According to Statistica, the average response time to a ransomware attack is 20 days. 20 days where your customers can’t order your product, 20 days where your end-users are unable to access important information - 20 days of incurred downtime for your organization resulting in massive profit losses and reputation damage. I think it goes without saying, time is of the essence during a ransomware attack.
Security teams have long leveraged tools like Microsoft Sentinel to aggregate and normalize their security events, alert on threat detection, and most importantly, orchestrate threat responses through a variety of automated playbooks. Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) tools like Sentinel enable SecOps to respond to threats in an automated and efficient manner. However, SecOps can’t do this alone - often, responding to a threat results in the need for some sort of recovery to take place, which in turn involves collaboration with backup teams. The backup teams have their own set of valuable insights that can aid in the threat response. For instance, Rubrik Security Cloud customers are able to quickly answer important questions around ransomware recovery such as:
- What is the blast radius of the attack? What applications, files and folders have been compromised?
- Has any sensitive information been affected and where is it located?
- When did the first occurrence of malware enter the environment? What is the last known clean copy of data?
- Can we safely restore applications without the risk of reinfecting the environment?
Unfortunately, due to the siloed nature of many organizations, retrieving the answers to these questions only adds to the threat response time and increases the organizations' downtime. But what if there was a better way? What if we could bring insights from both the SecOps and IT Ops departments together in a centralized location to foster collaboration and automate recoveries?
Introducing Rubrik Security Cloud integration with Microsoft Sentinel
With the Rubrik Security Cloud integration into Microsoft Sentinel, Security and IT Operations teams now have the ability to make data-driven decisions around threat response and automate recoveries directly from within the confines of Microsoft Sentinel. This new integration brings delivers key Rubrik data security insights and functionality front and center into Microsoft Sentinel such as:
- Ransomware Investigation & Monitoring - After each and every backup, Rubrik Security Cloud leverages a machine learning algorithm to detect the change rate between snapshots, resulting in a listing of files which have been created, modified and deleted. This listing is then sent through another machine learning algorithm which looks for signs of encryption and ransomware. This resulting blast radius is then sent to Microsoft Sentinel and attached to an incident to aid in the threat response
- Sensitive Data Monitoring & Management - Rubrik enables the ability to scan for sensitive data based on a number of prebuilt and custom analyzers mapped to common compliance regulations such as Personally Identifiable Information (PII) and PCI-DSS. Results from these scans are then sent to Microsoft Sentinel and attached to an incident to aid in the threat response.
- Threat Monitoring and Hunting - Using YARA rules targeting malware, Rubrik investigates a time-series history of data points to determine when the initial infection occurred. This listing of both infected and clean snapshots is sent to Microsoft Sentinel to aid in recovery efforts.
- Automated, mass or surgical recovery - Rubrik provides the ability to surgically recover only what is needed or to pursue mass image-level recovery of applications. The many recovery methods provided by Rubrik can be executed directly from within Microsoft Sentinel
By bringing data insights from both SecOps and ITOps together, organizations are able to determine the scope of the attack more efficiently, automate recoveries, and save valuable time and money that would be otherwise lost.
How does it work?
Installation of the Rubrik Sentinel integration is a breeze and can be accomplished in a few minutes. First, install the Rubrik Data Connector through the Sentinel Data Connectors gallery. From there, simply configure the webhooks functionality within Rubrik Security Cloud to send anomaly, sensitive data, and threat-hunting events to the newly deployed function URL.
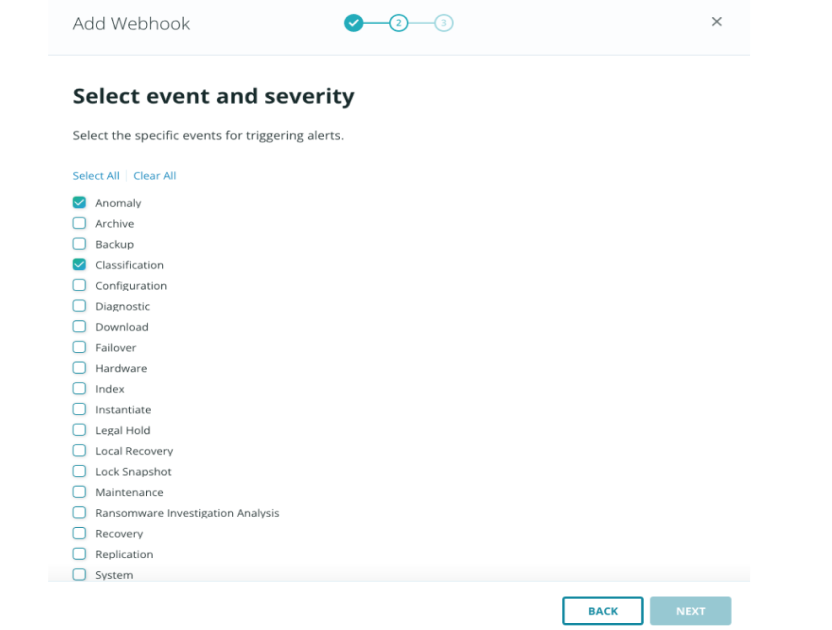
That's it! You will now see specific Rubrik events within the Sentinel query analyzer along with a number of Rubrik-related logic apps that can be utilized.
As anomalies are detected within Rubrik and sent to Microsoft Sentinel, a custom analytics rule is triggered which automates the creation of an incident. Simultaneous to the incident creation, a playbook is executed, gathering further information around the anomaly such as the number of files and folders which have been created, modified, and deleted, along with whether signs of encryption are present. Information from Rubrik Sensitive Data Monitoring and Remediation service is also collected, allowing operators to easily see if any of their sensitive information such as PII or HIPAA has been compromised.
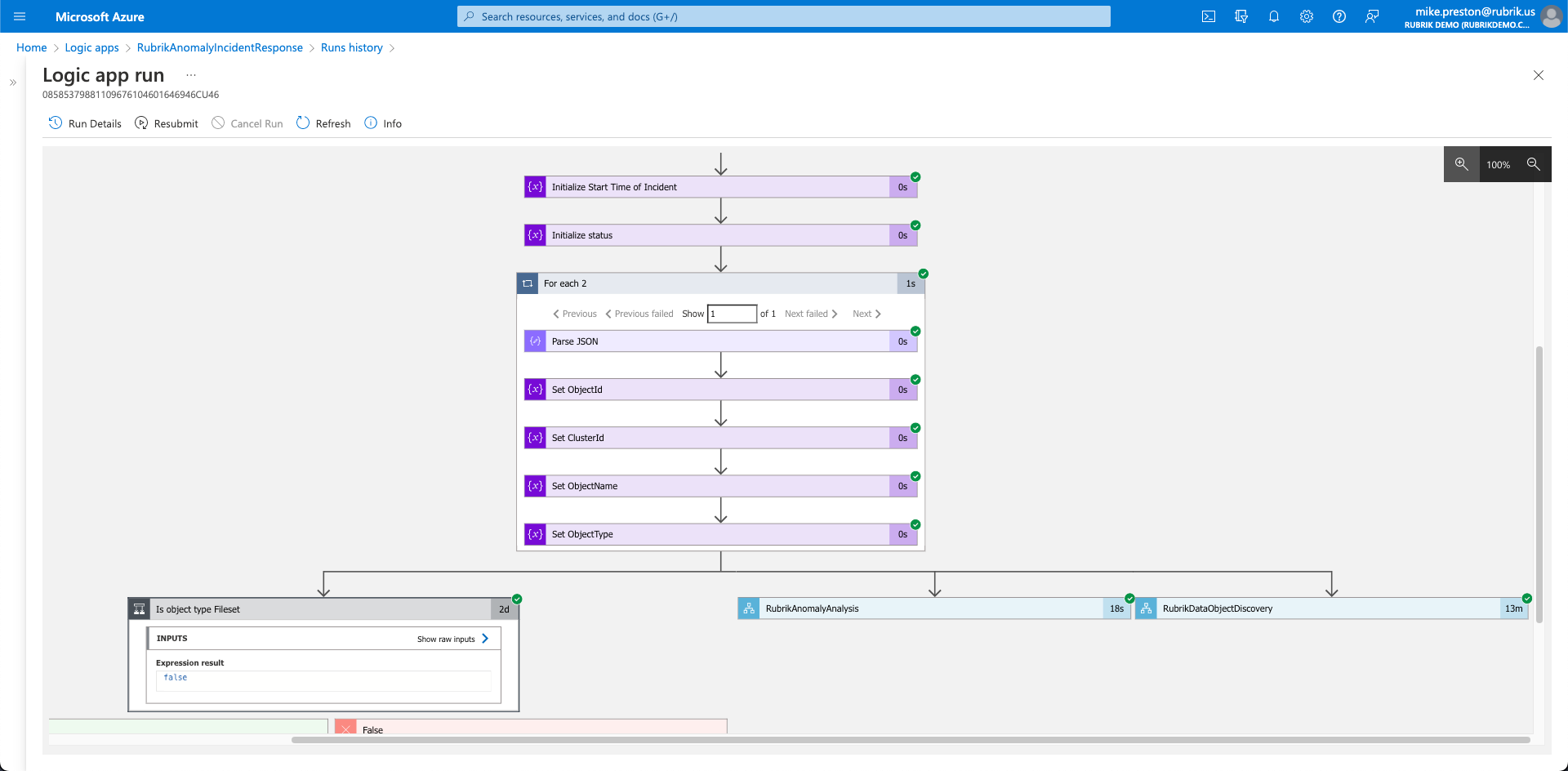
Once complete, an adaptive card is sent to a designated Microsoft Teams channel where both Security and IT Operations can collaborate on the issue and ultimately make a decision on whether or not to trigger a recovery. If recovery is needed, information is passed through Microsoft Teams to Sentinel which initiates a Rubrik Threat Hunt to determine the last known clean copy of data based on user-specified YARA rules.
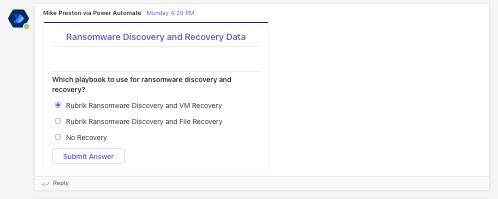
When Rubrik determines that last known clean backup, the recovery is automatically invoked - all without leaving the confines of Microsoft Sentinel.
Conclusion
Bringing security and backup teams together during an outage can take time, furthermore, shedding light on the blast radius of an attack and what data has been affected only adds to that. The Rubrik integration with Microsoft Sentinel provides a common data treasure trove for security and backup teams to triage, analyze, and recover their data, minimizing the amount of business disruption. Rubrik complements Microsoft's perimeter and cloud security detection tools with comprehensive data security that safeguards your most precious asset, data, so it will always be available for recovery.
To learn more about how to leverage Rubrik and Microsoft’s joint data security solutions, register for Rubrik Winter Release where we will dive deeper into our cybersecurity offerings.
