The process of securing an organization's valuable data oftentimes is quite fluid. Teams will initially set Access Control Lists (ACLs) on our data, ensuring that only the people who need access, have access, but things change. People move in and out of the company, move horizontally within the organization, and configuration drift occurs. With this, often updating these ACLs gets forgotten or missed, leaving access to this sensitive information wide open to users and groups that quite honestly, don’t need it.
Many ransomware attacks are the result of a compromised user account, it’s crucial to ensure that organizations know where their sensitive data is, what type of sensitive information it is, and how much of it exits. In 2022, Rubrik observed that a typical organization had 562,301 files containing sensitive data and 24,881,378 sensitive records within these files.
Another critical piece to the puzzle: organizations must understand exactly who has access to this information data and how that access has changed over time. Only then can the company take proactive actions to ensure its data is secure.
Introducing User Access Analysis
Rubrik Sensitive Data Monitoring and Management has long provided insights around classifying sensitive information, pointing out what type of data and where that data exists within environments. We are excited to introduce this added layer of insights within Rubrik Security Cloud so that our customers truly understand who has access to this sensitive information as well, offering a holistic view of sensitive data and its’ respective exposure risk.
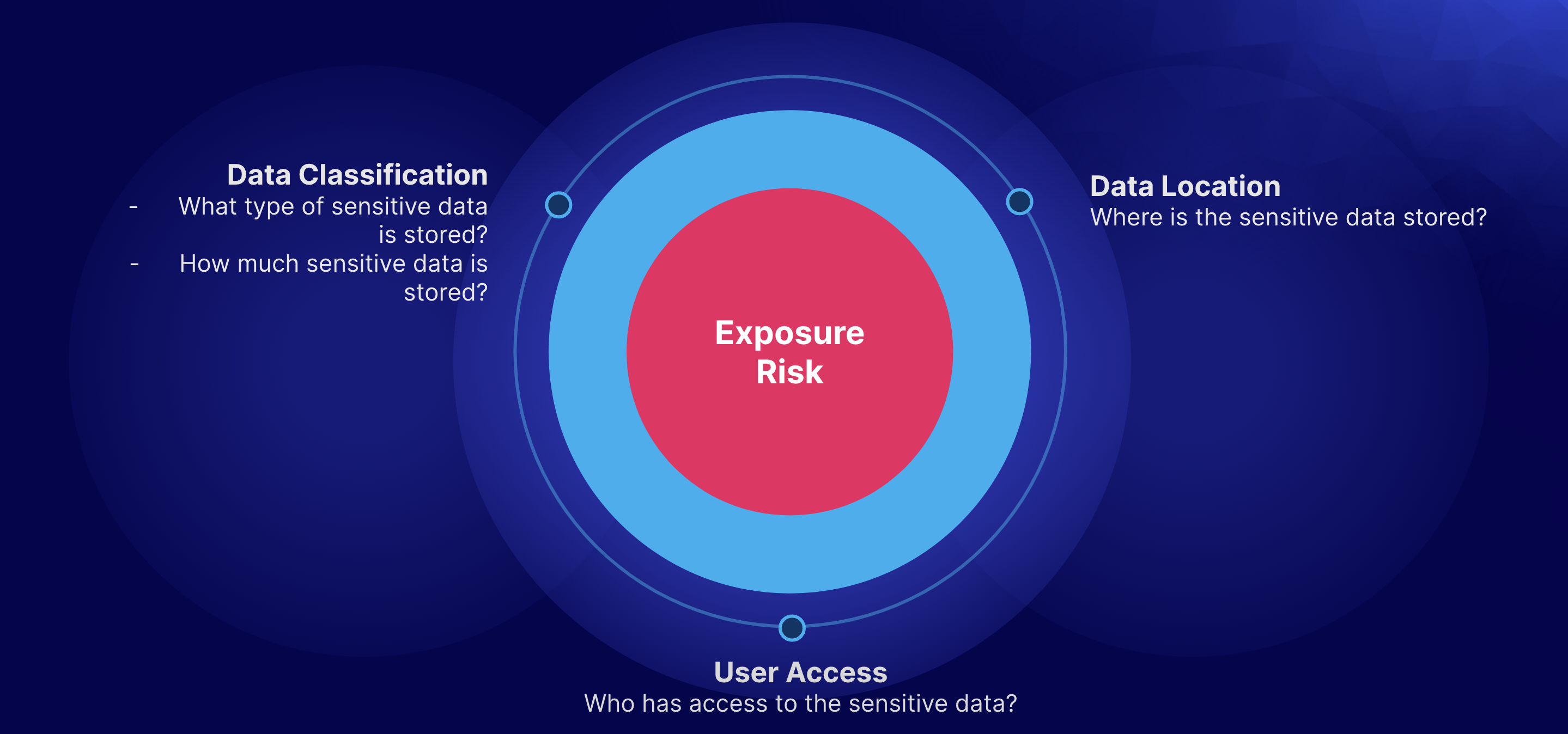
User Access Analysis will complete the exposure risk triad by tying into Sensitive Data Monitoring and Management and pointing out exactly who has access to your sensitive data, be it individual users or groups. This will allow organizations to take valuable, proactive steps to ensure that proper ACLs are in place, only allowing access to data to those who should have it, essentially minimizing the impact of a cyber attack should it occur through a compromised user account with over-provisioned access.
User Access Analysis is fundamentally powered through risk calculation. By allowing organizations to set risk levels on their analyzers, customers are able to better align Rubrik’s prebuilt sensitive data analyzers with their business objectives. For instance, an analyzer scanning for PCI data is certainly important and may be set to high risk, while an analyzer scanning for IP Addresses, while still important, probably can be deemed as lower risk. During the scanning for sensitive information, Rubrik takes these defined risk levels and provides a risk analysis through three different lenses: File Risk, Object Risk, and User Risk. Let’s take a look at each.
File Risk - File Risk is determined by the level of risk of the matched analyzer on the files themselves. If a file contains hits from a high-risk analyzer, it is deemed a high-risk file, and so on for medium and low risk.
Object Risk - File Risk then bubbles up into the overall object risk - if an object or a workload contains files that have been labeled as high risk, the object itself is high-risk, and again, the same for medium and low risk.
User Risk - User Risk is calculated by analyzing the types of files and their associated risk that users have access to. If a user has access to high-risk files, then the user is deemed as a high-risk user, and so on for medium and low risk.
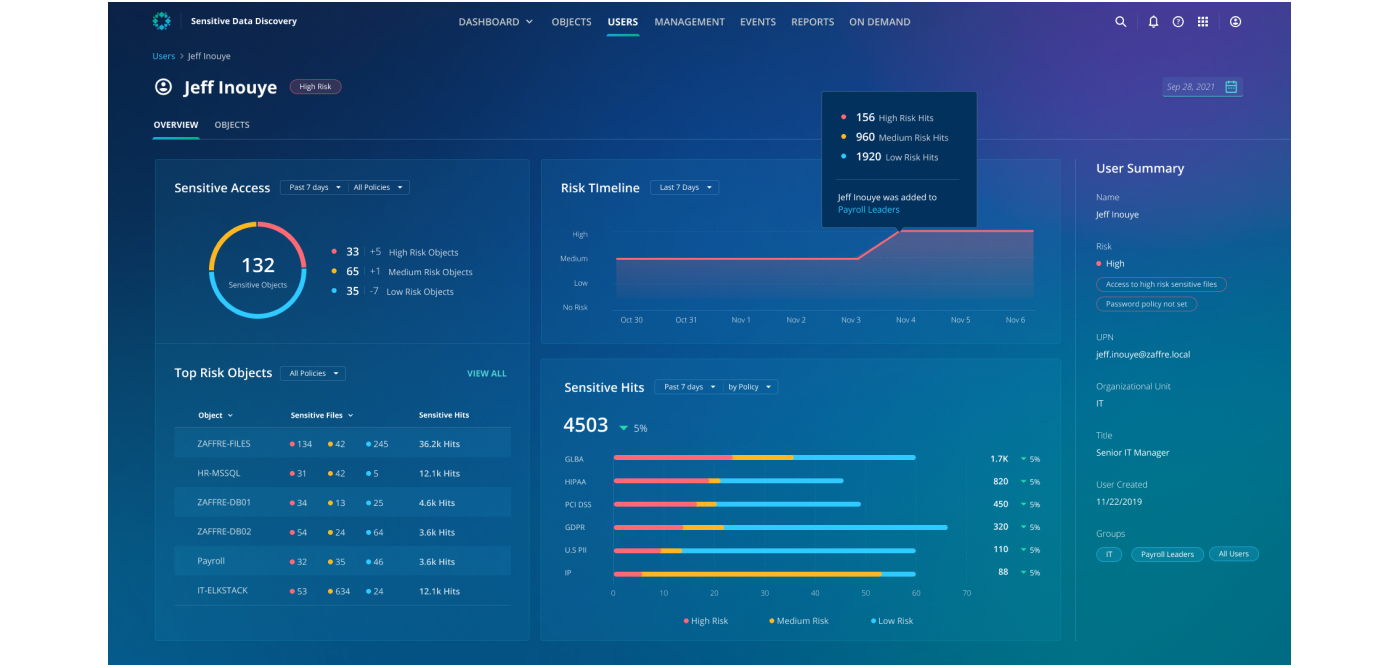
In addition to simply pointing out who has access to your sensitive information and bubbling up risk analysis and exposure to the UI, User Access Analysis will also report on how that access has changed over time. Take the above image as an example, we can see that our user Jeff has been deemed a high-risk user, and we can also see exactly when Jeff’s risk status changed. In addition to this, valuable information is displayed to attempt to hint at what else happened during that risk elevation - in this case, Jeff was added to the “Payroll Dump” AD Group, which in turn had access to high-risk files, thus increasing Jeff's overall risk. If this was not a desired action, we can then take a proactive action to remove Jeff from the group, ensuring that his access isn’t overprovisioned.
User Access Activity enables proactive data risk management by providing visibility into sensitive data access, calculating risk, and tracking changes to the data and associated risk over time. Using analytics, User Access Activity will identify and rank the users and groups who have access to sensitive data to enable administrators to take appropriate measures to protect their sensitive data. And the entire process of scanning for sensitive data and determining user access will happen on your backup data, essentially, the catalog of your entire environment - no heavy-duty agents, no impact on production. Remember, you wouldn’t leave your valuables sitting out on your front porch accessible to the world, so why would you leave your data unattended?
Start Your Journey to Regain Control
To learn more about this exciting advancement in zero trust data security and to find out how you can discover who has access to your sensitive information, join us at Forward, Rubrik’s annual user conference, to dive deeper into this announcement. Register for Forward here.
SAFE HARBOR STATEMENT: Any unreleased services or features referenced in this document are not currently available and may not be made generally available on time or at all, as may be determined in our sole discretion. Any such referenced services or features do not represent promises to deliver, commitments, or obligations of Rubrik, Inc. and may not be incorporated into any contract. Customers should make their purchase decisions based upon services and features that are currently generally available.
