There’s a crisis in healthcare. The crisis we are referring to is not the economic system, but rather cyber threats targeted at hospitals’ data. In February, a cyberattack in Los Angeles left the Hollywood Presbyterian Medical Center paralyzed without access to electronic records while its hackers held its computer systems captive for a reputedly multi-million dollar ransom. The result – a 40 bitcoin (approximately $17,000) payment and a loss of operations for over a week. This cyberthreat, known as ransomware, is growing and is predicted to increase in 2016. In one week alone, three hospitals were hit by ransomware attacks.
How do hospitals protect themselves from ransomware threats? To answer this question, we sat down with David Ramos, who leads the development of Rubrik’s security measures. Ramos has a Ph.D. from Stanford in Computer Science and discovered dozens of security bugs in open source software, including three in OpenSSL for which security advisories were issued. Ramos explains why hospitals are especially vulnerable to these types of attacks, and why data protection and security need to be integrated at the highest standard in a reliable backup solution.
Q. What is Ransomware? How is Ransomware different from other cyber threats?
A. Ransomware is a special type of malware in which an attacker holds users’ data hostage until a ransom is paid. Many forms of ransomware use strong cryptography to encrypt a victim’s data using an encryption key known only to the attacker. After a specified length of time, the attacker deletes the encryption key, and the victim’s data is lost forever. Even if the victim pays the attacker prior to this deadline, the attacker may or may not provide the victim with the required decryption key.
Ransomware differs from traditional threats to information security in that the attacker’s goal is not to steal the data, but rather to prevent the victim from accessing his or her own data. In other words, ransomware is a denial-of-service attack rather than an attack on data privacy. In most cases, the data affected by ransomware never actually leaves the organization. This aspect of ransomware makes traditional network defenses that aim to prevent data exfiltration ineffective against these attacks. In fact, ransomware can often successfully attack a victim even if firewalls and other defenses prevent it from communicating any information back to the attacker.
Q. Why are healthcare organizations more vulnerable to ransomware attacks?
A. Healthcare organizations have a critical need for continuous access to their data beyond that of most other industries. Patient records, imaging data, and other clinical data is stored exclusively in electronic records in many healthcare organizations today. If this data becomes unavailable to healthcare providers at any time, patients’ lives may be at risk. Worse, organizations that employ automated systems for dispensing drugs and performing other basic tasks may be ill-equipped to handle an unplanned outage caused by ransomware.
Attackers realize the criticality of healthcare data and are increasingly targeting healthcare organizations with ransomware. Unfortunately, the very criticality of the data that makes healthcare organizations an appealing target to attackers also makes it difficult for healthcare IT organizations to take steps to prevent these attacks. For example, many end-user computer systems utilized by healthcare providers run outdated operating systems with known vulnerabilities. Updating these systems, while reducing the likelihood of an attack, would potentially cause its own disruption to patient care. In addition, patient records and imaging data are often transferred between healthcare organizations using physical media (e.g., CD/DVD) provided by patients. If the patient provides media infected with ransomware, the infection can quickly spread to the provider’s computer system and from there, infect the remainder of the organization.
Q. What is the best form of defense for healthcare organizations against these cyber attacks?
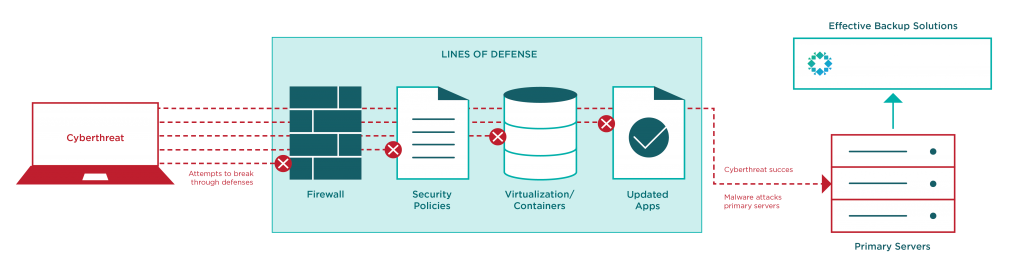
A. As with all information security threats, the best mitigation for ransomware is a defense in depth. Healthcare organizations can reduce the likelihood of infection by maintaining up-to-date software free of known vulnerabilities. By employing technologies such as virtualization or containers, healthcare IT organizations may be able to distribute up-to-date software without the disruption caused by traditional software updates.
Ideally, systems with access to critical data should be used only for that purpose. Enforcing a security policy to prevent other uses of these systems would dramatically reduce the chance of malware infection via malicious web pages or e-mail attachments. In addition, traditional network defenses such as firewalls should be employed. All of these strategies (and many others) serve to reduce the attack surface exposed by healthcare organizations.
Unfortunately, no combination of security measures will completely protect an organization from ransomware or other security breach. IT organizations need to address this problem with an approach that integrates security and data protection. They should not only make attacks difficult to mount, but also ensure that they have access to their data if an attack is successful. Healthcare organizations must maintain reliable and effective backups of their critical data in case of a compromise. With an effective backup solution, ransomware recovery can ideally be reduced to a minor inconvenience with minimal effect on patient care.
Q. What does a backup solution need to ensure that data is protected?
A. An effective backup solution is reliable, durable, secure, and allows data to be restored near-instantaneously.
- A reliable solution is one that takes backups at the prescribed interval. Every time. Without exception. In the event of a ransomware infection, this interval represents the maximum length of time over which changes to the data may be lost. For example, a reliable solution configured to take a backup every four hours should always possess a copy of the protected data that is no more than four hours old.
- A durable solution is one that is resilient to low-level failures such as power loss, mechanical hard disk failures, or even critical components such as the CPU or motherboard.
- A secure solution is one that ensures both the privacy and the integrity of the protected data. Only authorized users should be able to restore the contents of a backup, and the solution should prevent a backup from ever being modified. In particular, ransomware running on a system must never be able to delete or encrypt the backups of that system, which would negate the entire purpose for the backup! In an effective backup architecture, a system being backed up should never have the ability to remove its own backups.
- Finally, an effective backup solution must provide near-instantaneous access to the backed up data in order to minimize downtime in the event of an attack or other failure. Any solution that requires the complete contents of a backup to be first restored to a remote system before it can be utilized is, by this definition, ineffective. Particularly when patient data is involved, organizations must be able live mount and unlock the value of their backups immediately when needed.
Q. How does backup need to evolve so that data protection and security are integrated?
A. The need for significant changes to how backups are managed and protected is imperative. In the last ten years, there has been a lack of innovation while the amount of data growth has been exponential. Legacy architectures are far too complex. Using multiple stacked solutions results in fragmented management and numerous single points of failure that are complicated to address. Additionally, most solutions are not designed for fast data recovery. Often, recovering data can take days or weeks. A modern backup environment must address these issues as well as ensure data security without reducing the speed and efficiency of its data management.
At Rubrik, we aim to equip our customers with the tools needed to recover from unforeseen data loss or ransomware scenarios as painlessly as possible. Our Converged Data Management appliances provide customers automated backup, instant recovery, unlimited replication and archival at infinite scale. Our latest appliance raises the security bar and protects data privacy by offering industry-leading FIPS 140-2 Level 2 certified self-encrypting drives. By providing a backup solution that encrypts data, consistently maintains reliable backups, and provides the necessary functionality, enterprises needing the highest level of security can now ensure that their backup environments adhere to the same standards as their primary infrastructure. In the face of a ransomware attack or other data loss, it is imperative that data protection measures be as strong as possible.
