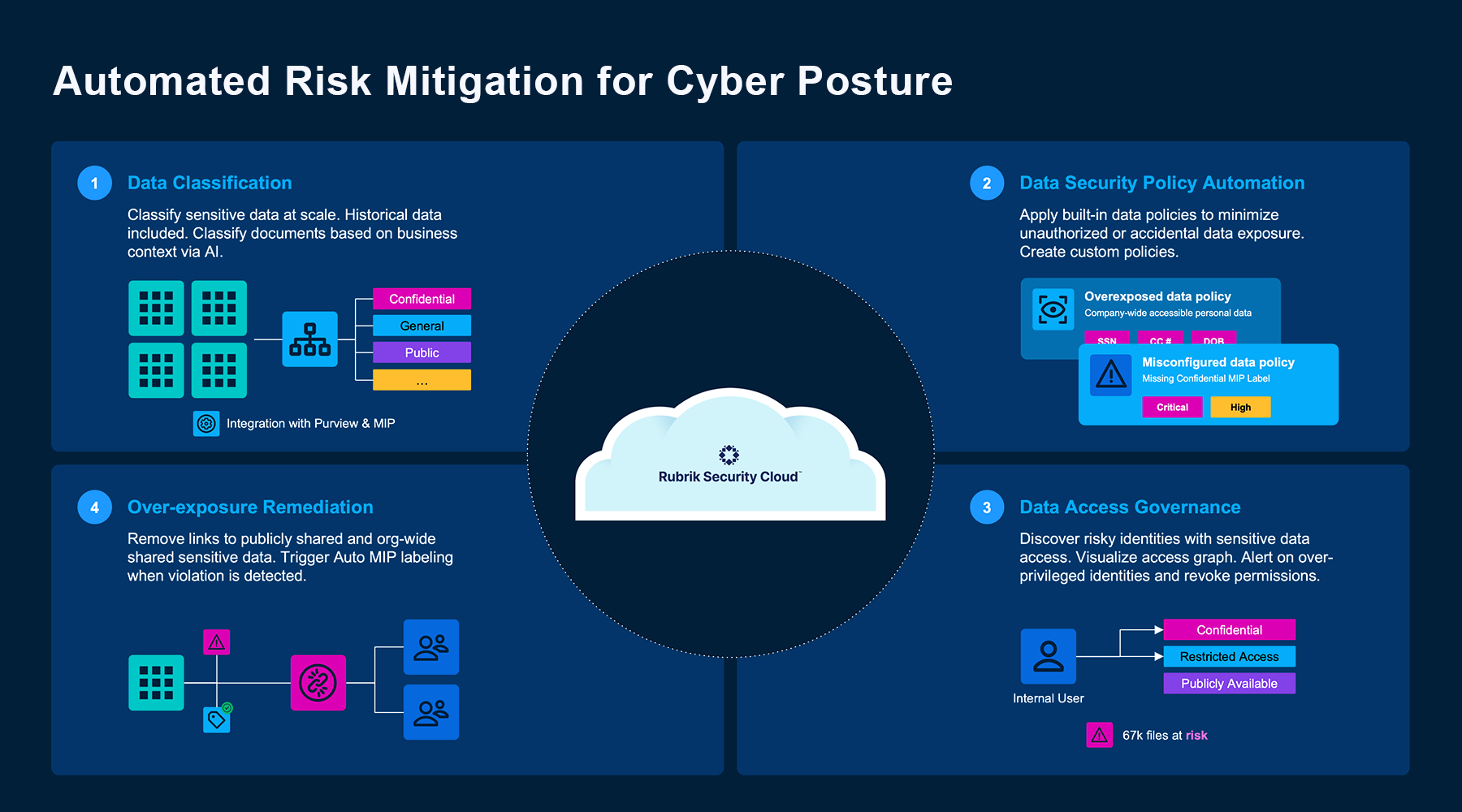
3. Proactive Data Risk Management (DSPM)
Automatically discover sensitive data, flag exposure, and enforce MIP labels at scale. Catch risky configurations before Copilot or external apps amplify them.
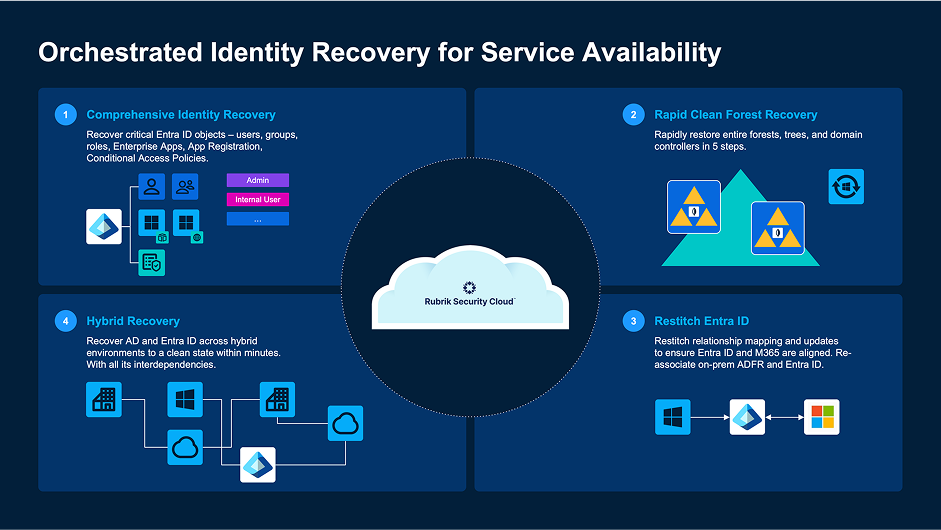
4. Identity Recovery for AD + Entra ID
Recover hybrid identity environments—on-prem AD and Entra ID—using guided workflows. Bring back access safely, without reinfection, even after an identity-based attack
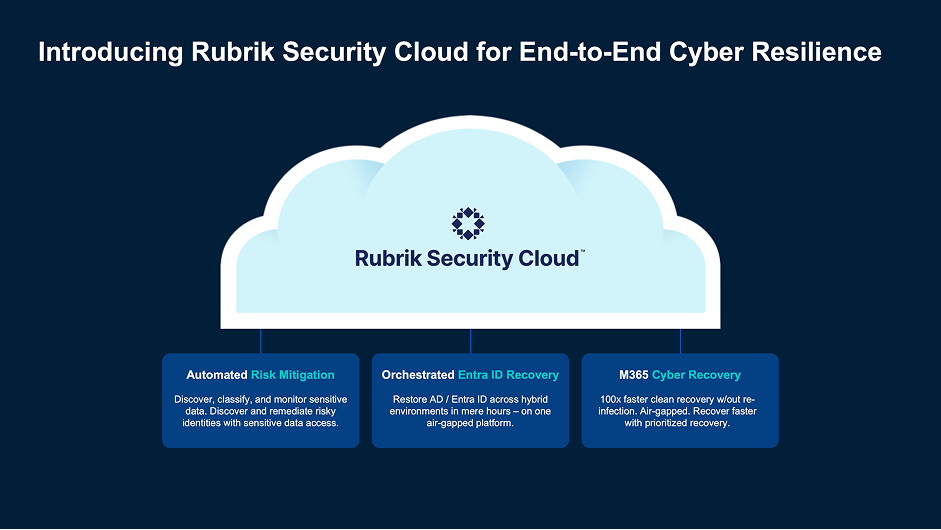
Introducing Rubrik Security Cloud for End-to-End Cyber Resilience
We’re now bringing all these pillars together in a unified solution. Rubrik Security Cloud for Microsoft 365 delivers a new layer of cyber resilience—built to reduce exposure, detect fast, and recover cleanly across both data and identity. It’s not just backup. It’s a strategic, platform-level defense before, during, and after the attack.
Microsoft’s Travis Wynn makes it clear: “Cyber resilience is business resilience. You need to run during the attack and recover fast after.”
Resilience Before, During, and After the Attack
Before: Harden posture by limiting exposure and securing identity.
During: Detect fast with anomaly and IOC detection. Protect recovery points.
After: Restore the right systems in the right order — including identity — to get back online quickly.
Watch the Full Session from Rubrik Forward
To dive deeper into real-world threats and how to build resilience into your M365 strategy, watch the full SaaS cyber resilience session from Rubrik Forward — featuring Microsoft experts and security leaders who’ve lived through real attacks.
Don’t wait for a breach to expose the gaps.
Rubrik helps you build not just backup — but true cyber resilience.