In this blog
If you haven’t already checked it out, make sure to check out the latest Zero Labs report. Don’t worry, I’ll wait.
Ok, you’re back? As you may have noticed in the report, identity-based attacks are a booming business for threat actors. Breaches are up. Breakout times are down. The impact of breaches is skyrocketing. It’s a perfect storm and it’s getting worse.
So what do you do about it?
In many cases, these new attacks are able to sidestep traditional EDR protections. The attacker has legitimate credentials—whether through social engineering, credential stuffing, or stolen session tokens. Often they will live off the land using legitimate tools.
So there might not be any malware for EDR to detect.
To combat these new attack patterns, you need the best in class detection for identity-based threats. CrowdStrike Next-Gen Identity Security provides exactly this, with detection and response capabilities so that you can identify compromised identities, investigate, and lock them down quickly.
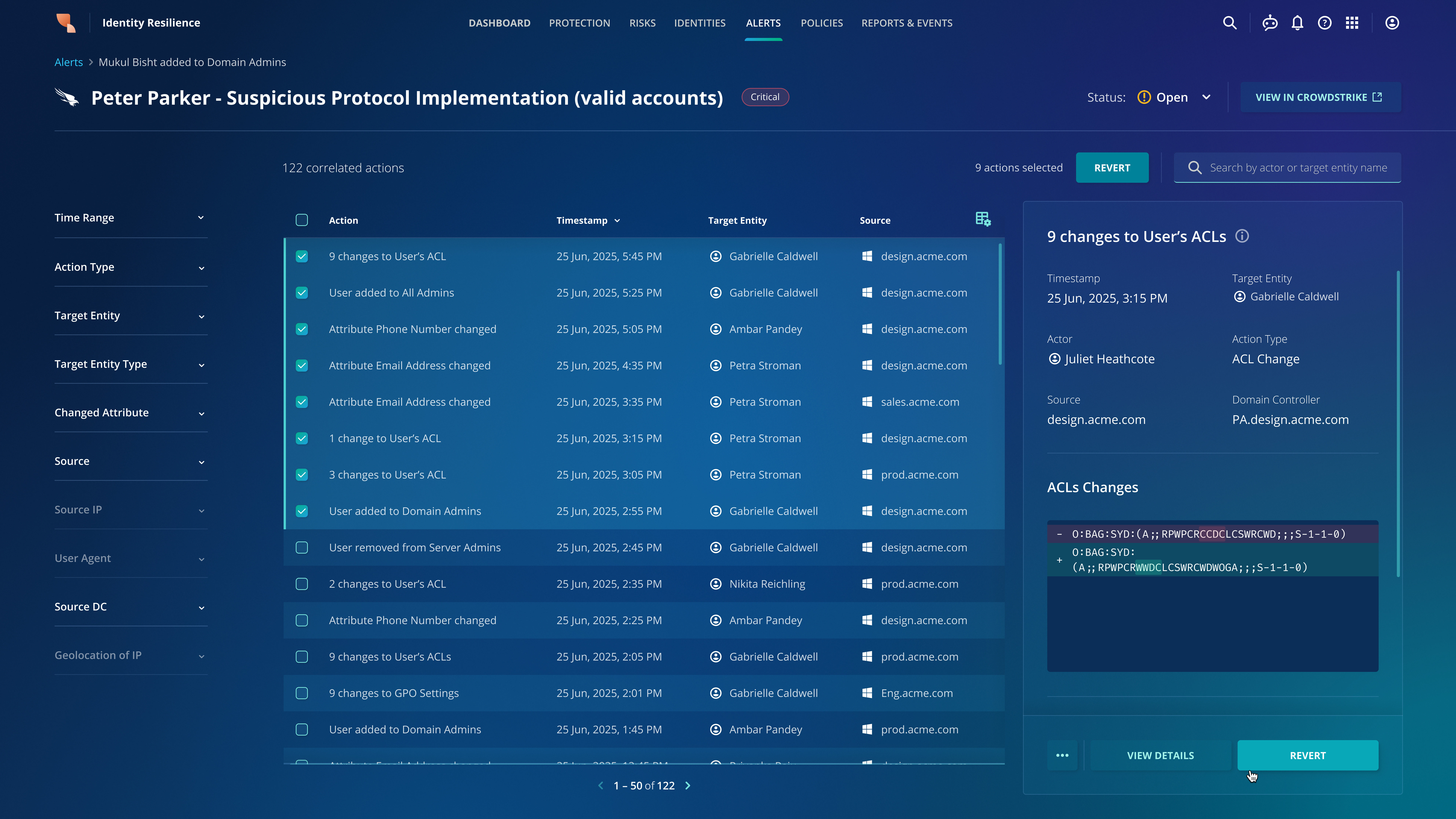
Rubrik Identity Resilience captures all activity within the Identity Provider (IdP) into an immutable activity log, showing which actor took which action on which target identity. Now, a new integration with CrowdStrike Next-Gen Identity Security makes it simple for you to quickly identify every action taken by a compromised identity—from the moment the initial breach was detected right up to the moment that the SOC analyst locks the compromised account down using the Fusion SOAR workflow.
Without this, your route to undoing those changes is to hunt in your SIEM for the actions your adversary made, then figure out how to revert them.
This isn’t just showing you what they did, either. Much like the recently announced Rubrik Agent Cloud for agentic AI, once the suspect activities have been confirmed, you can simply select the actions in the Identity Resilience interface and rewind them back.
Why Identity Security Needs Rollback
Put yourself in the adversary’s shoes. If you were able to successfully compromise an identity and gain administrative privileges, what would you do next?
You probably know there’s a good chance that the defenders are noticing the breadcrumbs that you dropped. It can surely only be a matter of time before they latch onto you and lock you out.
So what would you do to cover your tracks?
If you haven’t already, you might want to establish persistence, perhaps by creating further identities that you could use to reconnect when the defender identifies the compromised identity, and then disables it. Maybe make some other changes to expose Active Directory to future attacks.
Regardless, the defender needs visibility into exactly what actions the threat actor has taken. And you need to be able to roll those changes back.
How it works
Once integrated with CrowdStrike, Rubrik Identity Resilience polls the CrowdStrike Falcon Next-Gen Identity Security APIs for identity based events. When events are detected by CrowdStrike, they are ingested into Rubrik where they are correlated against the actions that Rubrik already collects from the environment. In the event of an incident, all that is required is to select the compromised identity and decide if you want to roll back all actions or only specific ones.
Reverting these changes occurs through an API call to the same Rubrik Backup Service that is used to backup Active Directory, which in turn makes an LDAP call to Active Directory.
Within moments, it is like the changes hadn’t happened at all. Any newly created identities your adversary created, any IdP configurations that might make it easier for them to regain access to your systems are wiped out.
The Rubrik Identity Resilience integration with CrowdStrike Next-Gen Identity Security is now Generally Available. Learn more about Rubrik Identity Resilience and schedule a demo today!