Security teams use tools like Microsoft Sentinel to aggregate their security events, alert on threat detection, and most importantly, orchestrate threat responses through a variety of automated playbooks. By providing both Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) functionality, Sentinel enables teams to respond to threats quickly and efficiently.
As part of our Winter Release, Rubrik showcased the integration of Rubrik Security Cloud with Microsoft Sentinel.
With this bidirectional integration, teams can both (1) enrich their investigations by bringing Rubrik insights (e.g., anomalies, sensitive data) into Sentinel; and (2) execute Rubrik workflows (e.g., threat hunt, orchestrated recovery) directly from within Sentinel and Microsoft Teams.
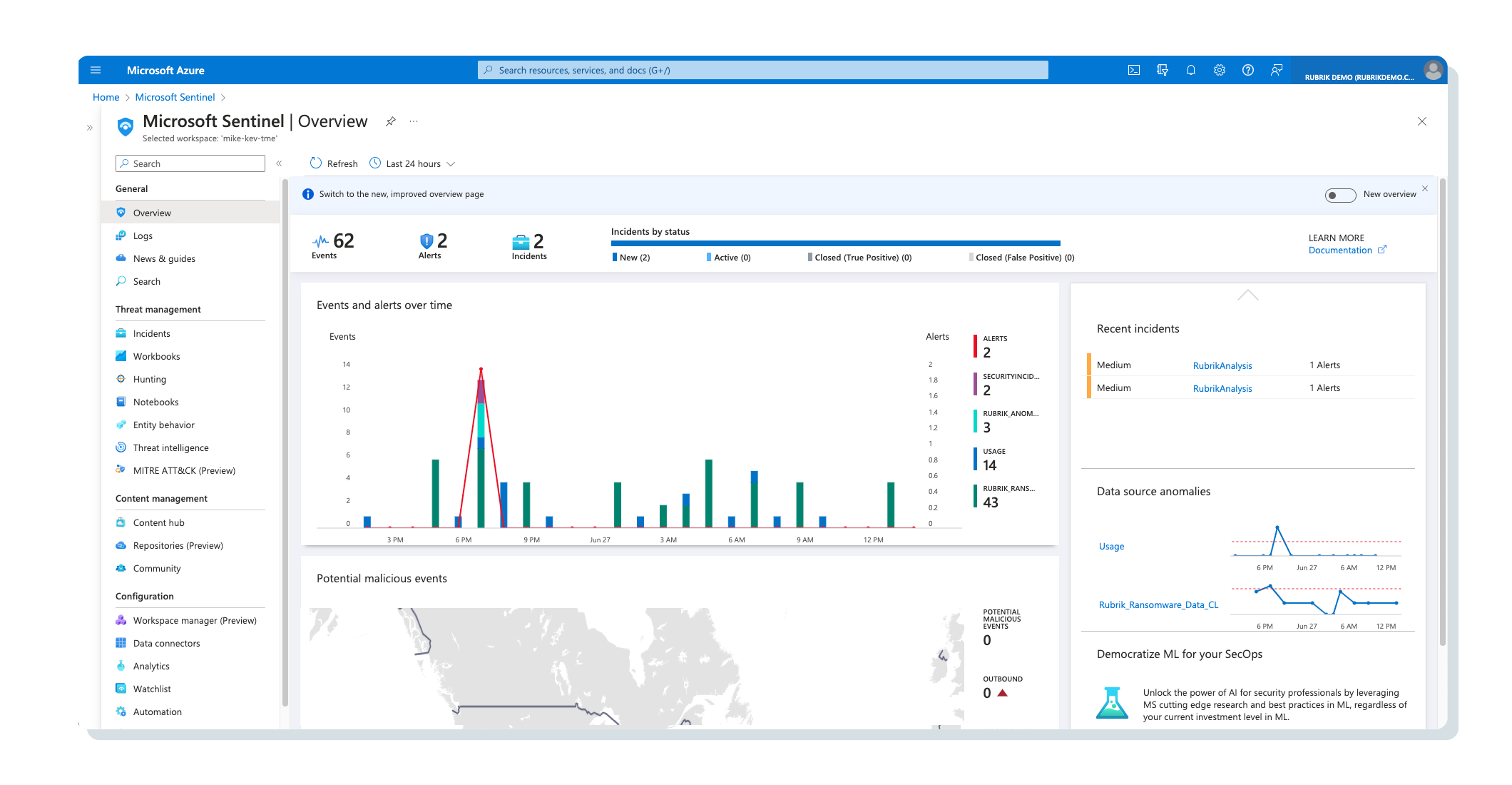
View Rubrik-generated anomaly alerts within Sentinel
Now there is a way to streamline incident response even further.
Introducing a new integration with Azure OpenAI Service
Azure OpenAI Service uses large-scale, generative AI models, allowing organizations to streamline operations and improve efficiency. Coupling this with the scale, simplicity, and privacy delivered by Azure, organizations can be assured that:
Data is not shared with other Customers – Customers retain control over their prompts (inputs) and completions (outputs), embeddings, and training data and what happens with it..
Data is not used to train the foundational AI models – While customer provided data may be used to train customer-owned models, foundational AI models are not retrained utilizing customer data.
Data is protected by comprehensive enterprise compliance and security controls – Azure security controls can be utilized to ensure data is secure and protected.
By incorporating the power of large language models and generative AI, Rubrik and Microsoft are empowering IT and security teams to:
Streamline Incident Creation to help incident response teams prioritize alerts by automatically creating an incident in Sentinel based on anomalous activity detected within the Rubrik Security Cloud machine learning models.
Recommend Task Workstreams by suggesting incident response tasks that will enable IT and security teams to investigate the incident more rapidly while preserving evidence for forensics purposes.
Accelerate Cyber Recovery by dynamically generating Kusto Query Language (KQL) syntax for investigating the incident in Microsoft Sentinel, allowing IT and security teams to react swiftly to maintain business resilience.
How It Works
It begins with the existing Rubrik integration with Microsoft Sentinel. Rubrik Anomaly Detection continuously monitors backups as they are ingested, feeding data through a machine learning model utilized to detect not only file activity (e.g., additions, modifications, deletions) but also encryption within the filesystem. As anomalies are identified, this information flows into Microsoft Sentinel tables, bringing Rubrik’s valuable time-series analysis of data into the hands of security teams.
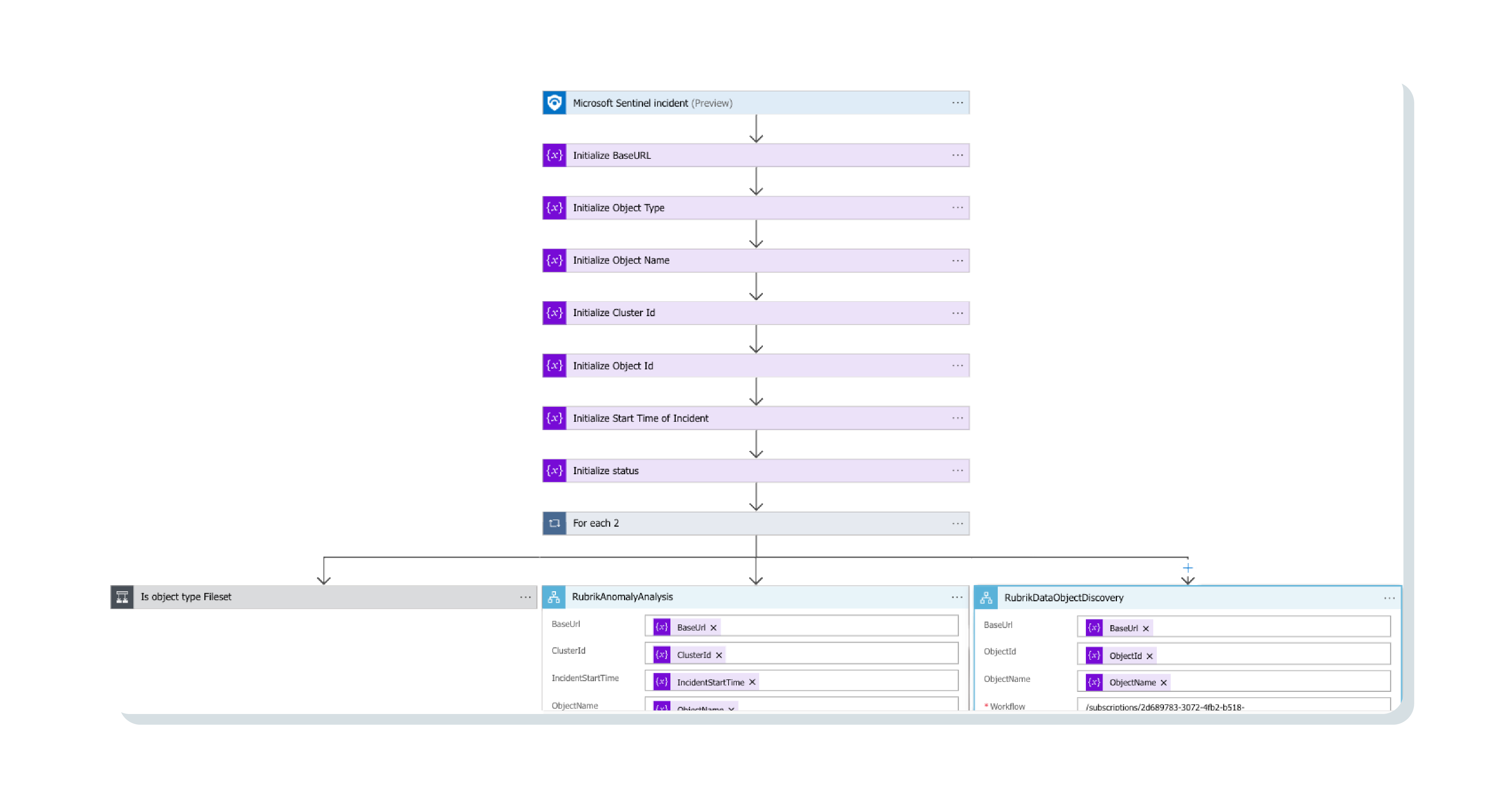
A custom analytics rule within Sentinel watches for the anomalous activity indicated by Rubrik. When found, an incident is automatically created, generating a workspace for security teams to both triage and collaborate on the threat. On top of this, playbooks are also triggered within Sentinel gathering key data from Rubrik Sensitive Data Monitoring & Management service such as what sensitive data exists, how much of it exists, and where it is located. All this information is readily available within Sentinel for SecOps to utilize in the triage and root-cause analysis of the incident.
In parallel to gathering information around sensitive data, the future integration will execute another Sentinel playbook, this time connecting to Azure OpenAI Service. The playbook is designed to provide key information to the OpenAI model including Rubrik Security Cloud capabilities, the capabilities of the pre-built Rubrik SOAR playbooks, and information around the incident itself. The goal – Azure OpenAI Service generates recommendations around suggested next steps incident responders can take and attaches them as tasks to the incident within Sentinel.
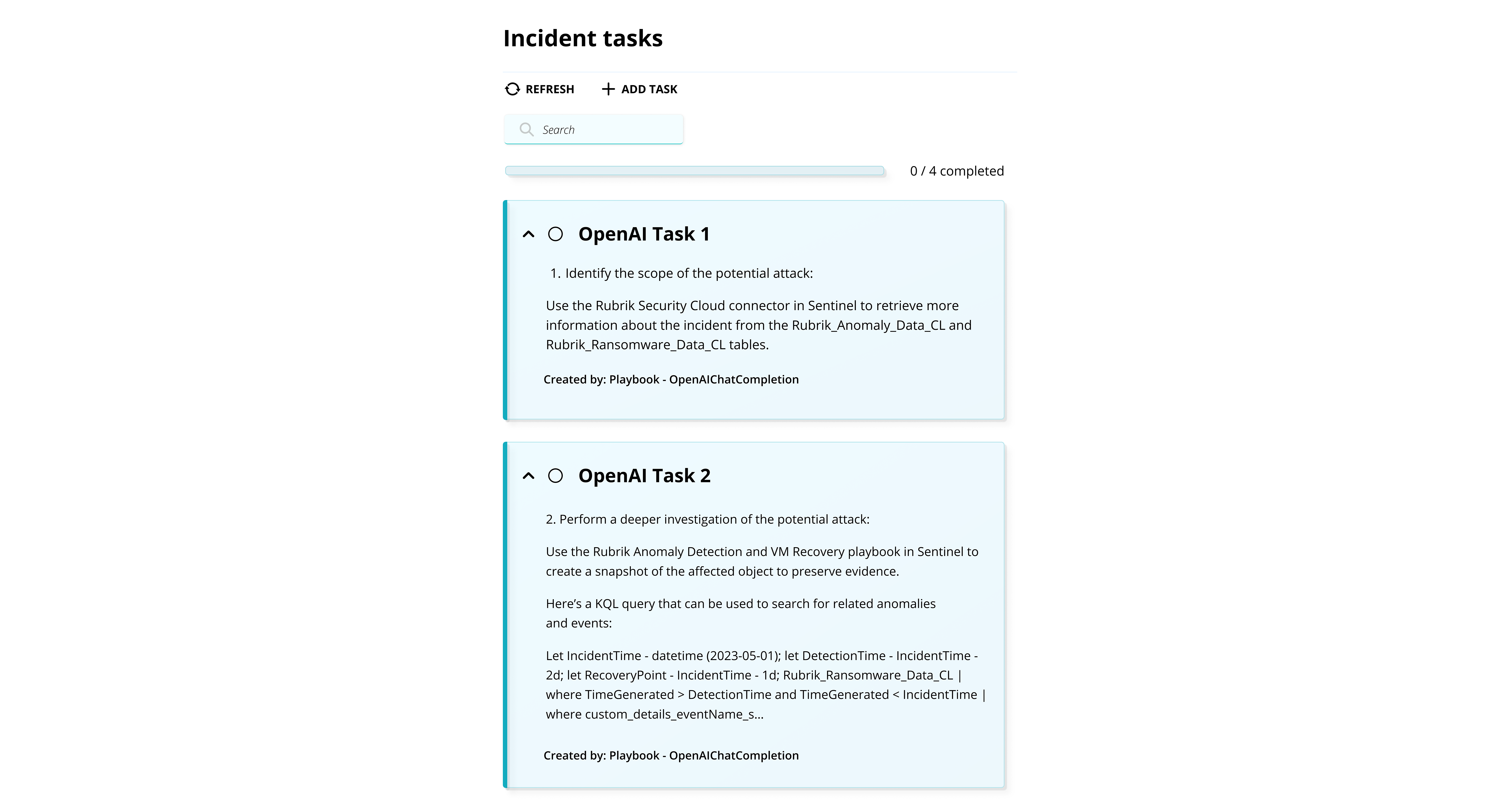
Depending on the type of incident, recommendations can vary. Some examples of the AI generated recommendations are:
Identify the scope of the potential attacks by leveraging the playbooks within Microsoft Sentinel to gather more information from Rubrik Security Cloud through the Anomaly Detection service.
Identify traces of malware within backups by providing YARA rules and leveraging playbooks connecting to Rubrik Threat Hunting.
Perform deeper investigations and quickly search for related events in the Sentinel dashboard with AI-generated Kusto Query Language (KQL) syntax.
Conclusion
In the midst of a ransomware attack, time is of the essence. The speed at which an organization responds to the attack can greatly impact both the scope of the attack and the potential for a successful recovery. Rubrik has generated valuable insights for security teams to utilize, within Sentinel, to respond to attacks. Now, additional AI-generated recommendations can help ensure that security teams are even more armed to investigate, triage, and recover from cyber threats.
To learn more, visit the Rubrik and Microsoft Sentinel solution page.
SAFE HARBOR STATEMENT: Any unreleased services or features referenced in this document are not currently available and may not be made generally available on time or at all, as may be determined in our sole discretion. Any such referenced services or features do not represent promises to deliver, commitments, or obligations of Rubrik, Inc. and may not be incorporated into any contract. Customers should make their purchase decisions based upon services and features that are currently generally available.
