We are excited to announce the general availability of Threat Monitoring and Turbo Threat Hunt for NAS Cloud Direct (NCD), bringing automated threat detection to your on-premises file storage and cloud file services.
With this release, two powerful capabilities can now protect your data:
Threat Monitoring provides continuous, automated scanning of every backup for known threats.
Turbo Threat Hunt enables on-demand investigation to identify clean recovery points in seconds during active incidents.
The Backup Visibility Gap
Production environments typically have layered security: endpoint EDR agents, network intrusion detection, SIEM correlation, and vulnerability scanning.
But backup infrastructure? That's often where security visibility ends.
Modern ransomware campaigns systematically exploit this gap between production security and backup security. Attacks follow a predictable pattern:
Initial compromise through phishing, credential theft, or vulnerability exploitation
Lateral movement to capture adjacent systems and establish persistence
Patient waiting while malware is archived in routine backup cycles (30-90 days)
Simultaneous detonation of malware to encrypt production systems and delete/corrupt backups
This threat landscape is severe. According to Palo Alto Networks' Unit 42, 99% of IT and security leaders were made aware of at least one attack in 2022, dealing with attacks an average of 52 times that year. The highest ransom demand reached $50 million USD.
The stakes are high:
Organizations often discover backup contamination only after attempting recovery
Restoring infected backups leads to reinfection, extending downtime, and compounding costs
If threats lurk undetected in backup snapshots, which backup is safe to restore?
Without automated threat detection, answering that question requires manual investigation, mounting snapshots individually, scanning with antivirus tools, and documenting results. For enterprises with thousands of snapshots, this process takes weeks or months.
Threat Monitoring and Turbo Threat Hunting address this visibility gap with three complementary capabilities:
Proactive detection identifies threats as they enter backups, enabling early response before production impact escalates.
Rapid investigation delivers answers in seconds during active incidents, allowing teams to identify clean recovery points while still on the incident response call rather than waiting weeks for forensic analysis.
Zero performance impact on production file servers and NAS arrays, and attackers monitoring production systems remain unaware of ongoing investigations as both capabilities operate out-of-band on backup infrastructure.
How It Works: Threat Monitoring
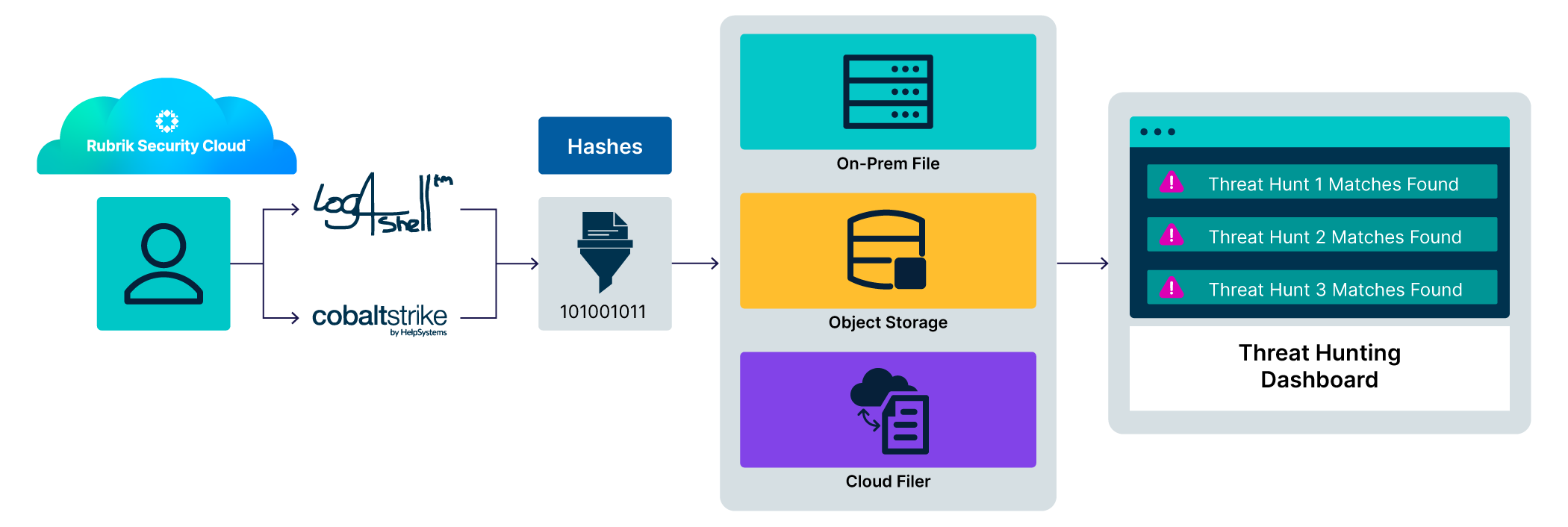
Figure 1: How Threat Monitoring works
Continuous Automated Detection
Threat Monitoring automatically scans every backup snapshot for Indicators of Compromise using curated threat intelligence that updates daily.
The Process: As backups are ingested from NAS CD sources, Rubrik computes file hashes (MD5, SHA1, and SHA256) for executables, scripts, and other high-risk file types. These hashes are stored in a catalog. When the threat intelligence feed updates with new IOCs, the system automatically queries the existing hash catalog without rescanning snapshots.
What Gets Scanned: The system focuses on file types commonly exploited by attackers:
Linux systems:
- Any file with the execute permission bit set
- ELF binary format files (identified by file header)
Windows systems:
- Common executable and script extensions including: .exe, .dll, .bat, .ps1, .cmd, .js, .vbs, and others
- Complete list: .acm, .ax, .bat, .cmd, .com, .cpl, .dll, .drv, .efi, .exe, .js, .jse, .msi, .mui, .ocx, .ps1, .psc1, .scr, .sys, .tsp, .vbe, .vbs, .wsf, .wsh
- PE (Portable Executable) format files (identified by file header)
File selection uses extension matching, file type detection (magic numbers), and permission analysis to balance comprehensive threat coverage with scanning efficiency.
This architecture is both fast and cost-effective. When security researchers discover new threats, Rubrik can detect them retroactively in historical backups by checking pre-computed hashes against newly published IOCs.
Intelligence Sources
The threat feed aggregates intelligence from multiple authoritative sources:
Rubrik Zero Labs: Internal threat research focused specifically on data-centric attacks, ransomware targeting backup infrastructure, and emerging malware families affecting NAS and file storage.
Rubrik InfoSec: Real-world intelligence from protecting Rubrik's own infrastructure and insights gained across thousands of customer deployments.
Vetted Third-Party Sources: Carefully selected feeds from trusted security research organizations and open-source intelligence projects.
Rubrik's security team curates the intelligence feed to ensure high quality and minimize false positives. IOCs are validated before inclusion and the feed updates daily to protect against the latest threats. Organizations can also import custom IOCs from their own threat intelligence platforms, Information Sharing and Analysis Centers (ISACs), or internal security investigations.
Out-of-Band Analysis
All scanning occurs on backup infrastructure, completely separate from production NAS systems.
This means zero performance impact on file servers. No additional load on production storage arrays. No network bandwidth consumed by scan traffic.
If attackers are present in your production environment—monitoring processes, watching network traffic, or observing security tool activity—they remain completely unaware of threat detection occurring in your backup infrastructure.
This out-of-band approach enables security teams to gather evidence, map attack timelines, and identify compromised systems without tipping off adversaries or triggering immediate data destruction.
Set It and Forget It
Initial configuration takes mere minutes. Then, Threat Monitoring runs continuously without manual intervention. New snapshots from NAS CD sources are automatically scanned as they're created. New threat intelligence gets ingested and checked against the existing hash catalog automatically. Daily feed updates happen in the background.
Your security team engages only when there's an actual IOC detection, receiving alerts with full context on the threat, affected systems, and timeline.
How It Works: Turbo Threat Hunt
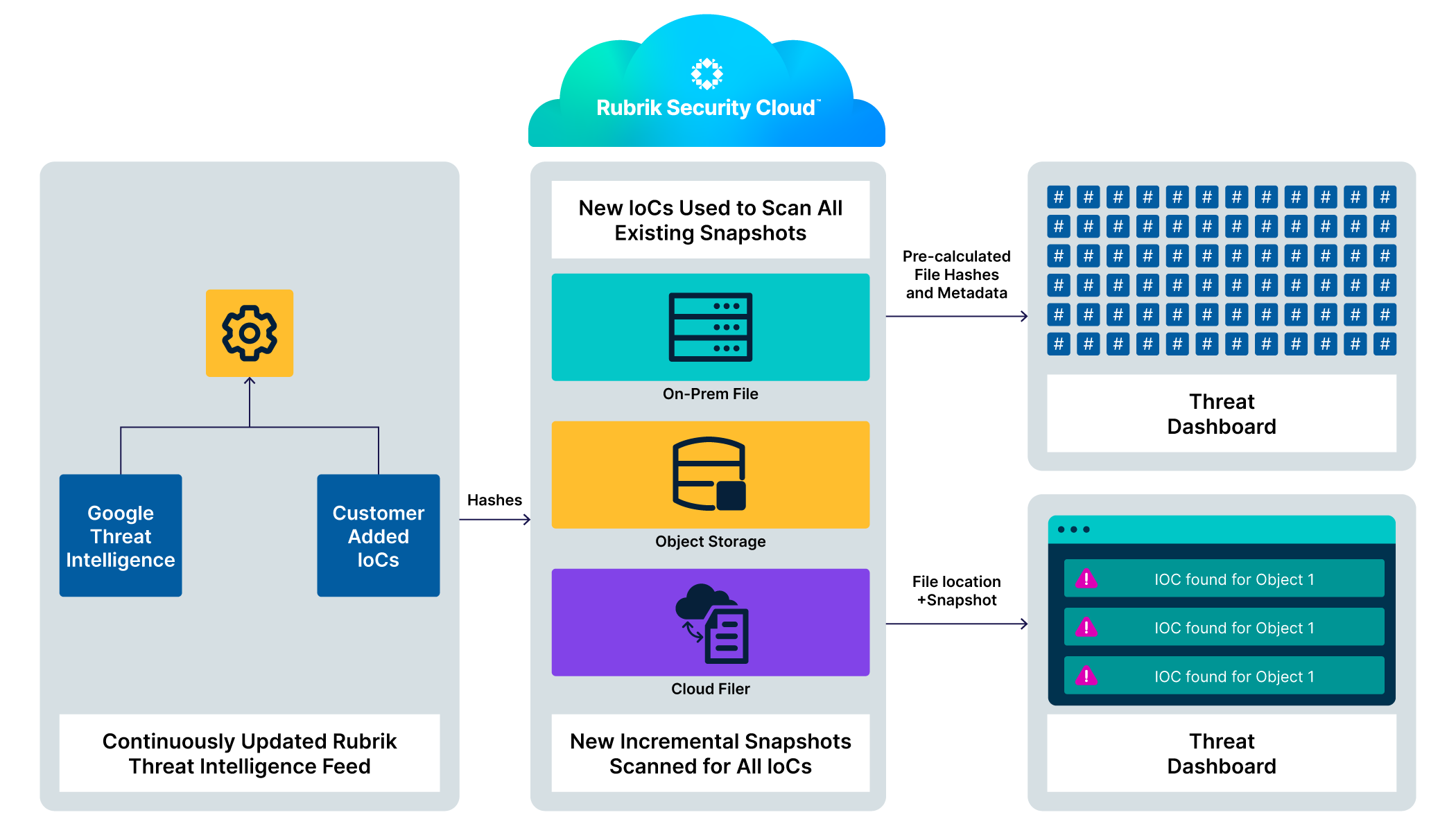
Figure 2: How Threat Hunting works
On-Demand Rapid Investigation
When you're responding to an active incident and need to know which backups are safe to restore, Turbo Threat Hunt delivers answers in seconds.
In large NAS environments, the traditional serial backup investigation can take weeks or months. The team has to mount each snapshot to an isolated system, wait for the mount and decompression operations, run antivirus or malware scans on the mounted data, document the results, unmount the snapshot, and move on to the next snapshot. Then repeat these steps hundreds or thousands of times.
Now, Turbo Threat Hunt can leverage the continuously built hash catalog from Threat Monitoring. When you provide IOCs, the system performs database queries against indexed hashes rather than scanning raw backup data. Internal testing demonstrates scanning speeds of approximately 80,000 backups in under a minute. This performance is possible because the system queries pre-computed metadata rather than mounting, decompressing, and scanning actual snapshot files.
Both capabilities operate out-of-band on the backup infrastructure, ensuring zero performance impact on your production file servers and keeping your investigation invisible to attackers.
What's Included in This GA
This GA release focuses on hash-based IOC detection (MD5, SHA1, SHA256) with daily feed updates. Turbo Threat Hunt can scan approximately 80,000 snapshots in under a minute and supports up to 100 hashes per hunt. These features require Rubrik Enterprise Edition.
Supported Sources:
On-Premises: NetApp (7-Mode, Cluster Mode), Dell PowerScale
(Isilon), Qumulo, Pure (FlashBlade, FlashArray), Nutanix File Server, IBM
Storage Scale (GPFS), Vast Data, Generic NFS/NFSv4/SMB
Object Storage: Generic S3 (on-premises S3-compatible object storage)
Cloud File Services: AWS FSx for NetApp ONTAP, Azure NetApp Files, Azure Files
Deployment: Enable per NCD site (RSC cluster) with granular control over which on-premises environments receive automated threat detection.
Intelligence: Daily feed updates from Google Threat Intelligence powered by Mandiant, Rubrik Zero Labs, Rubrik InfoSec, plus custom IOC imports.
Operation: All scanning happens out-of-band on backup infrastructure, zero file server performance impact, no attacker visibility into investigations.
Integration: Alerts route to SIEM/SOAR platforms (Splunk, QRadar, Sentinel, ServiceNow) via webhooks and APIs.
The Bottom Line
During every cyber incident, one question determines the success of recovery: "Which backup is safe to restore?" With Threat Monitoring and Turbo Threat Hunting for NAS Cloud Direct, the answer changes from "We're investigating" to "Here's a clean backup—and we can prove it."
Enable today and protect your data on-premises file storage, on-premises object storage, and cloud file services with continuous threat detection and instant investigation.
Contact your Rubrik account team for guided walkthroughs, assistance with SIEM/SOAR integrations, or deployment questions.
