Hackers aren’t breaking in, they’re logging in - and looking for your sensitive data.
With threat actors using stolen credentials to bypass perimeter defenses, cyber attacks are inevitable. Rubrik DSPM helps you to proactively secure and monitor your data, thereby minimizing the impact of security incidents.
94%
of IT and security leaders reported their organizations experienced a significant cyber attack last year.¹
82%
incidents involving malicious insiders were based on the abuse of privileged access.²
98%
of organizations report significant data visibility challenges.³
Gain visibility. Reduce risk. Minimize impact.
Rubrik DSPM automatically discovers, classifies, and monitors your sensitive data so you can remediate data security violations, minimize access to sensitive data, and detect data threats early.
Data Discovery and Classification
Gain visibility and control of your data across on-prem, cloud, and Saas, so you can put security controls in place, manage data requirements, and guide your organization’s AI strategy.


Data Risk Management
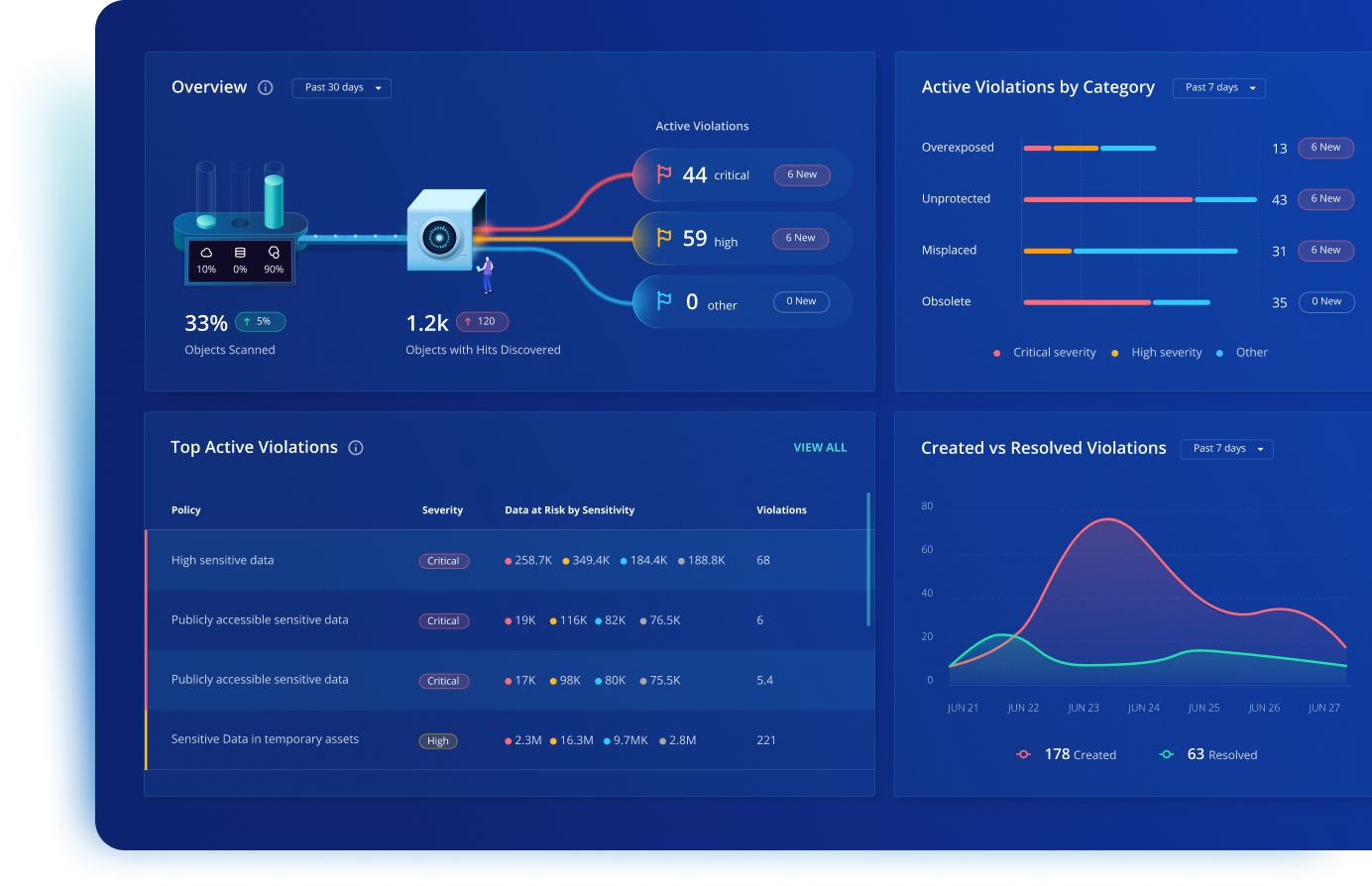
Get alerted to sensitive data that is overexposed, misconfigured, obsolete, or misplaced – so you can remediate risks and minimize the impact of cyber attacks.
Data Access Governance (DAG)
Minimize the impact of security incidents by strategically managing access to your organization’s sensitive data.


Data Detection and Response (DDR)
Get alerted to anomalous and suspicious cloud data activity in near real time so you can investigate and contain data breaches early, minimizing the damage to your business.
Explore more of our resources


Demo
Intro to Rubrik Security Cloud
Take a self-guided demo to explore our data security platform that protects, monitors, and quickly recovers your data.