Microsoft 365 (M365) is no longer merely a productivity suite; it has become the operational backbone of modern enterprises, a critical asset that demands robust protection. Which makes it a high-value target for cyber threats.
While Microsoft manages the security of its cloud infrastructure, the Shared Responsibility Model places the M365 data and identity protection in the hands of the customer. Native tools lack the immutable, air-gapped backups and intelligently orchestrated recovery capabilities essential for handling major or minor incidents. So many M365 instances suffer from significant cybersecurity gaps.
Rubrik delivers complete M365 cyber resilience by unifying data and identity protection on a single, comprehensive platform. For CISOs, this goes beyond just backup; it becomes a comprehensive solution featuring immutable backups, data threat analytics (DTA), advanced recovery orchestration, proactive data security posture management (DSPM), and orchestrated AD/Entra ID identity recovery. Together, these capabilities can address a range of cyber threats, including information theft, ransomware, insider threats, accidental deletion, overexposure of sensitive data, and identity compromise.
Several key Rubrik features can help increase the resilience of your M365 instance: Data Discovery and Classification, Data Threat Analytics, and Advanced Recovery Orchestration. Here’s how.
Data Discovery and Classification
Rubrik's Data Discovery and Classification discovers sensitive information in structured and unstructured data that is subject to regulation, finding all data in the enterprise that matches a specified data classification rule.
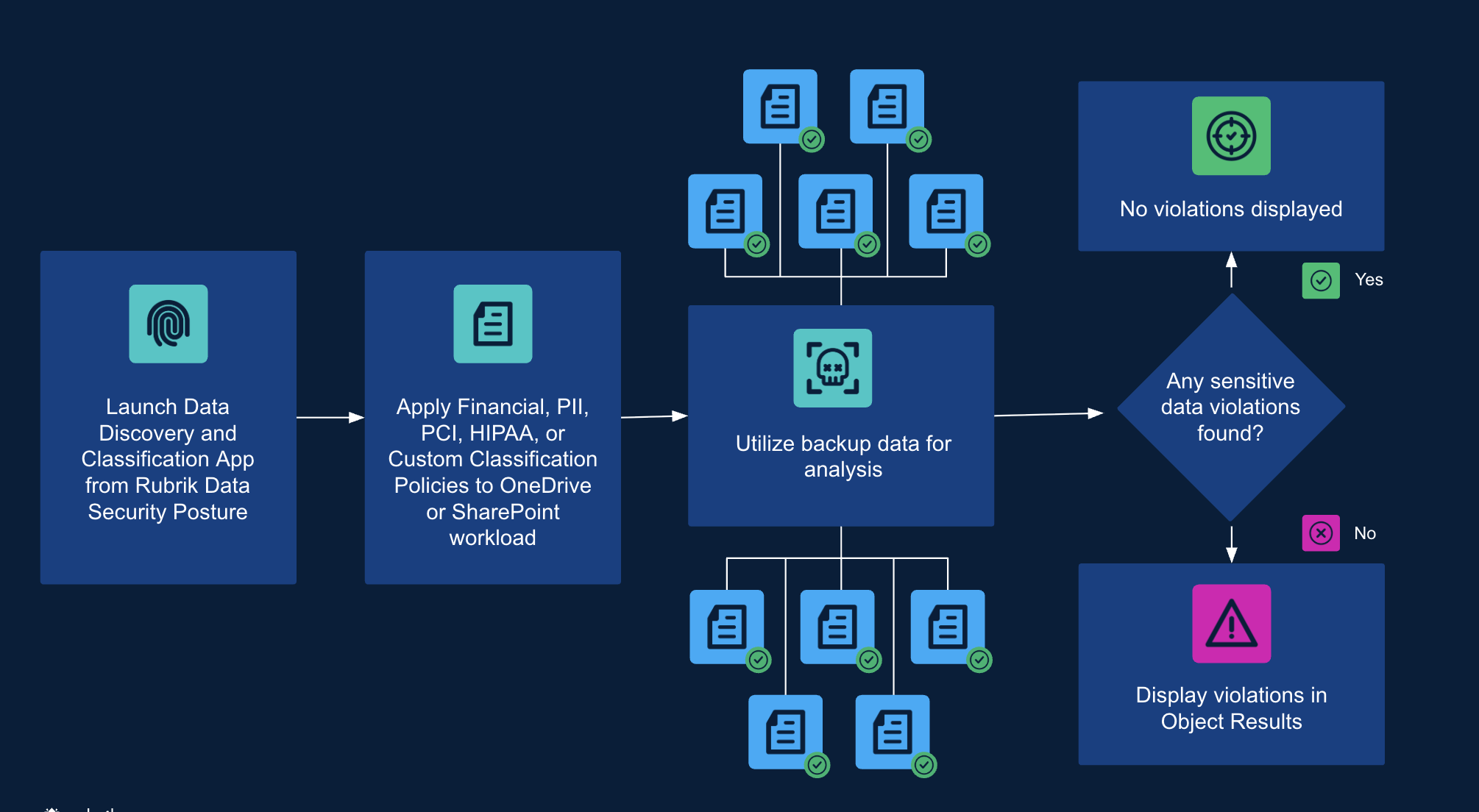
Here's how Rubrik can provide agentless, non-intrusive identification of sensitive data within your M365 backups.:
Launch the Application: Begin by launching the Data Discovery and Classification App directly from Rubrik Data Security Posture.
Apply Classification Policies: Apply a range of pre-built classification policies, including those for Financial, PII, PCI, HIPAA, or define Custom Classification Policies to your OneDrive or SharePoint workloads. You can leverage common data type analyzers to find data, such as credit card numbers, social security numbers, bank routing numbers, etc., or define custom dictionaries, expressions, and policies.
Utilize Backup Data for Analysis: Crucially, the analysis is performed directly on your backup data, ensuring zero impact on your live production environment.
Violation Display: If no sensitive data violations are found, the system displays this confirmation. If violations are detected, they are clearly displayed in the Object Results, providing actionable insights into where sensitive data resides and where it might be exposed.
Data Threat Analytics
Rubrik Data Threat Analytics provides detection, investigation, and response to cyber threats, proactively safeguarding your M365 data. Let’s break down each of the security applications.
Anomaly Detection: Anomaly Detection can proactively identify unusual activity —particularly encryption—within your M365 backup data. It provides clear visibility into potential threats, ensuring that only genuine incidents are flagged.
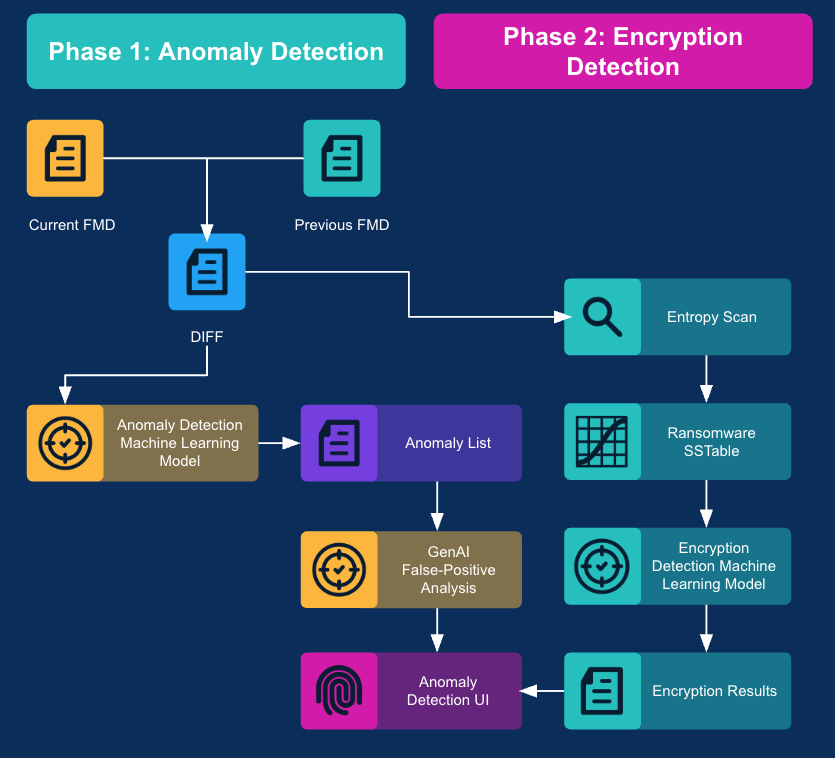
Here's how it works:
Difference Identification: Metadata from M365 snapshots is generated and compared to previous versions to identify differences across the snapshot. This is referred to as DIFF File Meta Data or DIFF FMD.
ML Anomaly Detection: This DIFF FMD data is fed into an ML model to pinpoint potential anomalies.
Optional GenAI False Positive Analysis: For enhanced accuracy, detected anomalies can optionally undergo GenAI False Positive Analysis. Here, an additional ML model further analyzes files to determine the likelihood of actual encryption, preventing false alarms.
Entropy Scan: Concurrently, an Entropy Scan is performed on the DIFF FMD data, with encryption statistics saved for further analysis.
UI Presentation: All validated anomaly and encryption detection results are then presented in the Anomaly Detection UI, offering clear insights into potential threats.
Threat Monitoring: Threat Monitoring, a core component of Rubrik's Data Threat Analytics, provides continuous and automated scanning of your M365 backup data for Indicators of Compromise (IOCs). This "set it and forget it" feature ensures proactive and effortless threat detection without impacting production systems.
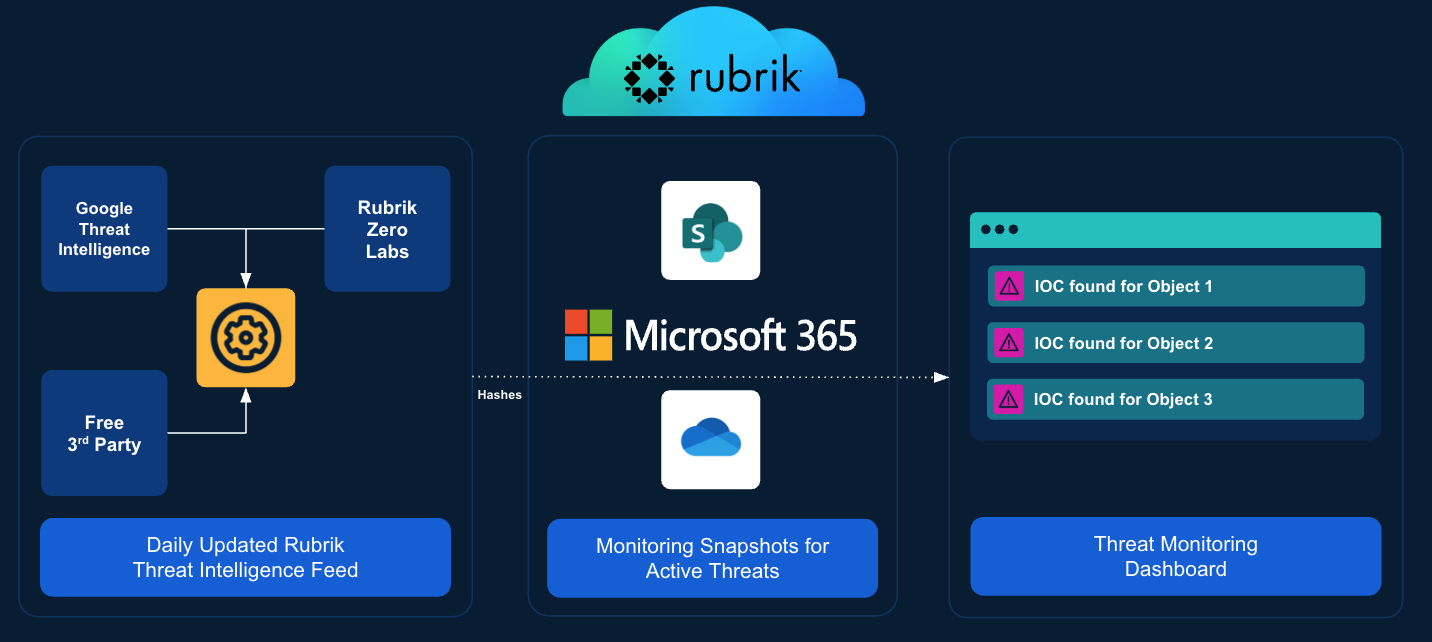
Here's how it works:
Activation: Enabled within RSC.
Automated Scanning: Rubrik automatically initiates scans for IOCs in your time-series backup data. Threat Monitoring periodically checks for new snapshots after every backup, ensuring continuous active monitoring
Threat Intelligence Feed: The most up-to-date and actively relevant IOCs associated with cyberattacks integrated into the process, leveraging verified intelligence M365 hashes, sources from Rubrik Zero Labs, Rubrik SOC, and Google Threat Intelligence.
Match Reporting: If any matches are found, the object name, match type, and location are immediately displayed on your dashboard.
Effortless Operation: Once enabled, it automatically ingests new threat intelligence and scans for IOCs in your backups, requiring no further manual intervention.
Threat Hunting: Rubrik Threat Hunting drastically speeds up incident response by reducing the time to find malware-free recovery points from hours to seconds. This powerful capability allows organizations to quickly select secure recovery points, prevent reinfection, and significantly accelerate incident response and forensic analysis.
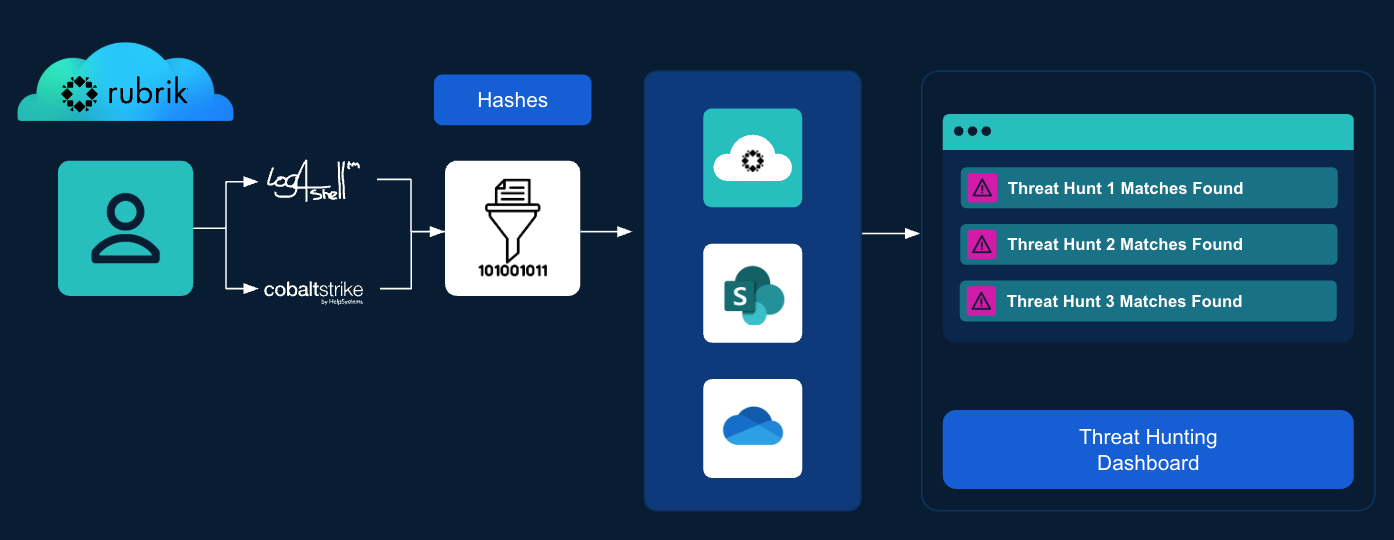
Here's how it works:
Pre-computed Hashes: At the time of backup ingest, Rubrik calculates hashes and stores the details in a hash table in RSC. This way, Rubrik only needs to look in the hash table when new IOC hashes become available—no additional filesystem churn is required. This allows for instant identification of clean recovery points without needing to mount and scan individual files.
Automated Threat Hunts: During an incident, security teams can simply input known malware indicators to initiate a threat hunt. Rubrik Turbo Threat Hunting then swiftly scans the pre-computed hashes rather than the actual backup environment to pinpoint unaffected recovery points.
Recovery Options
Rubrik's Recovery Solutions deliver fast, granular, and flexible data restoration in your M365 environment. Let’s explore some recovery options.
Prioritized Recovery in Rubrik's M365 protection provides a streamlined approach to restore critical data quickly. This feature allows organizations to rapidly recover essential information for Entra ID, SharePoint, and Teams groups, minimizing downtime and business impact. Here's how it works:
Initiate Recovery: Start the Recovery Wizard for your desired Entra ID, SharePoint, or Teams groups.
Select Prioritized Recovery: Choose Prioritized Recovery as your preferred restoration option.
Define Recovery Window: Specify a Recovery Window (e.g., the last 7 days) to prioritize the recovery of the most recent and vital emails, documents, or chats.
Optional Full Recovery: Optionally, choose to automatically recover any remaining data after the prioritized set is complete, ensuring full data availability with flexibility.

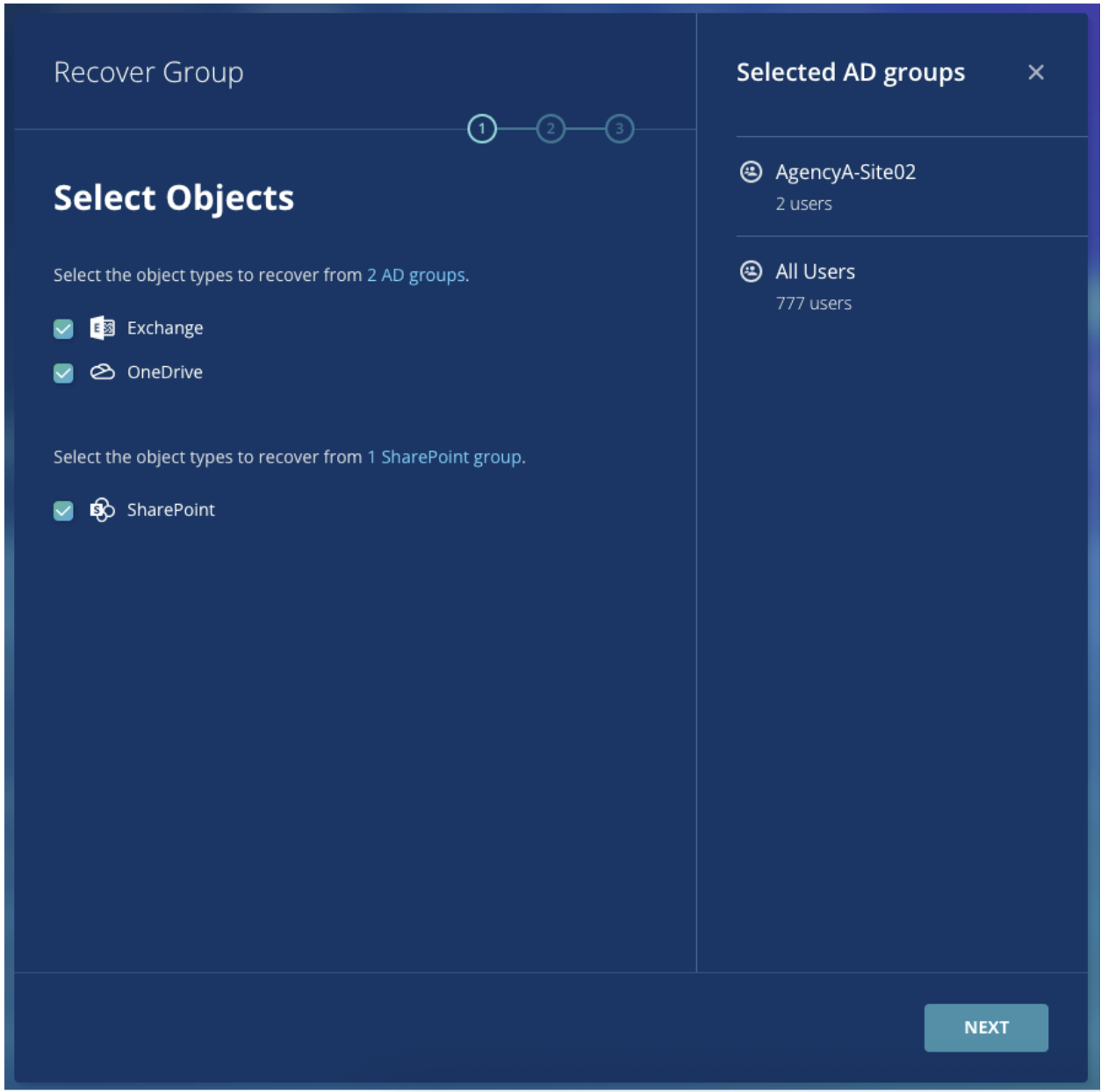
Rubrik M365 Mass Recovery simplifies the restoration of large sets of M365 data by allowing organizations to recover groups of objects simultaneously, rather than individually. This significantly accelerates recovery times for critical M365 services. Here's how it works:
For Exchange and OneDrive: Users are added to Entra ID groups. These groups are then selected for recovery within RSC.
For SharePoint and Teams: Rubrik uses wildcard groups to select multiple SharePoint sites and Teams. Wildcard groups are populated using simple regex patterns that match against SharePoint site and Team names. If a match is found, the object is considered a member of that wildcard group.
Parallel Recovery: Once groups are selected, the mass recovery of objects is performed much like individual recoveries, but with multiple objects recovered in parallel for efficiency.
Self-Service Recovery empowers end-users to restore their own data, drastically cutting down on waiting times and freeing up IT teams to focus on strategic initiatives. It's about reclaiming productivity and minimizing business disruption. Here's how it works:
Administrator Setup: IT administrators create a Self-Service Recovery role in Rubrik Security Cloud (RSC) and assign it to the relevant SSO user group.
User Access: End-users log into Rubrik Security Cloud using their standard organizational credentials or SSO.
Data Selection & Recovery: Users navigate directly to their Exchange or OneDrive data, search for and select items, and initiate an in-place restore.
Safe Restoration: Recovered items appear in a new folder, ensuring original data remains untouched.
Status Notifications: Both the end-user and administrators receive notifications about the recovery status.

Regain Control of Your Business-Critical Microsoft 365 Data
Rubrik can extend your backup and recovery protections far beyond native M365 tools, minimizing business disruption and accelerating response times during incidents by integrating advanced intelligence directly into the backup process.
Key features, such as Anomaly Detection, Threat Monitoring, and Threat Hunting, help organizations identify clean, malware-free recovery points, effectively preventing potential reinfection. Additionally, Rubrik enhances operational recovery through its Prioritized Recovery orchestration, mass recovery, and self-service recovery. The solution also offers Data Discovery and Classification to assess potential sensitive data exposure during incidents.
Overall, Rubrik is not just a backup solution; it’s a comprehensive data protection strategy that enhances resilience and ensures business continuity.
Ready to experience these capabilities firsthand? Access Data Threat Analytics, Prioritized Recovery for M365, or Self-Recovery hands-on lab to get started!
