Data masking transforms sensitive information into a disguised version, preserving the data's format but making it unreadable and unusable to unauthorized users. Developers building new enterprise applications need to test how those apps interact with realistic data and data masking makes it possible to do so without exposing medical, financial, or other sensitive personal information on non-production servers. Masked data is also important for researchers who need anonymized or partially anonymized datasets for analysis, and as a means of safely sharing data with third-party partners.
What Is Data Masking and Why Does It Matter?
The term data masking encompasses a set of data security techniques that replace real data with altered yet realistic-looking values. These surrogate values mimic the format and structure of the original data but are unusable or unreadable for unauthorized or non-production purposes.
It's important for enterprises to identify sensitive data and mask it proactively to keep it safe while maintaining dataset utility. Sensitive data includes personally identifiable information (PII) like financial and health-related records, such as names, credit card and Social Security numbers, or medical histories.
Data masking helps you maintain data privacy and regulatory compliance—think GDPR, HIPAA, or PCI DSS—without interrupting your operational workflows. Developers and testers can operate on datasets that behave like real data, but without the risk of exposing sensitive content during development, testing, or staging.
Real-world scenarios for masked data are plentiful:
In test environments, which often lack the security measures regulated industries require, developers can simulate user interactions using realistic yet safe datasets
Analytics teams can run reports on pseudodata
For training purposes, employees can work with example datasets reflecting real use cases
Third-party integrations can receive only masked data, ensuring confidentiality across partnerships.
Static vs. Dynamic Data Masking Explained
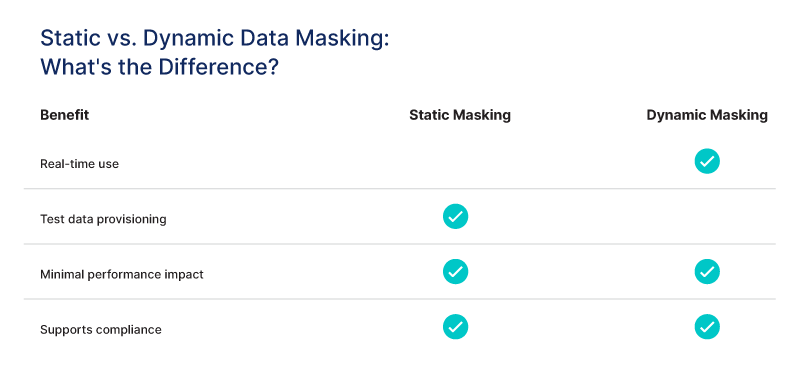
There are two different types of data masking: static and dynamic.
Static data masking creates a permanently masked copy of a dataset. The process involves taking a snapshot or clone of the original data, then replacing sensitive values like names, Social Security numbers, or account details with realistic substitutes. The resulting dataset retains the same structure as the original but contains only anonymized or fictitious records. This is an irreversible process that creates a copy; so static data masking is best suited for non-production environments like testing, analytics, or employee training.
For example, a development team could create a masked clone of a customer database where real Social Security numbers are replaced with randomized values, ensuring confidentiality while still enabling realistic application testing.
Dynamic data masking, by contrast, operates in real time. Instead of creating a new dataset, it applies masking rules as users query the database or application. The original data remains intact in storage, but unauthorized viewers only see masked or partial values. Common use cases include internal access control and regulatory audits, where certain roles require limited data visibility.
For example, a customer service representative might see only the last four digits of a credit card number. This approach is increasingly valuable for protecting cloud data in scenarios where sensitive information flows across distributed systems.
Key Benefits of Data Masking for Security and Compliance
The most important benefit of data masking is that it strengthens data privacy, preventing exposure of real values by substituting them with masked data. However, there are a number of other advantages as well:
Maintains referential integrity: Data masking preserves relationships between fields in a dataset (such as IDs, account numbers, or patient records), even when sensitive details are anonymized.
Supports compliance: Regulations like GDPR, HIPAA, and CCPA require that you control access to personal and regulated data, and data masking helps organizations in closely regulated industries like healthcare providers and legal firms meet those requirements.
Reduces insider threats and leaks: By restricting access to sensitive data, data masking lowers the risk of accidental disclosure or deliberate misuse during development, testing, or third-party collaboration.
Best Practices for Implementing Data Masking in 2025
Getting started with data masking in your organization? Here are the best practices to follow so that you can quickly generate masked data that is useful for development or analytics environments but doesn’t expose sensitive information:
Identify and classify sensitive data: The first step is to find the data fields that require sensitive treatment, such as PII, financial records, or regulated datasets, to apply policies where they matter most.
Select the right masking techniques: Remember, use static data masking for dev/test environments where permanent masked copies are sufficient, and dynamic masking for live systems that require real-time protection.
Automate workflows: The data sets you'll be seeking to mask are no doubt massive. Automate the discovery and masking of sensitive data as much as possible.
Preserve referential integrity: Masked values must maintain the same relationships as the original dataset to keep applications, analytics, and testing accurate.
Audit and update regularly: Compliance standards and threats evolve, so organizations should routinely review and refine masking rules to stay aligned with regulations and security needs.
Data masking secures sensitive data in both production and non-production environments by providing a realistic substitute. Rubrik can simplify and assist the data masking process with automated discovery, classification, and policy-driven protection that supports compliance and privacy. Your organization should include data masking alongside other controls for protecting cloud data as part of a broad data security and privacy strategy.