Akira is a ransomware-as-a-service operation that surfaced in March 2023 and quickly expanded across North America, Europe, and Australia. It primarily hits small and midsize businesses and public institutions, but larger enterprises aren’t immune.
If Akira’s ransomware successfully infects your system, the attackers will hit you with what security pros call double extortion. The attack will both encrypt and exfiltrate your data. Attackers will demand that you pay up, both to regain control of your data and to prevent them from leaking or selling sensitive stolen information.
Like many forms of ransomware, Akira blends credential theft, social engineering, and VPN exploitation to gain access to your system. What makes Akira distinct is that once it breaches your system, it turns its attention to your hypervisors. Within weeks of the malware's debut on the scene, its operators were deploying a Linux variant that targeted VMware ESXi hosts—allowing them to encrypt dozens or hundreds of virtual machines from a single control point. Later builds added VM-specific options such as “vmonly” and “stopvm,” enabling rapid mass encryption of virtualized workloads. The U.S. Department of Health and Human Services noted that Akira’s Linux variant specifically disrupts VMware-based environments.
As of early 2024, the group’s leak site listed roughly 200 victims, and open-source analyses estimate total ransom proceeds approaching $42 million—though keep in mind those figures are based on public claims rather than verified disclosures.
The bottom line is that if your backup or recovery workflows share the same control plane as production VMs, Akira’s ESXi focus can turn that architecture into a single point of failure.
How Akira Ransomware Works
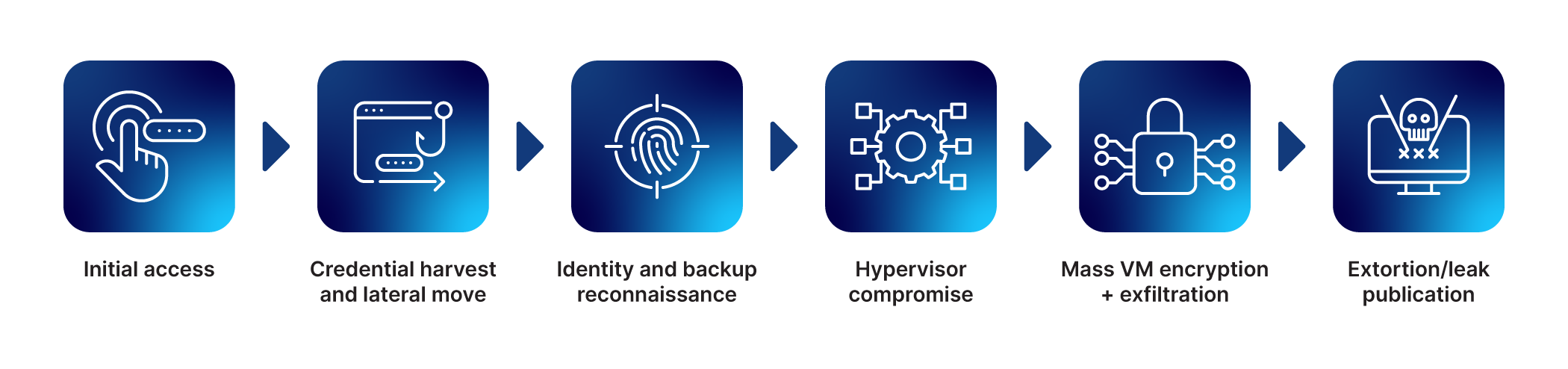
Akira cyberattacks begin with attackers using one of the typical means of gaining access to their victims' infrastructure. This typically uses one or more of the following common tactics: phishing emails, credential theft, exposed RDP, or compromised VPN sessions. Recent reporting also ties Akira to exploitation of edge-device flaws—SonicWall appliances, for example—underscoring how unpatched perimeter gear enables access.
Once the attackers are inside, they hunt for identity systems, backup consoles, and hypervisors.
When the bad guys find VMware ESXi or other hypervisors, they exploit management interfaces or stolen admin credentials to gain control of many VMs at once. Akira’s Linux-based encryptor can run on ESXi hosts and uses VM-aware switches to stop virtual machines gracefully, then encrypt guest files or attached datastores. At the same time, operators commonly exfiltrate sensitive files using rclone, SCP, or cloud storage APIs.
Double extortion follows. The victim panics because their production data is encrypted, and then is also threatened with a leak of the stolen data if the ransom isn’t paid. It's a businesslike extortion process rather than a chaotic scam. During negotiations, the attackers demonstrate what files they've stolen as proof of their success and provide the victims with deadlines and even the chance to negotiate a reduced ransom.
Operators may also deploy backdoors and create rogue admin accounts, poisoning recovery paths so restore points look compromised.
CISA has a good breakdown of the process, but a simplified attack flow chart looks something like this:
Who is Behind Akira? Profiling the Hacker Group
Akira operates as a Ransomware-as-a-Service (RaaS) crew: a core developer team recruits affiliates to carry out intrusions, then splits the proceeds. The model reduces the developer’s exposure while scaling attack volume. Attribution remains imprecise, but technical clues and language artifacts point to operators likely resident in Russia or nearby states. That's typical of many prolific RaaS groups, though definitive state sponsorship or exact identities can't be publicly confirmed.
The attackers will demand payment in cryptocurrency, with negotiations conducted via the group’s leak/negotiation site and private messaging, which is all standard operating procedure for ransomware. Their extortion playbook is psychological and transactional: publish proof files, set deadlines, offer discounts, and threaten public exposure to force payment.
Real-World Impact: Case Examples of Akira Attacks
Most organizations are understandably reluctant to describe successful cyberattacks against their infrastructure. But Akira has been tied to a number of high-profile incidents:
Stanford University: In late 2023, Stanford admitted that its public-safety system suffered a ransomware incident; Akira later claimed it was the perpetrator and posted files it had allegedly exfiltrated. The university treated it as a contained compromise, but the episode shows how quickly sensitive repositories can be targeted and announced on leak sites.
Hitachi Ventara: In April 2025, this major cyber-infrastructure provider reported a disruptive ransomware incident and took servers offline; several outlets linked the activity to Akira even as the vendor continued its investigation. For a service provider like Hitachi Ventara that hosts multiple customers, the downtime would've made this an extremely costly attack.
Toppan Next Tech: This Singapore-based printing company reported a ransomware intrusion that exposed client statements. Subsequent leak-site posts and threat trackers indicate the Akira group later claimed responsibility.
Across these and other attacks, Akira publishes large daily victim lists and posts proof documents to pressure payments, making the attacks much more damaging than the initial data encryption event. The group moves quickly and leaves ruinous financial damage in its wake. That’s why a proactive, architecture-first recovery posture matters, and why organizations should build recovery paths that don’t rely on a single control plane.
How to Protect Against Akira Ransomware
Akira leverages access, reconnaissance, and hypervisor control to maximize damage. You need a multi-layer defensive posture to limit its impact. Here's a quick step-by-step checklist:
Harden access and perimeter: Patch VPN/SSL appliances, remove exposed RDP, rotate credentials, and tighten MFA and conditional access
Limit blast radius with the principle of least privilege: Segment networks, separate admin duties, and avoid using the same accounts for backups and production
Detect earlier: Add telemetry that covers identity systems, hypervisor consoles, and backup activity so you can spot the attackers' discovery and exfiltration processes
Practice recovery: Rehearse full identity and hypervisor restores in advance so you can act quickly under pressure if an attack does succeed
Rubrik Security Cloud provides multiple layers of resilience in the face of threats like Akira:
Immutable, logically air-gapped backups: Akira aims to corrupt or delete backups. Rubrik snapshots are immutable: they cannot be altered or removed by attackers, even if primary credentials are compromised. This logical air gap gives teams a clean recovery source when production is poisoned.
Anomaly detection on backup data: Akira’s reconnaissance and exfiltration produce unusual file-movement patterns. Rubrik continuously analyzes backup snapshots for strange adds, deletes, or encryption signatures so defenders can spot compromise windows and select a precise clean restore point.
Rapid, large-scale recovery: Instead of slowly restoring files one by one, Rubrik can instantly mount snapshots and bring files, apps, or whole VMs back up within minutes—letting critical operations resume while deeper recovery proceeds.
Sensitive data discovery: When Akira attackers threaten to publicize stolen data, teams need to know what was exposed. Rubrik’s continuous scanning classifies PII/PHI and other sensitive data inside backups, so response and notification can be prioritized accurately.
Threat hunting and surgical restores: By indexing historical snapshots, Rubrik helps identify the blast radius and recover only data you know is clean, so you can avoid reintroducing malware on systems you've just restored.
Rubrik Continuous Data Protection captures these snapshots and enables near-instant rollback to a known-clean state. And a single-pane interface like the Data Security Command Center can correlate backup telemetry, anomaly alerts, and sensitive-data scans, so your backup artifacts become assets you can use to hunt and respond to threats.
In short, while endpoint security and firewalls are focused on preventing the initial breach, Rubrik provides cyber resilience. If an attacker like Akira does get through your defenses, you can protect your data, rapidly restore your business operations, and confidently refuse to pay the ransom.
Building a Ransomware-Ready Cybersecurity Posture
Akira is a fast-moving, destructive strain of malware that hits companies with unprepared architectures and sends them into weeks-long tailspins. Long-term defense combines people, process, and platform: you should adopt continuous data protection, isolate backup control planes, and practice orchestrated identity recovery. Pair hardening and detection with frequent, automated recovery rehearsals so teams can act decisively when compromise happens. Architecture—not luck—determines whether an intrusion becomes a brief interruption or an existential disaster.
To protect your business continuity, contact Rubrik to discuss your recovery architecture.

