Don't wait until it's too late
Level up your cyber readiness and incident response. Bounce back with confidence by restoring operations to a clean state—with minimal downtime and data loss. Always be prepared to orchestrate recovery of data and applications using recovery plans with well-defined processes and predictable timelines.
Recovery Simulation
Improve cyber readiness and incident response by creating, testing and validating your cyber recovery plans in isolated environments.
Threat Containment
Isolate infected snapshots to reduce the recovery risk of reintroducing the malware into the environment during a recovery operation.
Cyber Recovery
Restore business operations rapidly and with confidence by surgically recovering impacted applications, files, or objects, at scale.
Bounce back confidently and predictably
Always be prepared and when needed orchestrate a safe and rapid recovery of data and applications with recovery plans that have well-defined processes and predictable timelines.
Take the uncertainty out of cyber recovery
Operational complexity and untested recovery plans can result in data loss and prolonged downtime during cyber attacks. Improve cyber readiness and incident response by creating, testing, and validating recovery plans in isolated environments.


Recover the data, not the malware
Inadvertently recovering malware-infected data can lead to increased downtime and costs. Safely isolate infected snapshots to prevent accidental access and reduce the risk of reintroducing malware into the environment during a recovery operation.
Quickly identify a clean recovery point
Stop wasting time looking for a recovery point. Recover data and applications to a clean state using insights into the point and scope of attack. Execute smooth recovery operations with no dependency on key personnel or specialized cybersecurity skills.


Orchestrate a smooth recovery of data and applications
When disaster or ransomware strikes, a simple, scalable, and flexible recovery path can help avoid costly interruptions. Recover what you need—whether it's hundreds of VMs, tens of thousands of files, or just a few infected files—using guided workflows for file-level, object-level, application-level, or system-wide restores.
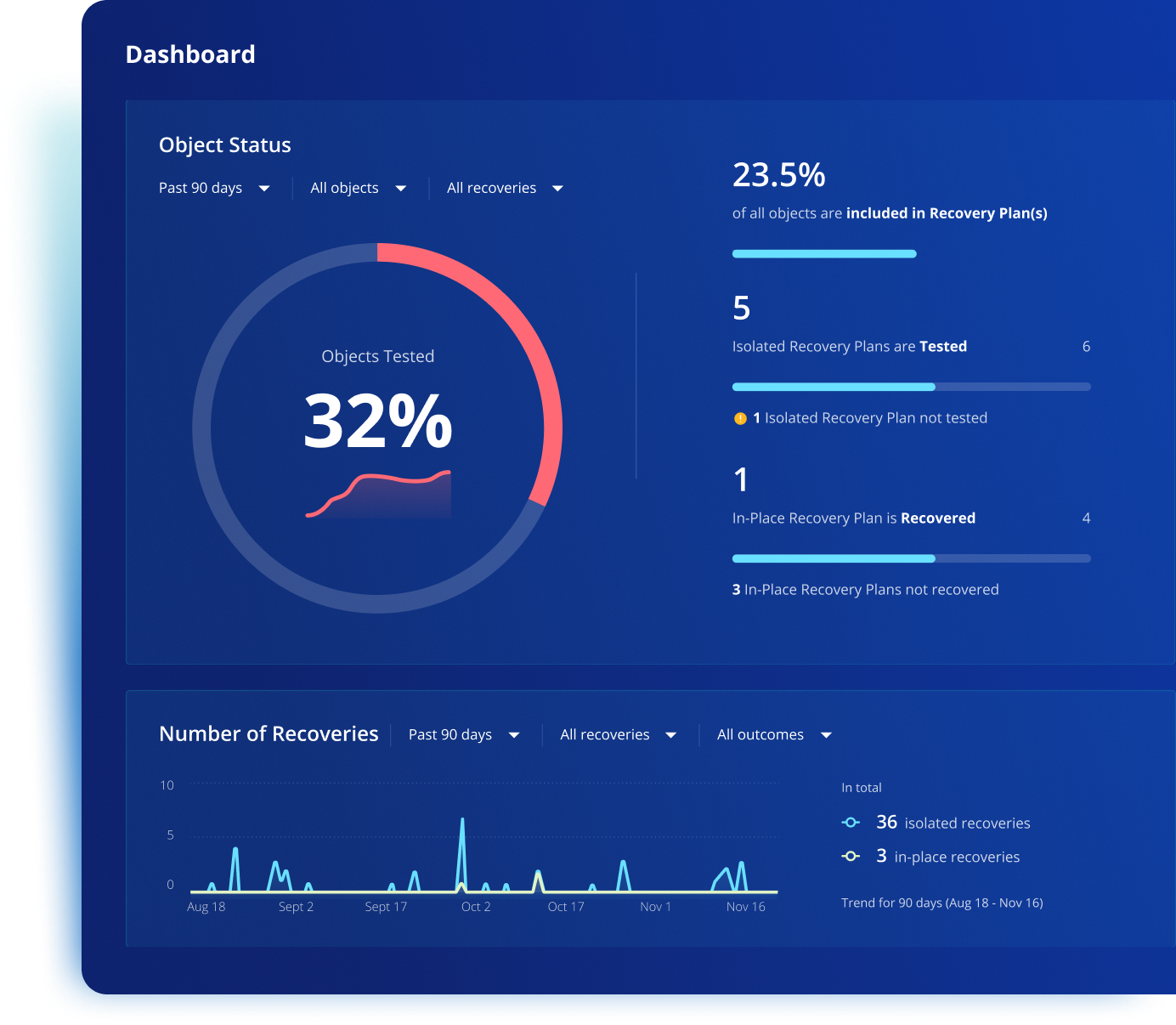
Track recovery progress and conduct forensics
Monitor recovery progress, measuring key outcomes such as execution time and generate reports for compliance. Conduct thorough post-attack forensic investigations in secure, isolated environments to understand the root cause, attack origin and other post-incident reviews.

Explore more of our resources


Demo
Cyber Recovery with Rubrik Security Cloud
Explore how Rubrik Cyber Recovery feature provides proactive testing and automation of end-to-end recovery.