Sensitive Data Monitoring
Reduce sensitive data exposure
Reduce sensitive data exposure and manage exfiltration risk by discovering what types of sensitive data you have and where it lives.
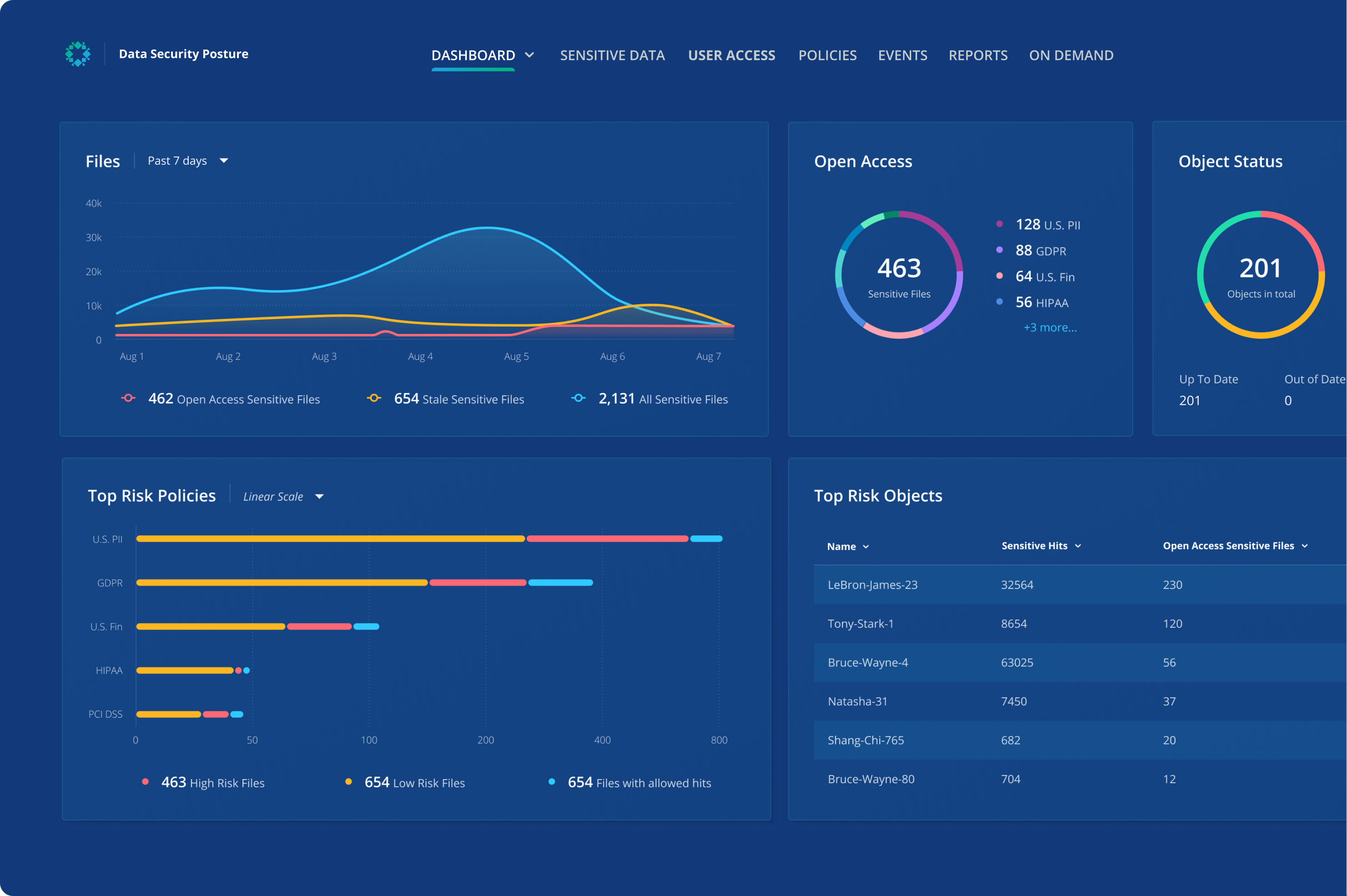
Organize and secure sensitive data
Lack of visibility into sensitive data can lead to vulnerabilities and unnecessary incident response costs. Rubrik Sensitive Data Monitoring scans backup snapshots and locates sensitive data in files and applications to help you stay compliant.
Automate Policy Enforcement
Assess Data Exposure
Facilitate Compliance
Document where sensitive data is in order to maintain regulatory requirements.
2025 Gartner® Magic Quadrant™ for Backup and Data Protection Platforms.
Read the Gartner 2025 Magic Quadrant report for an in‑depth analysis of the enterprise backup and data protection market, and why Rubrik is positioned as a Leader for the 6th consecutive year.

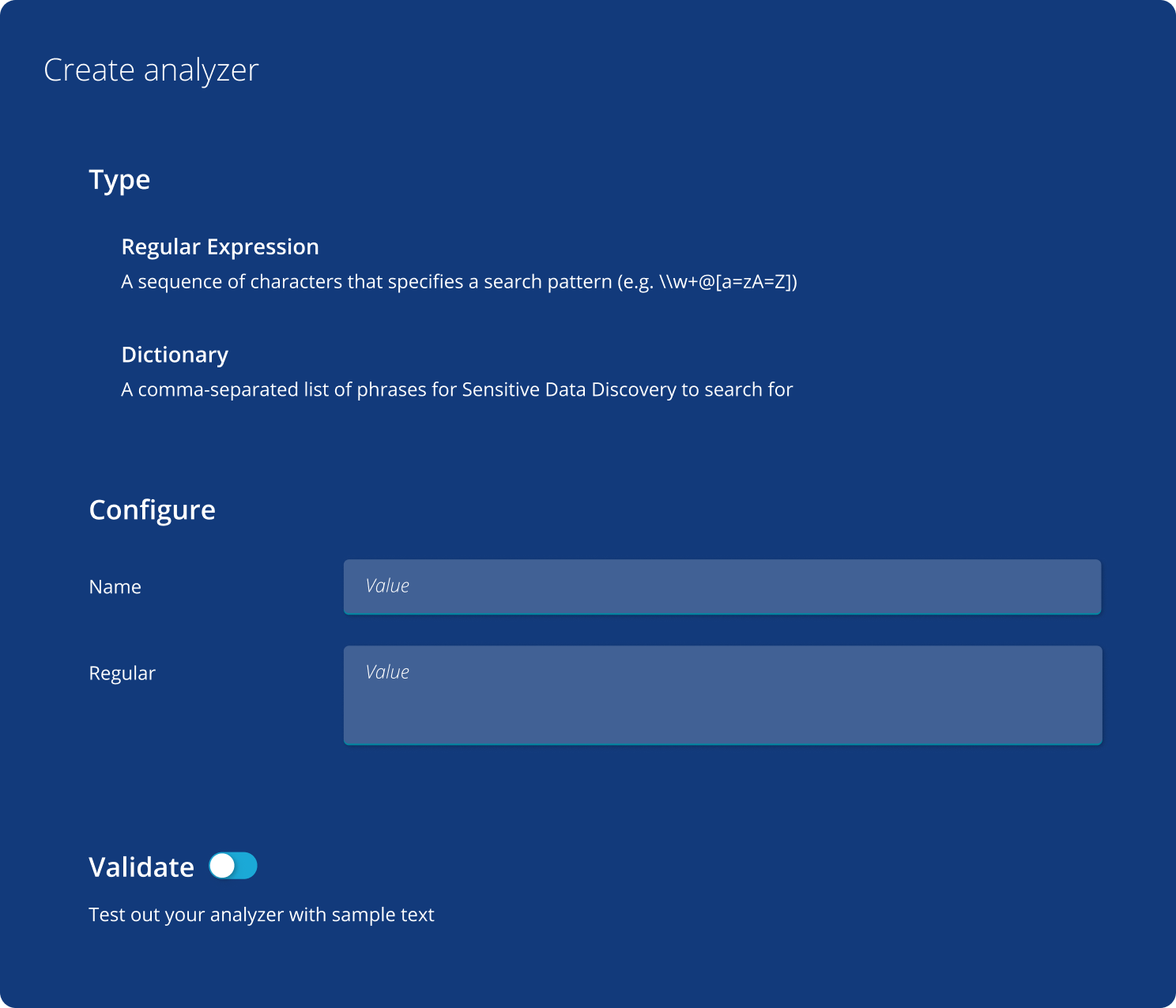
Enforce policies automatically
Use pre-defined templates or create custom policies to quickly identify and classify sensitive data without impacting production.
Get policy violation alerts
Rubrik alerts you when data may violate policies. You can also schedule periodic reports to help maintain compliance with GDPR, PCI-DSS, HIPAA, and GLBA regulations.

Pinpoint data exposure
Search the index using keywords or custom fields, such as name, social security number, or credit card number to identify potential exposure and risk.
5 Keys to Mitigating Data Risk
Learn 5 tips to help you protect your data, minimize sensitive data exposure, and recover quickly in the event of ransomware.


Sensitive Data Monitoring: The Complete Demo
Sensitive data monitoring can help you better prepare and respond to ransomware attacks, while ensuring regulatory compliance.

Sensitive Data Monitoring
Rubrik Sensitive Data Monitoring is a SaaS application that discovers, classifies, and then reports on sensitive data without any impact to production.
Sensitive Data Monitoring
See how Rubrik Sensitive Data Monitoring can help you manage your sensitive data and monitor who has access to it.

